Merk
Tilgang til denne siden krever autorisasjon. Du kan prøve å logge på eller endre kataloger.
Tilgang til denne siden krever autorisasjon. Du kan prøve å endre kataloger.
Microsoft Defender for Cloud Apps lar deg automatisk bruke følsomhetsetiketter fra Microsoft Purview. Disse etikettene brukes på filer som en filpolicystyringshandling, og kan, avhengig av etikettkonfigurasjonen, bruke kryptering for ekstra beskyttelse. Du kan også undersøke filer ved å filtrere etter den brukte følsomhetsetiketten i Defender for Cloud Apps. Bruk av etiketter gir større synlighet og kontroll over sensitive data i skyen. Integrering av Microsoft Purview med Defender for Cloud Apps er like enkelt som å velge én enkelt avmerkingsboks.
Ved å integrere Microsoft Purview i Defender for Cloud Apps, kan du bruke den fulle kraften til både tjenester og sikre filer i skyen, inkludert:
- Muligheten til å bruke følsomhetsetiketter som en styringshandling på filer som samsvarer med bestemte policyer
- Muligheten til å vise alle klassifiserte filer på en sentral plassering
- Muligheten til å undersøke i henhold til klassifiseringsnivå, og kvantifisere eksponering av sensitive data over skyprogrammene dine
- Muligheten til å opprette policyer for å sikre at klassifiserte filer håndteres på riktig måte
Forutsetninger
Obs!
Hvis du vil aktivere denne funksjonen, trenger du både en Defender for Cloud Apps-lisens og en lisens for Microsoft Purview. Så snart begge lisensene er på plass, synkroniserer Defender for Cloud Apps organisasjonens etiketter fra Microsoft Purview.
- Hvis du vil arbeide med Microsoft Purview-integrering, må du aktivere App-koblingen for Microsoft 365.
For at Defender for Cloud Apps skal kunne bruke følsomhetsetiketter, må de publiseres som en del av en policy for følsomhetsetiketter i Microsoft Purview.
Defender for Cloud Apps støtter for øyeblikket bruk av følsomhetsetiketter fra Microsoft Purview for følgende filtyper:
- Word: docm, docx, dotm, dotx
- Excel: xlam, xlsm, xlsx, xltx
- PowerPoint: potm, potx, ppsx, ppsm, pptm, pptx
- PDF-fil
Obs!
For PDF må du bruke enhetlige etiketter.
Denne funksjonen er for øyeblikket tilgjengelig for filer som er lagret i Box, Google Workspace, SharePoint Online og OneDrive. Flere skyapper støttes i fremtidige versjoner.
Slik fungerer det
Du kan se følsomhetsetikettene fra Microsoft Purview i Defender for Cloud Apps. Så snart du integrerer Defender for Cloud Apps med Microsoft Purview, skanner Defender for Cloud Apps filer på følgende måte:
Defender for Cloud Apps henter listen over alle følsomhetsetikettene som brukes i leieren. Denne handlingen utføres hver time for å holde listen oppdatert.
Defender for Cloud Apps skanner deretter filene etter følsomhetsetiketter, som følger:
- Hvis du har aktivert automatisk skanning, legges alle nye eller endrede filer til i skannekøen, og alle eksisterende filer og repositorier skannes.
- Hvis du angir en filpolicy for å søke etter følsomhetsetiketter, legges disse filene til i skannekøen for følsomhetsetiketter.
Som nevnt er disse skanningene for følsomhetsetikettene som ble oppdaget i den første skanningen, Defender for Cloud Apps gjør for å se hvilke følsomhetsetiketter som brukes i leieren. Eksterne etiketter, klassifiseringsetiketter som er angitt av noen utenfor leieren, legges til i listen over klassifiseringsetiketter. Hvis du ikke vil søke etter disse, merker du av for Bare skanne filer for Microsoft Information Protection følsomhetsetiketter og advarsler for innholdsinspeksjon fra denne leieren.
Når du aktiverer Microsoft Purview på Defender for Cloud Apps, skannes alle nye filer som legges til i de tilkoblede skyappene, for følsomhetsetiketter.
Du kan opprette nye policyer i Defender for Cloud Apps som bruker følsomhetsetikettene automatisk.
Integreringsgrenser
Legg merke til følgende begrensninger når du bruker Microsoft Purview-etiketter med Defender for Cloud Apps.
| Grense | Beskrivelse |
|---|---|
| Filer med etiketter eller beskyttelse brukt utenfor Defender for Cloud Apps | Ubeskyttede etiketter som brukes utenfor Defender for Cloud Apps, kan overstyres av Defender for Cloud Apps men kan ikke fjernes.
Defender for Cloud Apps kan ikke fjerne etiketter med beskyttelse mot filer som ble merket utenfor Defender for Cloud Apps. Hvis du vil skanne filer med beskyttelse som brukes utenfor Defender for skyapper, kan du gi tillatelse til å undersøke innhold for beskyttede filer. |
| Filer merket av Defender for Cloud Apps | Defender for Cloud Apps overstyrer ikke etiketter på filer som allerede er merket av Defender for Cloud Apps. |
| Passordbeskyttede filer | Defender for Cloud Apps kan ikke lese etiketter på passordbeskyttede filer. |
| Tomme filer | Tomme filer merkes ikke av Defender for Cloud Apps. |
| Biblioteker som krever utsjekking | Defender for Cloud Apps kan ikke merke filer som er plassert i biblioteker som er konfigurert til å kreve utsjekking. |
| Omfangskrav | For at Defender for Cloud Apps skal gjenkjenne en følsomhetsetikett, må etikettomfanget i Purview konfigureres for minst filer og e-postmeldinger. |
Obs!
Microsoft Purview er Microsofts hovedløsning for merketjenester. Hvis du vil ha mer informasjon, kan du se dokumentasjonen for Microsoft Purview.
Slik integrerer du Microsoft Purview med Defender for Cloud Apps
Aktiver Microsoft Purview
Alt du trenger å gjøre for å integrere Microsoft Purview med Defender for Cloud Apps er å velge én enkelt avmerkingsboks. Ved å aktivere automatisk skanning aktiverer du søk etter følsomhetsetiketter fra Microsoft Purview på Microsoft 365-filene dine uten å måtte opprette en policy. Når du har aktivert det, ser du dem i Defender for Cloud Apps hvis du har filer i skymiljøet som er merket med følsomhetsetiketter fra Microsoft Purview.
Slik aktiverer du Defender for Cloud Apps skanne filer med innholdsinspeksjon aktivert for følsomhetsetiketter:
Velg Innstillinger i Microsoft Defender-portalen. Velg deretter Skyapper. Gå deretter til Information Protection ->Microsoft Information Protection.
Under Innstillinger for Microsoft Information Protection velger du Automatisk skanning av nye filer for følsomhetsetiketter fra Microsoft Information Protection og advarsler for innholdsinspeksjon.

Når du har aktivert Microsoft Purview, kan du se filer som har følsomhetsetiketter og filtrere dem per etikett i Defender for Cloud Apps. Når Defender for Cloud Apps er koblet til skyappen, kan du bruke integreringsfunksjonene for Microsoft Purview til å bruke følsomhetsetiketter fra Microsoft Purview (med eller uten kryptering) i Defender for Cloud Apps, ved å legge dem direkte til filer eller ved å konfigurere en filpolicy til å bruke følsomhetsetiketter automatisk som en styringshandling.
Obs!
Automatisk skanning skanner ikke eksisterende filer før de endres på nytt. Hvis du vil skanne eksisterende filer etter følsomhetsetiketter fra Microsoft Purview, må du ha minst én filpolicy som inkluderer innholdsinspeksjon. Hvis du ikke har noen, oppretter du en ny filpolicy, sletter alle forhåndsinnstilte filtre, under Inspeksjonsmetode velger du Innebygd DLP. Velg Inkluder filer som samsvarer med et forhåndsinnstilt uttrykk, i innholdsinspeksjonsfeltet, og velg en forhåndsdefinert verdi, og lagre policyen. Dette muliggjør innholdsinspeksjon, som automatisk oppdager følsomhetsetiketter fra Microsoft Purview.
Angi interne og eksterne etiketter
Som standard skanner Defender for Cloud Apps følsomhetsetiketter som ble definert i organisasjonen, og eksterne etiketter som er definert av andre organisasjoner.
Hvis du vil ignorere følsomhetsetiketter som er angitt utenfor organisasjonen, går du til Microsoft Defender-portalen og velger Innstillinger. Velg deretter Skyapper. Velg Microsoft Information Protection under Information Protection. Velg deretter Bare skanne filer for Microsoft Information Protection følsomhetsetiketter og advarsler for innholdsinspeksjon fra denne leieren.

Bruke etiketter direkte på filer
Velg Filer under Skyapper i Microsoft Defender-portalen. Velg deretter filen du vil beskytte. Velg de tre prikkene på slutten av filens rad, og velg deretter Bruk følsomhetsetikett.

Obs!
Defender for Cloud Apps kan bruke Microsoft Purview på filer som er opptil 30 MB.
Velg en av organisasjonens følsomhetsetiketter som skal brukes på filen, og velg Bruk.

Når du har valgt en følsomhetsetikett og velger Bruk, bruker Defender for Cloud Apps følsomhetsetiketten på den opprinnelige filen.
Du kan også fjerne følsomhetsetiketter ved å velge alternativet Fjern følsomhetsetikett .
Hvis du vil ha mer informasjon om hvordan Defender for Cloud Apps og Microsoft Purview fungerer sammen, kan du se Bruke følsomhetsetiketter automatisk fra Microsoft Purview.
Etikettfiler automatisk
Du kan automatisk bruke følsomhetsetiketter på filer ved å opprette en filpolicy og angi Bruk følsomhetsetikett som styringshandling.
Følg disse instruksjonene for å opprette filpolicyen:
Opprett en filpolicy.
Angi policyen for å inkludere filtypen du vil finne. Du kan for eksempel velge alle filer der Access-nivået ikke er likt Internt , og der eier-OU er lik økonomiteamet ditt.
Velg Bruk følsomhetsetikett under styringshandlinger for den aktuelle appen, og velg deretter etiketttypen.
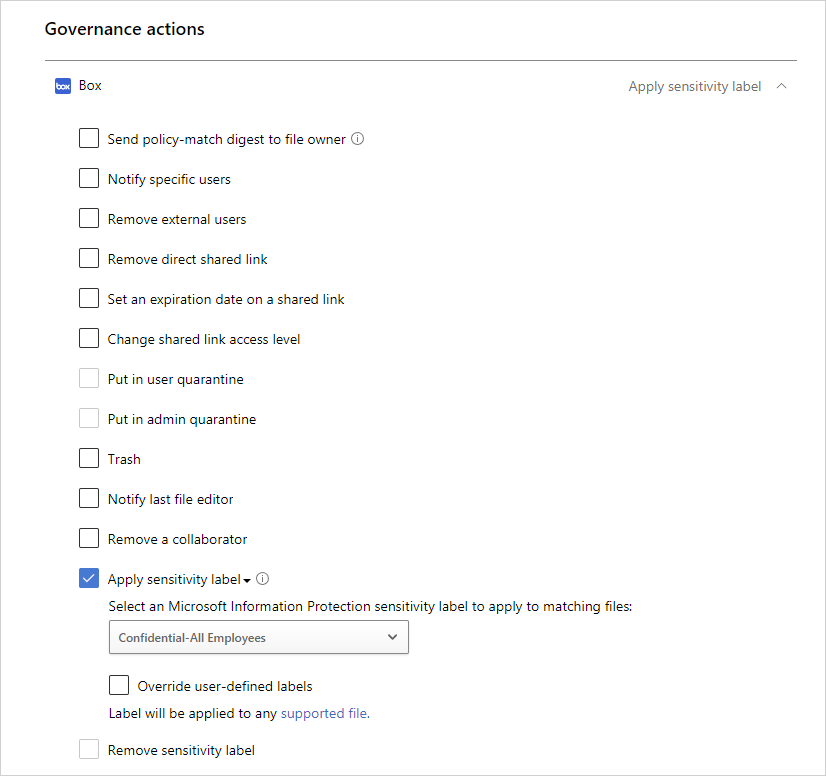
Obs!
- Muligheten til å bruke en følsomhetsetikett er en kraftig funksjon. For å beskytte kunder mot å feilaktig bruke en etikett på et stort antall filer, er det som en sikkerhetsforanstaltning en daglig grense på 100 Bruk etiketthandlinger per app, per leier. Når den daglige grensen er nådd, stanses handlingen Bruk etikett midlertidig og fortsetter automatisk neste dag (etter 12:00 UTC).
- Når en policy er deaktivert, deaktiveres alle ventende etikettoppgaver for denne policyen.
- I etikettkonfigurasjonen må tillatelser tilordnes til godkjente brukere, eller alle brukere i organisasjonen, for at Defender for Cloud Apps skal kunne lese etikettinformasjon.
Kontroller fileksponering
La oss for eksempel si at du merket følgende dokument med en Microsoft Purview-følsomhetsetikett:

Du kan se dette dokumentet i Defender for Cloud Apps ved å filtrere på følsomhetsetiketten for Microsoft Purview på Filer-siden.

Du kan få mer informasjon om disse filene og følsomhetsetikettene i filskuffen. Bare velg den relevante filen på Filer-siden , og kontroller om den har en følsomhetsetikett.
Deretter kan du opprette filpolicyer i Defender for Cloud Apps for å kontrollere filer som deles upassende, og finne filer som er merket og nylig ble endret.
- Du kan opprette en policy som automatisk bruker en følsomhetsetikett på bestemte filer.
- Du kan også utløse varsler om aktiviteter relatert til filklassifisering.
Obs!
Når følsomhetsetiketter er deaktivert på en fil, vises de deaktiverte etikettene som deaktivert i Defender for Cloud Apps. Slettede etiketter vises ikke.
Eksempelpolicy – konfidensielle data som deles eksternt på Box:
Opprett en filpolicy.
Angi policyens navn, alvorlighetsgrad og kategori.
Legg til følgende filtre for å finne alle konfidensielle data som deles eksternt i Box:

Eksempelpolicy – begrensede data som nylig ble endret utenfor Kundedata-mappen på SharePoint:
Opprett en filpolicy.
Angi policyens navn, alvorlighetsgrad og kategori.
Legg til følgende filtre for å finne alle nylig endrede begrensede filer mens du utelater Kundedata-mappen i mappevalgalternativet:

Du kan også velge å angi varsler, brukervarsler eller utføre umiddelbare handlinger for disse policyene. Mer informasjon om styringshandlinger.
Mer informasjon om Microsoft Purview.
Neste trinn
Hvis det oppstår problemer, er vi her for å hjelpe. Hvis du vil ha hjelp eller støtte for produktproblemet, kan du åpne en støtteforespørsel.
