Hello @Denis Dal Molin ,
Thanks for posting your query on Microsoft Q&A. PDB answers to your ask as follows:
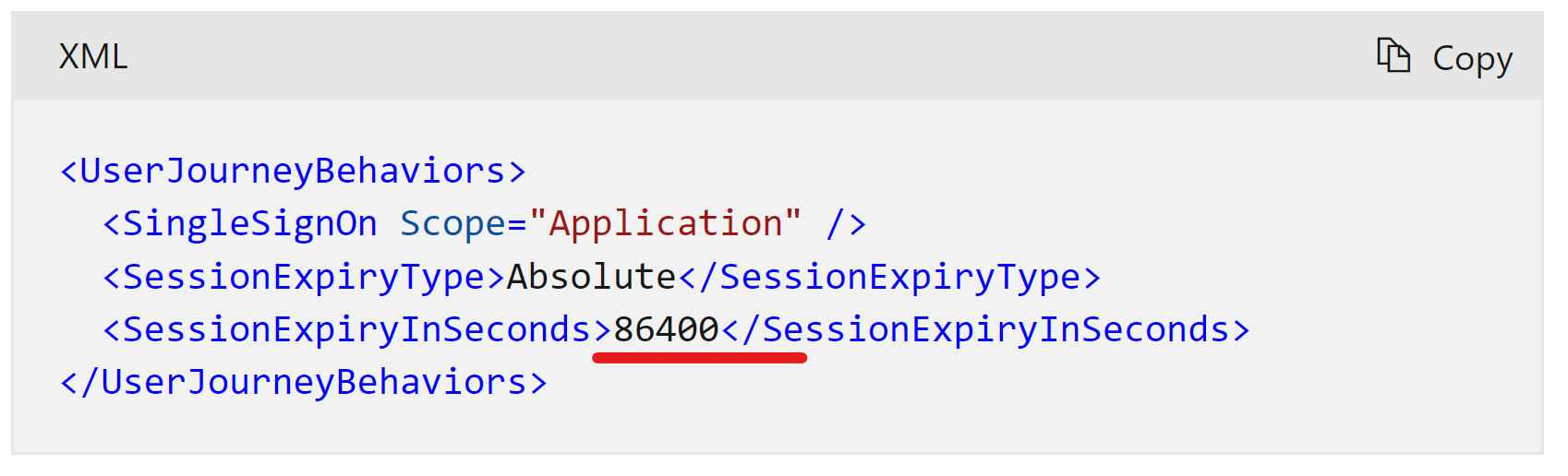
- Control the token lifetime (SAML) and session duration
To define a session duration for SAML you could use "TokenLifeTimeInSeconds" in Saml2AssertionIssuer technical profile metadata.
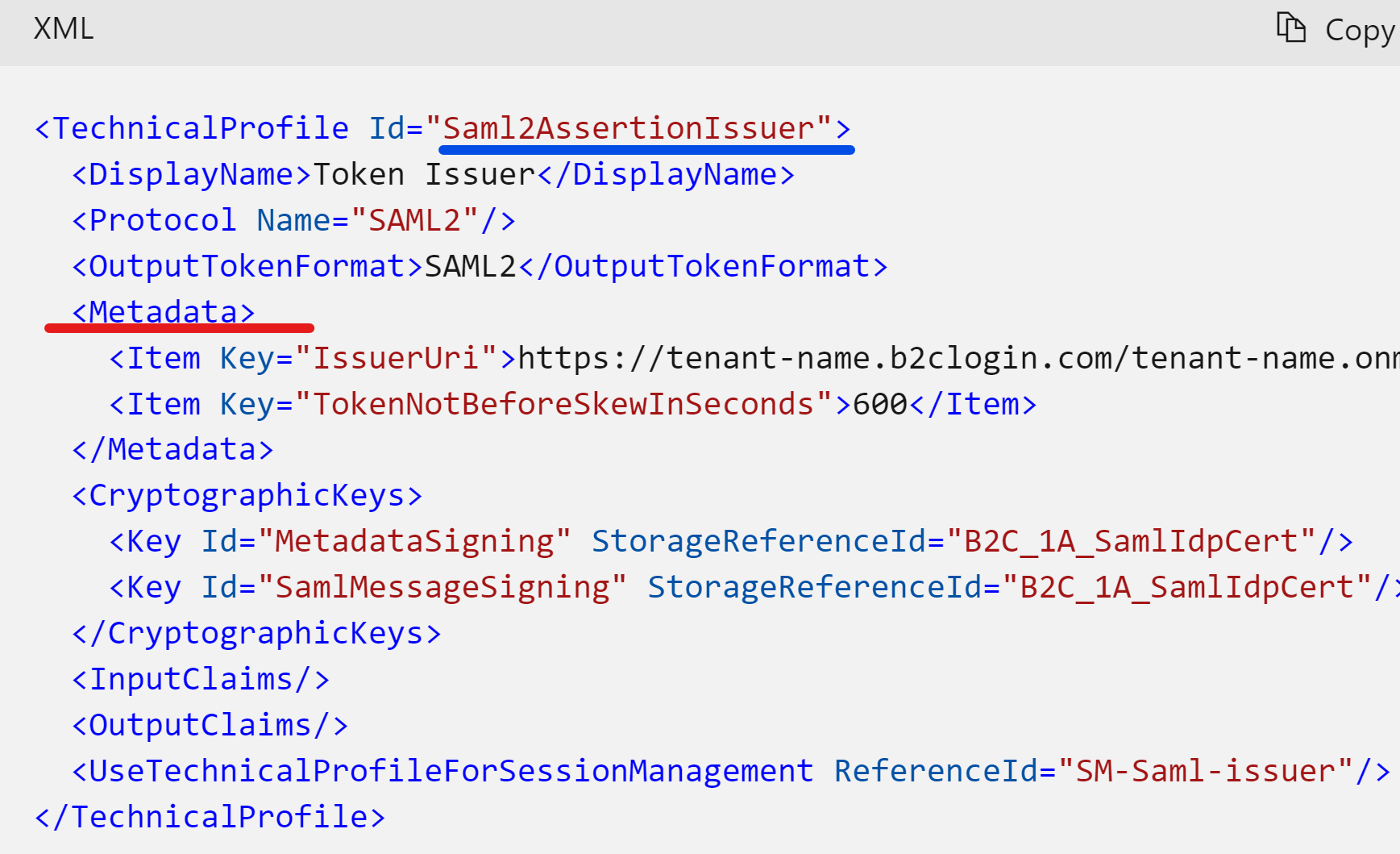
As per https://learn.microsoft.com/en-us/azure/active-directory-b2c/saml-issuer-technical-profile#metadata TokenLifeTimeInSeconds specifies the life of the SAML Assertion. This value is in seconds from the NotBefore value referenced above. The default value is 300 seconds (5 Min).
When a user successfully authenticates with a local or social account, Azure AD B2C stores a cookie-based session on the user's browser. The cookie is stored under the Azure AD B2C tenant domain name, such as https://contoso.b2clogin.com.
From an application's perspective, the validity period of the token is specified by the NotOnOrAfter value of the <conditions …> element in the token. After the validity period of the token has ended, the client must initiate a new authentication request, which will often be satisfied without interactive sign in as a result of the Single Sign On (SSO) Session token.
The token is used to initialize a session to the user and is used for as long as the session has not expired. The 'NotOnOrAfter' attribute of the token isn't checked, only if a new session needs to be created the 'NotOnOrAfter' value of the token is checked.
So, a user that is actively using the site will never lose his session but with the current way they use progress once the expiration of the token took place, the user loses access to the system and needs to sign in again.
I would like if the user closed the browser without logging out, when reopened it will prompt for credentials
This could be achieved for local accounts only by removing /excluding Keep me signed in (KMSI) claim, when you enable the feature, users can opt to stay signed in, so the session remains active after they close the browser. The reference sample could be found https://github.com/azure-ad-b2c/unit-tests/blob/main/session/Session_KeepAliveInDays.xml
Also, the SAML IDP metadata should have ForceAuthN set to true
Passes the ForceAuthN value in the SAML authentication request to determine if the external SAML IDP will be forced to prompt the user for authentication. By default, Azure AD B2C sets the ForceAuthN value to false on initial login. If the session is then reset (for example by using the prompt=login in OIDC) then the ForceAuthN value will be set to true. Setting the metadata item as shown below will force the value for all requests to the external IDP. Possible values: true or false. Ref: https://learn.microsoft.com/en-us/azure/active-directory-b2c/saml-identity-provider-technical-profile#metadata
Please do let me know if you have any further queries for me in the comments section.
Thanks,
Akshay Kaushik
Please "Accept the answer", "Upvote" and rate your experience if the suggestion works as per your business need. This will help us and others in the community as well.