إشعار
يتطلب الوصول إلى هذه الصفحة تخويلاً. يمكنك محاولة تسجيل الدخول أو تغيير الدلائل.
يتطلب الوصول إلى هذه الصفحة تخويلاً. يمكنك محاولة تغيير الدلائل.
عندما يسأل مسؤولو تكنولوجيا المعلومات عن عدد تطبيقات السحابة التي يعتقدون أن موظفيهم يستخدمونها، في المتوسط يقولون 30 أو 40، عندما يكون المتوسط في الواقع أكثر من 1000 تطبيق منفصل يستخدمه الموظفون في مؤسستك. يساعدك Shadow IT على معرفة التطبيقات المستخدمة وتحديدها ومستوى المخاطر. يستخدم 80٪ من الموظفين تطبيقات غير معتمدة لم يراجعها أحد، وقد لا يكونوا متوافقين مع نهج الأمان والتوافق الخاصة بك. ولأن موظفيك يمكنهم الوصول إلى مواردك وتطبيقاتك من خارج شبكة شركتك، لم يعد من الكافي وجود قواعد ونهج على جدران الحماية الخاصة بك.
في هذا البرنامج التعليمي، ستتعلم كيفية استخدام اكتشاف السحابة لاكتشاف التطبيقات التي يتم استخدامها، واستكشاف مخاطر هذه التطبيقات، وتكوين النهج لتحديد التطبيقات الخطرة الجديدة التي يتم استخدامها، وإلغاء حظر هذه التطبيقات من أجل حظرها في الأصل باستخدام الوكيل أو جهاز جدار الحماية الخاص بك
تلميح
بشكل افتراضي، لا يمكن Defender for Cloud Apps اكتشاف التطبيقات غير الموجودة في الكتالوج.
لمشاهدة بيانات Defender for Cloud Apps لتطبيق غير موجود حاليا في الكتالوج، نوصي بالتحقق من مخططنا أو إنشاء تطبيق مخصص.
كيفية اكتشاف Shadow IT وإدارته في شبكتك
استخدم هذه العملية لنشر اكتشاف سحابة Shadow IT في مؤسستك.
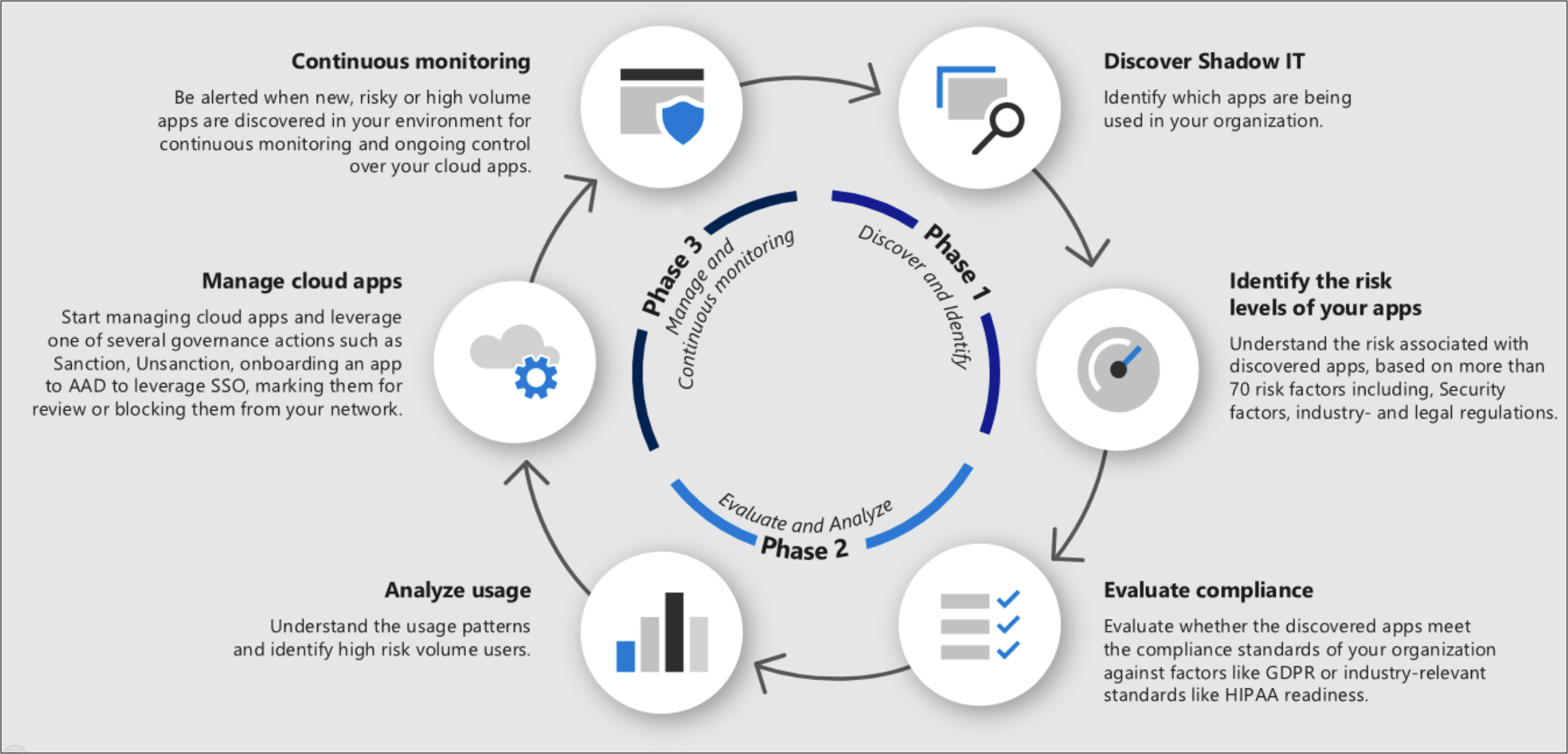
المرحلة 1: اكتشاف Shadow IT وتحديده
اكتشاف Shadow IT: حدد الوضع الأمني لمؤسستك من خلال تشغيل اكتشاف السحابة في مؤسستك لمعرفة ما يحدث بالفعل في شبكتك. لمزيد من المعلومات، راجع إعداد اكتشاف السحابة. يمكن القيام بذلك باستخدام أي من الطرق التالية:
ابدأ العمل بسرعة مع اكتشاف السحابة من خلال التكامل مع Microsoft Defender لنقطة النهاية. يمكنك هذا التكامل الأصلي من البدء فورا في جمع البيانات على نسبة استخدام الشبكة السحابية عبر Windows 10 والأجهزة Windows 11، داخل شبكتك وخارجها.
للتغطية على جميع الأجهزة المتصلة بشبكتك، من المهم نشر جامع سجل Defender for Cloud Apps على جدران الحماية والوكلاء الآخرين لجمع البيانات من نقاط النهاية وإرسالها إلى Defender for Cloud Apps للتحليل.
دمج Defender for Cloud Apps مع الوكيل الخاص بك. يتكامل Defender for Cloud Apps في الأصل مع بعض وكلاء الجهات الخارجية، بما في ذلك Zscaler.
نظرا لأن النهج مختلفة عبر مجموعات المستخدمين والمناطق ومجموعات الأعمال، فقد ترغب في إنشاء تقرير Shadow IT مخصص لكل وحدة من هذه الوحدات. لمزيد من المعلومات، راجع إنشاء تقارير مستمرة مخصصة.
الآن بعد أن تم تشغيل اكتشاف السحابة على شبكتك، انظر إلى التقارير المستمرة التي يتم إنشاؤها وانظر إلى لوحة معلومات اكتشاف السحابة للحصول على صورة كاملة عن التطبيقات المستخدمة في مؤسستك. من الجيد النظر إليها حسب الفئة، لأنك غالبا ما تجد أن التطبيقات غير المخولة يتم استخدامها لأغراض مشروعة متعلقة بالعمل لم تتم معالجتها بواسطة تطبيق مخول.
تحديد مستويات مخاطر تطبيقاتك: استخدم كتالوج Defender for Cloud Apps للتعمق في المخاطر التي ينطوي عليها كل تطبيق مكتشف. يتضمن كتالوج تطبيقات Defender for cloud أكثر من 31,000 تطبيق يتم تقييمها باستخدام أكثر من 90 عامل خطر. تبدأ عوامل الخطر من المعلومات العامة حول التطبيق (أين يوجد المقر الرئيسي للتطبيق، ومن هو الناشر)، ومن خلال تدابير الأمان وعناصر التحكم (دعم التشفير الثابت، يوفر سجل تدقيق لنشاط المستخدم). لمزيد من المعلومات، راجع العمل مع درجة المخاطر،
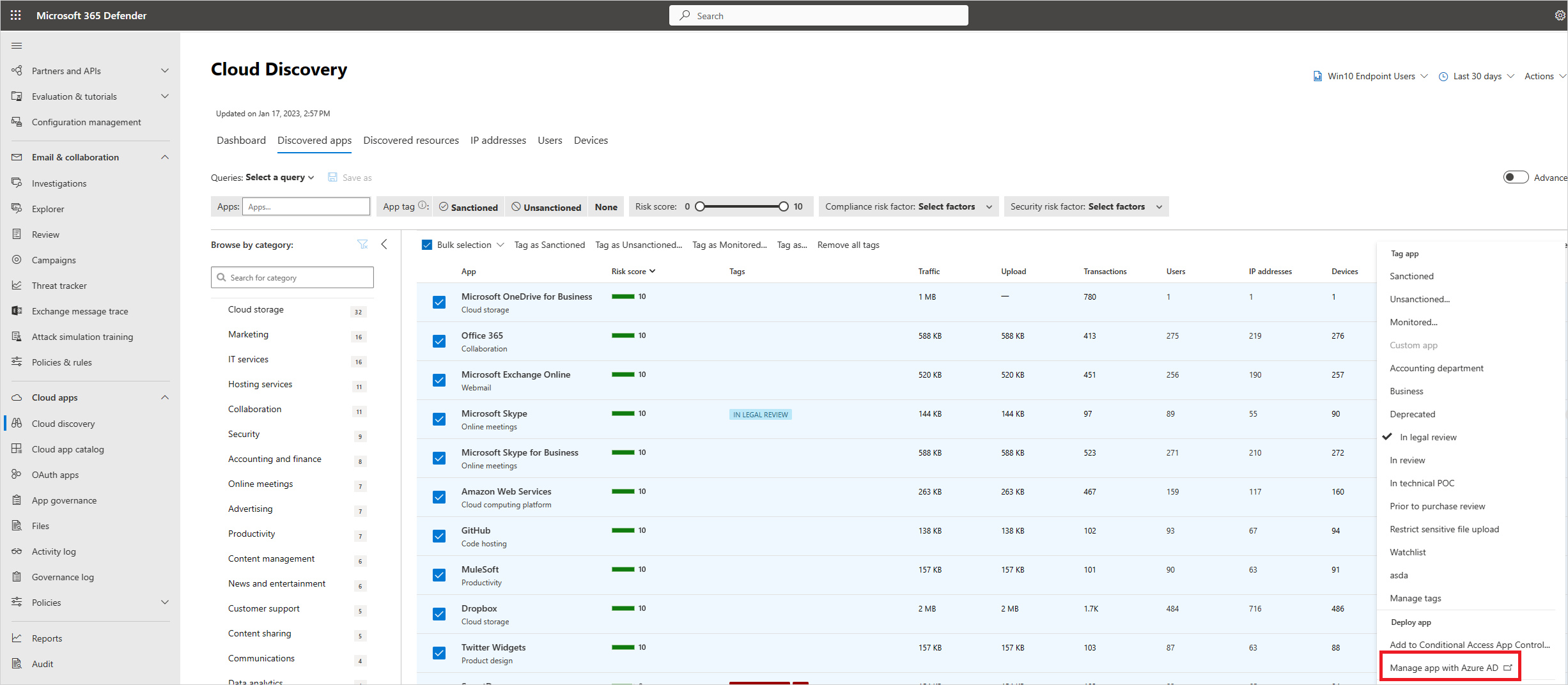
في Microsoft Defender Portal، ضمن Cloud Apps، حدد Cloud Discovery. ثم انتقل إلى علامة التبويب التطبيقات المكتشفة . قم بتصفية قائمة التطبيقات المكتشفة في مؤسستك حسب عوامل الخطر التي تهتم بها. على سبيل المثال، يمكنك استخدام عوامل التصفية المتقدمة للعثور على جميع التطبيقات ذات درجة مخاطرة أقل من 8.
يمكنك التنقل لأسفل في التطبيق لفهم المزيد حول توافقه عن طريق تحديد اسم التطبيق ثم تحديد علامة التبويب معلومات للاطلاع على تفاصيل حول عوامل مخاطر أمان التطبيق.
المرحلة 2: التقييم والتحليل
تقييم التوافق: تحقق مما إذا كانت التطبيقات معتمدة على أنها متوافقة مع معايير مؤسستك، مثل HIPAA أو SOC2.
في Microsoft Defender Portal، ضمن Cloud Apps، حدد Cloud Discovery. ثم انتقل إلى علامة التبويب التطبيقات المكتشفة . قم بتصفية قائمة التطبيقات المكتشفة في مؤسستك حسب عوامل مخاطر التوافق التي تهتم بها. على سبيل المثال، استخدم الاستعلام المقترح لتصفية التطبيقات غير المتوافقة.
يمكنك التنقل لأسفل في التطبيق لفهم المزيد حول توافقه عن طريق تحديد اسم التطبيق ثم تحديد علامة التبويب معلومات للاطلاع على تفاصيل حول عوامل مخاطر التوافق للتطبيق.
تحليل الاستخدام: الآن بعد أن عرفت ما إذا كنت تريد استخدام التطبيق في مؤسستك أم لا، فأنت تريد التحقق من كيفية ومن يستخدمه. إذا تم استخدامه فقط بطريقة محدودة في مؤسستك، فربما يكون الأمر على ما يرام، ولكن ربما إذا كان الاستخدام يتزايد، فأنت تريد أن يتم إعلامك به حتى تتمكن من تحديد ما إذا كنت تريد حظر التطبيق.
في Microsoft Defender Portal، ضمن Cloud Apps، حدد Cloud Discovery. ثم انتقل إلى علامة التبويب التطبيقات المكتشفة ، ثم انتقل لأسفل عن طريق تحديد التطبيق المحدد الذي تريد التحقيق فيه. تتيح لك علامة التبويب Usage معرفة عدد المستخدمين النشطين الذين يستخدمون التطبيق ومقدار نسبة استخدام الشبكة التي يقوم بإنشائه. يمكن أن يمنحك هذا بالفعل صورة جيدة لما يحدث مع التطبيق. بعد ذلك، إذا كنت تريد معرفة من يستخدم التطبيق، على وجه التحديد، يمكنك التنقل لأسفل عن طريق تحديد إجمالي المستخدمين النشطين. يمكن أن تمنحك هذه الخطوة المهمة معلومات ذات صلة، على سبيل المثال، إذا اكتشفت أن جميع مستخدمي تطبيق معين من قسم التسويق، فمن المحتمل أن تكون هناك حاجة تجارية لهذا التطبيق، وإذا كان الأمر محفوفا بالمخاطر، فيجب عليك التحدث إليهم حول بديل قبل حظره.
التعمق أكثر عند التحقيق في استخدام التطبيقات المكتشفة. اعرض المجالات الفرعية والموارد للتعرف على أنشطة محددة والوصول إلى البيانات واستخدام الموارد في خدمات السحابة الخاصة بك. لمزيد من المعلومات، راجع التعمق في التطبيقات المكتشفةواكتشاف الموارد والتطبيقات المخصصة.
تحديد التطبيقات البديلة: استخدم كتالوج تطبيقات السحابة لتحديد تطبيقات أكثر أمانا تحقق وظائف أعمال مماثلة للتطبيقات المكتشفة الخطرة، ولكنها تتوافق مع نهج مؤسستك. يمكنك القيام بذلك باستخدام عوامل التصفية المتقدمة للعثور على التطبيقات في نفس الفئة التي تتوافق مع عناصر تحكم الأمان المختلفة.
المرحلة 3: إدارة تطبيقاتك
إدارة تطبيقات السحابة: يساعدك Defender for Cloud Apps في عملية إدارة استخدام التطبيق في مؤسستك. بعد تحديد الأنماط والسلوكيات المختلفة المستخدمة في مؤسستك، يمكنك إنشاء علامات تطبيق مخصصة جديدة لتصنيف كل تطبيق وفقا لحالة عمله أو مبرراته. يمكن بعد ذلك استخدام هذه العلامات لأغراض مراقبة محددة، على سبيل المثال، تحديد نسبة استخدام الشبكة العالية التي تنتقل إلى التطبيقات التي تم وضع علامة عليها على أنها تطبيقات تخزين سحابية محفوفة بالمخاطر. يمكن إدارة علامات التطبيق ضمن Settings>Cloud Apps>Cloud Discovery>App tags. يمكن بعد ذلك استخدام هذه العلامات لاحقا للتصفية في صفحات اكتشاف السحابة وإنشاء النهج باستخدامها.
إدارة التطبيقات المكتشفة باستخدام معرض Microsoft Entra: يستخدم Defender for Cloud Apps أيضا تكامله الأصلي مع معرف Microsoft Entra لتمكينك من إدارة تطبيقاتك المكتشفة في معرض Microsoft Entra. بالنسبة للتطبيقات التي تظهر بالفعل في معرض Microsoft Entra، يمكنك تطبيق تسجيل الدخول الأحادي وإدارة التطبيق باستخدام معرف Microsoft Entra. للقيام بذلك، في الصف حيث يظهر التطبيق ذي الصلة، اختر النقاط الثلاث في نهاية الصف، ثم اختر إدارة التطبيق باستخدام معرف Microsoft Entra.
المراقبة المستمرة: الآن بعد أن قمت بالتحقيق في التطبيقات بدقة، قد ترغب في تعيين النهج التي تراقب التطبيقات وتوفر التحكم عند الحاجة.
حان الوقت الآن لإنشاء نهج بحيث يمكن تنبيهك تلقائيا عند حدوث شيء ما تشعر بالقلق بشأنه. على سبيل المثال، قد ترغب في إنشاء نهج اكتشاف التطبيق الذي يتيح لك معرفة متى يكون هناك ارتفاع في التنزيلات أو نسبة استخدام الشبكة من تطبيق تهتم به. لتحقيق ذلك، يجب تمكين السلوك الشاذ في نهج المستخدمين المكتشفين، وتحقق من توافق تطبيق التخزين السحابي، والتطبيق الجديد الخطر. يجب عليك أيضا تعيين النهج لإعلامك عن طريق البريد الإلكتروني. لمزيد من المعلومات، راجع مرجع قالب النهج، والمزيد حول نهج اكتشاف السحابة وتكوين نهج اكتشاف التطبيق.
انظر إلى صفحة التنبيهات واستخدم عامل تصفية نوع النهج لإلقاء نظرة على تنبيهات اكتشاف التطبيق. بالنسبة للتطبيقات التي تطابقت مع نهج اكتشاف التطبيق، يوصى بإجراء تحقيق متقدم لمعرفة المزيد حول مبررات الأعمال لاستخدام التطبيق، على سبيل المثال، عن طريق الاتصال بمستخدمي التطبيق. بعد ذلك، كرر الخطوات في المرحلة 2 لتقييم مخاطر التطبيق. ثم حدد الخطوات التالية للتطبيق، سواء وافقت على استخدامه في المستقبل أو تريد حظره في المرة التالية التي يصل إليها المستخدم، وفي هذه الحالة يجب وضع علامة عليه على أنه غير مصرع حتى يمكن حظره باستخدام جدار الحماية أو الوكيل أو بوابة الويب الآمنة. لمزيد من المعلومات، راجع التكامل مع Microsoft Defender لنقطة النهاية والتكامل مع Zscaler والتكامل مع تطبيقات ibossوحظر التطبيقات عن طريق تصدير برنامج نصي للكتلة.
المرحلة الرابعة: إعداد تقارير اكتشاف تكنولوجيا المعلومات في Shadow Advanced
بالإضافة إلى خيارات إعداد التقارير المتوفرة في Defender for Cloud Apps، يمكنك دمج سجلات الاكتشاف السحابي في Microsoft Sentinel لمزيد من التحقيق والتحليل. بمجرد أن تكون البيانات في Microsoft Sentinel، يمكنك عرضها في لوحات المعلومات، وتشغيل الاستعلامات باستخدام لغة استعلام Kusto، وتصدير الاستعلامات إلى Microsoft Power BI، والتكامل مع مصادر أخرى، وإنشاء تنبيهات مخصصة. لمزيد من المعلومات، راجع تكامل Microsoft Sentinel.
المرحلة 5: التحكم في التطبيقات المعتمدة
لتمكين التحكم في التطبيق عبر واجهات برمجة التطبيقات، قم بتوصيل التطبيقات عبر واجهة برمجة التطبيقات للمراقبة المستمرة.
حماية التطبيقات باستخدام التحكم في تطبيق الوصول المشروط.
تعني طبيعة تطبيقات السحابة أنه يتم تحديثها يوميا وتظهر التطبيقات الجديدة طوال الوقت. لهذا السبب، يستخدم الموظفون باستمرار تطبيقات جديدة ومن المهم متابعة تعقب ومراجعة وتحديث النهج الخاصة بك، والتحقق من التطبيقات التي يستخدمها المستخدمون، بالإضافة إلى أنماط استخدامهم وسلوكهم. يمكنك دائما الانتقال إلى لوحة معلومات اكتشاف السحابة ومعرفة التطبيقات الجديدة التي يتم استخدامها، واتباع الإرشادات الواردة في هذه المقالة مرة أخرى للتأكد من حماية مؤسستك وبياناتك.
الخطوات التالية
إذا واجهت أي مشاكل، فنحن هنا للمساعدة. للحصول على المساعدة أو الدعم لقضية المنتج، يرجى فتح تذكرة دعم.