Integrate Azure Activity logs and Azure Security Center Alerts over Syslog to QRadar
NOTE:
This blog post is outdated and some of the steps may not work correctly. If you have problems, please let us know at the Azure Log Integration forum.
With the first release of IBM QRadar's DSM for Azure Activity logs, you can now integrate your Azure logs to QRadar SIEM (Security Information and Event Management) and see it categorized correctly in QRadar.
By following the steps outlined here, you will be able to integrate the following logs to QRadar
- Azure Activity logs
- Azure Security Center Alerts
At this time there are about 1400 events from Azure Activity logs that will successfully map to categorized events in QRadar.
Before continuing, please review the topic at Azure log integration. It covers the high level architecture of the integration.
Step 1 - Install the Azure DSM released by IBM here: IBM QRadar 7.2 download
Step 2 - Uninstall any previous version of Azure log integration
If you have any previous version of Azure log integration installed, you will need to uninstall it first. Uninstalling it will remove all sources that are registered.
Steps to Uninstall –
- Open the command prompt as administrator and cd into c:\Program Files\Microsoft Azure Log Integration.
- Run the command
Azlog removeazureid
3. In Control Panel -->Add remove programs --> Microsoft Azure log integration --> uninstall
Install Azure log integration
- Download Azure log integration from the Microsoft Download Center and follow the install instructions
- Open command prompt as administration and cd into "c:\Program Files\Microsoft Azure Log Integration"
- Run “azlog.exe powershell”. This will open a PowerShell window
- In the PowerShell window, run the following to set up integration of Azure logs using syslog to the QRadar SIEM instance
Add-AzLogEventDestination -Name QRadarConsole1 -SyslogServer 10.0.0.5 -SyslogFormat LEEF
Name is a friendly name for the Destination
SyslogServer is the IP address of the QRadar console (you can specify Syslog Port if necessary).
- Run the command to create an Azure AD credential to use for the Azure log integration service
.\azlog.exe createazureid
- Run the command to authorize the Azure log integration credential to be able to read Azure logs
.\azlog authorize <SubscriptionID>
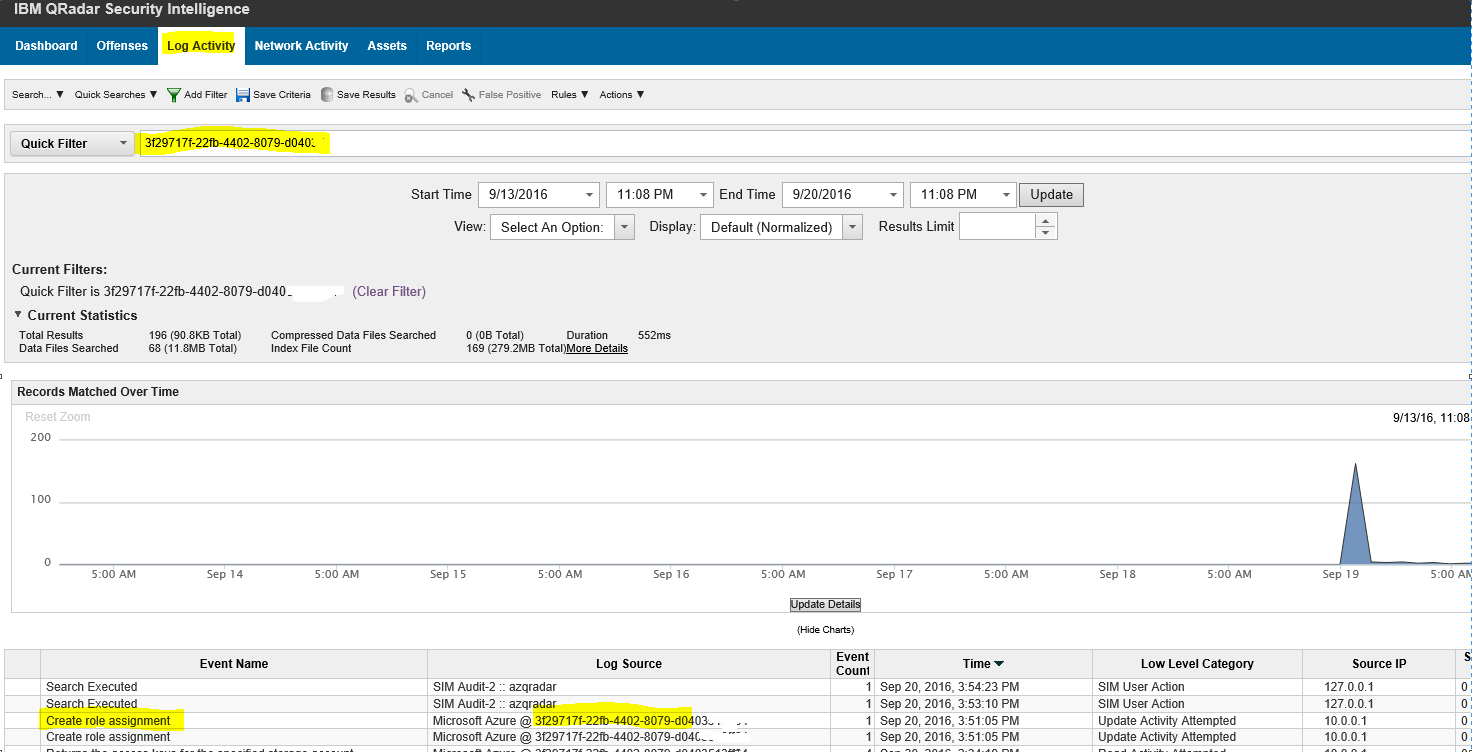
- Once Azure log integration starts sending logs to the QRadar SIEM instance, QRadar will autodiscover the source. You can verify the Log Activity tab on your QRadar console. Provide the SubscriptionID in the Quick filter or if you want to search across all subscriptions, provide ‘azure’ as the text in quick filter. Note that only 200 events are currently categorized