Hi @Sateesh Kumar Sharma • Thank you for reaching out.
As of now, B2C applications do not support graph operations. This means if you register an app in the B2C tenant using the option highlighted below, you won't be able to perform any graph operations using that app.
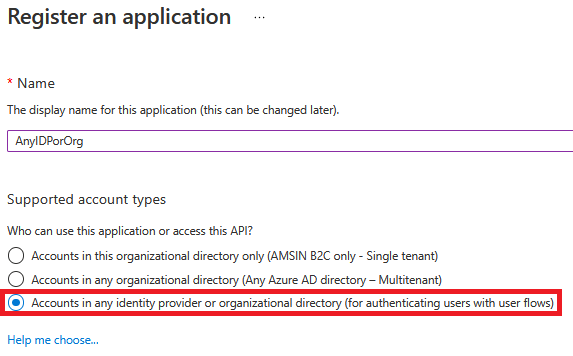
Reason: In your case, you need these Permissions to register applications but if you go to the API permissions blade of your application, you won't see these permissions and only openID and offline_access are the available permissions, as shown below:
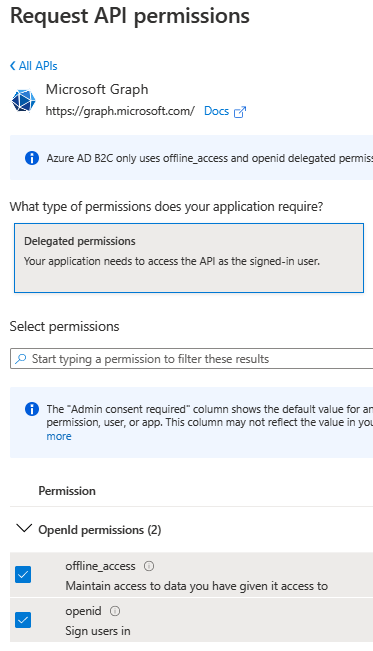
Currently, you can use the standard Azure AD functionality of B2C tenant for this purpose.
- Register the application using any of the first two options (single tenant or multitenant app)
- In the application, grant admin consent to these Permissions
- Acquire access token using below parameters, and use the token as bearer token to register the applications via graph api. POST https://login.microsoftonline.com/your_tenant.onmicrosoft.com/oauth2/v2.0/token client_id:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
grant_type:password
scope:https://graph.microsoft.com/.default
username:username@your_tenant.onmicrosoft.com
password:********
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.