Special Command: Using s to Explore The Memory
Very often I found myself scanning the stack or the entire virtual memory for the process to find information that may help me.
This information may be strings, DWORDS, bytes, chars, etc…
To accomplish this you should use the s command.
Here I exemplify how you can use it to scan the memory for specific information.
These are some possible variations:
s –sa initialAddress finalAddress ß Dump all ASCII strings
s –u initialAddress finalAddress “string” ß Dump all Unicode strings that matches
s –[1]a initialAddress finalAddress “stringToSearchFor” ß Gets just the address where the strings that match the argument are located
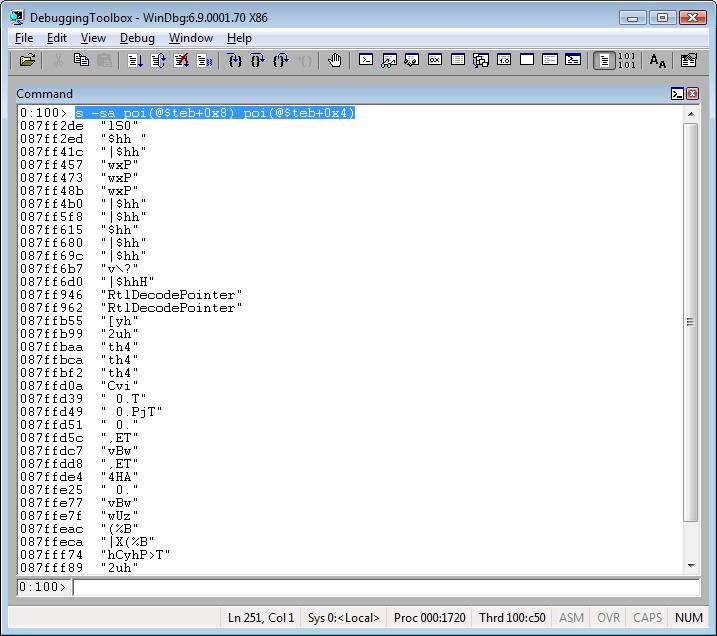
Displaying all ASCII strings from the current call stack:
s -sa poi(@$teb+0x8) poi(@$teb+0x4)
Displaying all UNICODE strings from the current call stack:
s -su poi(@$teb+0x8) poi(@$teb+0x4)
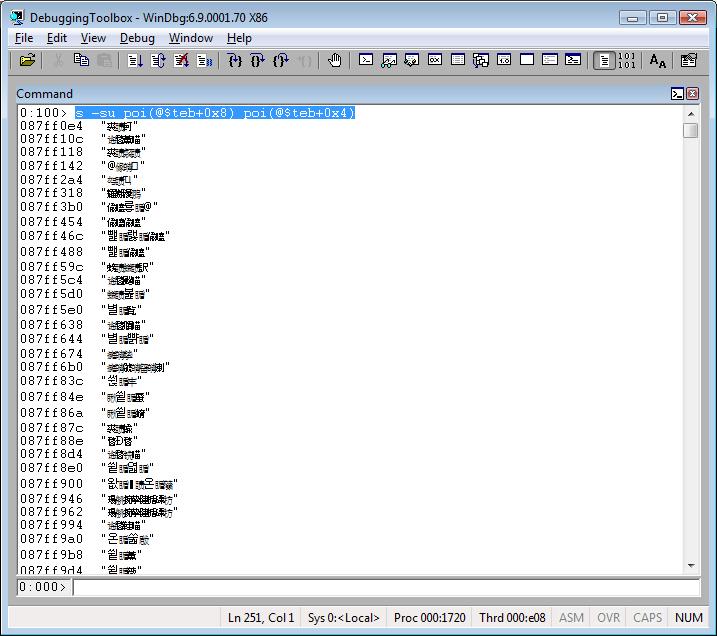
Just garbage, that's why the characters above are not readable.
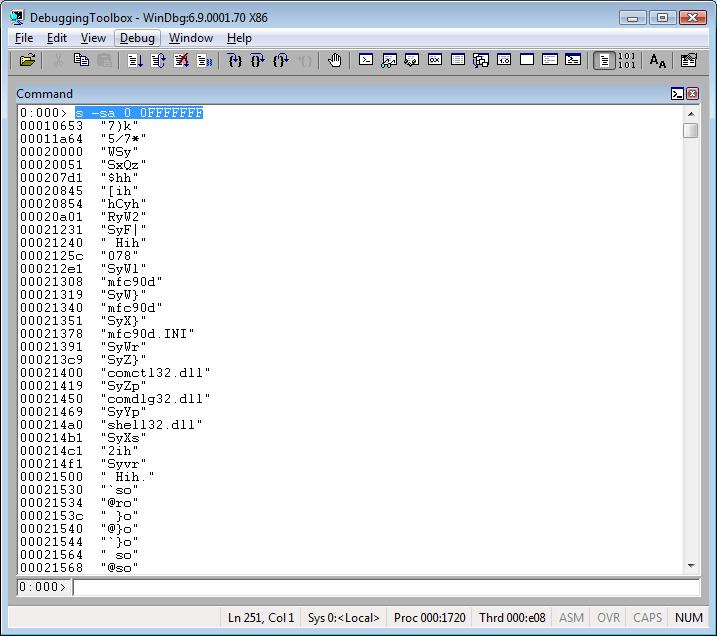
Displaying all occurrences ASCII strings that appear within the process virtual memory:
s –sa 0 0FFFFFFF
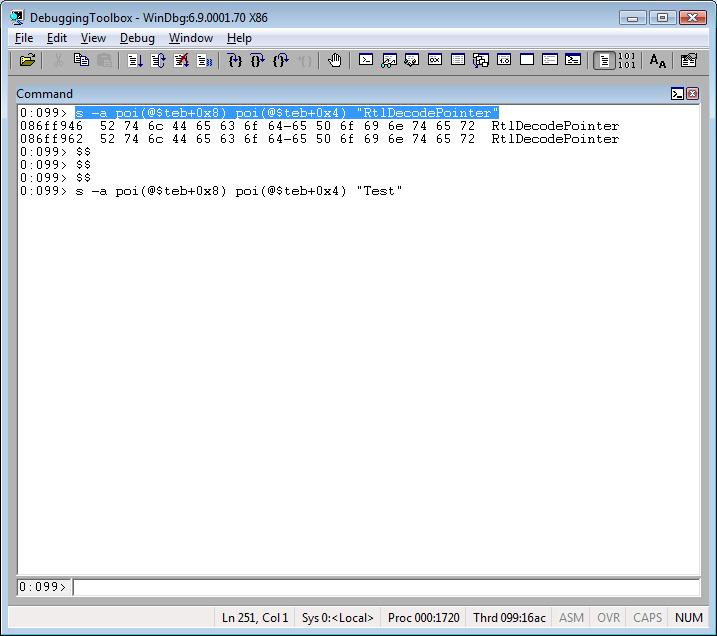
Searching for a specific ASCII string in the current call stack:
s -a poi(@$teb+0x8) poi(@$teb+0x4) "RtlDecodePointer"
s -a poi(@$teb+0x8) poi(@$teb+0x4) "Test"
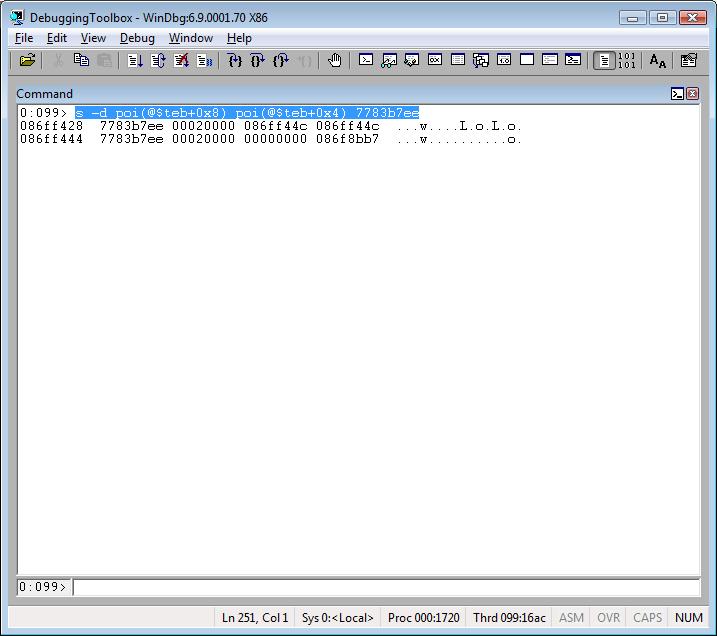
Searching for a specific DWORD in the current call stack:
s -d poi(@$teb+0x8) poi(@$teb+0x4) 7783b7ee
Tip: Sometimes you need to use the addresses returned from the s command. For example, you may want to use a loop that scans the returned addresses.
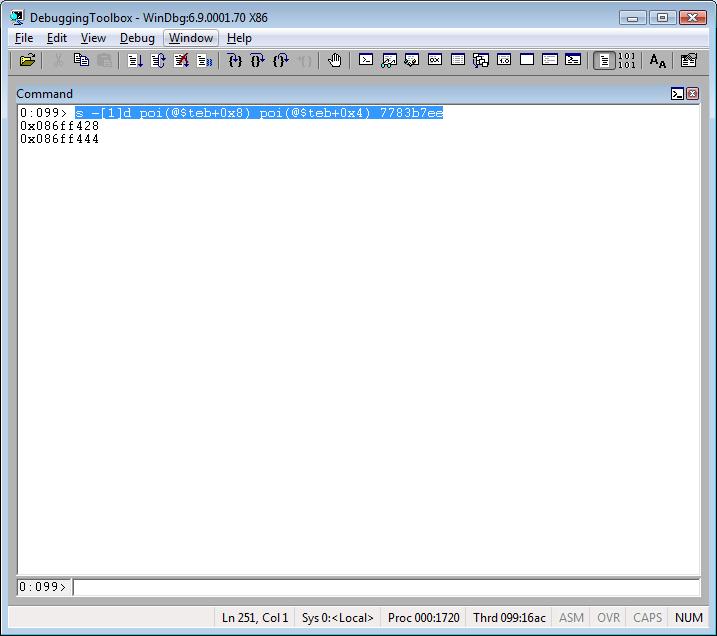
I’ll talk about loops in a future article; thus, this is just the command to return the addresses:
s -[1]d poi(@$teb+0x8) poi(@$teb+0x4) 7783b7ee
s -[1]a poi(@$teb+0x8) poi(@$teb+0x4) "RtlDecodePointer"
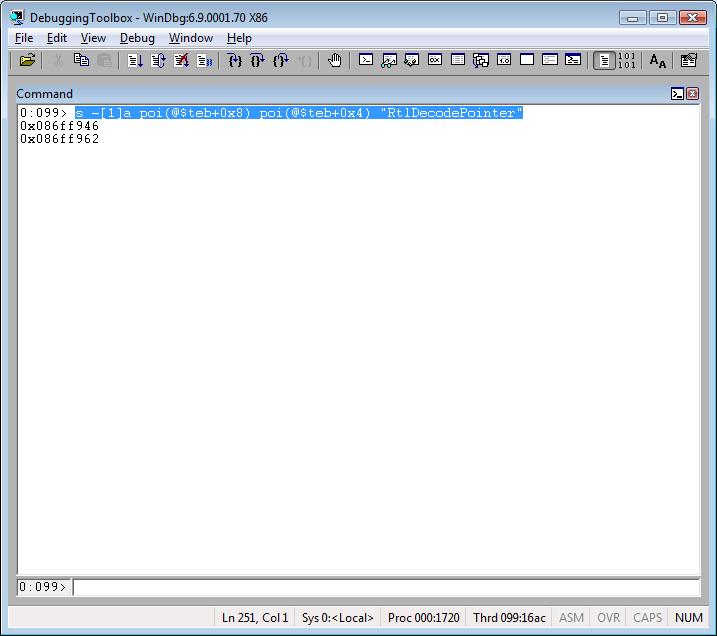
Notice the –[1] . This is used to return only the addresses that match the query.
Here you can see scripts that may be using the s command.
Comments
- Anonymous
March 11, 2008
PingBack from http://msdnrss.thecoderblogs.com/2008/03/11/special-command-using-s-to-explore-the-memory/