This resolved my problem after troubleshooting for 3 weeks. Thanks
"On Windows Server 2019 with NPS role installed, open an admin command prompt & run the following command:"
1.sc sidtype IAS unrestricted
2.Reboot the server
3.Attempt the connection
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Because there were too many confusions by some moderators and other people, I read on other different pages with the same given solution to the problem to authenticate through NPS.
On that server for Windows Server 2019, open Command and type the following:
After a success message, restart the server.
I was able to authenticate through my phone, but my laptop didn't except through VPN on the second server from this one.
This resolved my problem after troubleshooting for 3 weeks. Thanks
"On Windows Server 2019 with NPS role installed, open an admin command prompt & run the following command:"
1.sc sidtype IAS unrestricted
2.Reboot the server
3.Attempt the connection
SSTP is back up. I enabled TLS 1.2 before uninstalling and reinstalling RRAS in Server 2019 VPN. But L2TP has a processing error. L2TP and SSTP works on Server 2016 with no bugs. (One running NPS and other running VPN both on Server 2016)
Overall, The bugs are in Server 2019 for NPS (Windows 10 computers cannot connect, even Windows 10 Mobile)
The NPS and VPN will work correctly in Server 2016. There are some defects in Server 2019

Hi ,
From your screenshot, VPN and DC are installed on the same machine? We did not recommend install VPN and DC on the same machine.
Let's sort out the current problem. Based on my understanding, your issue is that WIFI authentication for windows machine not work with NPS server 2019. Is that right? Please feel free to let me know if my understanding is wrong. If yes, please refer to the following steps:
Best Regards,
Candy

Did you mean run the command of sc sidtype IAS unrestricted and restart the NPS server still doesn't work?
It might be that the default Windows firewall rules to allow inbound UDP port 1812 (RADIUS authentication) and inbound UDP port 1813 (RADIUS accounting) on NPS server do not work.
To do the troubleshooting, you can enable firewall logging on the NPS server to log both allowed and dropped packets. Attempt VPN connection and observe the firewall logs. Then you might see the firewall is dropping packets inbound on UDP port 1812, as the picture below:
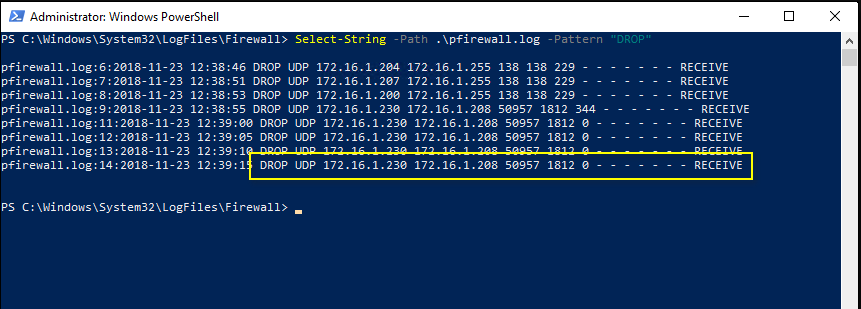
Run the command on the NPS server side:
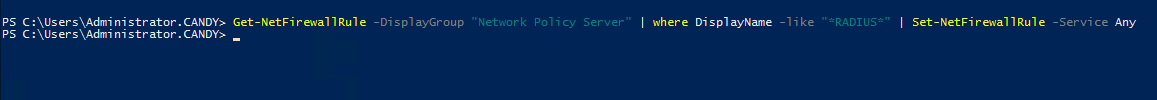
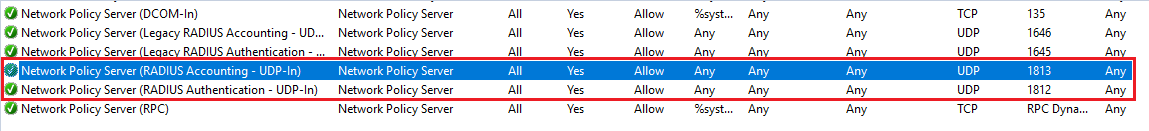
For (Get-NetFirewallRule -DisplayGroup "Network Policy Server" | where DisplayName -like "RADIUS" | Set-NetFirewallRule -Service Any), what do I do for this phrase? Do I go to firewall? I need a breakdown on how to do this. I did the command part already with (sc sidtype IAS unrestricted)
Also Is the port for 1812 and 1813 on server side or client side? Does TLS need to be enabled?
Also as an idea, if someone can compare both server setting, they can find out what's really going on with Server 2019