Implement Microsoft Purview's default DLP policies
Before an organization even creates its first Microsoft Purview Data Loss Prevention (DLP) policy, DLP helps to protect its sensitive information. It does so with two default DLP policies: Default policy for devices and Default policy for Teams.
Default policy for devices
This default DLP policy notifies the organization when a user shares email or documents containing sensitive information with someone outside the organization. Microsoft Purview displays this recommendation in a tile on the Home page of the Microsoft Purview compliance portal (see the following screenshot). If you don't see the recommendation at first, try selecting +More at the bottom of the tile.
This tile enables an organization to quickly view when and how much sensitive information the user shared. It also provides an option to refine the default DLP policy in just a few selections. This policy is fully customizable, the same as any DLP policy that you create yourself from scratch. You can also turn off or delete the policy, so that your users no longer receive policy tips or email notifications.
This default policy detects when a user shares Exchange, SharePoint, or OneDrive content containing at least one of the following sensitive information types with people outside the organization:
- Credit Card Number
- Content containing source code (as matched by Microsoft's Source Code trainable classifier)
- Content matching Microsoft's U.S. HIPAA Enhanced template
- Content containing the organization's intellectual property (as matched by Microsoft's trainable classifiers related to IP, Project Documents, Mergers and Acquisitions files, Software Product development files, IT Infrastructure and Network Security documents, and Strategic planning documents)
Default policy for Teams
Microsoft extended the Microsoft Purview DLP capabilities to include Microsoft Teams chat and channel messages, including private channel messages. This capability includes a default DLP policy for Microsoft Teams for first-time customers to the Microsoft Purview compliance portal.
This default DLP policy tracks sensitive information shared internally and externally to the organization. This policy is on by default for all users of the tenant. It doesn't generate any policy tips for end users. However, it does generate an Alert event and also triggers a low severity email to an administrator, who you must add in the policy. Administrators can view the activities and edit the policy's details in the Microsoft Purview compliance portal.
To edit the default policy for better performance or to delete it, just use an account with DLP Compliance Management permissions.
View the report and refine the Default policy for devices
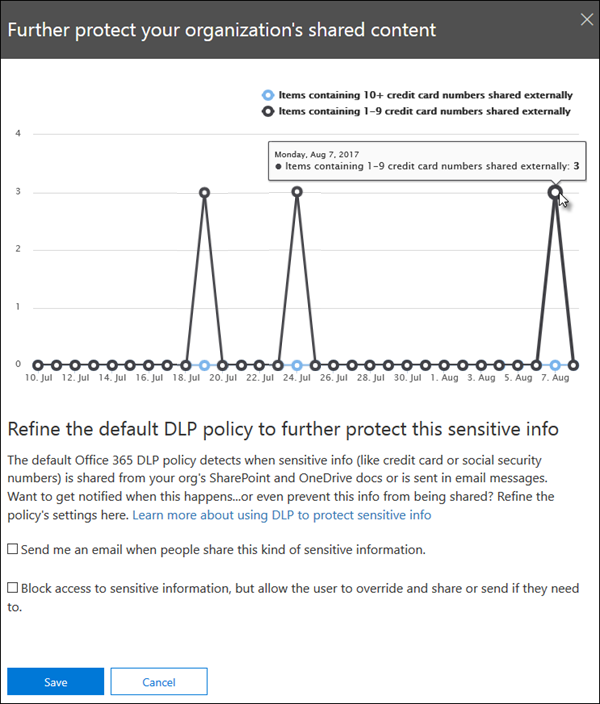
As mentioned previously, the Default policy for devices notifies an organization when a user shares email or documents containing sensitive information with someone outside the company**.** It displays this message in a tile that appears on the Home page of the Microsoft Purview compliance portal. In this tile, you can choose the Refine DLP policy option to display a detailed report of the activity. The report shows when users shared content containing sensitive information in the past 30 days, and how much content they shared.
Note
Rule matches can take up to 48 hours to show up in the tile.
To help protect the sensitive information, the Default policy for devices:
- Detects when users shared with people outside the organization any content in Exchange, SharePoint, and OneDrive that contained at least one piece of sensitive information.
- Shows a policy tip and sends an email notification to users when they attempt to share this sensitive information with people outside the organization. For more information on these options, see Send email notifications and show policy tips for DLP policies.
- Generates detailed activity reports. They enable an organization to track things like who shared the content with people outside the organization and when they did it. You can use the DLP reports and audit log data (where Activity = DLP) to see this information.
To quickly refine the Default policy for devices, you can choose to have it:
- Send the enterprise admin an incident report email when users share this sensitive information with people outside the organization.
- Add other users to the email incident report.
- Block access to the content containing the sensitive information but allow the user to override and share or send if they need to.
Additional reading. For more information on incident reports or restricting access, see Data loss prevention reference.
If you want to change these options later, you can edit the default DLP policy at any time - see the next section.
The Default policy for devices appears on the Policies page in the Microsoft Purview compliance portal, under the Data loss prevention group.
This policy is fully customizable, just like any DLP policy that you create yourself from scratch. You can also turn off or delete the policy, so that users no longer receive policy tips or email notifications.
The Further protect shared content widget
A Further protect shared content widget may appear in the "Recommended for you" tile. This widget only appears when:
- There are no data loss prevention policies in the Microsoft Purview compliance portal or Exchange admin center. This widget helps organizations get started with DLP. As such, it doesn't appear if you already have DLP policies.
- Users shared content containing at least one piece of sensitive information with someone outside your organization in the past 30 days.
Note
Rule matches can take up to 48 hours to be available to the widget. As such, after the default DLP policy detects someone sharing sensitive information externally, it may take up to two days for the recommendation to appear.
After you use the widget to refine the default DLP policy, the widget disappears from the Home page.