Authenticate .NET apps to Azure services during local development using developer accounts
Developers need to debug and test cloud apps on their local workstations. When an app runs on a developer's workstation during local development, it must still authenticate to any Azure services used by the app. This article covers how to use a developer's Azure credentials to authenticate the app to Azure during local development.

For an app to authenticate to Azure during local development using the developer's Azure credentials, the developer must be signed in to Azure from one of the following developer tools:
- Visual Studio
- Azure CLI
- Azure Developer CLI
- Azure PowerShell
The Azure Identity library can detect that the developer is signed in from one of these tools. The library can then obtain the Microsoft Entra access token via the tool to authenticate the app to Azure as the signed-in user.
This approach is easiest to set up for a development team since it takes advantage of the developers' existing Azure accounts. However, a developer's account likely has more permissions than required by the app, therefore exceeding the permissions the app runs with in production. As an alternative, you can create application service principals to use during local development, which can be scoped to have only the access needed by the app.
1 - Create Microsoft Entra group for local development
Since there are almost always multiple developers who work on an app, a Microsoft Entra group is recommended to encapsulate the roles (permissions) the app needs in local development. This approach offers the following advantages:
- Every developer is assured to have the same roles assigned since roles are assigned at the group level.
- If a new role is needed for the app, it only needs to be added to the group for the app.
- If a new developer joins the team, they gain the necessary permissions to work on the app after being added to the group.
If you have an existing Microsoft Entra group for your development team, you can use that group. Otherwise, complete the following steps to create a Microsoft Entra group.
Note
By default, the creation of Microsoft Entra groups is limited to certain privileged roles in a directory. If you're unable to create a group, contact an administrator for your directory. If you're unable to add members to an existing group, contact the group owner or a directory administrator. To learn more, see Manage Microsoft Entra groups and group membership.
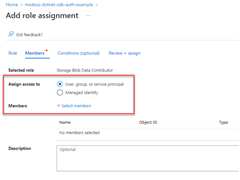
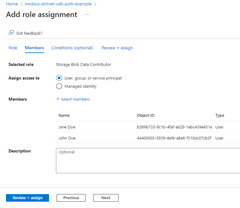
2 - Assign roles to the Microsoft Entra group
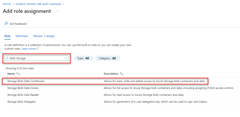
Next, determine what roles (permissions) your app needs on what resources and assign those roles to your app. In this example, the roles are assigned to the Microsoft Entra group created in step 1. Groups can be assigned a role at a resource, resource group, or subscription scope. This example shows how to assign roles at the resource group, scope since most apps group all their Azure resources into a single resource group.
3 - Sign in to Azure using developer tooling
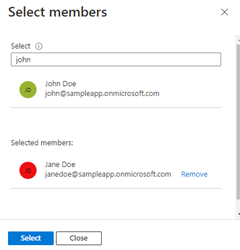
Next, sign in to Azure using one of several developer tools. The account you authenticate should also exist in the Microsoft Entra group you created and configured earlier.
Navigate to Tools > Options to open the options dialog.
In the Search Options box at the top, type Azure to filter the available options.
Under Azure Service Authentication, choose Account Selection.
Select the drop-down menu under Choose an account and choose to add a Microsoft Account. A window opens, prompting you to pick an account. Enter the credentials for your desired Azure account, and then select the confirmation.

Select OK to close the options dialog.
4 - Implement DefaultAzureCredential in your application
DefaultAzureCredential is an opinionated, ordered sequence of mechanisms for authenticating to Microsoft Entra ID. Each authentication mechanism is a class derived from the TokenCredential class and is known as a credential. At runtime, DefaultAzureCredential attempts to authenticate using the first credential. If that credential fails to acquire an access token, the next credential in the sequence is attempted, and so on, until an access token is successfully obtained. In this way, your app can use different credentials in different environments without writing environment-specific code.
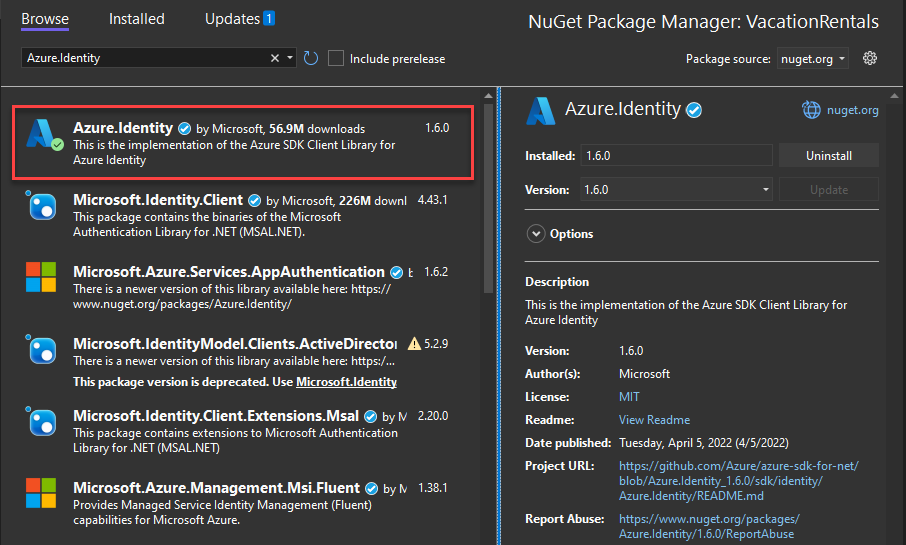
To use DefaultAzureCredential, add the Azure.Identity and optionally the Microsoft.Extensions.Azure packages to your application:
In a terminal of your choice, navigate to the application project directory and run the following commands:
dotnet add package Azure.Identity
dotnet add package Microsoft.Extensions.Azure
Azure services are accessed using specialized client classes from the various Azure SDK client libraries. These classes and your own custom services should be registered so they can be accessed via dependency injection throughout your app. In Program.cs, complete the following steps to register a client class and DefaultAzureCredential:
- Include the
Azure.IdentityandMicrosoft.Extensions.Azurenamespaces viausingdirectives. - Register the Azure service client using the corresponding
Add-prefixed extension method. - Pass an instance of
DefaultAzureCredentialto theUseCredentialmethod.
For example:
using Microsoft.Extensions.Azure;
using Azure.Identity;
builder.Services.AddAzureClients(clientBuilder =>
{
clientBuilder.AddBlobServiceClient(
new Uri("https://<account-name>.blob.core.windows.net"));
clientBuilder.UseCredential(new DefaultAzureCredential());
});
An alternative to UseCredential is to instantiate DefaultAzureCredential directly:
using Azure.Identity;
builder.Services.AddSingleton<BlobServiceClient>(_ =>
new BlobServiceClient(
new Uri("https://<account-name>.blob.core.windows.net"),
new DefaultAzureCredential()));
When the preceding code runs on your local development workstation, it looks in the environment variables for an application service principal or at locally installed developer tools, such as Visual Studio, for a set of developer credentials. Either approach can be used to authenticate the app to Azure resources during local development.
When deployed to Azure, this same code can also authenticate your app to other Azure resources. DefaultAzureCredential can retrieve environment settings and managed identity configurations to authenticate to other services automatically.