I have solved by using custom action.
// added Custome Rules
custom_rules { name = "allowaspNetCoreCookie"
priority = 25
rule_type = "MatchRule"
match_conditions
{ match_variables
{ variable_name = "RequestHeaders"
selector = "Cookie"}
operator = "StartsWith"
negation_condition = false
match_values = [".AspNetCore.OpenIdConnect."]
}
action = "Allow"
}
WAF exclusion Rule for cookie name

I am using WAF and creating exclusion Rule. I wanted the exclude the aspnet openid connect cookie as cookie name itself is violating's the WAF rule. based on the documentation I think WAF exclusion work son value not on the name . please suggest Warning. Pattern match \"(/\*!?|\*/|[';]--|--[\s\r\n\v\f]|(?:--[^-]?-)|([^\-&])#.?[\s\r\n\v\f]|;?\x00)\" at REQUEST_COOKIES_NAMES
.AspNetCore.OpenIdConnect.Nonce.CfDJ8By4xDotf-JCnJS9BHH__BdvvJNm8WXFRbFcr_D65PUBazmnXcJkPvNQCra4aguO1TCLHdCmZ0liD9mgNBbAg--tqwE2hMio7BLj2Mu3J7UQKMBg2_vbaNJzGTAciiAOQaCQZc4dCDCN5nCf3bP3YU2Zis9Njk-BcF95mxaubrKWl3-EdW9BmdY9Avxc2PMIhr ....
https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/application-gateway-waf-configuration#waf-exclusion-lists
I am writing the exclusion rule like this.
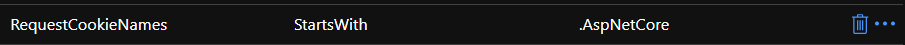
-
 Somnath Shukla 411 Reputation points
Somnath Shukla 411 Reputation points2021-05-27T12:13:02.507+00:00
1 additional answer
Sort by: Most helpful
-
 GitaraniSharma-MSFT 47,676 Reputation points Microsoft Employee
GitaraniSharma-MSFT 47,676 Reputation points Microsoft Employee2021-05-27T09:36:03.747+00:00 Hello @Somnath Shukla ,
As mentioned in this article, the values of the chosen field aren't evaluated against WAF rules, but their names still are, which means the exclusion rules only exclude the checking of a cookie's value, not of its name.
I found similar issue reported here : https://github.com/dotnet/aspnetcore/issues/4589
You could try adding the list of exclusion rules provided in the additional context on this issue.
There is a user voice feedback raised in the following forum for this which you could upvote in case you are facing similar issue: https://feedback.azure.com/forums/217313-networking/suggestions/36260122-web-application-firewall-cookie-exclusions-only-exFor more information, please refer : https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/web-application-firewall-troubleshoot#using-an-exclusion-list
Request you to have a look into these and in the meantime, I will check with the Azure WAF PG team to see if they can provide some insights on same.
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.