Windows 10 Group Policy vs. Intune MDM Policy who wins?
When I speak with organizations about managing Windows 10 devices with Microsoft Intune there is a concern about disruption of current projects to deploy new OSs, patches, etc. When moving to Intune for managing Windows devices, Intune will leverage the built-in MDM agent vs. having to install another agent to manage Windows 10 devices.
With modern management of Windows 10, the process of updating and upgrading Windows 10 devices is seen as continual process. Updating Windows doesn’t have to be seen a massive project, evaluate your current processes for updating Windows and look at updating Windows 10 as an ongoing predictable process for IT and end users. In addition your users and company benefit from the latest security features built into Windows 10.
Managing Windows policies are also a concern when moving to a newer OS. Traditionally, configuration policies are managed by Group Policy, however Modern Management of Windows 10 with Microsoft Intune also has a set of policies, even policies that are duplicative of Group Policy (where applicable, not all Group Policies are available via MDM or CSP ) . In environments where Group Policies are deployed and managed by Intune there’s the question of which policy wins. The following describes which policy wins according to Windows 10 version.
Windows 10 versions 1709 and earlier Group Policy will override MDM policies, even if an identical policy is configured in MDM.
Windows 10 version 1803 and beyond there is a new Policy CSP setting called ControlPolicyConflict that includes the policy of MDMWinsOverGP, where the preference of which policy wins can be controlled, i.e. Microsoft Intune MDM policy.
For more details about the new ControlPolicyConfict setting please visit: /en-us/windows/client-management/mdm/policy-csp-controlpolicyconflict#controlpolicyconflict-mdmwinsovergp
What happens to the policy if the device is unenrolled from Intune? If applicable, Group Policy will re-apply the policies in this scenario.
Setting up a policy
In the link above, the “scope” of the policy is set for “device” so we’ll need to target the policy at the device scope.
To learn more about user and device scopes please visit: /en-us/windows/client-management/mdm/policy-configuration-service-provider#policy-scope
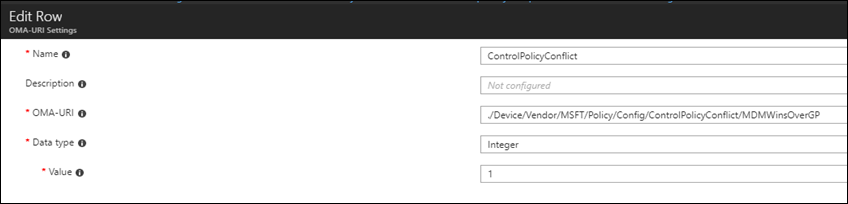
Since the ControlPolicyConfict policy applies to the device, we’ll have to utilize the following string: ./Device/Vendor/MSFT/Policy/Config/AreaName/PolicyName to configure the policy.
Next replace AreaName/PolicyName with ControlPolicyConflict/MDMWinsOverGP
After the modification to the string, the policy should look like the following: ./Device/Vendor/MSFT/Policy/Config/ControlPolicyConflict/MDMWinsOverGP
Creating the policy
Let’s create a new policy in Intune to control the GP vs. MDM winner
- Navigate to portal.azure.com and locate Intune
- Select “Device configuration à Profiles à Create profile”
- Under Platform select Windows 10 and later
- Under Profile type select “custom” and “add”
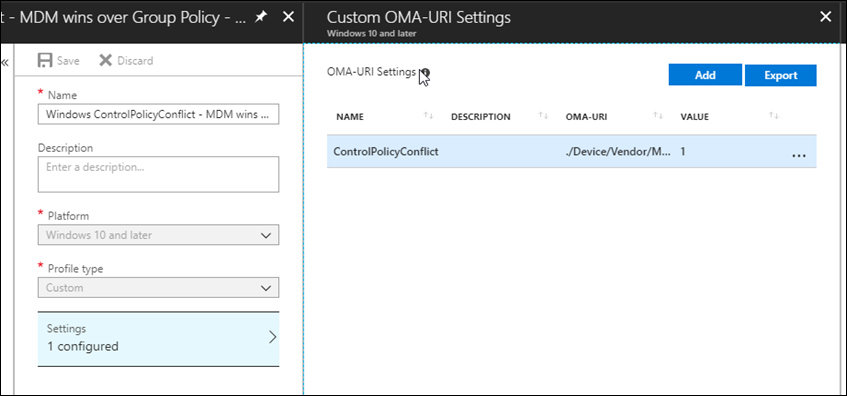
- Name the custom setting with something intuitive
- For OMA-URI add the policy OMA-URI string: ./Device/Vendor/MSFT/Policy/Config/ControlPolicyConflict/MDMWinsOverGP
- For Data type select Integer and add the number 1
Supported values for this policy are as follows:
0 (default)
1 - The MDM policy is used and the GP policy is blocked.
Let’s take a look how the policy is applied
- On the Windows 10 device, select the Windows icon > Settings > Accounts > Access work or school à under the account name select Info
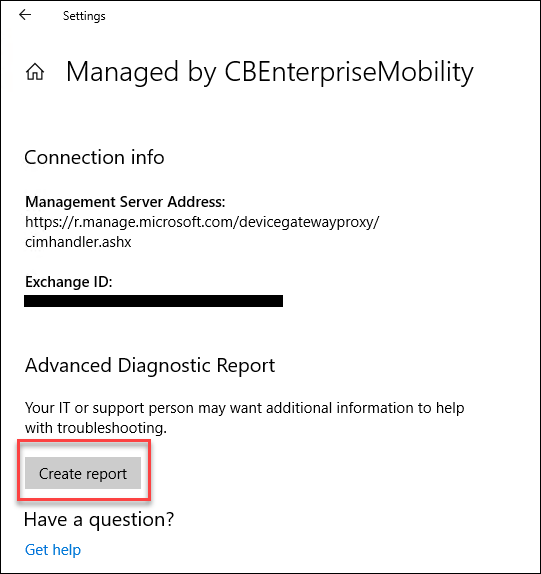
- Sync with Microsoft Intune by selecting “Sync”
- Once the Sync as completed select “Create report”
- Once the report is completed a folder will open containing an .html file
- Open the .html report and search for “MDMwins”
GP Setting before the MDM policy takes place :
MDM setting after the policy is applied (note: Windows 10 1803 is required to override the GP):
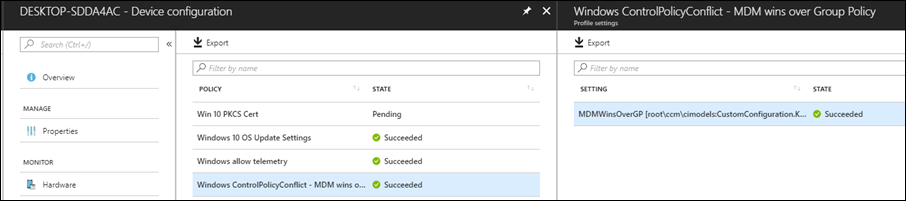
Let’s take a look at a report in Intune regarding the policy and if it was successfully applied. This useful to make sure the policies are actually applying or not.
Logging
Being able to investigate modifications to a device is extremely important, especially when troubleshooting.
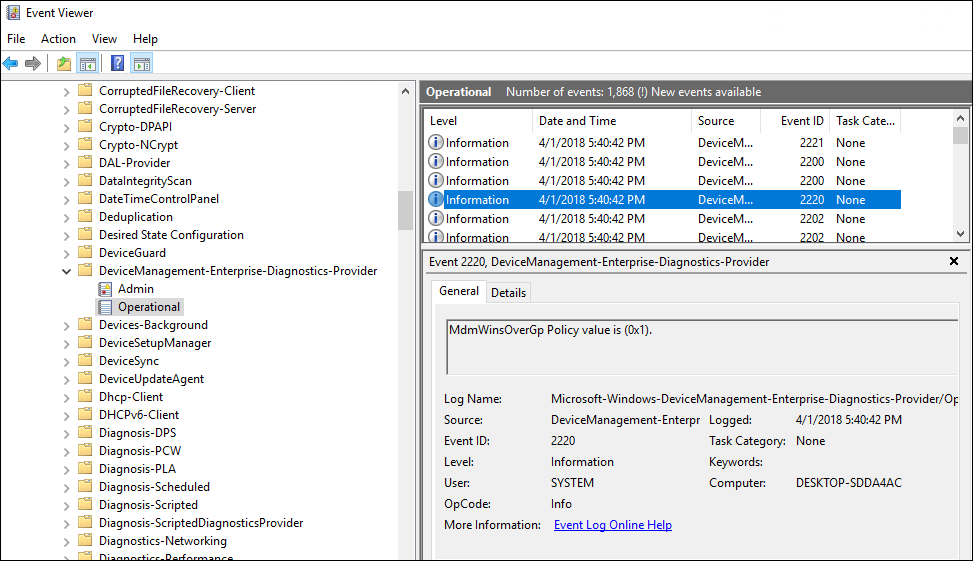
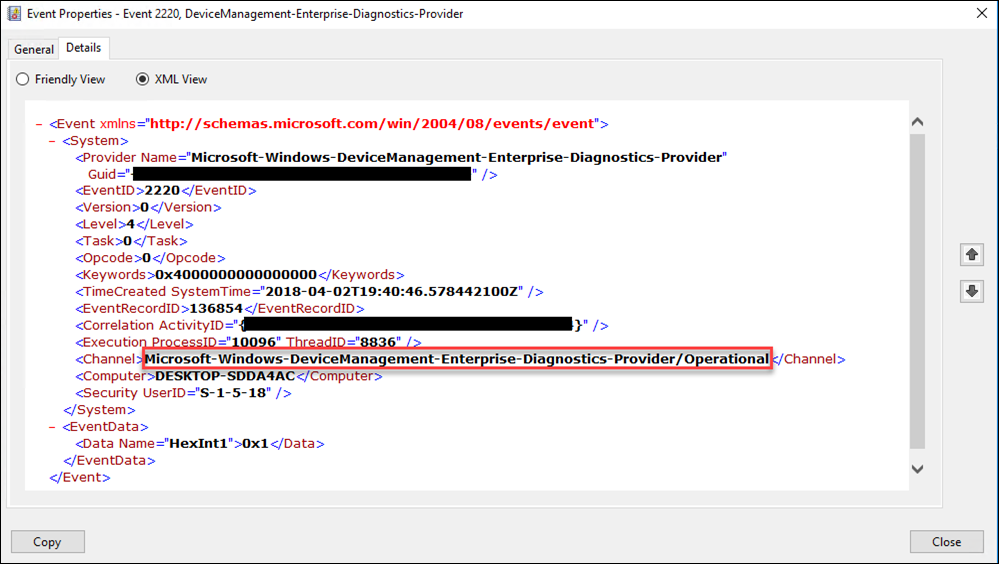
In event viewer we can access the event where the policy was applied as shown below. However digging through events, especially across multiple devices, can be a difficult process. This is where Microsoft Operations Management Suite (OMS) comes in.
Logging with Microsoft Operations Management Suite (OMS)
Within OMS there is the Log Analytics solution to manage logs from devices with the OMS agent installed. I won’t go into details about installing the OMS agent, however I will say it’s straight forward. Once the agent is installed (which I have it installed on all my devices so I can look at label changes with Azure Information Protection ( see my previous post ) and other aggregated information) we’ll need to grab the proper even log source name and populate that in Log Analytics.
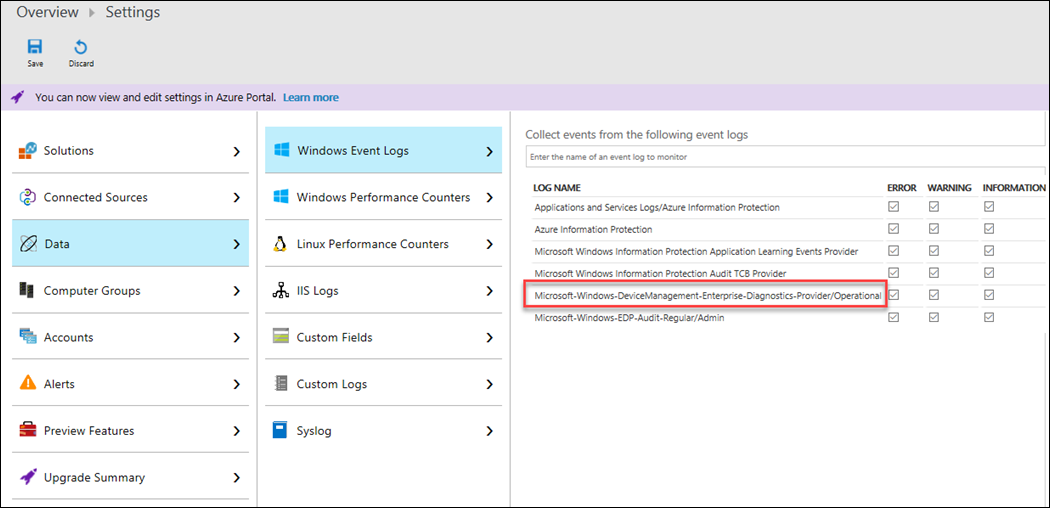
Find and copy the event log source or name: Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider
Paste the event log path in Log Analytics to “Windows Event Logs under Settings > Data > Windows Event Logs” as shown below:
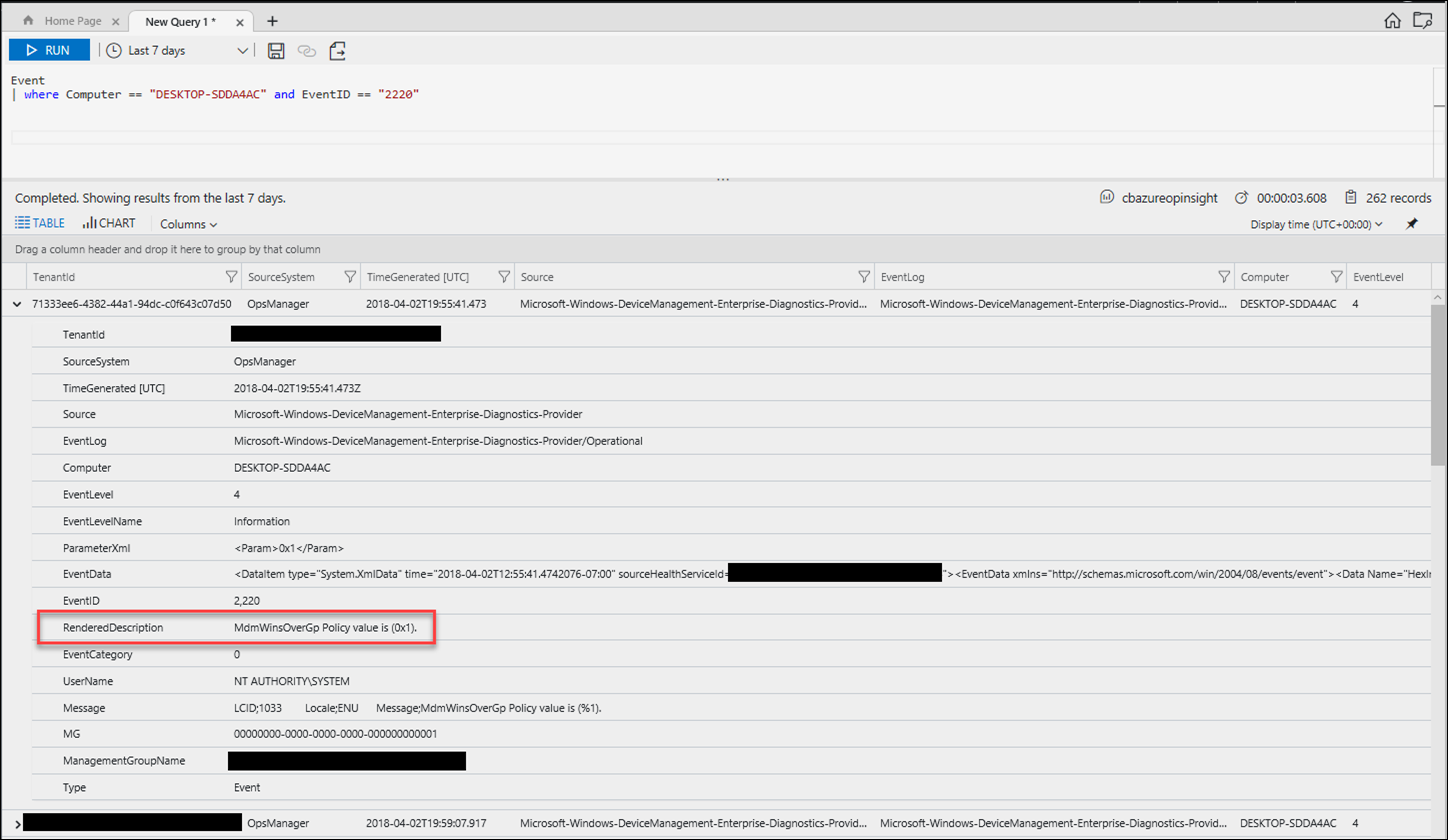
Give the logs a few minutes to sync from the device to OMS, then run the query below in log analytics analyzer and look for the MDMWinsOverGP policy created above:
For more details about Windows 10 MDM logging please visit: /en-us/windows/client-management/mdm/diagnose-mdm-failures-in-windows-10
Evaluating existing Group Policies to determine migration to MDM
Use the MDM Migration Analysis Tool (MMAT) to evaluate which Group Policies have been set for a target user/computer and cross-reference against its built-in list of supported MDM policies.
Download the MDM Migration Analysis Tool (MMAT): https://github.com/WindowsDeviceManagement/MMAT
For additional details about creating custom ADMX policies please view the following two great videos:
Enable ADMX backed policies in Intune: https://www.microsoft.com/en-us/videoplayer/embed/bdc9b54b-11b0-4bdb-a022-c339d16e7121
ADMX backed policy import example: https://www.microsoft.com/en-us/videoplayer/embed/a59888b1-429f-4a49-8570-c39a143d9a73
Keep up to date with MDM policies and other features via What’s new in MDM enrollment and management
That’s it, we’ve learned that there is a new policy added to Windows 10 1803 that will control if MDM policies win over Group Policies (where applicable, not all Group Policies are available via MDM or CSP), how to investigate policies via event viewer, and aggregate those logs using Log Analytics (OMS).