البرنامج التعليمي: حماية الملفات باستخدام عزل المسؤول
تعد نهج الملفات أداة رائعة للعثور على التهديدات لنهج حماية المعلومات الخاصة بك. على سبيل المثال، قم بإنشاء نهج الملفات التي تجد الأماكن التي خزن فيها المستخدمون المعلومات الحساسة وأرقام بطاقات الائتمان وملفات ICAP التابعة لجهة خارجية في السحابة الخاصة بك.
في هذا البرنامج التعليمي، ستتعلم كيفية استخدام Microsoft Defender for Cloud Apps للكشف عن الملفات غير المرغوب فيها المخزنة في السحابة الخاصة بك والتي تتركك عرضة للخطر، واتخاذ إجراء فوري لإيقافها في مساراتها وتأمين الملفات التي تشكل تهديدا باستخدام مسؤول العزل لحماية ملفاتك في السحابة، ومعالجة المشكلات، ومنع حدوث تسريبات مستقبلية.
فهم كيفية عمل العزل
ملاحظة
- للحصول على قائمة التطبيقات التي تدعم عزل المسؤول، راجع قائمة إجراءات الحوكمة.
- لا يمكن عزل الملفات المسماة بواسطة Defender for Cloud Apps.
- تقتصر إجراءات عزل المسؤول Defender for Cloud Apps على 100 إجراء يوميا.
- لا يمكن استخدام مواقع Sharepoint التي تتم إعادة تسميتها إما مباشرة أو كجزء من إعادة تسمية المجال كموقع مجلد لعزل المسؤول.
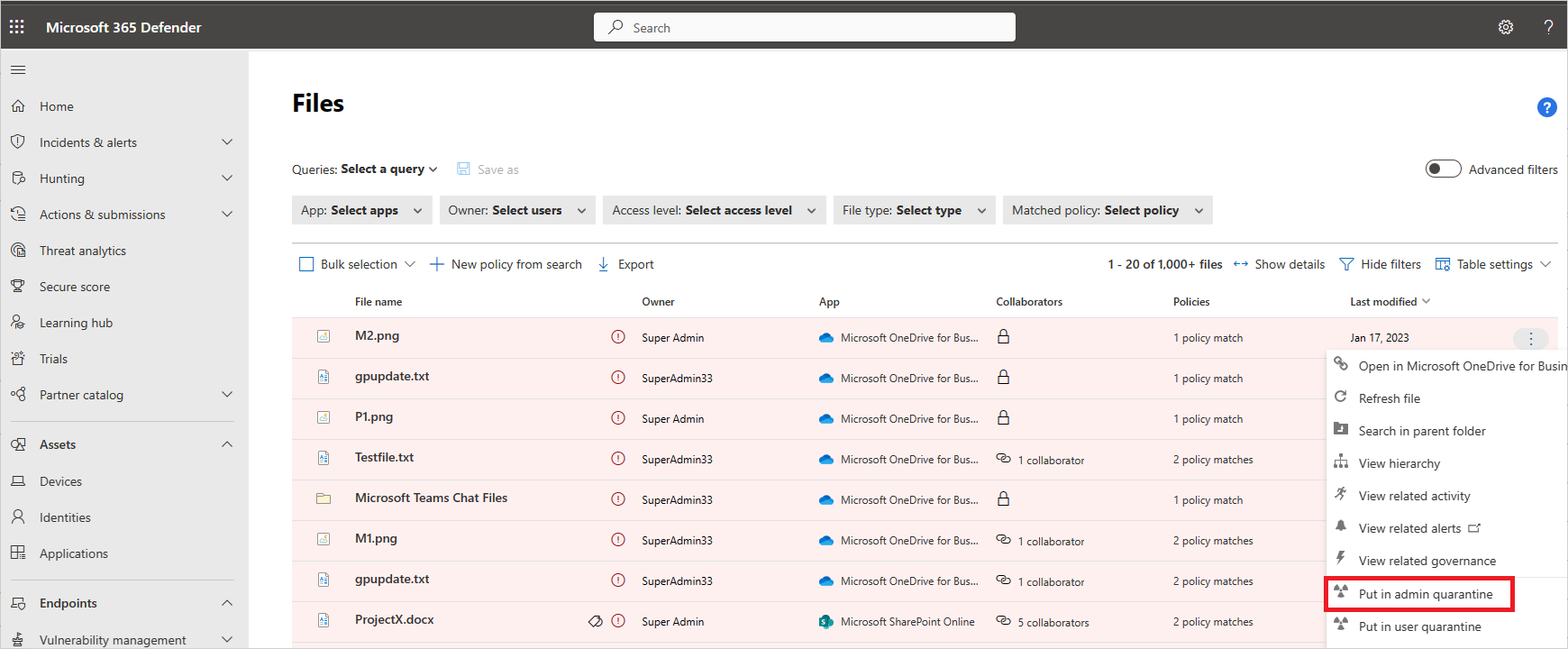
عندما يتطابق ملف مع نهج، يتوفر خيار العزل مسؤول للملف.
قم بأحد الإجراءات التالية لعزل الملف:
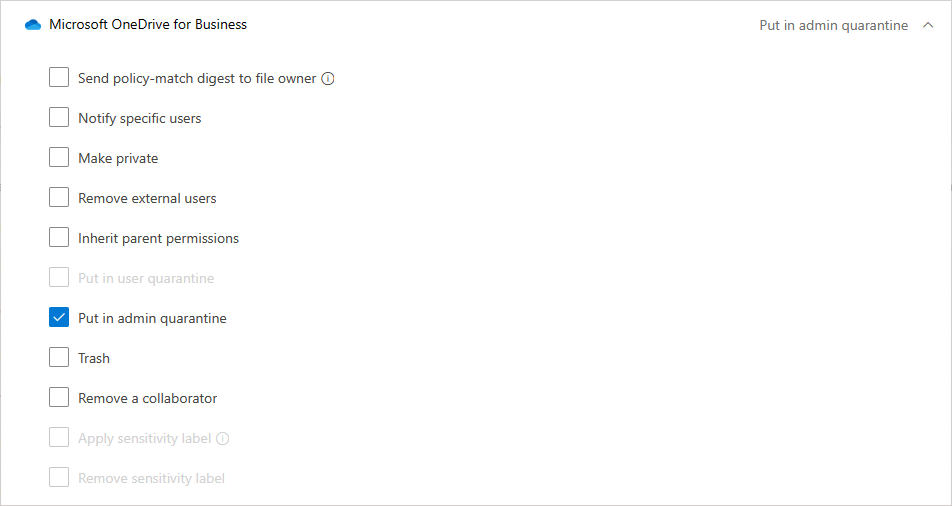
عند تطبيق مسؤول العزل، تحدث الأشياء التالية خلف الكواليس:
يتم نقل الملف الأصلي إلى مجلد عزل المسؤول الذي قمت بتعيينه.
يتم حذف الملف الأصلي.
يتم تحميل ملف tombstone إلى موقع الملف الأصلي.
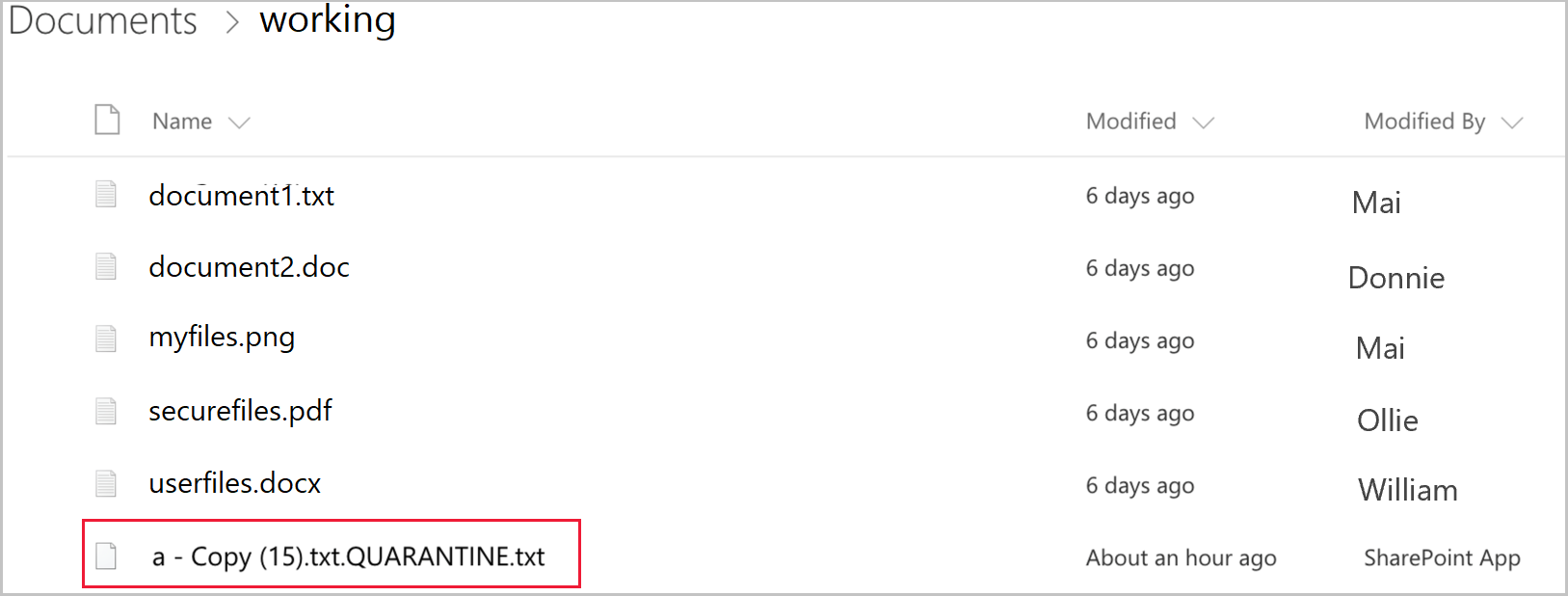
يمكن للمستخدم الوصول إلى ملف tombstone فقط. في الملف، يمكنهم قراءة الإرشادات المخصصة التي توفرها تكنولوجيا المعلومات ومعرف الارتباط لمنح تكنولوجيا المعلومات لتحرير الملف.
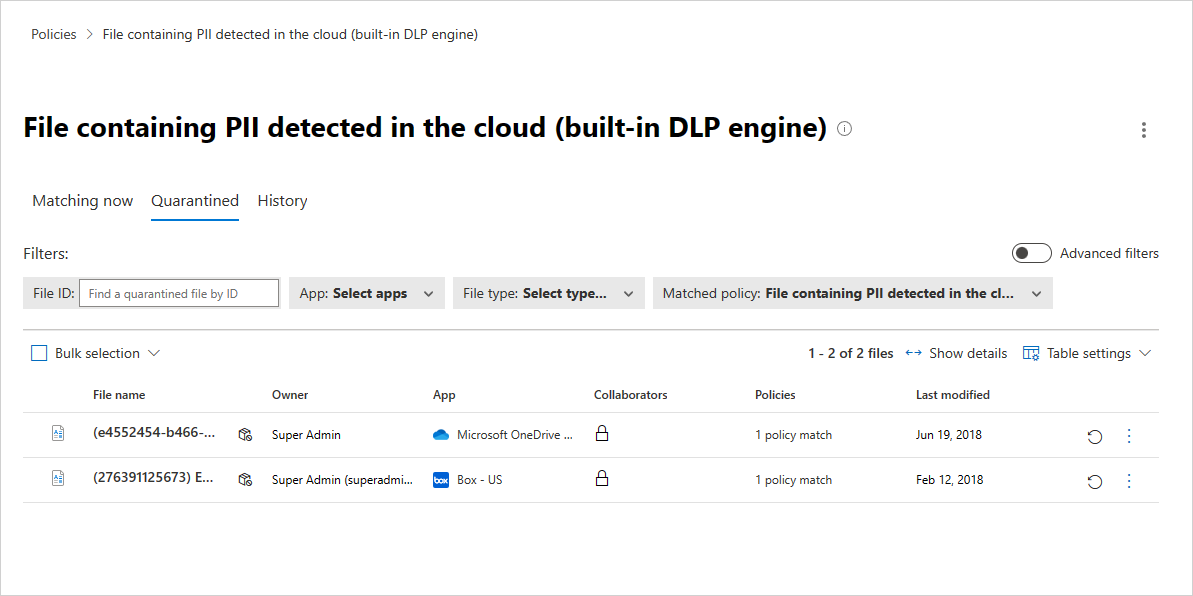
عندما تتلقى تنبيها بأنه تم عزل ملف، انتقل إلى Policies ->Policy Management. ثم حدد علامة التبويب حماية البيانات. في الصف الذي يحتوي على نهج الملف، اختر النقاط الثلاث في نهاية السطر، وحدد عرض جميع التطابقات. هذا يجلب لك تقرير التطابقات، حيث يمكنك مشاهدة الملفات المطابقة والعزل:
بعد عزل ملف، استخدم العملية التالية لمعالجة حالة التهديد:
افحص الملف في المجلد المعزول على SharePoint عبر الإنترنت.
يمكنك أيضا إلقاء نظرة على سجلات التدقيق للتعمق في خصائص الملف.
إذا وجدت أن الملف مقابل نهج الشركة، فقم بتشغيل عملية الاستجابة للحوادث (IR) الخاصة بالمؤسسة.
إذا وجدت أن الملف غير ضار، يمكنك استعادة الملف من العزل. عند هذه النقطة يتم إصدار الملف الأصلي، مما يعني أنه يتم نسخه مرة أخرى إلى الموقع الأصلي، ويتم حذف علامة الحذف، ويمكن للمستخدم الوصول إلى الملف.
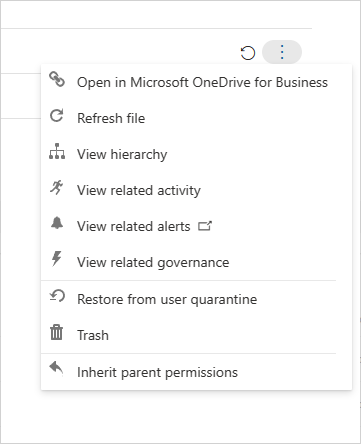
تحقق من أن النهج يعمل بسلاسة. بعد ذلك، يمكنك استخدام إجراءات الإدارة التلقائية في النهج لمنع المزيد من التسريبات وتطبيق عزل مسؤول تلقائيا عند مطابقة النهج.
ملاحظة
عند استعادة ملف:
- لم تتم استعادة المشاركات الأصلية، ويتم تطبيق توريث المجلد الافتراضي.
- يحتوي الملف المستعادة على أحدث إصدار فقط.
- إدارة الوصول إلى موقع مجلد العزل هي مسؤولية العميل.
إعداد عزل المسؤول
تعيين نهج الملفات التي تكشف عن الخروقات. تتضمن أمثلة هذه الأنواع من النهج ما يلي:
- نهج بيانات التعريف فقط مثل وصف الحساسية في SharePoint Online
- نهج DLP أصلي مثل النهج الذي يبحث عن أرقام بطاقات الائتمان
- سياسة الجهات الخارجية في ICAP مثل السياسة التي تبحث عن Vontu
تعيين موقع عزل:
بالنسبة إلى Microsoft 365 SharePoint أو OneDrive for Business، لا يمكنك وضع الملفات في عزل المسؤول كجزء من نهج حتى تقوم بإعداده:
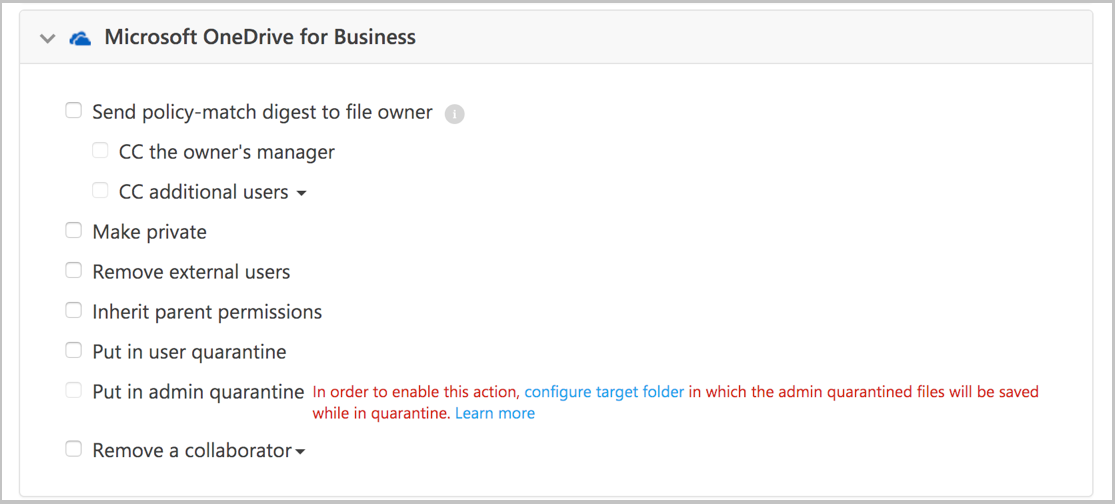
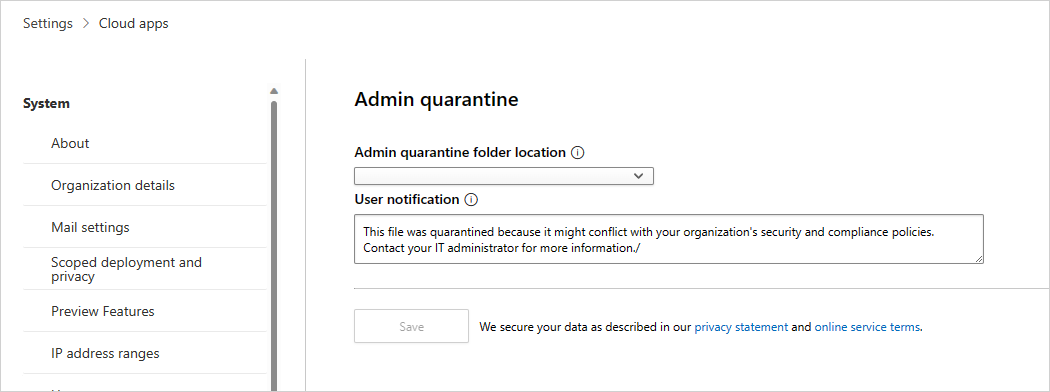
لتعيين إعدادات عزل المسؤول، في مدخل Microsoft Defender، حدد الإعدادات. ثم اختر تطبيقات السحابة. ضمن حماية البيانات، اختر مسؤول العزل. قم بتوفير موقع لموقع مجلد العزل وإخطار المستخدم الذي سيتلقىه المستخدم عند عزل ملفه.
ملاحظة
سيقوم Defender for Cloud Apps بإنشاء مجلد عزل على الموقع المحدد.
بالنسبة إلى Box، لا يمكن تخصيص موقع مجلد العزل ورسالة المستخدم. موقع المجلد هو محرك أقراص المسؤول الذي قام بتوصيل Box Defender for Cloud Apps ورسالة المستخدم هي: تم عزل هذا الملف إلى محرك أقراص المسؤول لأنه قد ينتهك نهج الأمان والتوافق الخاصة بشركتك. اتصل بمسؤول تكنولوجيا المعلومات للحصول على المساعدة.
الخطوات التالية
إذا واجهت أي مشاكل، فنحن هنا للمساعدة. للحصول على المساعدة أو الدعم لقضية المنتج، يرجى فتح تذكرة دعم.