Enable Microsoft Defender for Storage (classic)
This article explains how you can enable and configure Microsoft Defender for Storage (Classic) on your subscriptions by using various templates such as PowerShell, REST API, and others.
You can also upgrade to the new Microsoft Defender for Storage plan and use advanced security capabilities, including Malware Scanning and sensitive data threat detection. Benefit from a more predictable and granular pricing structure that charges per storage account, with extra costs for high-volume transactions. This new pricing plan also encompasses all new security features and detections.
Note
If you're using Defender for Storage (classic) with per-transaction or per-storage account pricing, you'll need to migrate to the new Defender for Storage plan to access these features and pricing. Learn about migrating to the new Defender for Storage plan.
Microsoft Defender for Storage is an Azure-native layer of security intelligence that detects unusual and potentially harmful attempts to access or exploit your storage accounts. It uses advanced threat detection capabilities and Microsoft Threat Intelligence data to provide contextual security alerts. Those alerts also include steps to mitigate the detected threats and prevent future attacks.
Microsoft Defender for Storage continuously analyzes the transactions of Azure Blob Storage, Azure Data Lake Storage, and Azure Files services. When potentially malicious activities are detected, security alerts are generated. Alerts are shown in Microsoft Defender for Cloud with the details of the suspicious activity, appropriate investigation steps, remediation actions, and security recommendations.
Analyzed telemetry of Azure Blob Storage includes operation types such as Get Blob, Put Blob, Get Container ACL, List Blobs, and Get Blob Properties. Examples of analyzed Azure Files operation types include Get File, Create File, List Files, Get File Properties, and Put Range.
Defender for Storage classic doesn’t access the Storage account data and has no impact on its performance.
Learn more about the benefits, features, and limitations of Defender for Storage. You can also learn more about Defender for Storage in the Defender for Storage episode of the Defender for Cloud in the Field video series.
Availability
| Aspect | Details |
|---|---|
| Release state: | General availability (GA) |
| Pricing: | Microsoft Defender for Storage is billed as shown in the pricing details and in the Defender plans in the Azure portal |
| Protected storage types: | Blob Storage (Standard/Premium StorageV2, Block Blobs) Azure Files (over REST API and SMB) Azure Data Lake Storage Gen2 (Standard/Premium accounts with hierarchical namespaces enabled) |
| Clouds: |
Set up Microsoft Defender for Storage (classic)
Set up per-transaction pricing for a subscription
For the Defender for Storage per-transaction pricing, we recommend that you enable Defender for Storage for each subscription so that all existing and new storage accounts are protected. If you want to only protect specific accounts, configure Defender for Storage for each account.
You can configure Microsoft Defender for Storage on your subscriptions in several ways:
Terraform template
To enable Microsoft Defender for Storage at the subscription level with per-transaction pricing using a Terraform template, add this code snippet to your template with your subscription ID as the parent_id value:
resource "azapi_resource" "symbolicname" {
type = "Microsoft.Security/pricings@2022-03-01"
name = "StorageAccounts"
parent_id = "<subscriptionId>"
body = jsonencode({
properties = {
pricingTier = "Standard"
subPlan = "PerTransaction"
}
})
}
To disable the plan, set the pricingTier property value to Free and remove the subPlan property.
Learn more about the ARM template AzAPI reference.
Bicep template
To enable Microsoft Defender for Storage at the subscription level with per-transaction pricing using Bicep, add the following to your Bicep template:
resource symbolicname 'Microsoft.Security/pricings@2022-03-01' = {
name: 'StorageAccounts'
properties: {
pricingTier: 'Standard'
subPlan: 'PerTransaction'
}
}
To disable the plan, set the pricingTier property value to Free and remove the subPlan property.
Learn more about the Bicep template AzAPI reference.
ARM template
To enable Microsoft Defender for Storage at the subscription level with per-transaction pricing using an ARM template, add this JSON snippet to the resources section of your ARM template:
{
"type": "Microsoft.Security/pricings",
"apiVersion": "2022-03-01",
"name": "StorageAccounts",
"properties": {
"pricingTier": "Standard",
"subPlan": "PerTransaction"
}
}
To disable the plan, set the pricingTier property value to Free and remove the subPlan property.
Learn more about the ARM template AzAPI reference.
PowerShell
To enable Microsoft Defender for Storage at the subscription level with per-transaction pricing using PowerShell:
If you don't have it already, install the Azure Az PowerShell module.
Use the
Connect-AzAccountcmdlet to sign in to your Azure account. Learn more about signing in to Azure with Azure PowerShell.Use these commands to register your subscription to the Microsoft Defender for Cloud Resource Provider:
Set-AzContext -Subscription <subscriptionId> Register-AzResourceProvider -ProviderNamespace 'Microsoft.Security'Replace
<subscriptionId>with your subscription ID.Enable Microsoft Defender for Storage for your subscription with the
Set-AzSecurityPricingcmdlet:Set-AzSecurityPricing -Name "StorageAccounts" -PricingTier "Standard"
Tip
You can use the GetAzSecurityPricing (Az_Security) to see all of the Defender for Cloud plans that are enabled for the subscription.
To disable the plan, set the -PricingTier property value to Free.
Learn more about the using PowerShell with Microsoft Defender for Cloud.
Azure CLI
To enable Microsoft Defender for Storage at the subscription level with per-transaction pricing using Azure CLI:
If you don't have it already, install the Azure CLI.
Use the
az logincommand to sign in to your Azure account. Learn more about signing in to Azure with Azure CLI.Use these commands to set the subscription ID and name:
az account set --subscription "<subscriptionId or name>"Replace
<subscriptionId>with your subscription ID.Enable Microsoft Defender for Storage for your subscription with the
az security pricing createcommand:az security pricing create -n StorageAccounts --tier "standard"
Tip
You can use the az security pricing show command to see all of the Defender for Cloud plans that are enabled for the subscription.
To disable the plan, set the -tier property value to free.
Learn more about the az security pricing create command.
REST API
To enable Microsoft Defender for Storage at the subscription level with per-transaction pricing using the Microsoft Defender for Cloud REST API, create a PUT request with this endpoint and body:
PUT https://management.azure.com/subscriptions/{subscriptionId}/providers/Microsoft.Security/pricings/StorageAccounts?api-version=2022-03-01
{
"properties": {
"pricingTier": "Standard",
"subPlan": "PerTransaction"
}
}
Replace {subscriptionId} with your subscription ID.
To disable the plan, set the -pricingTier property value to Free and remove the subPlan parameter.
Learn more about the updating Defender plans with the REST API in HTTP, Java, Go and JavaScript.
Set up per-transaction pricing for a storage account
You can configure Microsoft Defender for Storage with per-transaction pricing on your accounts in several ways:
ARM template
To enable Microsoft Defender for Storage for a specific storage account with per-transaction pricing using an ARM template, use the prepared Azure template.
If you want to disable Defender for Storage on the account:
- Sign in to the Azure portal.
- Navigate to your storage account.
- In the Security + networking section of the Storage account menu, select Microsoft Defender for Cloud.
- Select Disable.
PowerShell
To enable Microsoft Defender for Storage for a specific storage account with per-transaction pricing using PowerShell:
If you don't have it already, install the Azure Az PowerShell module.
Use the Connect-AzAccount cmdlet to sign in to your Azure account. Learn more about signing in to Azure with Azure PowerShell.
Enable Microsoft Defender for Storage for the desired storage account with the
Enable-AzSecurityAdvancedThreatProtectioncmdlet:Enable-AzSecurityAdvancedThreatProtection -ResourceId "/subscriptions/<subscription-id>/resourceGroups/<resource-group>/providers/Microsoft.Storage/storageAccounts/<storage-account>/"Replace
<subscriptionId>,<resource-group>, and<storage-account>with the values for your environment.
If you want to disable per-transaction pricing for a specific storage account, use the Disable-AzSecurityAdvancedThreatProtection cmdlet:
Disable-AzSecurityAdvancedThreatProtection -ResourceId "/subscriptions/<subscription-id>/resourceGroups/<resource-group>/providers/Microsoft.Storage/storageAccounts/<storage-account>/"
Learn more about the using PowerShell with Microsoft Defender for Cloud.
Azure CLI
To enable Microsoft Defender for Storage for a specific storage account with per-transaction pricing using Azure CLI:
If you don't have it already, install the Azure CLI.
Use the
az logincommand to sign in to your Azure account. Learn more about signing in to Azure with Azure CLI.Enable Microsoft Defender for Storage for your subscription with the
az security atp storage updatecommand:az security atp storage update \ --resource-group <resource-group> \ --storage-account <storage-account> \ --is-enabled true
Tip
You can use the az security atp storage show command to see if Defender for Storage is enabled on an account.
To disable Microsoft Defender for Storage for your subscription, use the az security atp storage update command:
az security atp storage update \
--resource-group <resource-group> \
--storage-account <storage-account> \
--is-enabled false
Learn more about the az security atp storage command.
Exclude a storage account from a protected subscription in the per-transaction plan
When you enable Microsoft Defender for Storage on a subscription for the per-transaction pricing, all current and future Azure Storage accounts in that subscription are protected. You can exclude specific storage accounts from the Defender for Storage protections using the Azure portal, PowerShell, or the Azure CLI.
We recommend that you enable Defender for Storage on the entire subscription to protect all existing and future storage accounts in it. However, there are some cases where people want to exclude specific storage accounts from Defender protection.
Exclusion of storage accounts from protected subscriptions requires you to:
- Add a tag to block inheriting the subscription enablement.
- Disable Defender for Storage (classic).
Note
Consider upgrading to the new Defender for Storage plan if you have storage accounts you would like to exclude from the Defender for Storage classic plan. Not only will you save on costs for transaction-heavy accounts, but you'll also gain access to enhanced security features. Learn more about the benefits of migrating to the new plan.
Excluded storage accounts in the Defender for Storage classic are not automatically excluded when you migrate to the new plan.
Exclude an Azure Storage account protection on a subscription with per-transaction pricing
To exclude an Azure Storage account from Microsoft Defender for Storage (classic), you can use:
Use PowerShell to exclude an Azure Storage account
If you don't have the Azure Az PowerShell module installed, install it using the instructions from the Azure PowerShell documentation.
Using an authenticated account, connect to Azure with the
Connect-AzAccountcmdlet, as explained in Sign in with Azure PowerShell.Define the AzDefenderPlanAutoEnable tag on the storage account with the
Update-AzTagcmdlet (replace the ResourceId with the resource ID of the relevant storage account):Update-AzTag -ResourceId <resourceID> -Tag @{"AzDefenderPlanAutoEnable" = "off"} -Operation MergeIf you skip this stage, your untagged resources continue receiving daily updates from the subscription level enablement policy. That policy enables Defender for Storage again on the account. Learn more about tags in Use tags to organize your Azure resources and management hierarchy.
Disable Microsoft Defender for Storage for the desired account on the relevant subscription with the
Disable-AzSecurityAdvancedThreatProtectioncmdlet (using the same resource ID):Disable-AzSecurityAdvancedThreatProtection -ResourceId <resourceId>
Use Azure CLI to exclude an Azure Storage account
If you don't have Azure CLI installed, install it using the instructions from the Azure CLI documentation.
Using an authenticated account, connect to Azure with the
logincommand as explained in Sign in with Azure CLI and enter your account credentials when prompted:az loginDefine the AzDefenderPlanAutoEnable tag on the storage account with the
tag updatecommand (replace the ResourceId with the resource ID of the relevant storage account):az tag update --resource-id MyResourceId --operation merge --tags AzDefenderPlanAutoEnable=offIf you skip this stage, your untagged resources continue receiving daily updates from the subscription level enablement policy. That policy enables Defender for Storage again on the account.
Tip
Learn more about tags in az tag.
Disable Microsoft Defender for Storage for the desired account on the relevant subscription with the
security atp storagecommand (using the same resource ID):az security atp storage update --resource-group MyResourceGroup --storage-account MyStorageAccount --is-enabled false
Exclude an Azure Databricks Storage account
Exclude an active Databricks workspace
Microsoft Defender for Storage can exclude specific active Databricks workspace storage accounts, when the plan is already enabled on a subscription.
To exclude an active Databricks workspace:
Sign in to the Azure portal.
Navigate to Azure Databricks >
Your Databricks workspace> Tags.In the Name field, enter
AzDefenderPlanAutoEnable.In the Value field, enter
offand then select Apply.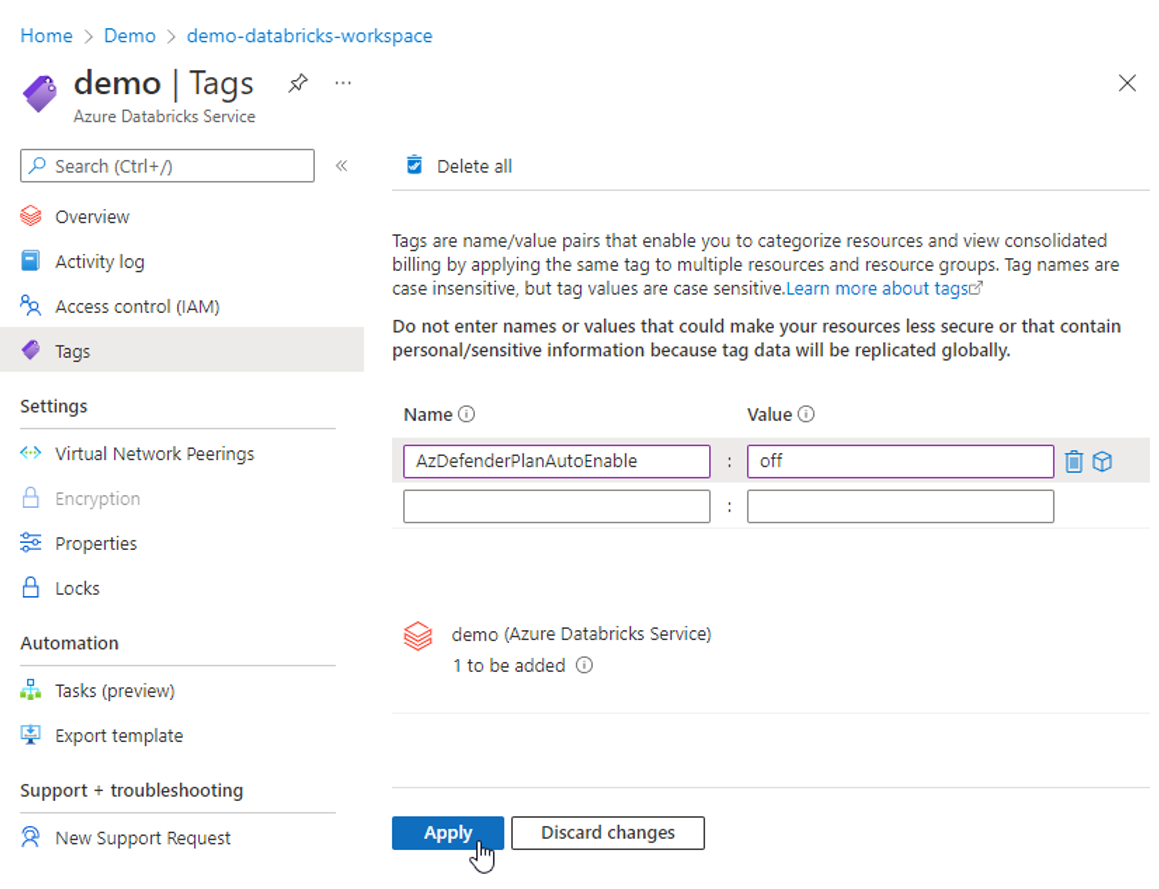
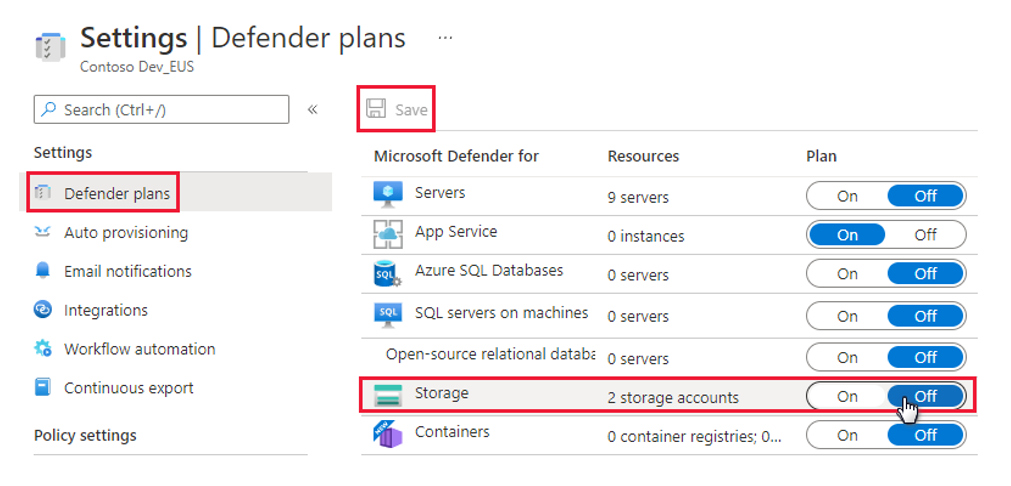
Navigate to Microsoft Defender for Cloud > Environment settings >
Your subscription.Turn the Defender for Storage plan to Off and select Save.
Re-enable Defender for Storage (classic) using one of the supported methods (you can’t enable Defender for Storage classic from the Azure portal).
The tags are inherited by the Storage account of the Databricks workspace and prevent Defender for Storage from turning on.
Note
Tags can't be added directly to the Databricks Storage account, or its Managed Resource Group.
Prevent autoenabling on a new Databricks workspace storage account
When you create a new Databricks workspace, you have the ability to add a tag that prevents your Microsoft Defender for Storage account from enabling automatically.
To prevent auto-enabling on a new Databricks workspace storage account:
Follow these steps to create a new Azure Databricks workspace.
In the Tags tab, enter a tag named
AzDefenderPlanAutoEnable.Enter the value
off.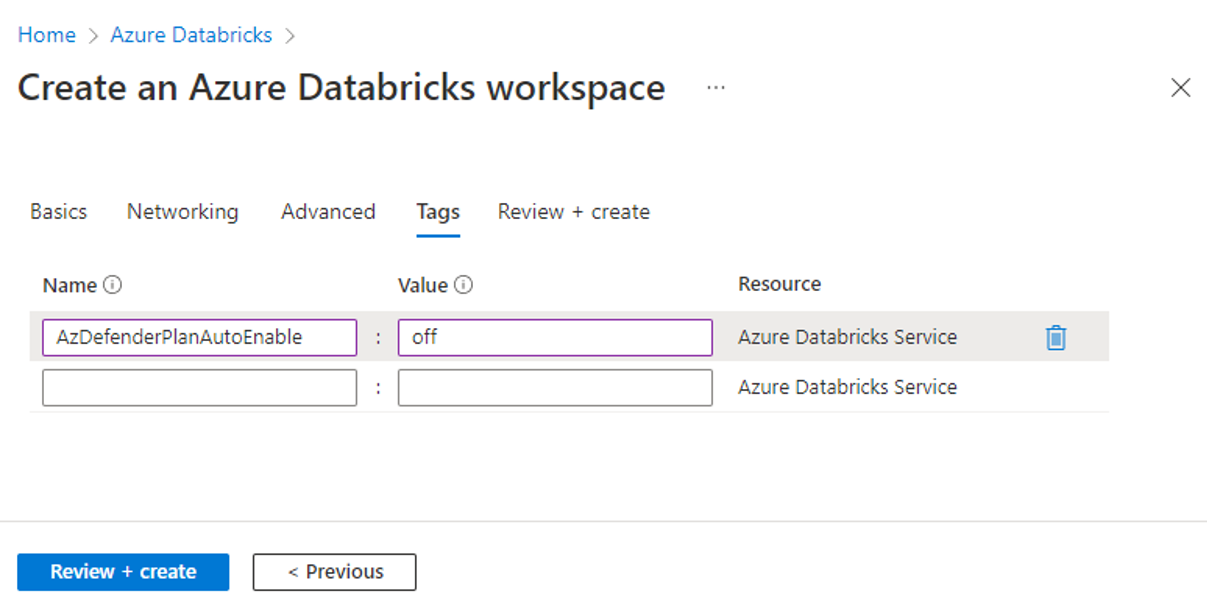
Continue following the instructions to create your new Azure Databricks workspace.
The Microsoft Defender for Storage account inherits the tag of the Databricks workspace, which prevents Defender for Storage from turning on automatically.
Next steps
- Check out the alerts for Azure Storage
- Learn about the features and benefits of Defender for Storage
- Check out common questions about Defender for Storage classic.
Зворотний зв’язок
Очікується незабаром: протягом 2024 року ми будемо припиняти використання механізму реєстрації проблем у GitHub для зворотного зв’язку щодо вмісту й замінювати його новою системою зворотного зв’язку. Докладніше: https://aka.ms/ContentUserFeedback.
Надіслати й переглянути відгук про