We are migrating our PowerShell scripts away from legacy auth and moving to use a Service principal and Certificate Based Authentication in our unattended PowerShell scripts.
We can successfully connect to Exchange Online and run all of our scripts as we could with legacy authentication. The problem comes when we connect to the Security & Compliance Center PowerShell module. We can connect fine (Connect-IPPSession -appID xxx -certificateThumbprint xxx) but the problem is assigning correct permissions to the Service Principal to enable us to perform Exchange Compliance Searches.
New-ComplianceSearch --> Command completes OK
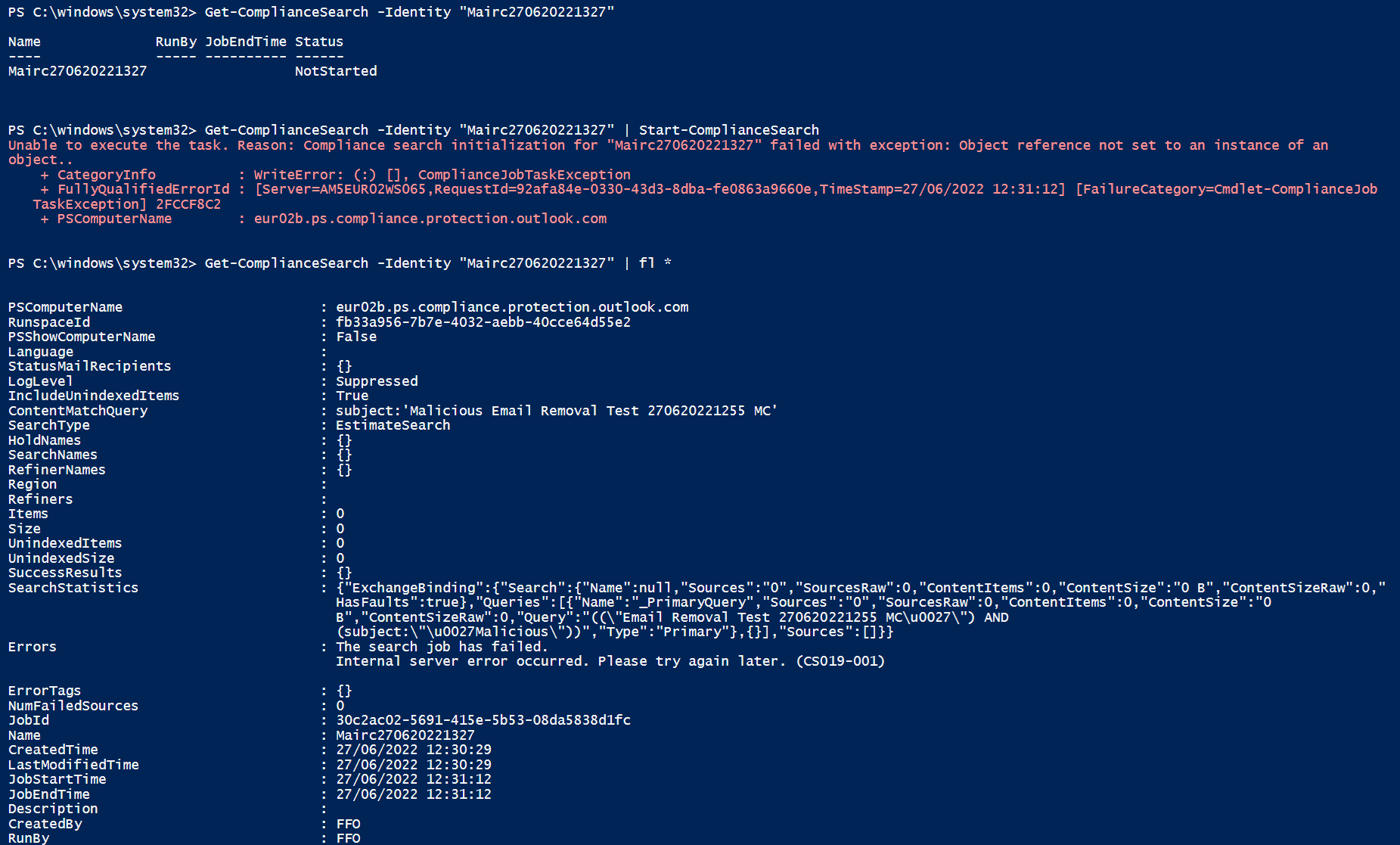
Start-ComplianceSearch --> Error
New-ComplianceSearchAction --> Error
Unable to execute the task. Reason: Compliance search initialization for "Search Name" failed with exception: Object reference not set to an instance of an object.
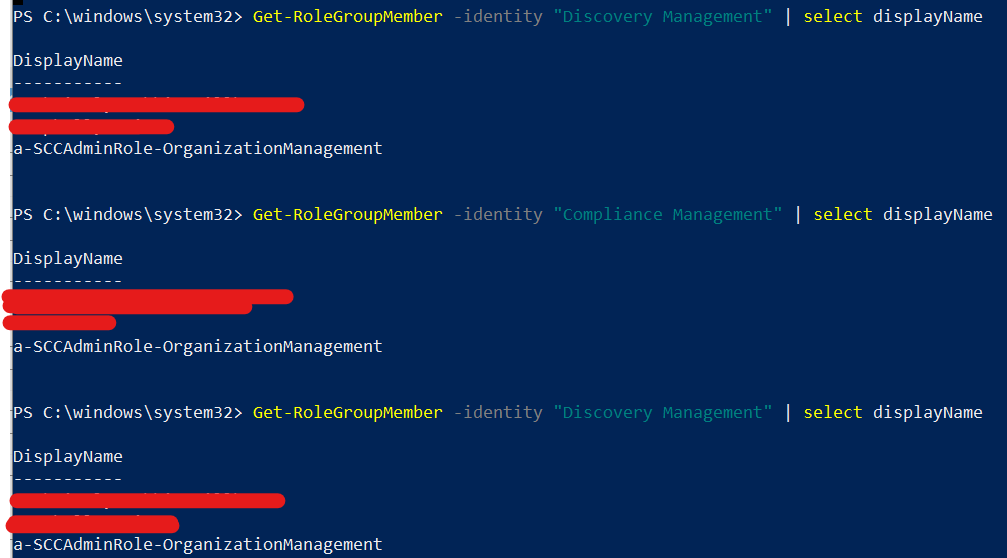
I suspect the error is because the Service Principal is not a member of Organization Management, Discovery Manager or Compliance Management in the compliance center. However, unlike the Azure AD Admin roles we cannot add a service prinicpal to the compliance center admin roles.
I added the Service Principal as a Global Admin in Azure AD to test if that would fix but the error continued.
Is there a way to run Start-ComplianceSearch command as a Service Principal in an unattended PowerShell script? Is there an equivalent to this command in Microsoft Graph?
UPDATE: For anyone encountering this, adding Service Principals to custom roles in SCC is now supported via Power Shell. See: https://learn.microsoft.com/en-gb/powershell/exchange/app-only-auth-powershell-v2?view=exchange-ps#assign-custom-role-groups-to-the-application-using-service-principals