Troubleshoot Active Directory Federation Services Idp-initiated sign-on
The Active Directory Federation Services (AD FS) sign-on page can be used to check if authentication is working. This test is done by navigating to the page and signing in. Also, you can use the sign-in page to verify that all SAML 2.0 relying parties are listed.
Enable the Idp-initiated sign on page
By default, AD FS in Windows 2016 doesn't have the sign on page enabled. To enable the page, you can use the PowerShell command Set-AdfsProperties. Use the following procedure to enable the page:
Open Windows PowerShell.
Enter
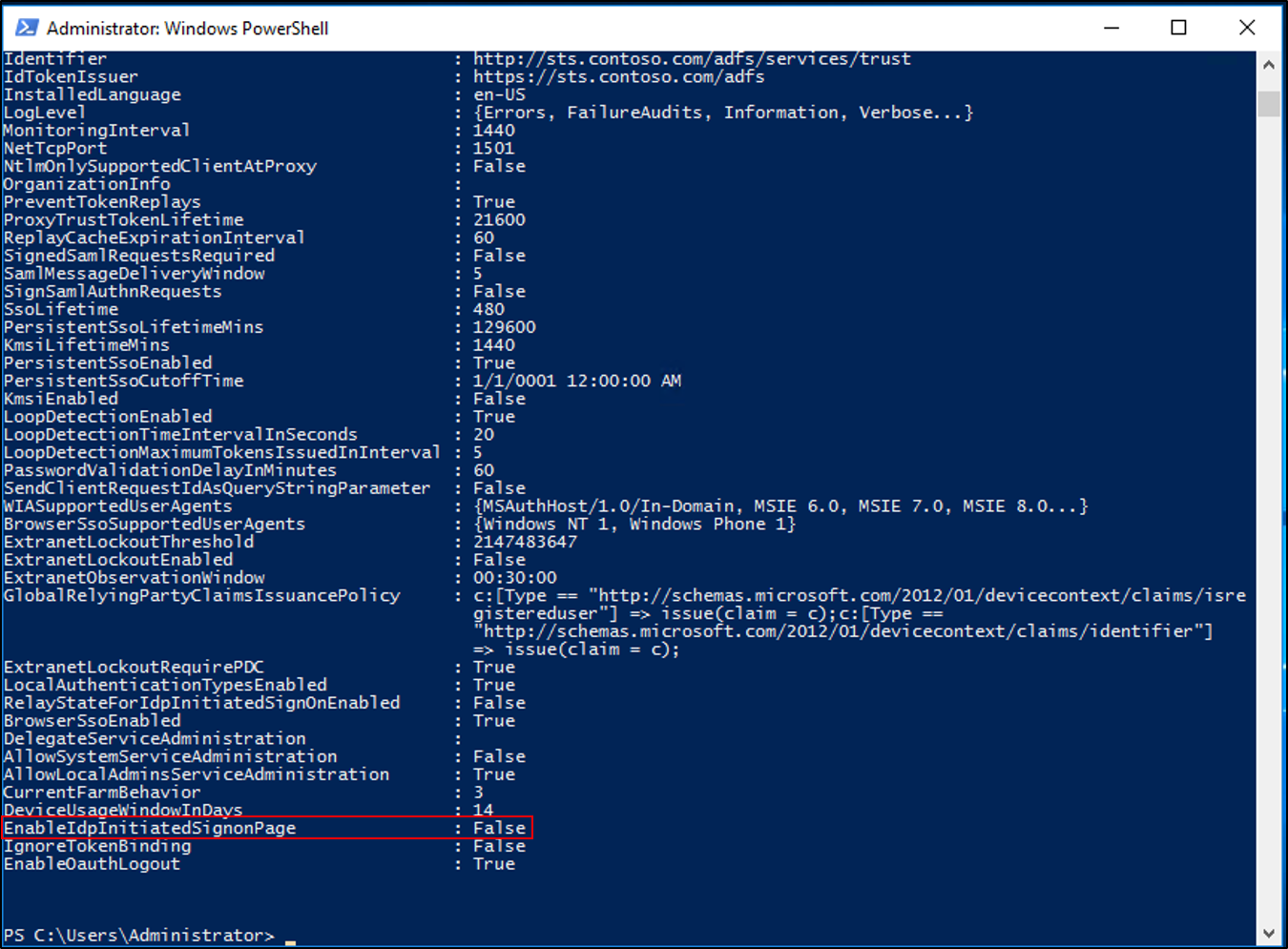
Get-AdfsPropertiesand hit enter.Verify the EnableIdpInitiatedSignonPage property is set to false.
In PowerShell, enter
Set-AdfsProperties -EnableIdpInitiatedSignonPage $true.PowerShell doesn't provide a confirmation for the
Set-AdfsPropertiescommand. To confirm the EnableIdpInitatedSignonPage property is set to true, enter theGet-AdfsPropertiescommand again and check the value for the property.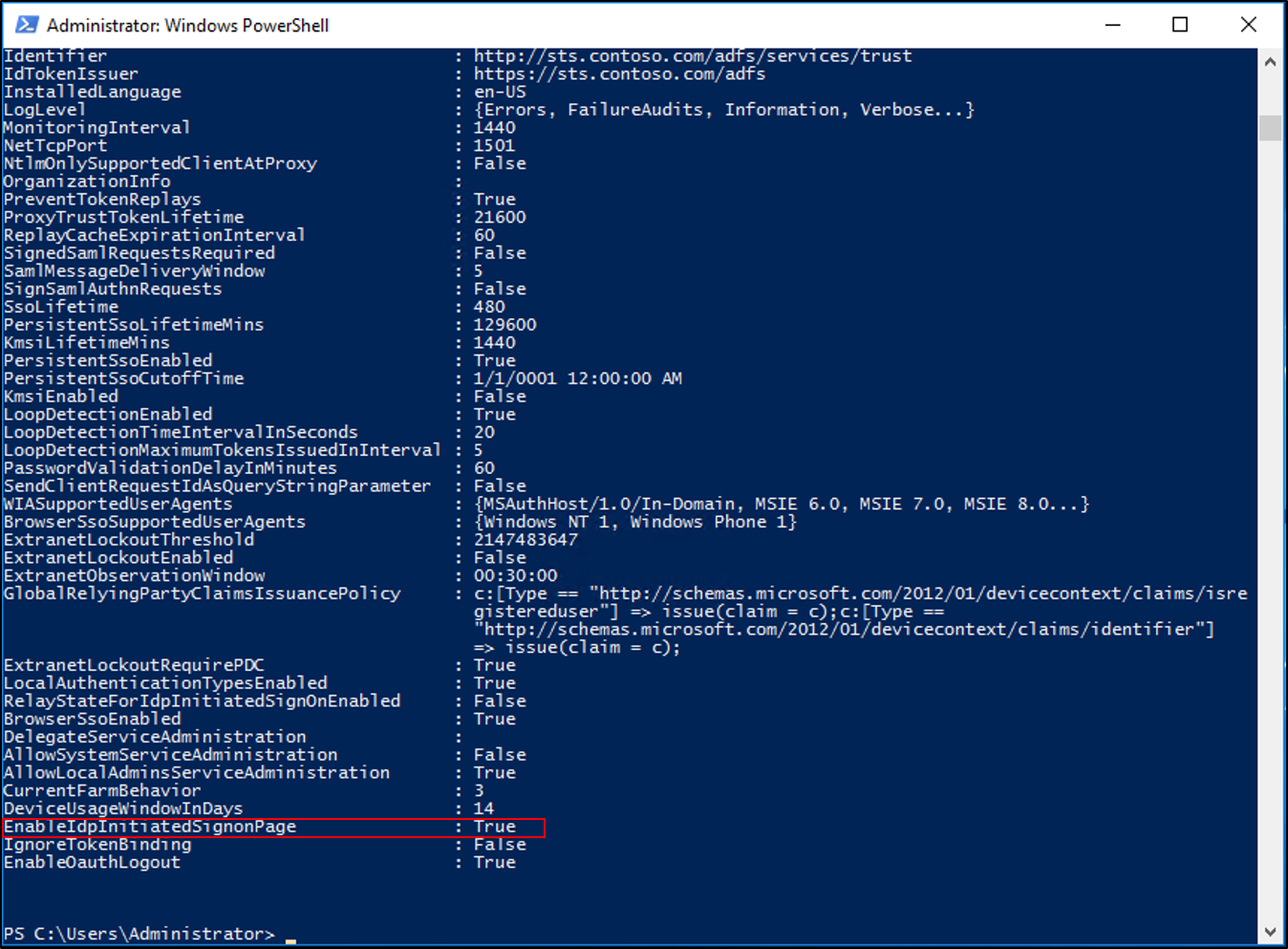
Test authentication
Use the following procedure to test AD FS authentication with the Idp-initiated sign on page.
Open a web browser, and go to the Idp sign on page. Your URL might look like
https://sts.contoso.com/adfs/ls/idpinitiatedsignon.aspx.You should be prompted to sign-in. Enter your credentials.
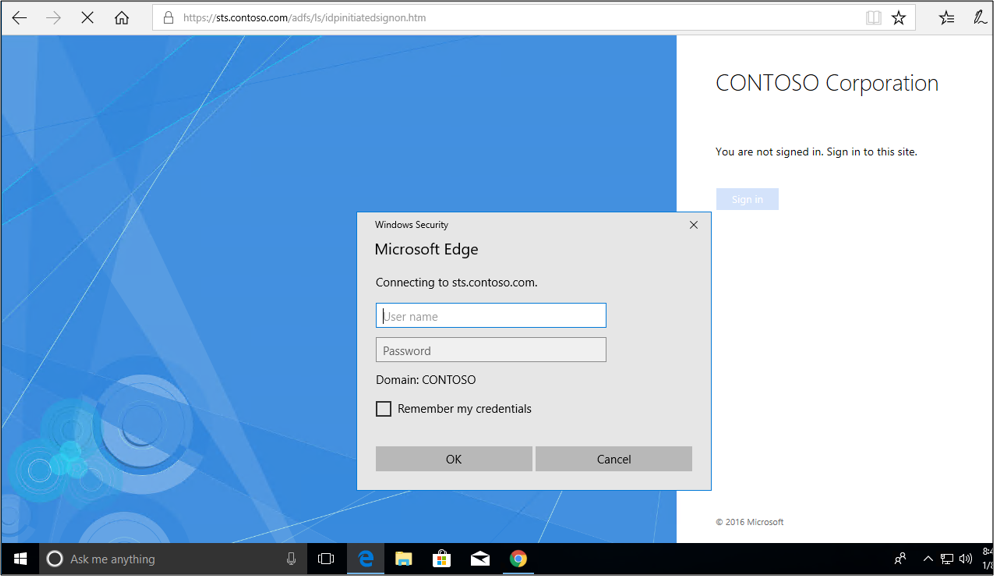
If the process succeeds, you’re signed in.
Test authentication with seamless sign in
You can test the seamless sign-in experience by making sure the URL for your AD FS servers is added to the local intranet zone of your internet options. Use the following procedure:
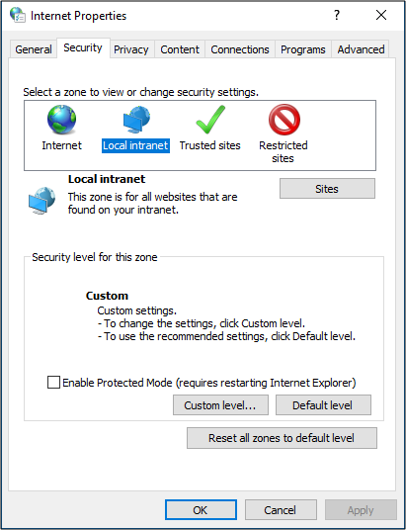
On a Windows 10 client, select Start and enter internet options and select Internet Options.
Select the Security tab, select Local intranet, and then select Sites.
Select Advanced.
Enter your URL and select Add. Select Close.
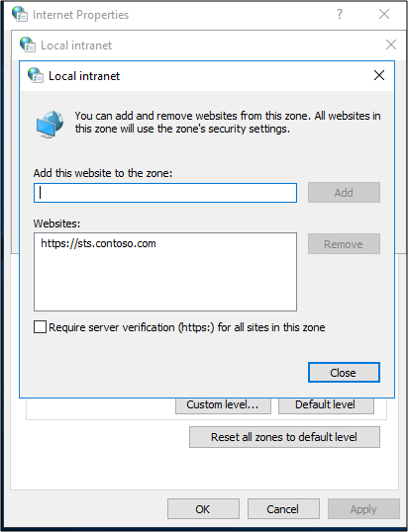
Select Ok. Then select Ok to close the internet options.
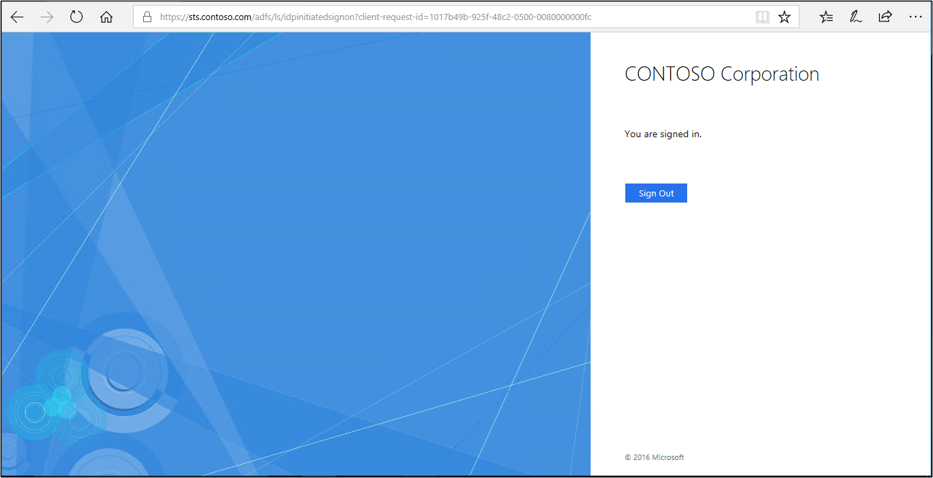
Open a web browser and go to the Idp sign on page. Your URL might look like
https://sts.contoso.com/adfs/ls/idpinitiatedsignon.aspx.Select the sign in button. You should automatically sign in and not be prompted for credentials.
Known Issues
The AD FS sign-on page can't be used to initiate a sign in with a claims provider trust that's configured with a WS-Federation passive endpoint only. Register a relying party such as ClaimsXRay to verify that a WS-Federation claims provider trust works as intended.