Identifying Failed Logon Attempts That Are Causing Account Lockouts in Threat Management Gateway 2010
In one of my previous posts entitled “ISA Server or Forefront TMG is Locking my Accounts Out” I wrote about the frustration some companies experience with account lockouts. In almost all cases, the cause for the account lockouts is that invalid user/password combinations have been saved on devices such as phones, tablets, or even on proxy aware programs. Inevitably the domain password policy requires the password to be changed but there are situations where it is not changed everywhere and this leads to pain for the administrators.
My advice when this happens was to tweak the internal domain password policies to the point where the lockouts were no longer happening or are greatly reduced. In some companies this is not possible due to stricter security guidelines or political pressure from management. I have talked to quite a few TMG administrators that would like a way to track the failed logon attempts and try to identify the source/devices. Unfortunately, prior to a fix in Service Pack 2 for Forefront TMG 2010, the failed logon attempts were always logged as “anonymous”.
In Service Pack 2 for TMG, a fix was included that will show you the username that was attempted for the failed logon. The fix is not enabled by default.
You can find the download for Service Pack 2 here.
You can find the information for the fix and how to enable it here.
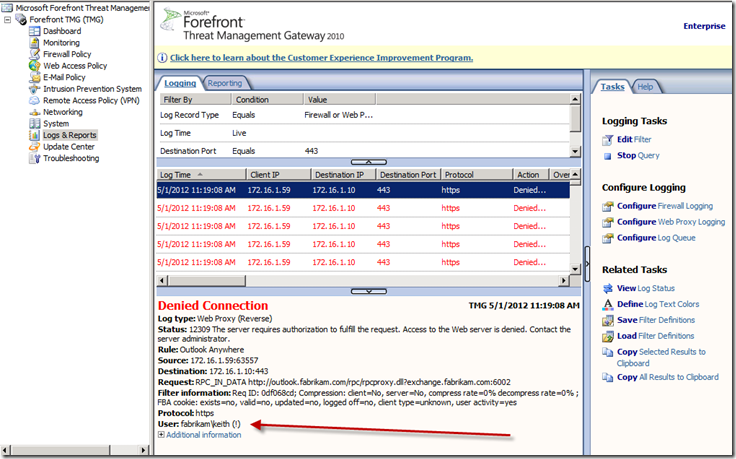
After you install SP2 and enable the fix you will now be able to identify the username that was attempted. This will show up in the Logging on Forefront TMG 2010 (See Figure 1). The attempted username shows up in the format domain\username (!)
The “(!)” symbol that is appended to the entry distinguishes it as being a failed attempt.
Fig. 1
Is this new information going to be helpful? Well, it depends. For cases where someone has bad credentials on a proxy aware application and are internal to the organization, I think this will be very helpful. It will identify the IP address of the computer where this is coming from. If the device is external to the company it will be less helpful. It’s often very hard to track devices such as phones that can get any random IP address. Even in cases where someone is at home on their own network, very few people know the IP address that has been given to network devices that connects them to the Internet. Since the attempts are now being logged you can approach the end user whose credentials are being used and ask them which device they were using at a specific time. At any rate, the new information is infinitely more helpful than merely being logged as “Anonymous”.
Conclusion
In this article I talked about a new feature that can be enabled to help identify failed attempts to authenticate through Forefront Threat Management Gateway 2010. I also talked about situations where this may be helpful to administrators. I am still of the opinion that account lockouts need to be addressed by tweaking your domain password policies but I am confident that this feature will be useful to organizations experiencing limited problems with lockouts.