恶意软件名称
我们根据计算机防病毒研究组织 (CARO) 恶意软件命名方案对检测到的恶意软件和不需要的软件进行命名。 方案使用以下格式:
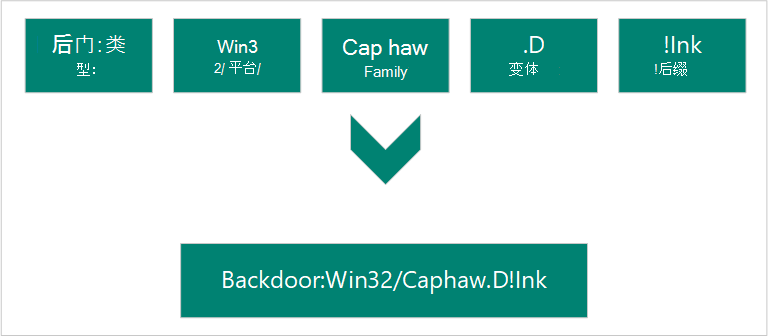
当我们的分析师研究特定威胁时,他们会确定每个组件的名称。
描述恶意软件在计算机上执行的操作。 蠕虫、病毒、特洛伊木马、后门和勒索软件是一些最常见的恶意软件类型。
* Adware
* Backdoor
* Behavior
* BrowserModifier
* Constructor
* DDoS
* Exploit
* HackTool
* Joke
* Misleading
* MonitoringTool
* Program
* Personal Web Server (PWS)
* Ransom
* RemoteAccess
* Rogue
* SettingsModifier
* SoftwareBundler
* Spammer
* Spoofer
* Spyware
* Tool
* Trojan
* TrojanClicker
* TrojanDownloader
* TrojanNotifier
* TrojanProxy
* TrojanSpy
* VirTool
* Virus
* Worm
平台将恶意软件引导到其兼容的操作系统 (,例如 Windows、macOS 和 Android) 。 平台指南还用于编程语言和文件格式。
* AndroidOS: Android operating system
* DOS: MS-DOS platform
* EPOC: Psion devices
* FreeBSD: FreeBSD platform
* iOS: iPhone operating system
* Linux: Linux platform
* macOS: MAC 9.x platform or earlier
* macOS_X: macOS X or later
* OS2: OS2 platform
* Palm: Palm operating system
* Solaris: System V-based Unix platforms
* SunOS: Unix platforms 4.1.3 or lower
* SymbOS: Symbian operating system
* Unix: general Unix platforms
* Win16: Win16 (3.1) platform
* Win2K: Windows 2000 platform
* Win32: Windows 32-bit platform
* Win64: Windows 64-bit platform
* Win95: Windows 95, 98 and ME platforms
* Win98: Windows 98 platform only
* WinCE: Windows CE platform
* WinNT: WinNT
* ABAP: Advanced Business Application Programming scripts
* ALisp: ALisp scripts
* AmiPro: AmiPro script
* ANSI: American National Standards Institute scripts
* AppleScript: compiled Apple scripts
* ASP: Active Server Pages scripts
* AutoIt: AutoIT scripts
* BAS: Basic scripts
* BAT: Basic scripts
* CorelScript: Corelscript scripts
* HTA: HTML Application scripts
* HTML: HTML Application scripts
* INF: Install scripts
* IRC: mIRC/pIRC scripts
* Java: Java binaries (classes)
* JS: JavaScript scripts
* LOGO: LOGO scripts
* MPB: MapBasic scripts
* MSH: Monad shell scripts
* MSIL: .NET intermediate language scripts
* Perl: Perl scripts
* PHP: Hypertext Preprocessor scripts
* Python: Python scripts
* SAP: SAP platform scripts
* SH: Shell scripts
* VBA: Visual Basic for Applications scripts
* VBS: Visual Basic scripts
* WinBAT: Winbatch scripts
* WinHlp: Windows Help scripts
* WinREG: Windows registry scripts
* A97M: Access 97, 2000, XP, 2003, 2007, and 2010 macros
* HE: macro scripting
* O97M: Office 97, 2000, XP, 2003, 2007, and 2010 macros - those that affect Word, Excel, and PowerPoint
* PP97M: PowerPoint 97, 2000, XP, 2003, 2007, and 2010 macros
* V5M: Visio5 macros
* W1M: Word1Macro
* W2M: Word2Macro
* W97M: Word 97, 2000, XP, 2003, 2007, and 2010 macros
* WM: Word 95 macros
* X97M: Excel 97, 2000, XP, 2003, 2007, and 2010 macros
* XF: Excel formulas
* XM: Excel 95 macros
* ASX: XML metafile of Windows Media .asf files
* HC: HyperCard Apple scripts
* MIME: MIME packets
* Netware: Novell Netware files
* QT: Quicktime files
* SB: StarBasic (StarOffice XML) files
* SWF: Shockwave Flash files
* TSQL: MS SQL server files
* XML: XML files
基于共同特征(包括归因到同一作者)对恶意软件进行分组。 安全软件提供商有时对同一恶意软件系列使用不同的名称。
按顺序用于恶意软件系列的每个不同版本。 例如,变体“.AF”的检测将在检测变体“之后创建。AE”。
提供有关恶意软件的额外详细信息,包括将其用作多组件威胁的一部分的方式。 在前面的示例中, “!lnk” 指示威胁组件是 Trojan 使用的快捷方式文件: Win32/Reveton.T。
* .dam: damaged malware
* .dll: Dynamic Link Library component of a malware
* .dr: dropper component of a malware
* .gen: malware that is detected using a generic signature
* .kit: virus constructor
* .ldr: loader component of a malware
* .pak: compressed malware
* .plugin: plug-in component
* .remnants: remnants of a virus
* .worm: worm component of that malware
* !bit: an internal category used to refer to some threats
* !cl: an internal category used to refer to some threats
* !dha: an internal category used to refer to some threats
* !pfn: an internal category used to refer to some threats
* !plock: an internal category used to refer to some threats
* !rfn: an internal category used to refer to some threats
* !rootkit: rootkit component of that malware
* @m: worm mailers
* @mm: mass mailer worm