Hello, I'm working on azure cspm integration for a client. Had few checks for which I couldn't figure out the endpoints with respect to my code. Since, it is for my client, I can't really mention the name of the storage account in the code. Rather retrieve it from the json data. So, I was given few checks to code:
- Ensures file shares do not allow full write delete or read ACL permissions
- Ensures tables do not allow full write delete or read ACL permissions
- Ensures queues do not allow full write delete or read ACL permissions
- Ensures that the Activity Log Container does not have public read access
Now, the first query is.. How do I access file service's ACL permissions from the Azure Portal? Cuz I was not able to figure that out.
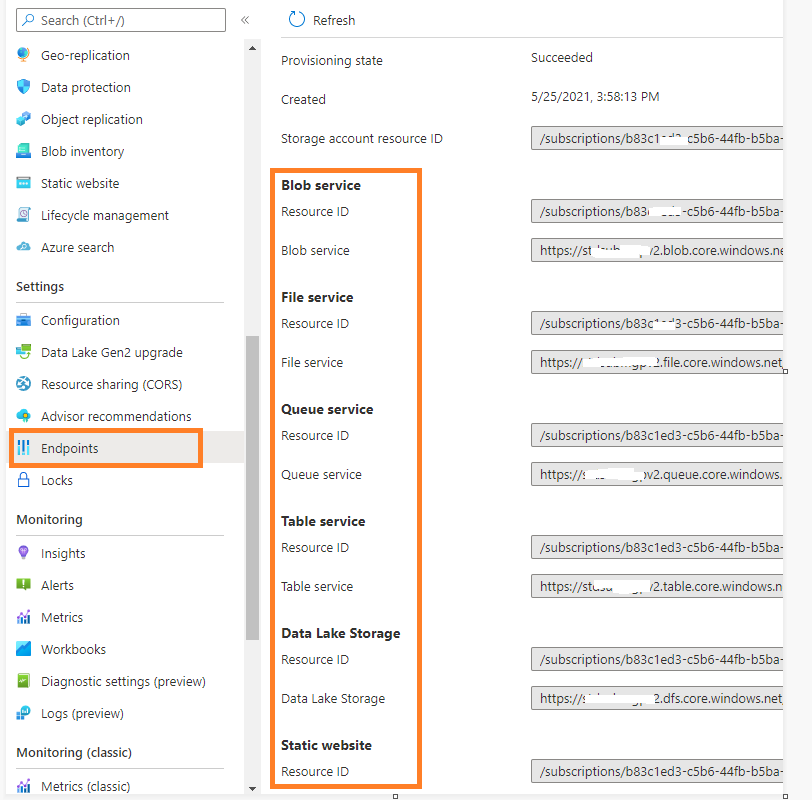
Secondly, what are the endpoints where the data is stored for files, tables and queue ACL permissions?
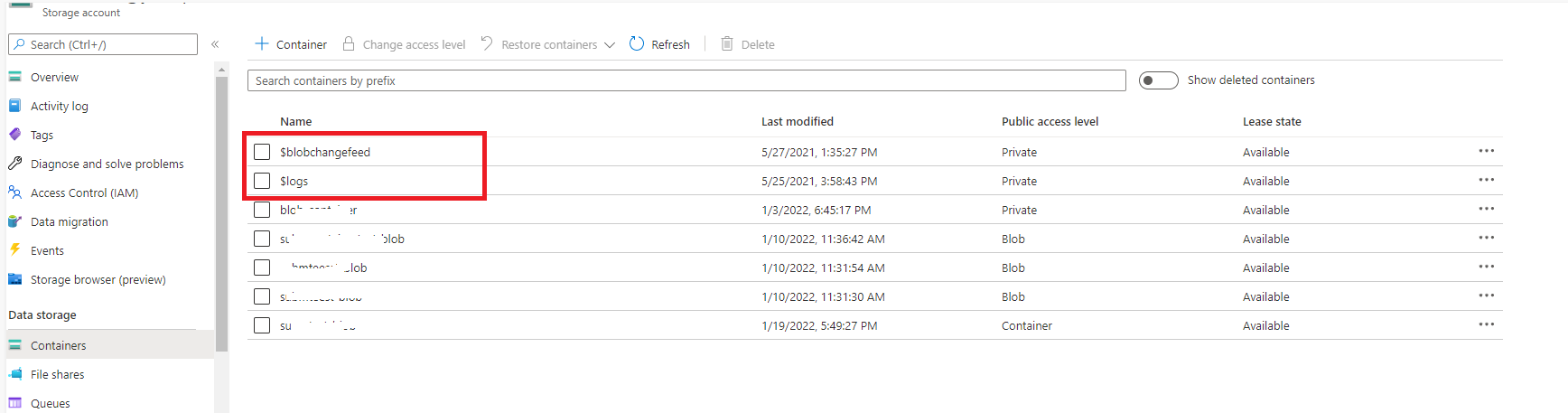
Third, what is the endpoint where I can find if the log container has public access or not?
Here's my code for reference... Please help me out with the endpoint with respect to the code.
import http.client
import json
import requests
def get_token():
r = requests.post("https://login.microsoftonline.com/TenantID/oauth2/token",data={"grant_type": "client_credentials", "client_secret": "xxxxxxxxxx ","client_id": "xxxxxxxxxxxx", "resource": "https://management.azure.com"})
ret_body = r.json()
return ret_body['access_token']
token = get_token()
headers = {'Authorization': 'Bearer ' + token}
conn = http.client.HTTPSConnection('management.azure.com')
conn.request("GET", '/subscriptions/SubscriptionID/providers/Microsoft.Storage/storageAccounts?api-version=2019-06-01', "", headers)
response = conn.getresponse()
data = response.read()
data = data.decode('utf-8')
data = json.loads(data)
#print(data)
def get_storage_acc_details():
storage_accounts_list = []
for storage_info in data["value"]:
storage = {}
#Storage Accounts
storage["resource_type"] = 'storage_accounts'
storage["resource_name"] = storage_info['name']
storage["resource_id"] = storage_info['id']
try:
if storage_info['properties']["encryption"]["services"]["file"]["enabled"] == True:
storage['is_file_encrypted'] = 1
else:
storage['is_file_encrypted'] = 0
except:
storage['is_file_encrypted'] = 0
try:
if storage_info["properties"]["encryption"]["services"]["blob"]["enabled"] == True:
storage['is_storage_encrypted'] = 1
else:
storage['is_storage_encrypted'] = 0
except:
storage['is_storage_encrypted'] = 0
try:
if storage_info['properties']['supportsHttpsTrafficOnly'] == True:
storage['is_https_traffic_allowed'] = 1
else:
storage['is_https_traffic_allowed'] = 0
except:
storage['is_https_traffic_allowed'] = 0
try:
if storage_info['properties']["encryption"]["keyvaultproperties"]:
storage["is_blob_encryption_configured"] = 1
else:
storage["is_blob_encryption_configured"] = 0
except:
storage["is_blob_encryption_configured"] = 0
try:
storage["is_AAD_domain_enabled"] = storage_info["properties"]["azureFilesIdentityBasedAuthentication"]
if storage_info["properties"]["azureFilesIdentityBasedAuthentication"]["directoryServiceOptions"] == "AADDS":
storage["is_AAD_domain_enabled"] = 1
else:
storage["is_AAD_domain_enabled"] = 0
except:
storage["is_AAD_domain_enabled"] = 0
try:
if storage_info["properties"]["networkAcls"]["bypass"] == "AzureServices":
storage["is_MsService_enabled"] = 1
else:
storage["is_MsService_enabled"] = 0
except:
storage["is_MsService_enabled"] = 0
try:
if storage_info['properties']["encryption"]["keyvaultproperties"]:
storage["is_BYOK_enabled"] = 1
else:
storage["is_BYOK_enabled"] = 0
except:
storage["is_BYOK_enabled"] = 0
network_access_list = storage_info["properties"]["networkAcls"]["virtualNetworkRules"]
if (network_access_list):
try:
for network_info in network_access_list:
if network_info["action"] == 'Allow':
storage["trusted_network_access"] = 1
else:
storage["trusted_network_access"] = 0
except:
storage["trusted_network_access"] = 0
else:
storage["trusted_network_access"] = 0
#Blob Service
conn = http.client.HTTPSConnection('management.azure.com')
conn.request("GET", '/' + storage["resource_id"] + '/blobServices/default?api-version=2019-06-01', "", headers)
response = conn.getresponse()
blob_data = response.read()
blob_data = blob_data.decode('utf-8')
blob_data = json.loads(blob_data)
storage["blob_name"] = blob_data["name"]
storage["blob_id"] = blob_data["id"]
try:
if blob_data['properties']["deleteRetentionPolicy"]["enabled"] == True:
storage['is_soft_delete_enabled'] = 1
else:
storage['is_soft_delete_enabled'] = 0
except:
storage['is_soft_delete_enabled'] = 0
#Blob Container
conn = http.client.HTTPSConnection('management.azure.com')
conn.request("GET", '/' + storage["resource_id"] + '/blobServices/default/containers?api-version=2019-06-01', "", headers)
response = conn.getresponse()
blob_container_data = response.read()
blob_container_data = blob_container_data.decode('utf-8')
blob_container_data = json.loads(blob_container_data)
for container_info in blob_container_data["value"]:
storage["container_name"] = container_info["name"]
storage["container_id"] = container_info["id"]
try:
if container_info["properties"]["immutableStorageWithVersioning"]["enabled"] == True:
storage["is_immutability_configured"] = 1
else:
storage["is_immutability_configured"] = 0
except:
storage["is_immutability_configured"] = 0
try:
if container_info["properties"]["publicAccess"] == "None":
storage["container_no_public_access"] = 1
else:
storage["container_no_public_access"] = 0
except:
storage["container_no_public_access"] = 0
storage_accounts_list.append(storage)
#print(storage_accounts_list)
get_storage_acc_details()
 and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.
and “up-vote” wherever the information provided helps you, this can be beneficial to other community members. 
 and
and  wherever the information provided helps you, this can be beneficial to other community members.
wherever the information provided helps you, this can be beneficial to other community members.