Assign access to workload owners
When you onboard your Amazon Web Service (AWS) or Google Cloud Platform (GCP) environments, Defender for Cloud automatically creates a security connector as an Azure resource within the connected subscription and resource group. Defender for Cloud also creates the identity provider as an IAM role required during the onboarding process.
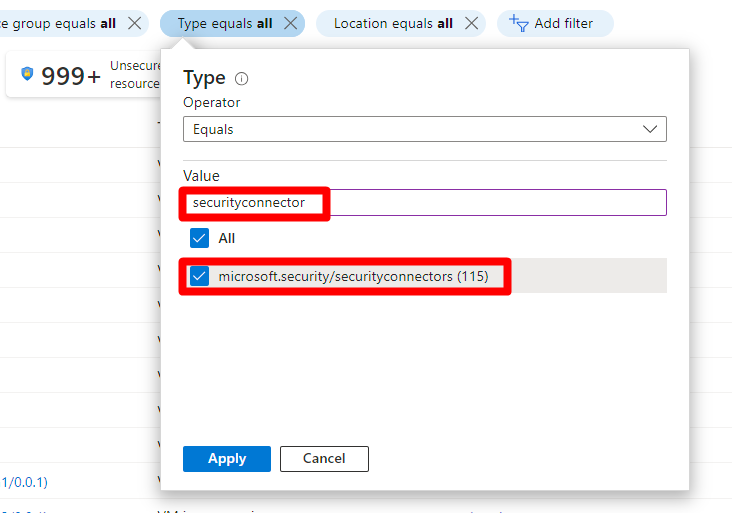
To assign permissions to users on a specific connector below the parent connector, you need to determine which AWS accounts or GCP projects you want users to access. You need to identify the security connectors that correspond to the AWS account or GCP project you want to assign users access to.
Prerequisites
An Azure account. If you don't already have an Azure account, you can create your Azure free account today.
Configure permissions on the security connector
Permissions for security connectors are managed through Azure Role-Based Access Control (RBAC). You can assign roles to users, groups, and applications at a subscription, resource group, or resource level.
Sign in to the Azure portal.
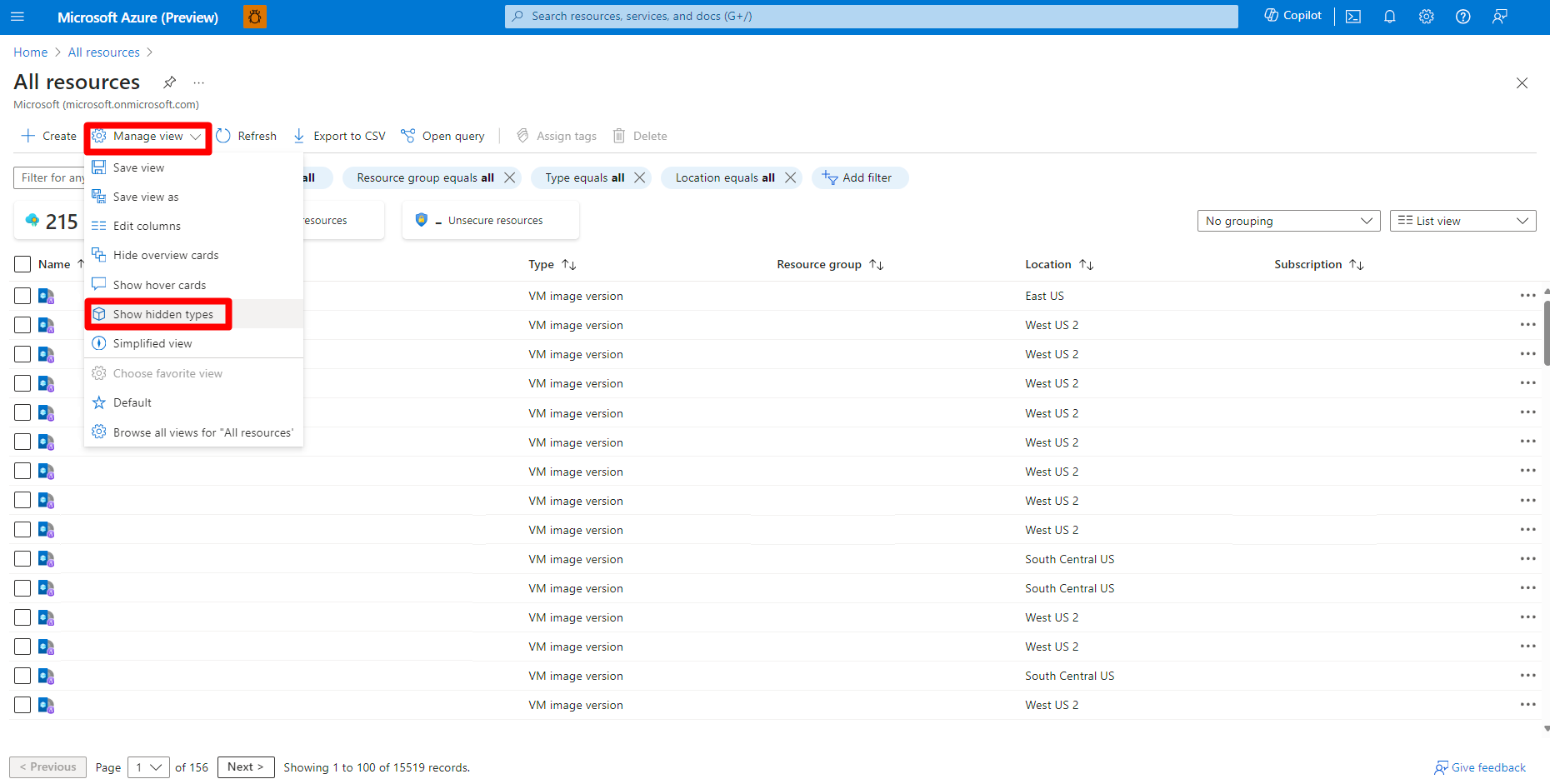
Navigate to Microsoft Defender for Cloud > Environment settings.
Locate the relevant AWS or GCP connector.
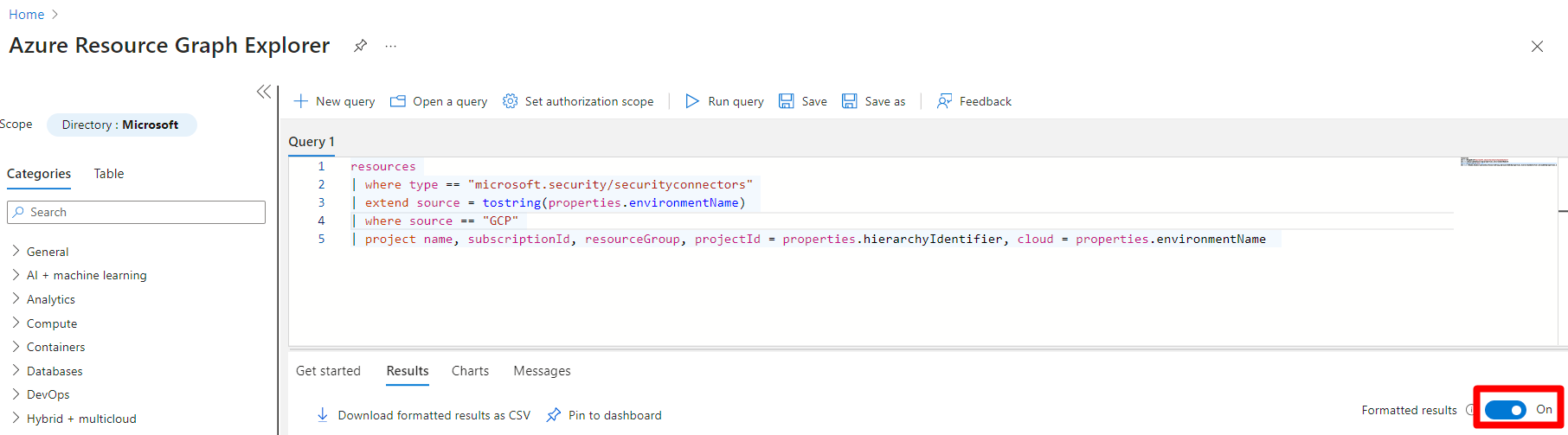
Assign permissions to the workload owners with All resources or the Azure Resource Graph option in the Azure portal.
Select Access control (IAM).
Select +Add > Add role assignment.
Select the desired role.
Select Next.
Select + Select members.

Search for and select the relevant user or group.
Select the Select button.
Select Next.
Select Review + assign.
Review the information.
Select Review + assign.
After setting the permission for the security connector, workload owners will be able to view recommendations in Defender for Cloud for the AWS and GCP resources associated with the security connector.