Not
Bu sayfaya erişim yetkilendirme gerektiriyor. Oturum açmayı veya dizinleri değiştirmeyi deneyebilirsiniz.
Bu sayfaya erişim yetkilendirme gerektiriyor. Dizinleri değiştirmeyi deneyebilirsiniz.
There are different tools and options to manage and operate BitLocker:
- the BitLocker PowerShell module
- the BitLocker drive encryption tools
- Control Panel
The BitLocker drive encryption tools and BitLocker PowerShell module can be used to perform any tasks that can be accomplished through the BitLocker Control Panel. They're appropriate to use for automated deployments and other scripting scenarios.
The BitLocker Control Panel applet allows users to perform basic tasks such as turning on BitLocker on a drive and specifying unlock methods and authentication methods. The BitLocker Control Panel applet is appropriate to use for basic BitLocker tasks.
This article describes the BitLocker management tools and how to use them, providing practical examples.
BitLocker PowerShell module
The BitLocker PowerShell module enables administrators to integrate BitLocker options into existing scripts with ease. For a list of cmdlets included in module, their description and syntax, check the BitLocker PowerShell reference article.
BitLocker drive encryption tools
The BitLocker drive encryption tools include the two command-line tools:
- Configuration Tool (
manage-bde.exe) can be used for scripting BitLocker operations, offering options that aren't present in the BitLocker Control Panel applet. For a complete list of themanage-bde.exeoptions, see the Manage-bde reference - Repair Tool (
repair-bde.exe) is useful for disaster recovery scenarios, in which a BitLocker protected drive can't be unlocked normally or using the recovery console
BitLocker Control Panel applet
Encrypting volumes with the BitLocker Control Panel (select Start, enter BitLocker, select Manage BitLocker) is how many users will use BitLocker. The name of the BitLocker Control Panel applet is BitLocker Drive Encryption. The applet supports encrypting operating system, fixed data, and removable data volumes. The BitLocker Control Panel organizes available drives in the appropriate category based on how the device reports itself to Windows. Only formatted volumes with assigned drive letters appear properly in the BitLocker Control Panel applet.
Important: The Shell Hardware Detection Service (ShellHWDetection) is required to manage BitLocker via Control Panel or via Explorer.
Use BitLocker within Windows Explorer
Windows Explorer allows users to launch the BitLocker Drive Encryption Wizard by right-clicking a volume and selecting Turn On BitLocker. This option is available on client computers by default. On servers, the BitLocker feature and the Desktop-Experience feature must first be installed for this option to be available. After selecting Turn on BitLocker, the wizard works exactly as it does when launched using the BitLocker Control Panel.
Check the BitLocker status
To check the BitLocker status of a particular volume, administrators can look at the status of the drive in the BitLocker Control Panel applet, Windows Explorer, manage-bde.exe command-line tool, or Windows PowerShell cmdlets. Each option offers different levels of detail and ease of use.
Follow the instructions below verify the status of BitLocker, selecting the tool of your choice.
To determine the current state of a volume you can use the Get-BitLockerVolume cmdlet, which provides information on the volume type, protectors, protection status, and other details. For example:
PS C:\> Get-BitLockerVolume C: | fl
ComputerName : DESKTOP
MountPoint : C:
EncryptionMethod : XtsAes128
AutoUnlockEnabled :
AutoUnlockKeyStored : False
MetadataVersion : 2
VolumeStatus : FullyEncrypted
ProtectionStatus : On
LockStatus : Unlocked
EncryptionPercentage : 100
WipePercentage : 0
VolumeType : OperatingSystem
CapacityGB : 1000
KeyProtector : {Tpm, RecoveryPassword}
Enable BitLocker
OS drive with TPM protector
The following example shows how to enable BitLocker on an operating system drive using only the TPM protector and no recovery key:
Enable-BitLocker C: -TpmProtector
OS drive with TPM protector and startup key
The following example shows how to enable BitLocker on an operating system drive using the TPM and startup key protectors.
Assuming the OS drive letter is C: and the USB flash drive is drive letter E:, here's the command:
If you choose to skip the BitLocker hardware test, encryption starts immediately without the need for a reboot.
Enable-BitLocker C: -StartupKeyProtector -StartupKeyPath E: -SkipHardwareTest
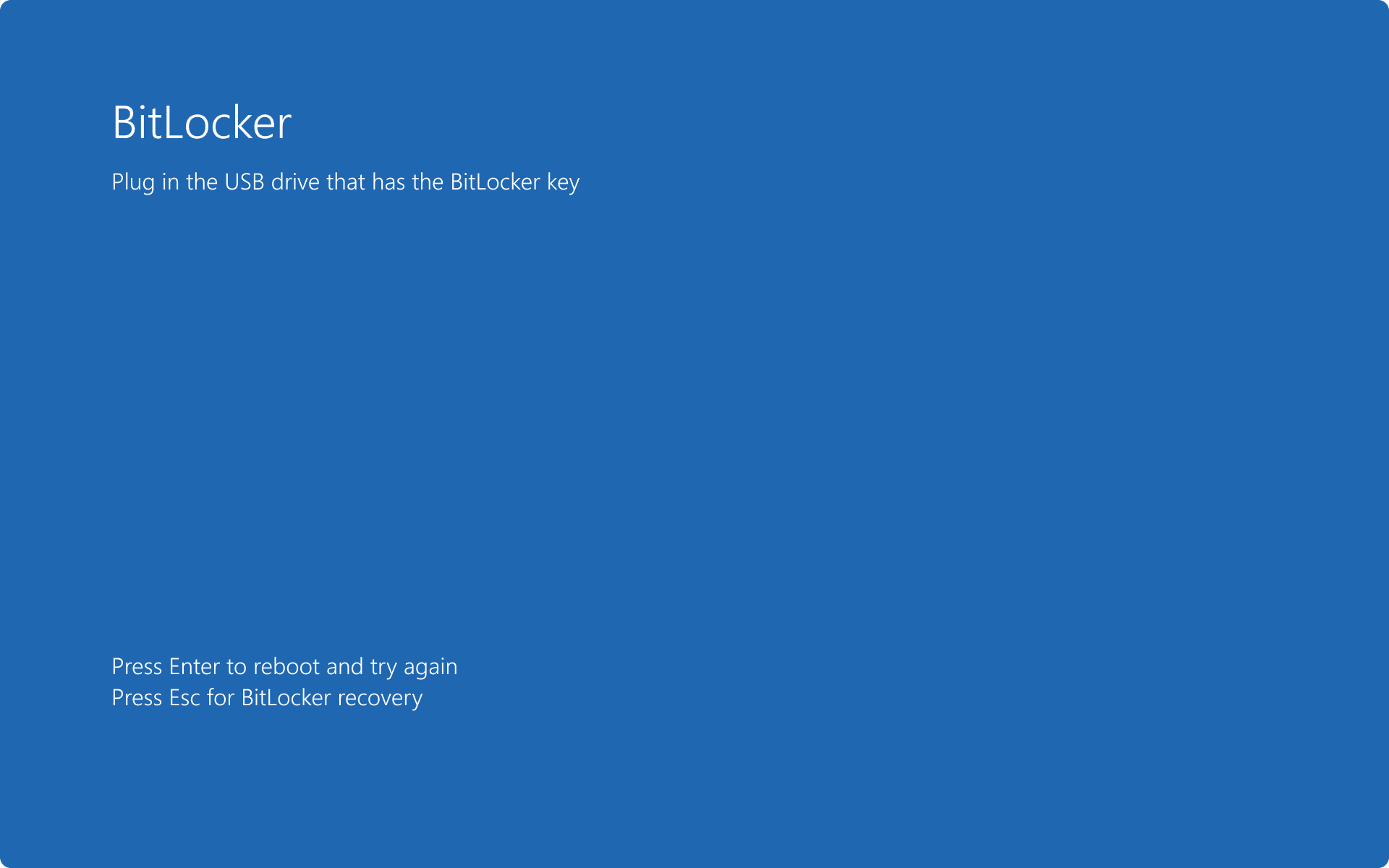
After reboot, the BitLocker preboot screen displays and the USB startup key must be inserted before the operating system can be started:
Data volumes
Data volumes use a similar process for encryption as operating system volumes, but they don't require protectors for the operation to complete.
Add the desired protectors prior to encrypting the volume. The following example adds a password protector to the E: volume using the variable $pw as the password. The $pw variable is held as a SecureString value to store the user-defined password:
$pw = Read-Host -AsSecureString
<user inputs password>
Add-BitLockerKeyProtector E: -PasswordProtector -Password $pw
Note
The BitLocker cmdlet requires the key protector GUID enclosed in quotation marks to execute. Ensure the entire GUID, with braces, is included in the command.
Example: Use PowerShell to enable BitLocker with a TPM protector
Enable-BitLocker D: -EncryptionMethod XtsAes256 -UsedSpaceOnly -TpmProtector
Example: Use PowerShell to enable BitLocker with a TPM+PIN protector, in this case with a PIN set to 123456:
$SecureString = ConvertTo-SecureString "123456" -AsPlainText -Force
Enable-BitLocker C: -EncryptionMethod XtsAes256 -UsedSpaceOnly -Pin $SecureString -TPMandPinProtector
Manage BitLocker protectors
The management of BitLocker protectors consists in adding, removing, and backing up protectors.
Managed BitLocker protectors by using the following instructions, selecting the option that best suits your needs.
List protectors
The list of protectors available for a volume (C: in the example) can be listed by running the following command:
(Get-BitLockerVolume -mountpoint C).KeyProtector
Add protectors
Add a recovery password protector
Add-BitLockerKeyProtector -MountPoint C -RecoveryPasswordProtector
Add a password protector
A common protector for a data volume is the password protector. In the next example, a password protector is added to a volume.
Add-BitLockerKeyProtector -MountPoint D -PasswordProtector
Add an Active Directory protector
The Active Directory protector is a SID-based protector that can be added to both operating system and data volumes, although it doesn't unlock operating system volumes in the preboot environment. The protector requires the SID for the domain account or group to link with the protector. BitLocker can protect a cluster-aware disk by adding an SID-based protector for the Cluster Name Object (CNO) that lets the disk properly failover and unlock to any member computer of the cluster.
Important
The SID-based protector requires the use of an additional protector such as TPM, PIN, recovery key, etc. when used on operating system volumes.
Note
This option is not available for Microsoft Entra joined devices.
In this example, a domain SID-based protector is added to a previously encrypted volume. The user knows the SID for the user account or group they wish to add and uses the following command:
Add-BitLockerKeyProtector C: -ADAccountOrGroupProtector -ADAccountOrGroup "<SID>"
To add the protector to a volume, either the domain SID or the group name preceded by the domain and a backslash are needed. In the following example, the CONTOSO\Administrator account is added as a protector to the data volume G.
Enable-BitLocker G: -AdAccountOrGroupProtector -AdAccountOrGroup CONTOSO\Administrator
To use the SID for the account or group, the first step is to determine the SID associated with the security principal. To get the specific SID for a user account in Windows PowerShell, use the following command:
Get-ADUser -filter {samaccountname -eq "administrator"}
Note
Use of this command requires the RSAT-AD-PowerShell feature.
Tip
Information about the locally logged on user and group membership can be found using: whoami.exe /all.
Remove protectors
To remove existing protectors on a volume, use the Remove-BitLockerKeyProtector cmdlet. A GUID associated with the protector to be removed must be provided.
The following commands return the list of key protectors and GUIDS:
$vol = Get-BitLockerVolume C
$keyprotectors = $vol.KeyProtector
$keyprotectors
By using this information, the key protector for a specific volume can be removed using the command:
Remove-BitLockerKeyProtector <volume> -KeyProtectorID "{GUID}"
Note
The BitLocker cmdlet requires the key protector GUID enclosed in quotation marks to execute. Ensure the entire GUID, with braces, is included in the command.
Note
You must have at least one unlock method for any BitLocker-encrypted drives.
Suspend and resume
Some configuration changes may require to suspend BitLocker and then resume it after the change is applied.
Suspend and resume BitLocker by using the following instructions, selecting the option that best suits your needs.
Suspend BitLocker
Suspend-BitLocker -MountPoint D
Resume BitLocker
Note
Resuming protection only works on devices that have accepted the Windows EULA.
Resume-BitLocker -MountPoint D
Reset and backup a recovery password
It's recommended to invalidate a recovery password after its use. In this example the recovery password protector is removed from the OS drive, a new protector added, and backed up to Microsoft Entra ID or Active Directory.
Remove all recovery passwords from the OS volume:
(Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | `
where-object {$_.KeyProtectorType -eq 'RecoveryPassword'} | `
Remove-BitLockerKeyProtector -MountPoint $env:SystemDrive
Add a BitLocker recovery password protector for the OS volume:
Add-BitLockerKeyProtector -MountPoint $env:SystemDrive -RecoveryPasswordProtector
Obtain the ID of the new recovery password:
(Get-BitLockerVolume -mountpoint $env:SystemDrive).KeyProtector | where-object {$_.KeyProtectorType -eq 'RecoveryPassword'} | ft KeyProtectorId,RecoveryPassword
Note
This next steps are not required if the policy setting Choose how BitLocker-protected operating system drives can be recovered is configured to Require BitLocker backup to AD DS.
Copy the ID of the recovery password from the output.
Using the GUID from the previous step, replace the {ID} in the following command and use the following command to back up the recovery password to Microsoft Entra ID:
BackuptoAAD-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId "{ID}"
Or use the following command to back up the recovery password to Active Directory:
Backup-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId "{ID}"
Note
The braces {} must be included in the ID string.
Disable BitLocker
Disabling BitLocker decrypts and removes any associated protectors from the volumes. Decryption should occur when protection is no longer required, and not as a troubleshooting step.
Disable BitLocker by using the following instructions, selecting the option that best suits your needs.
Windows PowerShell offers the ability to decrypt multiple drives in one pass. In the following example, the user has three encrypted volumes, which they wish to decrypt.
Using the Disable-BitLocker command, they can remove all protectors and encryption at the same time without the need for more commands. An example of this command is:
Disable-BitLocker
To avoid specifying each mount point individually, use the -MountPoint parameter in an array to sequence the same command into one line, without requiring additional user input. Example:
Disable-BitLocker -MountPoint C,D
Unlock a drive
If you connect a drive as a secondary drive to a device, and you have your BitLocker recovery key, you can unlock a BitLocker-enabled drive by using the following instructions.
In the next example, the D drive is the one to unlock. Select the option that best suits your needs.
Unlock-BitLocker -MountPoint D -RecoveryPassword xxxxxx-xxxxxx-xxxxxx-xxxxxx-xxxxxx-xxxxxx-xxxxxx-xxxxxx
For more information, see Unlock-BitLocker