Observação
O acesso a essa página exige autorização. Você pode tentar entrar ou alterar diretórios.
O acesso a essa página exige autorização. Você pode tentar alterar os diretórios.
Azure AD Managed Identities may be used to permission Azure CycleCloud to manage clusters in your subscription (as an alternative to using a Service Principal). Eles também podem ser atribuídos a VMs do CycleCloud para fornecer acesso aos recursos do Azure (como Armazenamento, Cofre de Chaves ou Registros de Contêiner do Azure).
Permissões de VM do CycleCloud com identidade gerenciada
O CycleCloud automatiza muitas chamadas para o Azure Resource Manager para fins de gerenciamento de clusters HPC. Essa automação requer certas permissões a serem concedidas ao CycleCloud. Esse acesso pode ser concedido ao CycleCloud configurando um Principal de Serviço ou atribuindo uma Identidade Gerenciada à VM do CycleCloud.
It is generally recommended to use either a System-Assigned or User-Assigned Managed Identity to grant those permissions rather than a Service Principal.
When Azure CycleCloud has been installed on an Azure VM with a Managed Identity assigned to it, the Add Subscription dialog will behave slightly differently. The Managed Identity authentication option will be enabled and pre-selected, and the Subscription ID will be pre-populated with the subscription of the host VM.
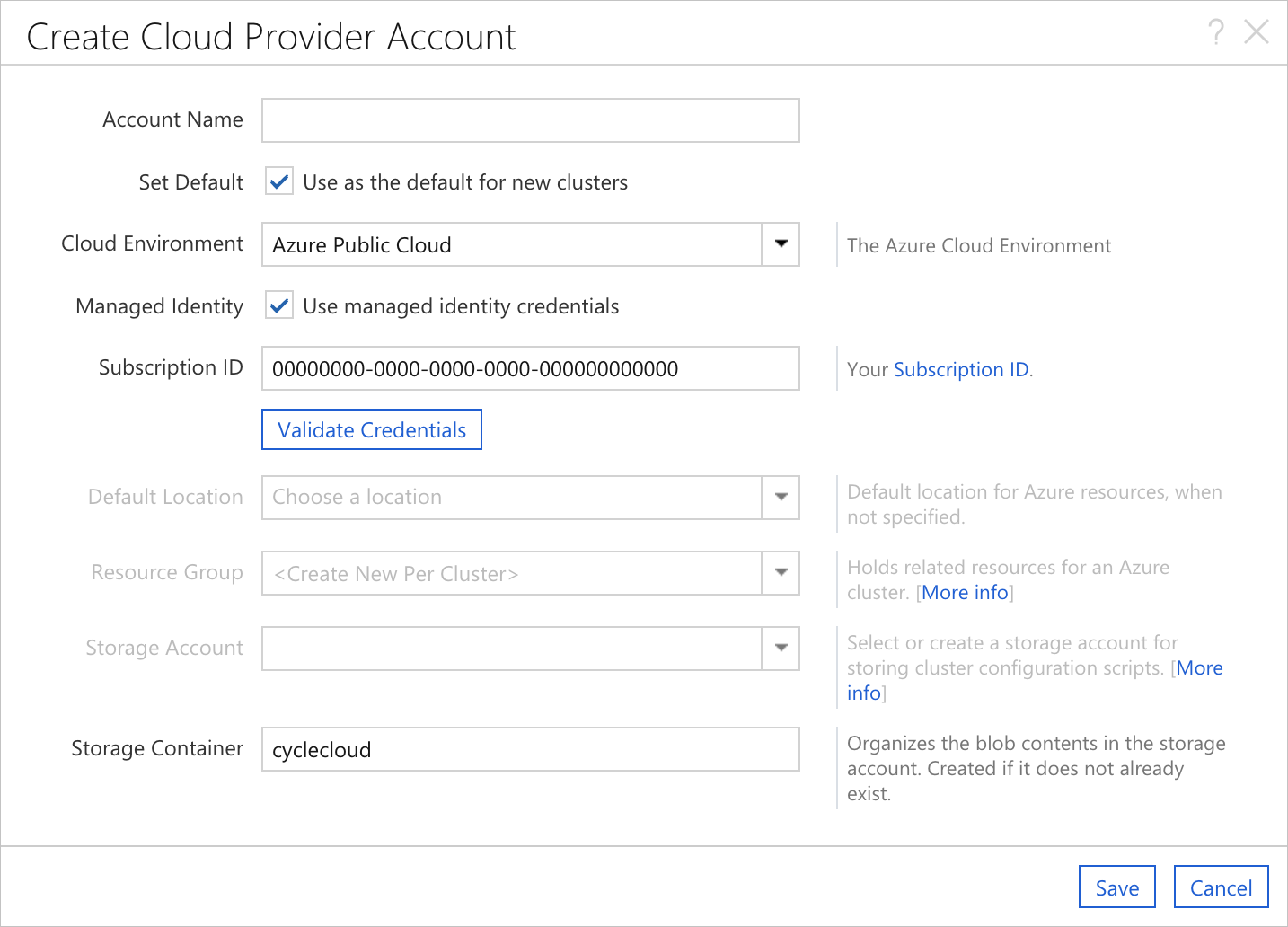

It is still possible to enter the standard set of credentials by simply selecting the App Registration authentication option. Ao fazer isso, os campos padrão serão adicionados ao formulário. Além disso, é perfeitamente aceitável usar um ID de Subscrição separado; o valor fornecido é apenas por conveniência.
When using a System Assigned Managed Identity, the ClientID field can be left blank. However, when using CycleCloud with a User-Assigned Managed Identity, the ClientID should be set to the ClientID of the specific Managed Identity intended for cluster orchestration.
Storage Locker Access
In addition to using a Managed Identity for cluster orchestration on the CycleCloud VM, CycleCloud can also be configured to assign a User-Assigned Managed Identity to clusters for Storage Account / Locker access from cluster nodes rather than using SAS tokens derived from the Storage Account's Shared Access Key.
To configure clusters to use a User-Assigned Managed Identity rather than the Shared Access Key, we recommend creating a dedicated User-Assigned Managed Identity with Storage Blob Data Reader access at the Storage Account scope. First, create the Storage Account and User-Assigned Managed Identity in your Azure Subscription. Then in the Storage Locker Configuration section of the "Add Subscription" dialog, select the new Managed Identity from the Locker Identity dropdown and the Storage Account from the Storage Account dropdown.
Criar uma função personalizada e uma identidade gerenciada para o CycleCloud
The simplest option (with sufficient access rights) is to assign the Contributor and Storage Blob Data Contributor roles for the Subscription to the CycleCloud VM as a System-Assigned Managed Identity. However, the Contributor Role has a higher privilege level than CycleCloud requires. A custom Role may be created and assigned to the VM. Similarly, the Storage Blob Data Contributor Role may be assigned at the Storage Account scope rather than subscription scope if the Storage Account has already been created.
Esta função abrange todos os recursos do CycleCloud:
{
"assignableScopes": [
"/subscriptions/<SubscriptionId>"
],
"description": "CycleCloud Orchestrator Role",
"permissions": [
{
"actions": [
"Microsoft.Authorization/*/read",
"Microsoft.Authorization/roleAssignments/*",
"Microsoft.Authorization/roleDefinitions/*",
"Microsoft.Commerce/RateCard/read",
"Microsoft.Compute/*/read",
"Microsoft.Compute/availabilitySets/*",
"Microsoft.Compute/disks/*",
"Microsoft.Compute/images/read",
"Microsoft.Compute/locations/usages/read",
"Microsoft.Compute/register/action",
"Microsoft.Compute/skus/read",
"Microsoft.Compute/virtualMachines/*",
"Microsoft.Compute/virtualMachineScaleSets/*",
"Microsoft.Compute/virtualMachineScaleSets/virtualMachines/*",
"Microsoft.ManagedIdentity/userAssignedIdentities/*/read",
"Microsoft.ManagedIdentity/userAssignedIdentities/*/assign/action",
"Microsoft.MarketplaceOrdering/offertypes/publishers/offers/plans/agreements/read",
"Microsoft.MarketplaceOrdering/offertypes/publishers/offers/plans/agreements/write",
"Microsoft.Network/*/read",
"Microsoft.Network/locations/*/read",
"Microsoft.Network/networkInterfaces/read",
"Microsoft.Network/networkInterfaces/write",
"Microsoft.Network/networkInterfaces/delete",
"Microsoft.Network/networkInterfaces/join/action",
"Microsoft.Network/networkSecurityGroups/read",
"Microsoft.Network/networkSecurityGroups/write",
"Microsoft.Network/networkSecurityGroups/delete",
"Microsoft.Network/networkSecurityGroups/join/action",
"Microsoft.Network/publicIPAddresses/read",
"Microsoft.Network/publicIPAddresses/write",
"Microsoft.Network/publicIPAddresses/delete",
"Microsoft.Network/publicIPAddresses/join/action",
"Microsoft.Network/register/action",
"Microsoft.Network/virtualNetworks/read",
"Microsoft.Network/virtualNetworks/subnets/read",
"Microsoft.Network/virtualNetworks/subnets/join/action",
"Microsoft.Resources/deployments/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Resources/subscriptions/resourceGroups/write",
"Microsoft.Resources/subscriptions/resourceGroups/delete",
"Microsoft.Resources/subscriptions/resourceGroups/resources/read",
"Microsoft.Resources/subscriptions/operationresults/read",
"Microsoft.Storage/*/read",
"Microsoft.Storage/checknameavailability/read",
"Microsoft.Storage/register/action",
"Microsoft.Storage/storageAccounts/blobServices/containers/delete",
"Microsoft.Storage/storageAccounts/blobServices/containers/read",
"Microsoft.Storage/storageAccounts/blobServices/containers/write",
"Microsoft.Storage/storageAccounts/blobServices/generateUserDelegationKey/action",
"Microsoft.Storage/storageAccounts/read",
"Microsoft.Storage/storageAccounts/listKeys/action",
"Microsoft.Storage/storageAccounts/write"
],
"dataActions": [
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/delete",
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read",
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write",
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/move/action",
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action"
],
"notActions": [],
"notDataActions": []
}
],
"Name": "CycleCloud <SubscriptionId>",
"roleType": "CustomRole",
"type": "Microsoft.Authorization/roleDefinitions"
}
Certifique-se de que substitui <SubscriptionId> pelo seu ID de subscrição. Essa função tem como escopo uma assinatura, mas pode ser definida como escopo para um único grupo de recursos, se preferir. Observe também que o nome deve ser exclusivo para o locatário.
Important
O uso de uma função personalizada requer uma licença do Microsoft Entra ID P1. To find the right license for your requirements, see Microsoft Entra plans and pricing.
Permissões opcionais
Se você estiver definindo o escopo do CycleCloud para usar um único grupo de recursos por cluster, poderá remover o seguinte de actions:
"Microsoft.Resources/subscriptions/resourceGroups/write",
"Microsoft.Resources/subscriptions/resourceGroups/delete",
Se você não estiver usando o CycleCloud para atribuir identidades gerenciadas a VMs criadas em clusters, poderá remover o seguinte de actions:
"Microsoft.Authorization/*/read",
"Microsoft.Authorization/roleAssignments/*",
"Microsoft.Authorization/roleDefinitions/*",
Advertência
Versões futuras do CycleCloud exigirão a capacidade de atribuir identidades gerenciadas a VMs, portanto, remover essas permissões não é recomendado.
Creating the Role
A role can be created from the role definitions via the Azure CLI . Use this role to create a role definition within the Azure Tenant. Once the role exists in the tenant, assign the role to an identity with proper scope.
Abaixo está o fluxo básico usando a CLI do Azure.
# Create a custom role definition
az role definition create --role-definition role.json
# Create user identity
az identity create --name <name>
# Assign the custom role to the identity with proper scope
az role assignment create --role <CycleCloudRole> --assignee-object-id <identity-id> --scope <subscription>
Now the custom role is assigned and scoped to the identity and can be used with a VM.
Atribuindo funções a VMs de cluster com identidade gerenciada
É comum que os nós de cluster exijam acesso aos Recursos do Azure. Por exemplo, muitos clusters exigem acesso ao Armazenamento do Azure, ao Cofre da Chave ou aos Registros de Contêiner do Azure para executar sua carga de trabalho. It is strongly recommended to pass the access credentials required using a User-Assigned Managed Identity rather than passing secrets/credentials to the node via cluster configuration.
User-Assigned Managed Identities may be configured on the cluster VMs using the Azure.Identities node property. The value of the Azure.Identities property is a comma-separated list of Managed Identity Resource ID strings:
[cluster sample]
...
[[node defaults]]
...
Azure.Identities = $ManagedServiceIdentity
...
[parameters Required Settings]
...
[[parameter ManagedServiceIdentity]]
ParameterType = Azure.ManagedIdentity
Label = MSI Identity
Description = The resource ID of the Managed Service Identity to apply to the nodes
...