I'm glad that support team was able to resolve your issue and thank you for posting your solution so that others experiencing the same thing can easily reference this! Since the Microsoft Q&A community has a policy that "[The question author cannot accept their own answer. They can only accept answers by others] (https://learn.microsoft.com/en-us/answers/support/accepted-answers#why-only-one-accepted-answer)", I'll repost your solution in case you'd like to "[Accept] (https://learn.microsoft.com/en-us/answers/support/accepted-answers#accepted-answer-in-a-question-thread)" the answer.
Answered by @Benard Mwanza
Below is the summary of few things he did to fix.
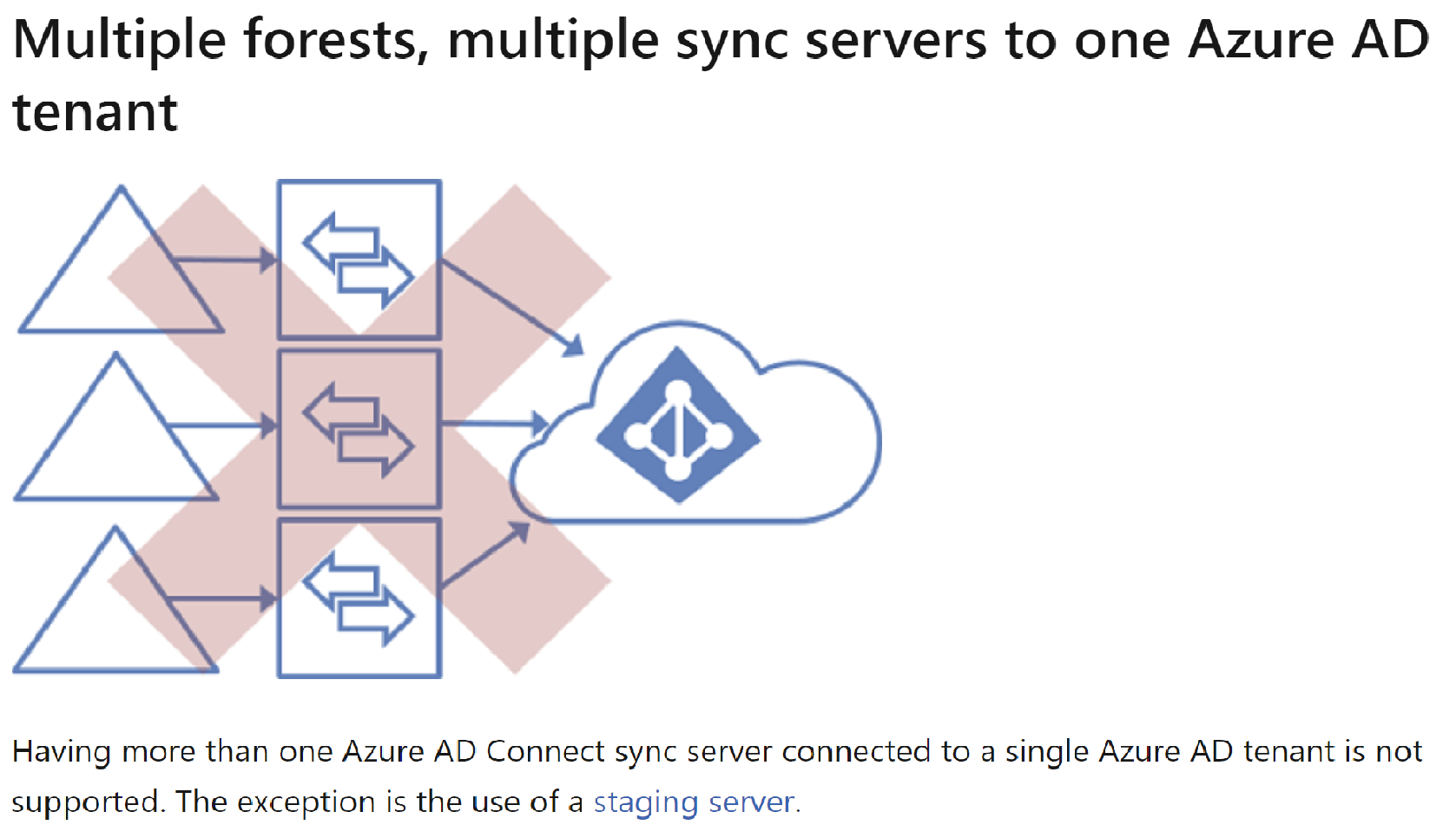
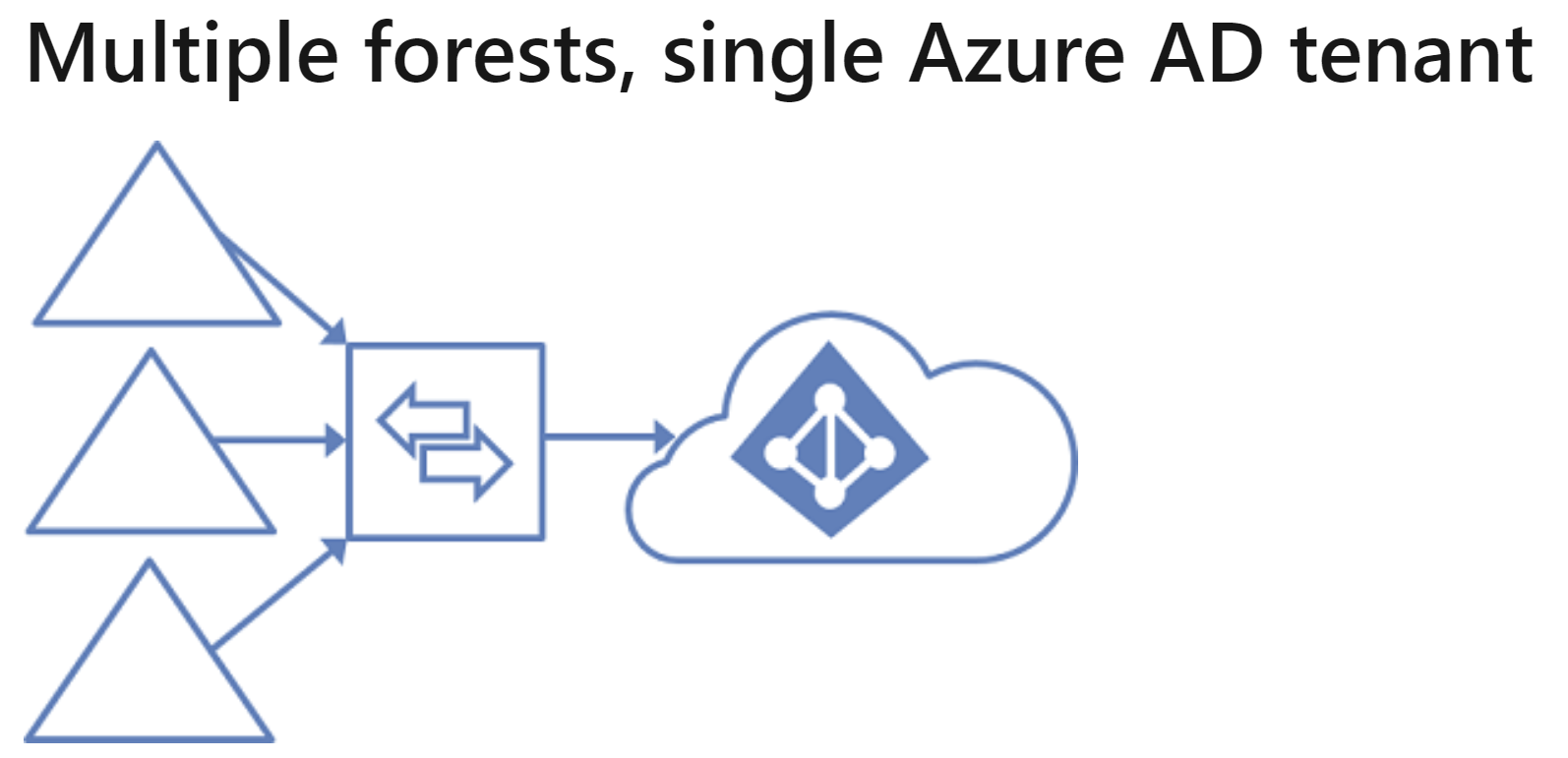
Configured a single AD connect server to synchronize objects from the three forests. Uninstalled the other two connect servers.
The AD connect server was not using TLS 1.2, so we enabled that first (required a reboot).
https://learn.microsoft.com/en-us/azure/active-directory/hybrid/reference-connect-tls-enforcement
Added MFA exception for the Azure AD connector account, this was done via conditional access policy as there was existing conditional access policies in place that requires all users to verify MFA before connecting to M365.
Reset the Azure AD connector account password, he pulled the link below.
https://learn.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-azureadaccount
Reset the password for Microsoft azure AD sync service logon account (NT SERVICE\ADSync) inside the AD connect
server (simply remove the existing password>choose to apply>Ok & then start the service).
I got to learn that synced GL administrator accounts cannot reset password using SSPR with password writeback. It's not supported
https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-sspr-writeback#unsupported-writeback-operations
Normal synced users are able to reset their passwords using sspr service with password writeback. This worked fine at the end.