Hi @Aleks Vujić ,
Thanks for reaching out.
I understand you are looking to configure your applications to allow to send e-mails without user context using the Microsoft Graph.
How should I configure "App registration" inside Azure portal for our use case (daemon background process)?
For any kind of application, registering the application is quite similar. For background processes as well, you can register the application by navigating to Azure Active Directory->App Registrations->New Registration
Name: Name of your application you want to choose
Type: Accounts in this organizational directory only (Single tenant) or based on scenario if there is multi tenant organization.
Redirect URI: Not required.
Create a client secret and store the value of secret at safe location.
Copy the ClientId, TenantId and ClientSecret which is needed to configure the appliciation.
We should use https://graph.microsoft.com/SMTP.Send scope, right?
For background processes, where there is no user interaction required, we need to set up application permission rather than delegated permissions.
You need to add Mail.Send permission as application permission to call send Mail API.
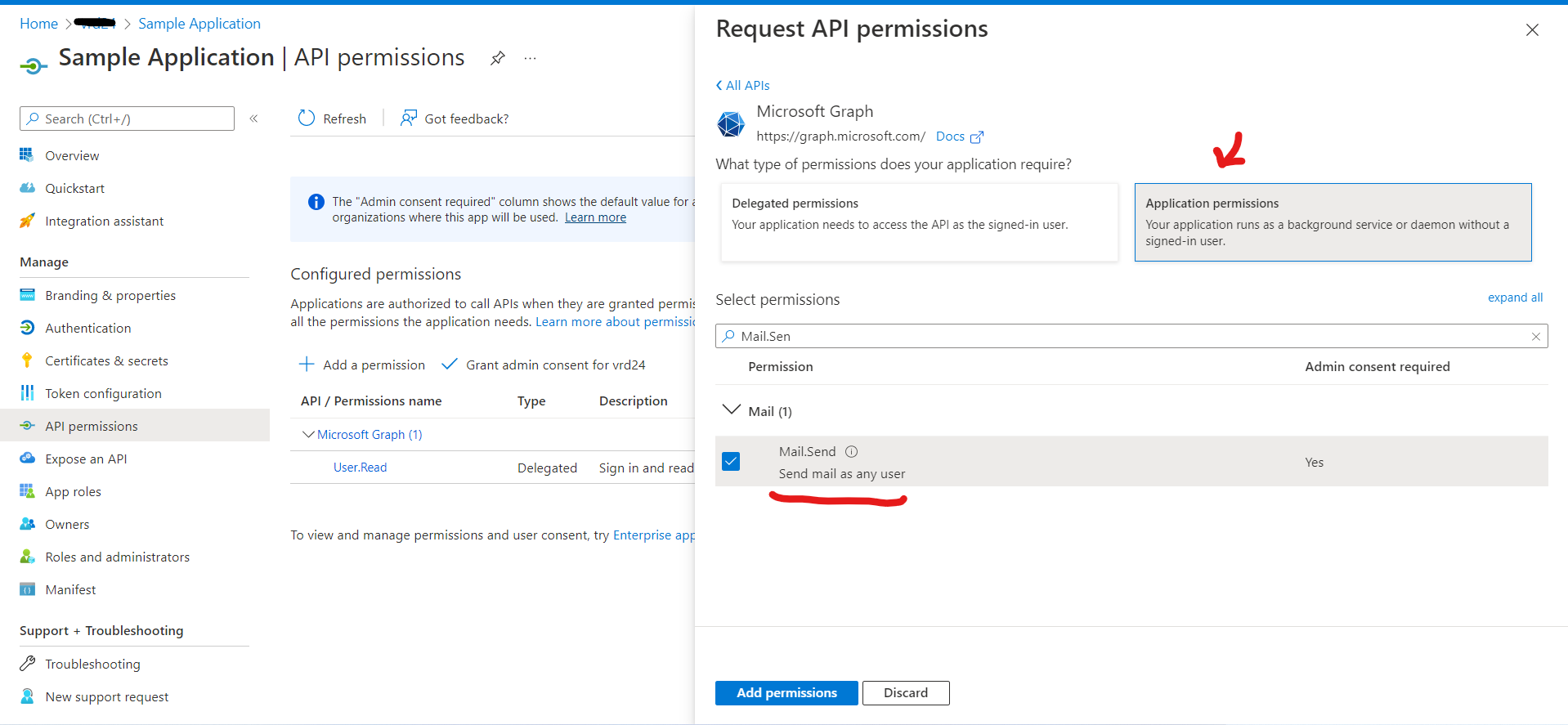
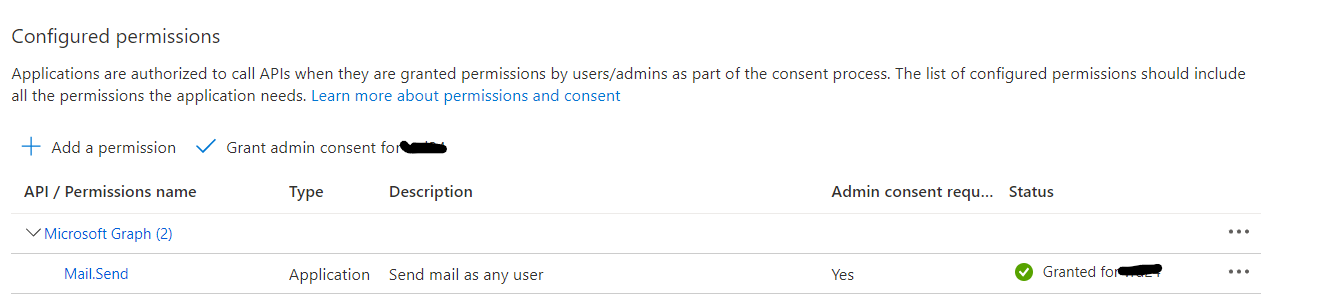
You need to grant admin consent for application permissions by clicking on "Grant Admin Consent for <yourTenant>".
Note: You do not require any third-party relay service like SMTP when you are using Graph API to send emails.
How should I handle the tokens inside .NET Core application? I assume that there should be some kind of never-expiring(?) refresh_token which can be used to retrieve new access_token when it expires?
Microsoft Authentication Library (MSAL) provide many ways to acquire and handle the token based on the application type. Client credential flow is used to acquire the token for daemon applications and maintain a token cache which is capable to refresh the token while acquire the token silently.
Once you will be able to get the access token. You can use GraphServiceClient to send message using sendMail endpoint.
GraphServiceClient graphClient = new GraphServiceClient( authProvider );
var message = new Message
{
Subject = "Meet for lunch?",
Body = new ItemBody
{
ContentType = BodyType.Text,
Content = "The new cafeteria is open."
},
ToRecipients = new List<Recipient>()
{
new Recipient
{
EmailAddress = new EmailAddress
{
Address = "fannyd@Company portal .onmicrosoft.com"
}
}
},
CcRecipients = new List<Recipient>()
{
new Recipient
{
EmailAddress = new EmailAddress
{
Address = "danas@Company portal .onmicrosoft.com"
}
}
}
};
var saveToSentItems = false;
await graphClient.Me
.SendMail(message,saveToSentItems)
.Request()
.PostAsync();
Since EmailService will be a long-running process it should follow the principle: "configure once, work automatically from then on".
MSAL manages the token silently and cache the token which also refresh the token when token is about to expire to maintain the session thoroughly.
Hope this will help.
Thanks,
Shweta
----------------------------------------
Please remember to "Accept Answer" if answer helped you.

