Quickstart: Create an Azure Firewall and a firewall policy - ARM template
In this quickstart, you use an Azure Resource Manager template (ARM template) to create an Azure Firewall and a firewall policy. The firewall policy has an application rule that allows connections to www.microsoft.com and a rule that allows connections to Windows Update using the WindowsUpdate FQDN tag. A network rule allows UDP connections to a time server at 13.86.101.172.
Also, IP Groups are used in the rules to define the Source IP addresses.
An Azure Resource Manager template is a JavaScript Object Notation (JSON) file that defines the infrastructure and configuration for your project. The template uses declarative syntax. You describe your intended deployment without writing the sequence of programming commands to create the deployment.
For information about Azure Firewall Manager, see What is Azure Firewall Manager?.
For information about Azure Firewall, see What is Azure Firewall?.
For information about IP Groups, see IP Groups in Azure Firewall.
If your environment meets the prerequisites and you're familiar with using ARM templates, select the Deploy to Azure button. The template opens in the Azure portal.
Prerequisites
- An Azure account with an active subscription. Create an account for free.
Review the template
This template creates a hub virtual network, along with the necessary resources to support the scenario.
The template used in this quickstart is from Azure Quickstart Templates.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"metadata": {
"_generator": {
"name": "bicep",
"version": "0.8.9.13224",
"templateHash": "2614956787969031174"
}
},
"parameters": {
"virtualNetworkName": {
"type": "string",
"defaultValue": "[format('vnet{0}', uniqueString(resourceGroup().id))]",
"metadata": {
"description": "Virtual network name"
}
},
"firewallName": {
"type": "string",
"defaultValue": "[format('fw{0}', uniqueString(resourceGroup().id))]",
"metadata": {
"description": "Azure Firewall name"
}
},
"numberOfPublicIPAddresses": {
"type": "int",
"defaultValue": 2,
"maxValue": 100,
"minValue": 1,
"metadata": {
"description": "Number of public IP addresses for the Azure Firewall"
}
},
"availabilityZones": {
"type": "array",
"defaultValue": [],
"metadata": {
"description": "Zone numbers e.g. 1,2,3."
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Location for all resources."
}
},
"infraIpGroupName": {
"type": "string",
"defaultValue": "[format('{0}-infra-ipgroup-{1}', parameters('location'), uniqueString(resourceGroup().id))]"
},
"workloadIpGroupName": {
"type": "string",
"defaultValue": "[format('{0}-workload-ipgroup-{1}', parameters('location'), uniqueString(resourceGroup().id))]"
},
"firewallPolicyName": {
"type": "string",
"defaultValue": "[format('{0}-firewallPolicy', parameters('firewallName'))]"
}
},
"variables": {
"copy": [
{
"name": "azureFirewallIpConfigurations",
"count": "[length(range(0, parameters('numberOfPublicIPAddresses')))]",
"input": {
"name": "[format('IpConf{0}', range(0, parameters('numberOfPublicIPAddresses'))[copyIndex('azureFirewallIpConfigurations')])]",
"properties": {
"subnet": "[if(equals(range(0, parameters('numberOfPublicIPAddresses'))[copyIndex('azureFirewallIpConfigurations')], 0), json(format('{{\"id\": \"{0}\"}}', variables('azureFirewallSubnetId'))), json('null'))]",
"publicIPAddress": {
"id": "[format('{0}{1}', variables('azureFirewallPublicIpId'), add(range(0, parameters('numberOfPublicIPAddresses'))[copyIndex('azureFirewallIpConfigurations')], 1))]"
}
}
}
}
],
"vnetAddressPrefix": "10.10.0.0/24",
"azureFirewallSubnetPrefix": "10.10.0.0/25",
"publicIPNamePrefix": "publicIP",
"azurepublicIpname": "[variables('publicIPNamePrefix')]",
"azureFirewallSubnetName": "AzureFirewallSubnet",
"azureFirewallSubnetId": "[resourceId('Microsoft.Network/virtualNetworks/subnets', parameters('virtualNetworkName'), variables('azureFirewallSubnetName'))]",
"azureFirewallPublicIpId": "[resourceId('Microsoft.Network/publicIPAddresses', variables('publicIPNamePrefix'))]"
},
"resources": [
{
"type": "Microsoft.Network/ipGroups",
"apiVersion": "2022-01-01",
"name": "[parameters('workloadIpGroupName')]",
"location": "[parameters('location')]",
"properties": {
"ipAddresses": [
"10.20.0.0/24",
"10.30.0.0/24"
]
}
},
{
"type": "Microsoft.Network/ipGroups",
"apiVersion": "2022-01-01",
"name": "[parameters('infraIpGroupName')]",
"location": "[parameters('location')]",
"properties": {
"ipAddresses": [
"10.40.0.0/24",
"10.50.0.0/24"
]
}
},
{
"type": "Microsoft.Network/virtualNetworks",
"apiVersion": "2022-01-01",
"name": "[parameters('virtualNetworkName')]",
"location": "[parameters('location')]",
"tags": {
"displayName": "[parameters('virtualNetworkName')]"
},
"properties": {
"addressSpace": {
"addressPrefixes": [
"[variables('vnetAddressPrefix')]"
]
},
"subnets": [
{
"name": "[variables('azureFirewallSubnetName')]",
"properties": {
"addressPrefix": "[variables('azureFirewallSubnetPrefix')]"
}
}
],
"enableDdosProtection": false
}
},
{
"copy": {
"name": "publicIpAddress",
"count": "[length(range(0, parameters('numberOfPublicIPAddresses')))]"
},
"type": "Microsoft.Network/publicIPAddresses",
"apiVersion": "2022-01-01",
"name": "[format('{0}{1}', variables('azurepublicIpname'), add(range(0, parameters('numberOfPublicIPAddresses'))[copyIndex()], 1))]",
"location": "[parameters('location')]",
"sku": {
"name": "Standard"
},
"properties": {
"publicIPAllocationMethod": "Static",
"publicIPAddressVersion": "IPv4"
}
},
{
"type": "Microsoft.Network/firewallPolicies",
"apiVersion": "2022-01-01",
"name": "[parameters('firewallPolicyName')]",
"location": "[parameters('location')]",
"properties": {
"threatIntelMode": "Alert"
}
},
{
"type": "Microsoft.Network/firewallPolicies/ruleCollectionGroups",
"apiVersion": "2022-01-01",
"name": "[format('{0}/{1}', parameters('firewallPolicyName'), 'DefaultNetworkRuleCollectionGroup')]",
"properties": {
"priority": 200,
"ruleCollections": [
{
"ruleCollectionType": "FirewallPolicyFilterRuleCollection",
"action": {
"type": "Allow"
},
"name": "azure-global-services-nrc",
"priority": 1250,
"rules": [
{
"ruleType": "NetworkRule",
"name": "time-windows",
"ipProtocols": [
"UDP"
],
"destinationAddresses": [
"13.86.101.172"
],
"sourceIpGroups": [
"[resourceId('Microsoft.Network/ipGroups', parameters('workloadIpGroupName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('infraIpGroupName'))]"
],
"destinationPorts": [
"123"
]
}
]
}
]
},
"dependsOn": [
"[resourceId('Microsoft.Network/firewallPolicies', parameters('firewallPolicyName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('infraIpGroupName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('workloadIpGroupName'))]"
]
},
{
"type": "Microsoft.Network/firewallPolicies/ruleCollectionGroups",
"apiVersion": "2022-01-01",
"name": "[format('{0}/{1}', parameters('firewallPolicyName'), 'DefaultApplicationRuleCollectionGroup')]",
"properties": {
"priority": 300,
"ruleCollections": [
{
"ruleCollectionType": "FirewallPolicyFilterRuleCollection",
"name": "global-rule-url-arc",
"priority": 1000,
"action": {
"type": "Allow"
},
"rules": [
{
"ruleType": "ApplicationRule",
"name": "winupdate-rule-01",
"protocols": [
{
"protocolType": "Https",
"port": 443
},
{
"protocolType": "Http",
"port": 80
}
],
"fqdnTags": [
"WindowsUpdate"
],
"terminateTLS": false,
"sourceIpGroups": [
"[resourceId('Microsoft.Network/ipGroups', parameters('workloadIpGroupName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('infraIpGroupName'))]"
]
}
]
},
{
"ruleCollectionType": "FirewallPolicyFilterRuleCollection",
"action": {
"type": "Allow"
},
"name": "Global-rules-arc",
"priority": 1202,
"rules": [
{
"ruleType": "ApplicationRule",
"name": "global-rule-01",
"protocols": [
{
"protocolType": "Https",
"port": 443
}
],
"targetFqdns": [
"www.microsoft.com"
],
"terminateTLS": false,
"sourceIpGroups": [
"[resourceId('Microsoft.Network/ipGroups', parameters('workloadIpGroupName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('infraIpGroupName'))]"
]
}
]
}
]
},
"dependsOn": [
"[resourceId('Microsoft.Network/firewallPolicies', parameters('firewallPolicyName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('infraIpGroupName'))]",
"[resourceId('Microsoft.Network/firewallPolicies/ruleCollectionGroups', parameters('firewallPolicyName'), 'DefaultNetworkRuleCollectionGroup')]",
"[resourceId('Microsoft.Network/ipGroups', parameters('workloadIpGroupName'))]"
]
},
{
"type": "Microsoft.Network/azureFirewalls",
"apiVersion": "2021-03-01",
"name": "[parameters('firewallName')]",
"location": "[parameters('location')]",
"zones": "[if(equals(length(parameters('availabilityZones')), 0), null(), parameters('availabilityZones'))]",
"properties": {
"ipConfigurations": "[variables('azureFirewallIpConfigurations')]",
"firewallPolicy": {
"id": "[resourceId('Microsoft.Network/firewallPolicies', parameters('firewallPolicyName'))]"
}
},
"dependsOn": [
"[resourceId('Microsoft.Network/firewallPolicies/ruleCollectionGroups', parameters('firewallPolicyName'), 'DefaultApplicationRuleCollectionGroup')]",
"[resourceId('Microsoft.Network/firewallPolicies', parameters('firewallPolicyName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('infraIpGroupName'))]",
"[resourceId('Microsoft.Network/firewallPolicies/ruleCollectionGroups', parameters('firewallPolicyName'), 'DefaultNetworkRuleCollectionGroup')]",
"publicIpAddress",
"[resourceId('Microsoft.Network/virtualNetworks', parameters('virtualNetworkName'))]",
"[resourceId('Microsoft.Network/ipGroups', parameters('workloadIpGroupName'))]"
]
}
]
}
Multiple Azure resources are defined in the template:
- Microsoft.Network/ipGroups
- Microsoft.Network/firewallPolicies
- Microsoft.Network/firewallPolicies/ruleCollectionGroups
- Microsoft.Network/azureFirewalls
- Microsoft.Network/virtualNetworks
- Microsoft.Network/publicIPAddresses
Deploy the template
Deploy the ARM template to Azure:
Select Deploy to Azure to sign in to Azure and open the template. The template creates an Azure Firewall, a virtual WAN and virtual hub, the network infrastructure, and two virtual machines.
In the portal, on the Create a Firewall and FirewallPolicy with Rules and Ipgroups page, type or select the following values:
- Subscription: Select from existing subscriptions.
- Resource group: Select from existing resource groups or select Create new, and select OK.
- Region: Select a region.
- Firewall Name: type a name for the firewall.
Select Review + create and then select Create. The deployment can take 10 minutes or longer to complete.
Review deployed resources
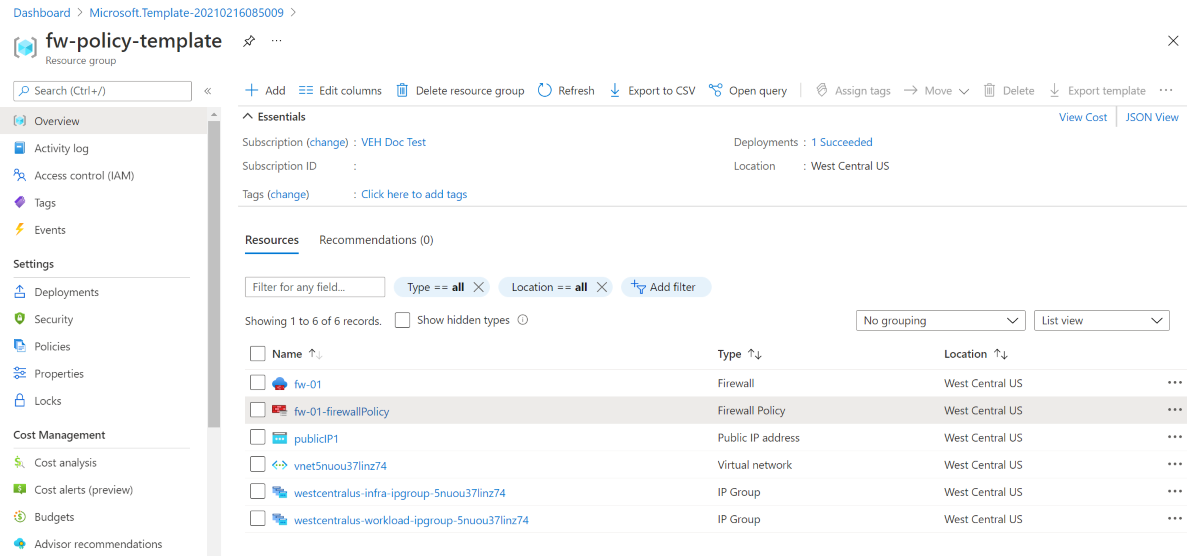
After deployment completes, you'll see the following similar resources.
Clean up resources
When you no longer need the resources that you created with the firewall, delete the resource group. This removes the firewall and all the related resources.
To delete the resource group, call the Remove-AzResourceGroup cmdlet:
Remove-AzResourceGroup -Name "<your resource group name>"
