Policy CSP - DeviceInstallation
Tip
This CSP contains ADMX-backed policies which require a special SyncML format to enable or disable. You must specify the data type in the SyncML as <Format>chr</Format>. For details, see Understanding ADMX-backed policies.
The payload of the SyncML must be XML-encoded; for this XML encoding, there are a variety of online encoders that you can use. To avoid encoding the payload, you can use CDATA if your MDM supports it. For more information, see CDATA Sections.
AllowInstallationOfMatchingDeviceIDs
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 1809 [10.0.17763] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/AllowInstallationOfMatchingDeviceIDs
This policy setting allows you to specify a list of Plug and Play hardware IDs and compatible IDs for devices that Windows is allowed to install. This policy setting is intended to be used only when the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting is enabled, however it may also be used with the "Prevent installation of devices not described by other policy settings" policy setting for legacy policy definitions.
When this policy setting is enabled together with the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting, Windows is allowed to install or update any device whose Plug and Play hardware ID or compatible ID appears in the list you create, unless another policy setting at the same or higher layer in the hierarchy specifically prevents that installation, such as the following policy settings:
- Prevent installation of devices that match these device IDs
- Prevent installation of devices that match any of these device instance IDs.
If the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting isn't enabled with this policy setting, then any other policy settings specifically preventing installation will take precedence.
Note
The "Prevent installation of devices not described by other policy settings" policy setting has been replaced by the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting for supported target Windows 10 versions. It's recommended that you use the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting when possible.
Alternatively, if this policy setting is enabled together with the "Prevent installation of devices not described by other policy settings" policy setting, Windows is allowed to install or update any device whose Plug and Play hardware ID or compatible ID appears in the list you create, unless another policy setting specifically prevents that installation (for example, the "Prevent installation of devices that match any of these device IDs" policy setting, the "Prevent installation of devices for these device classes" policy setting, the "Prevent installation of devices that match any of these device instance IDs" policy setting, or the "Prevent installation of removable devices" policy setting).
If you enable this policy setting on a remote desktop server, the policy setting affects redirection of the specified devices from a remote desktop client to the remote desktop server.
If you disable or don't configure this policy setting, and no other policy setting describes the device, the "Prevent installation of devices not described by other policy settings" policy setting determines whether the device can be installed.
Peripherals can be specified by their hardware identity. For a list of common identifier structures, see Device Identifier Formats. Test the configuration prior to rolling it out to ensure it allows the devices expected. Ideally test various instances of the hardware. For example, test multiple USB keys rather than only one.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_IDs_Allow |
| Friendly Name | Allow installation of devices that match any of these device IDs |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | AllowDeviceIDs |
| ADMX File Name | DeviceInstallation.admx |
Example:
To enable this policy, use the following SyncML. This example allows Windows to install compatible devices with a device ID of USB\Composite or USB\Class_FF. To configure multiple classes, use  as a delimiter.
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/AllowInstallationOfMatchingDeviceIDs</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><Data id="DeviceInstall_IDs_Allow_List" value="1USB\Composite2USB\Class_FF"/></Data>
</Item>
</Replace>
</SyncBody>
</SyncML>
To verify that the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]
AllowInstallationOfMatchingDeviceInstanceIDs
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 2004 [10.0.19041] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/AllowInstallationOfMatchingDeviceInstanceIDs
This policy setting allows you to specify a list of Plug and Play device instance IDs for devices that Windows is allowed to install. This policy setting is intended to be used only when the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting is enabled, however it may also be used with the "Prevent installation of devices not described by other policy settings" policy setting for legacy policy definitions.
When this policy setting is enabled together with the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting, Windows is allowed to install or update any device whose Plug and Play device instance ID appears in the list you create, unless another policy setting at the same or higher layer in the hierarchy specifically prevents that installation, such as the following policy settings:
- Prevent installation of devices that match any of these device instance IDs.
If the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting isn't enabled with this policy setting, then any other policy settings specifically preventing installation will take precedence.
Note
The "Prevent installation of devices not described by other policy settings" policy setting has been replaced by the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting for supported target Windows 10 versions. It's recommended that you use the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting when possible.
Alternatively, if this policy setting is enabled together with the "Prevent installation of devices not described by other policy settings" policy setting, Windows is allowed to install or update any device whose Plug and Play device instance ID appears in the list you create, unless another policy setting specifically prevents that installation (for example, the "Prevent installation of devices that match any of these device IDs" policy setting, the "Prevent installation of devices for these device classes" policy setting, the "Prevent installation of devices that match any of these device instance IDs" policy setting, or the "Prevent installation of removable devices" policy setting).
If you enable this policy setting on a remote desktop server, the policy setting affects redirection of the specified devices from a remote desktop client to the remote desktop server.
If you disable or don't configure this policy setting, and no other policy setting describes the device, the "Prevent installation of devices not described by other policy settings" policy setting determines whether the device can be installed.
Peripherals can be specified by their device instance ID. Test the configuration prior to rolling it out to ensure it allows the devices expected. Ideally test various instances of the hardware. For example, test multiple USB keys rather than only one.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_Instance_IDs_Allow |
| Friendly Name | Allow installation of devices that match any of these device instance IDs |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | AllowInstanceIDs |
| ADMX File Name | DeviceInstallation.admx |
Example:
To enable this policy, use the following SyncML.
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/AllowInstallationOfMatchingDeviceInstanceIDs</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><Data id="DeviceInstall_Instance_IDs_Allow_List" value="1USB\VID_1F75&PID_0917\47802411805883"/></Data>
</Item>
</Replace>
</SyncBody>
</SyncML>
Verify:
To verify the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]
AllowInstallationOfMatchingDeviceSetupClasses
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 1809 [10.0.17763] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/AllowInstallationOfMatchingDeviceSetupClasses
This policy setting allows you to specify a list of device setup class globally unique identifiers (GUIDs) for driver packages that Windows is allowed to install. This policy setting is intended to be used only when the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting is enabled, however it may also be used with the "Prevent installation of devices not described by other policy settings" policy setting for legacy policy definitions.
When this policy setting is enabled together with the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting, Windows is allowed to install or update driver packages whose device setup class GUIDs appear in the list you create, unless another policy setting at the same or higher layer in the hierarchy specifically prevents that installation, such as the following policy settings:
- Prevent installation of devices for these device classes
- Prevent installation of devices that match these device IDs
- Prevent installation of devices that match any of these device instance IDs.
If the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting isn't enabled with this policy setting, then any other policy settings specifically preventing installation will take precedence.
Note
The "Prevent installation of devices not described by other policy settings" policy setting has been replaced by the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting for supported target Windows 10 versions. It's recommended that you use the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting when possible.
Alternatively, if this policy setting is enabled together with the "Prevent installation of devices not described by other policy settings" policy setting, Windows is allowed to install or update driver packages whose device setup class GUIDs appear in the list you create, unless another policy setting specifically prevents installation (for example, the "Prevent installation of devices that match these device IDs" policy setting, the "Prevent installation of devices for these device classes" policy setting, the "Prevent installation of devices that match any of these device instance IDs" policy setting, or the "Prevent installation of removable devices" policy setting).
If you enable this policy setting on a remote desktop server, the policy setting affects redirection of the specified devices from a remote desktop client to the remote desktop server.
If you disable or don't configure this policy setting, and no other policy setting describes the device, the "Prevent installation of devices not described by other policy settings" policy setting determines whether the device can be installed.
Peripherals can be specified by their hardware identity. For a list of common identifier structures, see Device Identifier Formats. Test the configuration prior to rolling it out to ensure it allows the devices expected. Ideally test various instances of the hardware. For example, test multiple USB keys rather than only one.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_Classes_Allow |
| Friendly Name | Allow installation of devices using drivers that match these device setup classes |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | AllowDeviceClasses |
| ADMX File Name | DeviceInstallation.admx |
Example:
To enable this policy, use the following SyncML. This example allows Windows to install:
- Floppy Disks, ClassGUID = {4d36e980-e325-11ce-bfc1-08002be10318}
- CD ROMs, ClassGUID = {4d36e965-e325-11ce-bfc1-08002be10318}
- Modems, ClassGUID = {4d36e96d-e325-11ce-bfc1-08002be10318}
Enclose the class GUID within curly brackets {}. To configure multiple classes, use  as a delimiter.
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/AllowInstallationOfMatchingDeviceSetupClasses</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><Data id="DeviceInstall_Classes_Allow_List" value="1{4d36e980-e325-11ce-bfc1-08002be10318}2{4d36e965-e325-11ce-bfc1-08002be10318}3{4d36e96d-e325-11ce-bfc1-08002be10318}"/></Data>
</Item>
</Replace>
</SyncBody>
</SyncML>
Verify:
To verify that the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]
EnableInstallationPolicyLayering
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ [10.0.20348.256] and later ✅ Windows 10, version 1809 with KB5005102 [10.0.17763.2145] and later ✅ Windows 10, version 1903 [10.0.18362.1714] and later ✅ Windows 10, version 2004 with KB5004296 [10.0.19041.1151] and later ✅ Windows 11, version 21H2 [10.0.22000] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/EnableInstallationPolicyLayering
This policy setting will change the evaluation order in which Allow and Prevent policy settings are applied when more than one install policy setting is applicable for a given device. Enable this policy setting to ensure that overlapping device match criteria is applied based on an established hierarchy where more specific match criteria supersedes less specific match criteria. The hierarchical order of evaluation for policy settings that specify device match criteria is as follows:
Device instance IDs > Device IDs > Device setup class > Removable devices.
Device instance IDs.
- Prevent installation of devices using drivers that match these device instance IDs
- Allow installation of devices using drivers that match these device instance IDs.
Device IDs.
- Prevent installation of devices using drivers that match these device IDs
- Allow installation of devices using drivers that match these device IDs.
Device setup class.
- Prevent installation of devices using drivers that match these device setup classes
- Allow installation of devices using drivers that match these device setup classes.
Removable devices.
- Prevent installation of removable devices.
Note
This policy setting provides more granular control than the "Prevent installation of devices not described by other policy settings" policy setting. If these conflicting policy settings are enabled at the same time, the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting will be enabled and the other policy setting will be ignored.
If you disable or don't configure this policy setting, the default evaluation is used. By default, all "Prevent installation.". policy settings have precedence over any other policy setting that allows Windows to install a device.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_Allow_Deny_Layered |
| Friendly Name | Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | AllowDenyLayered |
| ADMX File Name | DeviceInstallation.admx |
Example:
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/EnableInstallationPolicyLayering</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><Data id="AllowDenyLayered" value="1"/></Data>;
</Item>
</Replace>
</SyncBody>
</SyncML>
Verify:
To verify that the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]
You can also change the evaluation order of device installation policy settings by using a custom profile in Intune.

PreventDeviceMetadataFromNetwork
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 1809 [10.0.17763] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventDeviceMetadataFromNetwork
This policy setting allows you to prevent Windows from retrieving device metadata from the Internet.
If you enable this policy setting, Windows doesn't retrieve device metadata for installed devices from the Internet. This policy setting overrides the setting in the Device Installation Settings dialog box (Control Panel > System and Security > System > Advanced System Settings > Hardware tab).
If you disable or don't configure this policy setting, the setting in the Device Installation Settings dialog box controls whether Windows retrieves device metadata from the Internet.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceMetadata_PreventDeviceMetadataFromNetwork |
| Friendly Name | Prevent device metadata retrieval from the Internet |
| Location | Computer Configuration |
| Path | System > Device Installation |
| Registry Key Name | SOFTWARE\Policies\Microsoft\Windows\Device Metadata |
| Registry Value Name | PreventDeviceMetadataFromNetwork |
| ADMX File Name | DeviceSetup.admx |
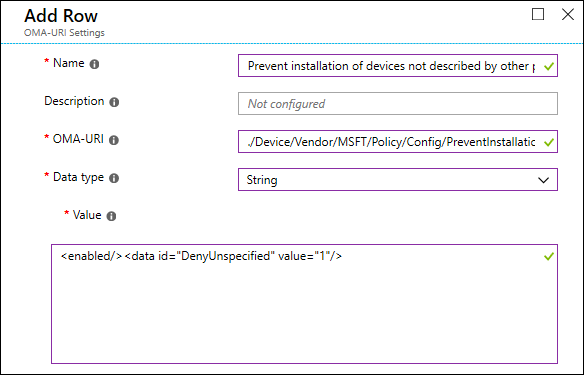
PreventInstallationOfDevicesNotDescribedByOtherPolicySettings
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 1809 [10.0.17763] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfDevicesNotDescribedByOtherPolicySettings
This policy setting allows you to prevent the installation of devices that aren't specifically described by any other policy setting.
Note
This policy setting has been replaced by the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting to provide more granular control. It's recommended that you use the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting instead of this policy setting.
If you enable this policy setting, Windows is prevented from installing or updating the driver package for any device that isn't described by either the "Allow installation of devices that match any of these device IDs", the "Allow installation of devices for these device classes", or the "Allow installation of devices that match any of these device instance IDs" policy setting.
If you disable or don't configure this policy setting, Windows is allowed to install or update the driver package for any device that isn't described by the "Prevent installation of devices that match any of these device IDs", "Prevent installation of devices for these device classes" policy setting, "Prevent installation of devices that match any of these device instance IDs", or "Prevent installation of removable devices" policy setting.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_Unspecified_Deny |
| Friendly Name | Prevent installation of devices not described by other policy settings |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | DenyUnspecified |
| ADMX File Name | DeviceInstallation.admx |
Example:
To enable this policy, use the following SyncML. This example prevents Windows from installing devices that aren't described by any other policy setting.
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfDevicesNotDescribedByOtherPolicySettings</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><data id="DenyUnspecified" value="1"/></Data>
</Item>
</Replace>
</SyncBody>
</SyncML>
Verify:
To verify the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]
You can also block installation by using a custom profile in Intune.
PreventInstallationOfMatchingDeviceIDs
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 1703 [10.0.15063] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfMatchingDeviceIDs
This policy setting allows you to specify a list of Plug and Play hardware IDs and compatible IDs for devices that Windows is prevented from installing. By default, this policy setting takes precedence over any other policy setting that allows Windows to install a device.
Note
To enable the "Allow installation of devices that match any of these device instance IDs" policy setting to supersede this policy setting for applicable devices, enable the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting.
If you enable this policy setting, Windows is prevented from installing a device whose hardware ID or compatible ID appears in the list you create.
If you enable this policy setting on a remote desktop server, the policy setting affects redirection of the specified devices from a remote desktop client to the remote desktop server.
If you disable or don't configure this policy setting, devices can be installed and updated as allowed or prevented by other policy settings.
Peripherals can be specified by their hardware identity. For a list of common identifier structures, see Device Identifier Formats. Test the configuration prior to rolling it out to ensure it blocks the devices expected. Ideally test various instances of the hardware. For example, test multiple USB keys rather than only one.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_IDs_Deny |
| Friendly Name | Prevent installation of devices that match any of these device IDs |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | DenyDeviceIDs |
| ADMX File Name | DeviceInstallation.admx |
Example:
To enable this policy, use the following SyncML. This example prevents Windows from installing compatible devices with a device ID of USB\Composite or USB\Class_FF. To configure multiple classes, use &#xF000; as a delimiter. To apply the policy to matching device classes that are already installed, set DeviceInstall_IDs_Deny_Retroactive to true.
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfMatchingDeviceIDs</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><data id="DeviceInstall_IDs_Deny_Retroactive" value="true"/><Data id="DeviceInstall_IDs_Deny_List" value="1USB\Composite2USB\Class_FF"/></Data>
</Item>
</Replace>
</SyncBody>
</SyncML>
Verify:
To verify the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]
You can also block installation and usage of prohibited peripherals by using a custom profile in Intune.
For example, this custom profile blocks installation and usage of USB devices with hardware IDs "USB\Composite" and "USB\Class_FF", and applies to USB devices with matching hardware IDs that are already installed.

PreventInstallationOfMatchingDeviceInstanceIDs
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 2004 [10.0.19041] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfMatchingDeviceInstanceIDs
This policy setting allows you to specify a list of Plug and Play device instance IDs for devices that Windows is prevented from installing. This policy setting takes precedence over any other policy setting that allows Windows to install a device.
If you enable this policy setting, Windows is prevented from installing a device whose device instance ID appears in the list you create.
If you enable this policy setting on a remote desktop server, the policy setting affects redirection of the specified devices from a remote desktop client to the remote desktop server.
If you disable or don't configure this policy setting, devices can be installed and updated as allowed or prevented by other policy settings.
Peripherals can be specified by their device instance ID. Test the configuration prior to rolling it out to ensure it allows the devices expected. Ideally test various instances of the hardware. For example, test multiple USB keys rather than only one.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_Instance_IDs_Deny |
| Friendly Name | Prevent installation of devices that match any of these device instance IDs |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | DenyInstanceIDs |
| ADMX File Name | DeviceInstallation.admx |
Example:
To enable this policy, use the following SyncML. This example prevents Windows from installing compatible devices with device instance IDs of USB\VID_1F75 and USB\VID_0781. To configure multiple classes, use  as a delimiter.
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfMatchingDeviceInstanceIDs</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><data id="DeviceInstall_Instance_IDs_Deny_Retroactive" value="true"/><Data id="DeviceInstall_Instance_IDs_Deny_List" value="1USB\VID_1F75&PID_0917\478024118058832USB\VID_0781&PID_5530\4C530001191214116305"/></Data>
</Item>
</Replace>
</SyncBody>
</SyncML>
Verify:
To verify the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]
You can also block installation and usage of prohibited peripherals by using a custom profile in Intune.
For example, this custom profile prevents installation of devices with matching device instance IDs.

To prevent installation of devices with matching device instance IDs by using custom profile in Intune:
Locate the device instance ID.
Replace
&in the device instance IDs with&. For example: ReplaceUSBSTOR\DISK&VEN_SAMSUNG&PROD_FLASH_DRIVE&REV_1100\0376319020002347&0withUSBSTOR\DISK&VEN_SAMSUNG&PROD_FLASH_DRIVE&REV_1100\0376319020002347&0.Note
Don't use spaces in the value.
Replace the device instance IDs with
&into the sample SyncML. Add the SyncML into the Intune custom device configuration profile.
PreventInstallationOfMatchingDeviceSetupClasses
| Scope | Editions | Applicable OS |
|---|---|---|
| ✅ Device ❌ User |
✅ Pro ✅ Enterprise ✅ Education ✅ Windows SE ✅ IoT Enterprise / IoT Enterprise LTSC |
✅ Windows 10, version 1703 [10.0.15063] and later |
./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfMatchingDeviceSetupClasses
This policy setting allows you to specify a list of device setup class globally unique identifiers (GUIDs) for driver packages that Windows is prevented from installing. By default, this policy setting takes precedence over any other policy setting that allows Windows to install a device.
Note
To enable the "Allow installation of devices that match any of these device IDs" and "Allow installation of devices that match any of these device instance IDs" policy settings to supersede this policy setting for applicable devices, enable the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting.
If you enable this policy setting, Windows is prevented from installing or updating driver packages whose device setup class GUIDs appear in the list you create.
If you enable this policy setting on a remote desktop server, the policy setting affects redirection of the specified devices from a remote desktop client to the remote desktop server.
If you disable or don't configure this policy setting, Windows can install and update devices as allowed or prevented by other policy settings.
Peripherals can be specified by their hardware identity. For a list of common identifier structures, see Device Identifier Formats. Test the configuration prior to rolling it out to ensure it blocks the devices expected. Ideally test various instances of the hardware. For example, test multiple USB keys rather than only one.
Description framework properties:
| Property name | Property value |
|---|---|
| Format | chr (string) |
| Access Type | Add, Delete, Get, Replace |
Tip
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy.
ADMX mapping:
| Name | Value |
|---|---|
| Name | DeviceInstall_Classes_Deny |
| Friendly Name | Prevent installation of devices using drivers that match these device setup classes |
| Location | Computer Configuration |
| Path | System > Device Installation > Device Installation Restrictions |
| Registry Key Name | Software\Policies\Microsoft\Windows\DeviceInstall\Restrictions |
| Registry Value Name | DenyDeviceClasses |
| ADMX File Name | DeviceInstallation.admx |
Example:
To enable this policy, use the following SyncML. This example prevents Windows from installing:
- Floppy Disks, ClassGUID = {4d36e980-e325-11ce-bfc1-08002be10318}
- CD ROMs, ClassGUID = {4d36e965-e325-11ce-bfc1-08002be10318}
- Modems, ClassGUID = {4d36e96d-e325-11ce-bfc1-08002be10318}
Enclose the class GUID within curly brackets {}. To configure multiple classes, use  as a delimiter. To apply the policy to matching device classes that are already installed, set DeviceInstall_Classes_Deny_Retroactive to true.
<SyncML>
<SyncBody>
<Replace>
<CmdID>$CmdID$</CmdID>
<Item>
<Target>
<LocURI>./Device/Vendor/MSFT/Policy/Config/DeviceInstallation/PreventInstallationOfMatchingDeviceSetupClasses</LocURI>
</Target>
<Meta>
<Format xmlns="syncml:metinf">string</Format>
</Meta>
<Data><enabled/><data id="DeviceInstall_Classes_Deny_Retroactive" value="true"/><Data id="DeviceInstall_Classes_Deny_List" value="1{4d36e980-e325-11ce-bfc1-08002be10318}2{4d36e965-e325-11ce-bfc1-08002be10318}3{4d36e96d-e325-11ce-bfc1-08002be10318}"/></Data>
</Item>
</Replace>
</SyncBody>
</SyncML>
Verify:
To verify the policy is applied, check C:\windows\INF\setupapi.dev.log and see if the following details are listed near the end of the log:
>>> [Device Installation Restrictions Policy Check]
>>> Section start 2018/11/15 12:26:41.659
<<< Section end 2018/11/15 12:26:41.751
<<< [Exit status: SUCCESS]