Sistem tarafından yönetilen anahtar sekmesiyle Active Directory kimlik doğrulamasında Azure Arc tarafından etkinleştirilen SQL Server - önkoşullar
Bu belgede, Active Directory (AD) kimlik doğrulamasıyla Azure Arc özellikli veri hizmetlerini dağıtmaya hazırlanma adımları açıklanmaktadır. Özellikle makalede, Kubernetes kaynaklarının dağıtımından önce yapılandırmanız gereken Active Directory nesneleri açıklanmaktadır.
Giriş bölümünde iki farklı tümleştirme modu açıklanmaktadır:
- Sistem tarafından yönetilen tuş sekmesi modu, sistemin her SQL Yönetilen Örneği için AD hesaplarını oluşturmasına ve yönetmesine olanak tanır.
- Müşteri tarafından yönetilen anahtar sekmesi modu, her SQL Yönetilen Örneği için AD hesaplarını oluşturmanıza ve yönetmenize olanak tanır.
gereksinimler ve öneriler iki tümleştirme modu için farklıdır.
| Active Directory Nesnesi | Müşteri tarafından yönetilen anahtar sekmesi | Sistem tarafından yönetilen tuş sekmesi |
|---|---|---|
| Kuruluş birimi (OU) | Önerilir | Zorunlu |
| Active Directory Bağlayıcısı için Active Directory etki alanı hizmet hesabı (DSA) | Gerekli değil | Zorunlu |
| SQL Yönetilen Örneği için Active Directory hesabı | Yönetilen her örnek için oluşturuldu | Sistem, yönetilen her örnek için AD hesabı oluşturur |
DSA hesabı - sistem tarafından yönetilen tuş sekmesi modu
Active Directory'de gerekli tüm nesneleri otomatik olarak oluşturabilmek için AD Bağlayıcısı'nın bir etki alanı hizmet hesabına (DSA) ihtiyacı vardır. DSA, sağlanan kuruluş birimi (OU) içindeki kullanıcı hesaplarını oluşturmak, yönetmek ve silmek için belirli izinlere sahip bir Active Directory hesabıdır. Bu makalede, bu Active Directory hesabının izninin nasıl yapılandırılır açıklanmaktadır. Örnekler, bu makalede örnek olarak DSA hesabını arcdsa çağırır.
Otomatik olarak oluşturulan Active Directory nesneleri
Arc özellikli SQL Yönetilen Örneği dağıtımı, otomatik olarak sistem tarafından yönetilen anahtar sekmesi modunda hesaplar oluşturur. Hesapların her biri bir SQL Yönetilen Örneği temsil eder ve SQL ömrü boyunca sistem tarafından yönetilir. Bu hesaplar, her SQL için gereken Hizmet Asıl Adları'na (SPN) sahip olur.
Aşağıdaki adımlarda zaten bir Active Directory etki alanı denetleyiciniz olduğu varsayılır. Etki alanı denetleyiciniz yoksa, aşağıdaki kılavuz yararlı olabilecek adımları içerir.
Active Directory nesneleri oluşturma
AD kimlik doğrulaması ile Arc özellikli bir SQL Yönetilen Örneği dağıtmadan önce aşağıdakileri yapın:
- Arc özellikli SQL Yönetilen Örneği ilgili tüm AD nesneleri için bir kuruluş birimi (OU) oluşturun. Alternatif olarak, dağıtımdan sonra mevcut bir OU'yu seçebilirsiniz.
- AD Bağlayıcısı için bir AD hesabı oluşturun veya var olan bir hesabı kullanın ve bu hesaba önceki adımda oluşturulan OU üzerinde doğru izinleri sağlayın.
OU oluşturma
Sistem tarafından yönetilen tuş sekmesi modu, belirlenmiş bir OU gerektirir. Müşteri tarafından yönetilen anahtar sekmesi modu için bir OU önerilir.
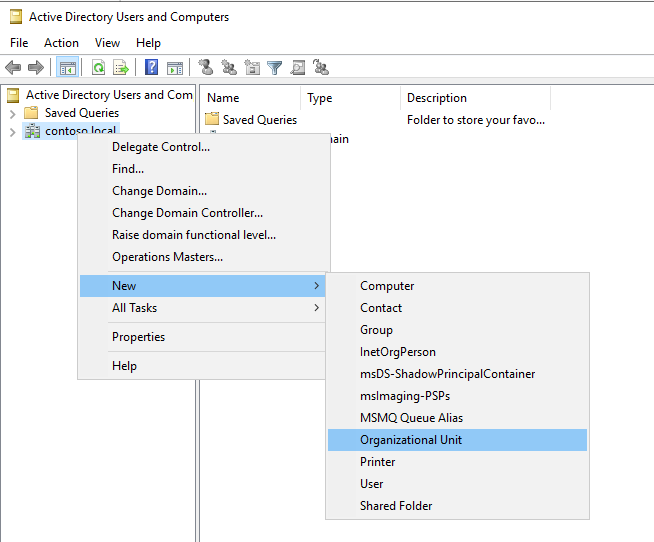
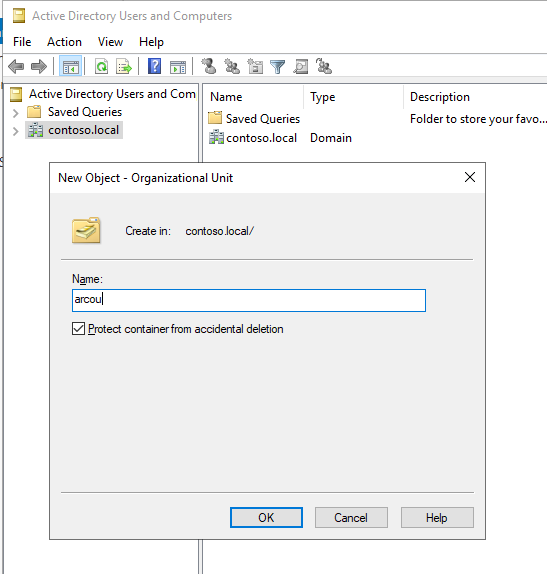
Etki alanı denetleyicisinde Active Directory Kullanıcıları ve Bilgisayarları açın. Sol panelde, OU'nuzu oluşturmak istediğiniz dizine sağ tıklayın ve Yeni>Kuruluş Birimi'ni seçin, ardından sihirbazdan gelen istemleri izleyerek OU'yu oluşturun. Alternatif olarak, PowerShell ile bir OU oluşturabilirsiniz:
New-ADOrganizationalUnit -Name "<name>" -Path "<Distinguished name of the directory you wish to create the OU in>"
Bu makaledeki örneklerde OU adı kullanılır arcou .
Etki alanı hizmet hesabını (DSA) oluşturma
Sistem tarafından yönetilen anahtar sekmesi modu için bir AD etki alanı hizmet hesabına ihtiyacınız vardır.
Etki alanı hizmet hesabı olarak kullanacağınız Active Directory kullanıcısını oluşturun. Bu hesap belirli izinler gerektirir. Mevcut bir Active Directory hesabınız olduğundan emin olun veya Arc özellikli SQL Yönetilen Örneği gerekli nesneleri ayarlamak için kullanabileceği yeni bir hesap oluşturun.
AD'de yeni kullanıcı oluşturmak için etki alanına veya OU'ya sağ tıklayıp Yeni Kullanıcı'yı> seçebilirsiniz:
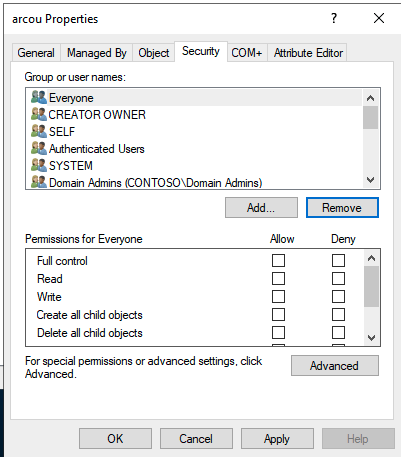
Bu hesap, bu makalede arcdsa olarak adlandırılır.
DSA için izinleri ayarlama
Sistem tarafından yönetilen tuş sekmesi modu için DSA izinlerini ayarlamanız gerekir.
İster DSA için yeni bir hesap oluşturdunuz ister mevcut bir Active Directory kullanıcı hesabını kullanıyor olun, hesabın sahip olması gereken belirli izinler vardır. DSA'nın OU'da kullanıcı, grup ve bilgisayar hesabı oluşturabilmesi gerekir. Aşağıdaki adımlarda Arc özellikli SQL Yönetilen Örneği etki alanı hizmet hesabı adı şeklindedirarcdsa.
Önemli
DSA için herhangi bir ad seçebilirsiniz, ancak AD Bağlayıcısı dağıtıldıktan sonra hesap adını değiştirmenizi önermeyiz.
Etki alanı denetleyicisinde Active Directory Kullanıcıları ve Bilgisayarları açın, Görünüm'e tıklayın, Gelişmiş Özellikler'i seçin
Sol panelde etki alanınıza gidin ve ardından
arcouOU'ya sağ tıklayın ve Özellikler'i seçin.
Not
OU'ya sağ tıklayıp Görünüm'ü seçerek Gelişmiş Özellikler'i seçtiğinizden emin olun
Güvenlik sekmesine gidin. Gelişmiş Özellikler'i seçin, OU'ya sağ tıklayın ve Görünüm'ü seçin.

Ekle... öğesini seçin ve arcdsa kullanıcısını ekleyin.
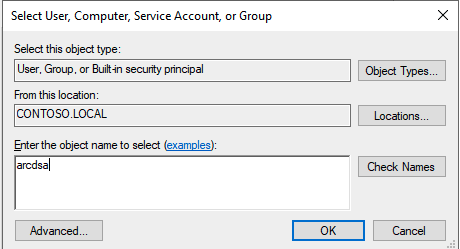
arcdsa kullanıcısını seçin ve tüm izinleri temizleyin, ardından Gelişmiş'i seçin.
Ekle'yi seçin
Sorumlu Seç'i seçin, arcdsa ekleyin ve Tamam'ı seçin.
Tür'i İzin Ver olarak ayarlayın.
Bu Nesneye ve tüm alt nesnelere Uygulanır'ı seçin.
Aşağı kaydırarak en alta gelin ve Tümünü temizle'yi seçin.
En üste geri kaydırın ve şunları seçin:
- Tüm özellikleri okuma
- Tüm özellikleri yazma
- Kullanıcı nesneleri oluşturma
- Kullanıcı nesnelerini silme
Tamam'ı seçin.
Ekle'yi seçin.
Sorumlu Seç'i seçin, arcdsa ekleyin ve Tamam'ı seçin.
Tür'i İzin Ver olarak ayarlayın.
Alt Kullanıcı nesnelerine Uygulanır'ı seçin.
Aşağı kaydırarak en alta gelin ve Tümünü temizle'yi seçin.
En üste geri kaydırın ve Parolayı sıfırla'yı seçin.
Tamam'ı seçin.
- Açık iletişim kutularını kapatmak için iki kez daha Tamam'ı seçin.
İlgili içerik
- Müşteri tarafından yönetilen bir anahtar sekmesi Active Directory (AD) bağlayıcısı dağıtma
- Sistem tarafından yönetilen bir anahtar sekmesi Active Directory (AD) bağlayıcısı dağıtma
- Active Directory'de (AD) Azure Arc tarafından etkinleştirilen bir SQL Yönetilen Örneği dağıtma
- Active Directory kimlik doğrulamasını kullanarak Azure Arc tarafından etkinleştirilen SQL Yönetilen Örneği bağlanma