你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
App Service Environment reference for DoD customers connected to the DISA CAP
This article explains the baseline configuration of an App Service Environment (ASE) with an internal load balancer (ILB) for customers who use the Defense Information Systems Agency (DISA) Cloud Access Point (CAP) to connect to Azure Government.
Environment configuration
Assumptions
You've deployed an ASE with an ILB and have implemented an ExpressRoute connection to the DISA CAP.
Route table
When you create the ASE via the Azure Government portal, a route table with a default route of 0.0.0.0/0 and next hop “Internet” is created. However, since DISA advertises a default route out of the ExpressRoute circuit, the User Defined Route (UDR) should either be deleted, or you should remove the default route to Internet.
You'll need to create new routes in the UDR for the management addresses to keep the ASE healthy. For Azure Government ranges, see App Service Environment management addresses.
- 23.97.29.209/32 -> Internet
- 13.72.53.37/32 -> Internet
- 13.72.180.105/32 -> Internet
- 52.181.183.11/32 -> Internet
- 52.227.80.100/32 -> Internet
- 52.182.93.40/32 -> Internet
- 52.244.79.34/32 -> Internet
- 52.238.74.16/32 -> Internet
Make sure the UDR is applied to the subnet your ASE is deployed to.
Network security group (NSG)
The ASE will be created with the following inbound and outbound security rules. The inbound security rules must allow ports 454-455 with an ephemeral source port range (*). The following images describe the default NSG rules generated during the ASE creation. For more information, see Networking considerations for an App Service Environment.
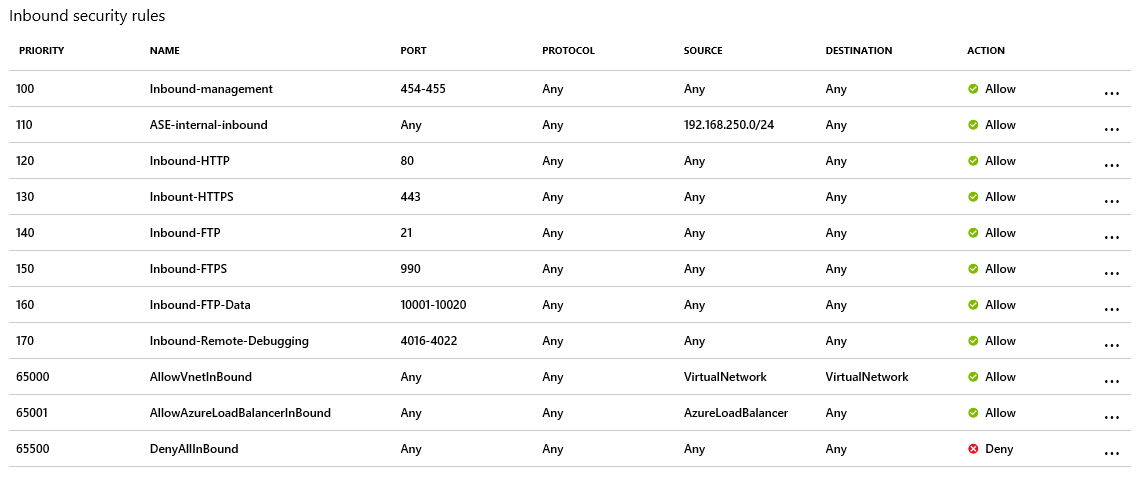
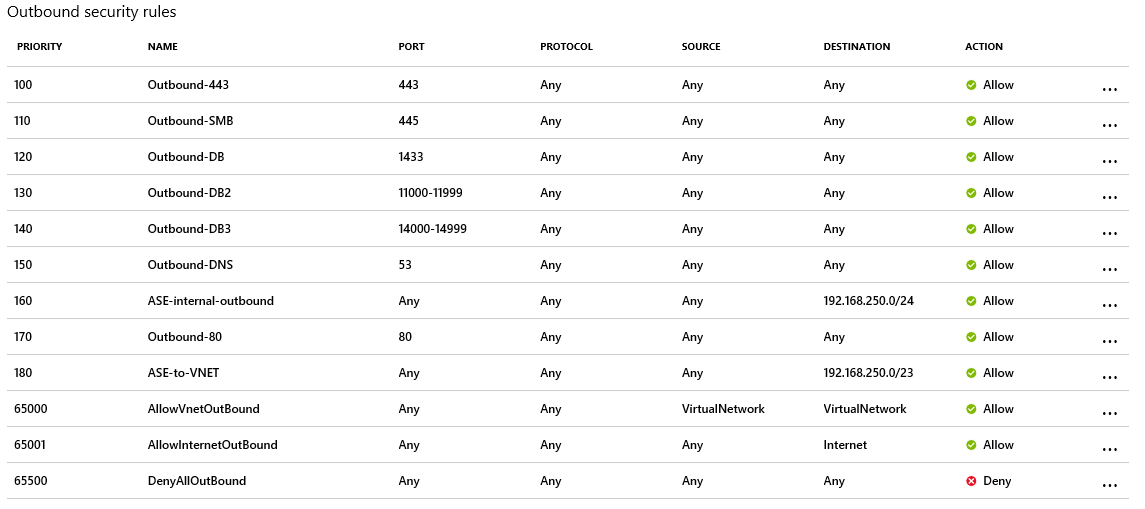
Service endpoints
Depending on the storage you use, you need to enable service endpoints for Azure SQL Database and Azure Storage to access them without going back to the DISA CAP. You also need to enable the Event Hubs service endpoint for ASE logs. For more information, see Networking considerations for App Service Environment: Service endpoints.
FAQs
How long will it take for configuration changes to take effect?
Some configuration changes may take time to become effective. Allow several hours for changes to routing, NSGs, ASE Health, and so on, to propagate and take effect. Otherwise, you can optionally reboot the ASE.
Azure Resource Manager template sample
Note
To deploy non-RFC 1918 IP addresses in the portal, you must pre-stage the VNet and subnet for the ASE. You can use an Azure Resource Manager template to deploy the ASE with non-RFC1918 IPs as well.

This template deploys an ILB ASE into the Azure Government or DoD regions.
Next steps
- Sign up for Azure Government trial
- Acquiring and accessing Azure Government
- Ask questions via the azure-gov tag on StackOverflow
- Azure Government blog
- Azure Government overview
- Azure Government security
- Azure Government compliance
- Secure Azure computing architecture
- Azure Policy overview
- Azure Policy regulatory compliance built-in initiatives
- Azure Government services by audit scope
- Azure Government isolation guidelines for Impact Level 5 workloads
- Azure Government DoD overview