Improve regulatory compliance
Microsoft Defender for Cloud helps you to meet regulatory compliance requirements by continuously assessing resources against compliance controls, and identifying issues that are blocking you from achieving a particular compliance certification.
In the Regulatory compliance dashboard, you manage and interact with compliance standards. You can see which compliance standards are assigned, turn standards on and off for Azure, AWS, and GCP, review the status of assessments against standards, and more.
Integration with Purview
Compliance data from Defender for Cloud now seamlessly integrates with Microsoft Purview Compliance Manager, allowing you to centrally assess and manage compliance across your organization's entire digital estate.
When you add any standard to your compliance dashboard (including compliance standards monitoring other clouds like AWS and GCP), the resource-level compliance data is automatically surfaced in Compliance Manager for the same standard.
Compliance Manager thus provides improvement actions and status across your cloud infrastructure and all other digital assets in this central tool. For more information, see multicloud support in Microsoft Purview Compliance Manager.
Before you start
- By default, when you enable Defender for Cloud on an Azure subscription, AWS account, or GCP plan, the MCSB plan is enabled.
- You can add more non-default compliance standards when at least one paid plan is enabled in Defender for Cloud.
- You must be signed in with an account that has reader access to the policy compliance data. The Reader role for the subscription has access to the policy compliance data, but the Security Reader role doesn't. At a minimum, you need to have Resource Policy Contributor and Security Admin roles assigned.
Assess regulatory compliance
The Regulatory compliance dashboard shows which compliance standards are enabled. It shows the controls within each standard, and security assessments for those controls. The status of these assessments reflects your compliance with the standard.
The dashboard helps you to focus on gaps in standards, and to monitor compliance over time.
In the Defender for Cloud portal, open the Regulatory compliance page.
Use the dashboard in accordance with the numbered items in the image.
- (1). Select a compliance standard to see a list of all controls for that standard.
- (2). View the subscriptions on which the compliance standard is applied.
- (3). Select and expand a control to view the assessments associated with it. Select an assessment to view the associated resources, and possible remediation actions.
- (4). Select Control details to view the Overview, Your Actions, and Microsoft Actions tabs.
- (5). In Your Actions, you can see the automated and manual assessments associated with the control.
- (6). Automated assessments show the number of failed resources and resource types, and link you directly to the remediation information.
- (7). Manual assessments can be manually attested, and evidence can be linked to demonstrate compliance.
Investigate issues
You can use information in the dashboard to investigate issues that might affect compliance with the standard.
In the Defender for Cloud portal, open Regulatory compliance.
Select a regulatory compliance standard, and select a compliance control to expand it.
Select Control details.
- Select Overview to see the specific information about the Control you selected.
- Select Your Actions to see a detailed view of automated and manual actions you need to take to improve your compliance posture.
- Select Microsoft Actions to see all the actions Microsoft took to ensure compliance with the selected standard.
Under Your Actions, you can select a down arrow to view more details and resolve the recommendation for that resource.
For more information about how to apply recommendations, see Implementing security recommendations in Microsoft Defender for Cloud.
Note
Assessments run approximately every 12 hours, so you will see the impact on your compliance data only after the next run of the relevant assessment.
Remediate an automated assessment
The regulatory compliance has both automated and manual assessments that might need to be remediated. Using the information in the regulatory compliance dashboard, improve your compliance posture by resolving recommendations directly within the dashboard.
In the Defender for Cloud portal, open Regulatory compliance.
Select a regulatory compliance standard, and select a compliance control to expand it.
Select any of the failing assessments that appear in the dashboard to view the details for that recommendation. Each recommendation includes a set of remediation steps to resolve the issue.
Select a particular resource to view more details and resolve the recommendation for that resource.
For example, in the Azure CIS 1.1.0 standard, select the recommendation Disk encryption should be applied on virtual machines.In this example, when you select Take action from the recommendation details page, you arrive in the Azure Virtual Machine pages of the Azure portal, where you can enable encryption from the Security tab:
For more information about how to apply recommendations, see Implementing security recommendations in Microsoft Defender for Cloud.
After you take action to resolve recommendations, you'll see the result in the compliance dashboard report because your compliance score improves.
Assessments run approximately every 12 hours, so you'll see the impact on your compliance data only after the next run of the relevant assessment.
Remediate a manual assessment
The regulatory compliance has automated and manual assessments that might need to be remediated. Manual assessments are assessments that require input from the customer to remediate them.
In the Defender for Cloud portal, open Regulatory compliance.
Select a regulatory compliance standard, and select a compliance control to expand it.
Under the Manual attestation and evidence section, select an assessment.
Select the relevant subscriptions.
Select Attest.
Enter the relevant information and attach evidence for compliance.
Select Save.
Generate compliance status reports and certificates
To generate a PDF report with a summary of your current compliance status for a particular standard, select Download report.
The report provides a high-level summary of your compliance status for the selected standard based on Defender for Cloud assessments data. The report's organized according to the controls of that particular standard. The report can be shared with relevant stakeholders, and might provide evidence to internal and external auditors.
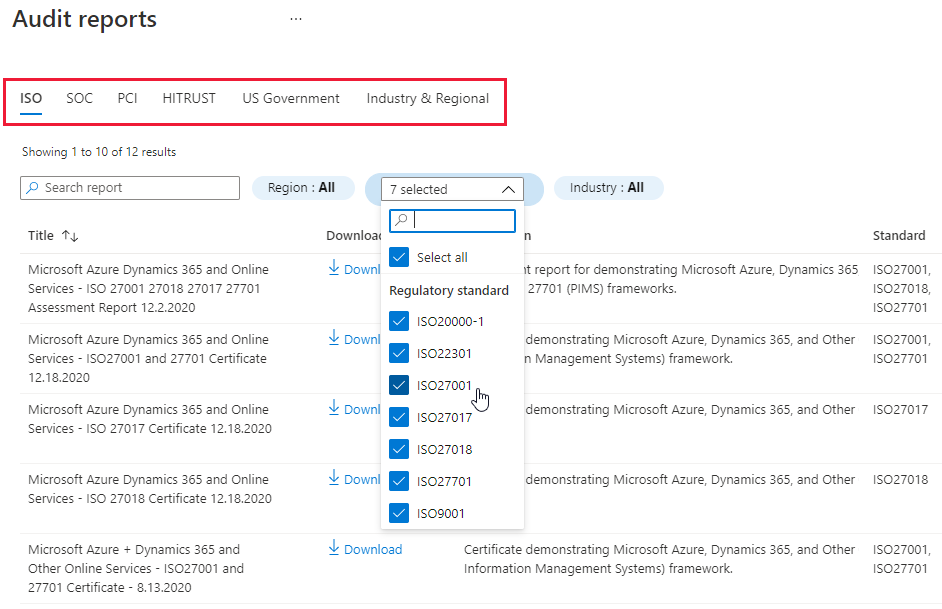
To download Azure and Dynamics certification reports for the standards applied to your subscriptions, use the Audit reports option.
Select the tab for the relevant reports types (PCI, SOC, ISO, and others) and use filters to find the specific reports you need:
For example, from the PCI tab you can download a ZIP file containing a digitally signed certificate demonstrating Microsoft Azure, Dynamics 365, and Other Online Services' compliance with ISO22301 framework, together with the necessary collateral to interpret and present the certificate.
When you download one of these certification reports, you're shown the following privacy notice:
By downloading this file, you are giving consent to Microsoft to store the current user and the selected subscriptions at the time of download. This data is used in order to notify you in case of changes or updates to the downloaded audit report. This data is used by Microsoft and the audit firms that produce the certification/reports only when notification is required.
Continuously export compliance status
If you want to track your compliance status with other monitoring tools in your environment, Defender for Cloud includes an export mechanism to make this straightforward. Configure continuous export to send select data to an Azure Event Hubs or a Log Analytics workspace. Learn more in continuously export Defender for Cloud data.
Use continuous export data to an Azure Event Hubs or a Log Analytics workspace:
Export all regulatory compliance data in a continuous stream:
Export weekly snapshots of your regulatory compliance data:
Tip
You can also manually export reports about a single point in time directly from the regulatory compliance dashboard. Generate these PDF/CSV reports or Azure and Dynamics certification reports using the Download report or Audit reports toolbar options.
Trigger a workflow when assessments change
Defender for Cloud's workflow automation feature can trigger Logic Apps whenever one of your regulatory compliance assessments changes state.
For example, you might want Defender for Cloud to email a specific user when a compliance assessment fails. You need to first create the logic app (using Azure Logic Apps) and then set up the trigger in a new workflow automation as explained in Automate responses to Defender for Cloud triggers.
Next steps
To learn more, see these related pages:
- Customize the set of standards in your regulatory compliance dashboard - Learn how to select which standards appear in your regulatory compliance dashboard.
- Managing security recommendations in Defender for Cloud - Learn how to use recommendations in Defender for Cloud to help protect your multicloud resources.
- Check out common questions about regulatory compliance.