Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
IT Administrators in organizations may want to control certain aspects of Dev Tunnels to achieve consistency or compliance across their organization. An easy way to accomplish this level of control is to configure and then deploy group policy settings to the client machines. The Dev Tunnels in Visual Studio, port forwarding built into Visual Studio Code, the Visual Studio Code Remote - Tunnels extension, and devtunnel CLI policies are consolidated in the Administrator Template files (ADMX/ADML) for Dev Tunnels.
In this quickstart, you'll learn how to configure and deploy Dev Tunnels group policy settings across your organization.
Prerequisites
- Windows Server 2016, Windows Server 2019, Windows Server 2022, Windows 8.1, Windows 10, Windows 11
- Active Directory
- Access to Local Group Policy Editor
Note
The policies are only applicable on Windows machines.
Policies Supported
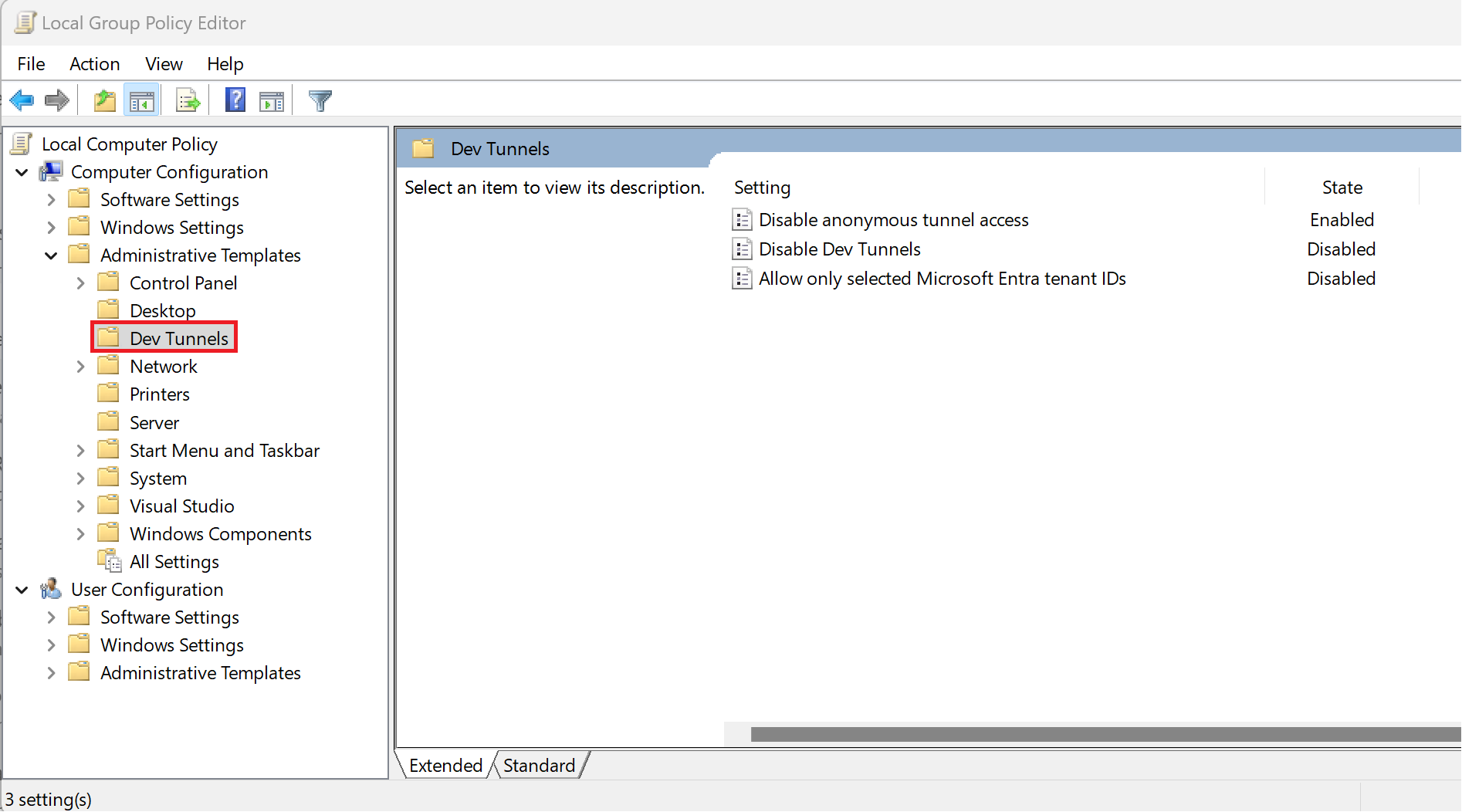
- Disable anonymous tunnel access: Disallow anonymous tunnel access. Enabling this policy enforces users to select either private or organization for tunnel access. This means users cannot connect to an existing tunnel with anonymous access control, host an existing tunnel with anonymous access control, or add anonymous access to existing or new tunnels.
- Disable Dev Tunnels: Disallow users from using the Dev Tunnels service. All commands, with few exceptions, should be denied access when this policy is enabled. Exceptions: unset, echo, ping, and user.
- Allow only selected Microsoft Entra tenant IDs: Users must authenticate within the given tenant list to access Dev Tunnels. When enabling this policy, multiple tenant IDs can be added by using a semicolon or comma to separate each. All commands, with few exceptions, should be denied access when this policy is enabled and the user's tenant ID isn't in the list of allowed tenant IDs. Exceptions: unset, echo, ping, and user. Follow the steps in this article to find your Microsoft Entra tenant ID.
Configure policies with Local Group Policy Editor
Download the Administrator Template files
- Head over to the Microsoft Download Center and download the Administrator Template files (ADMX/ADML) for Dev Tunnels.
- Navigate to the
C:\Windows\PolicyDefinitionsfolder and add theTunnelsPolicies.admxfile. - Navigate to the
C:\Windows\PolicyDefinitions\en-USfolder and add theTunnelsPolicies.admlfile.
Apply the policies using the Local Group Policy Editor
- Open Command Prompt and run
gpupdate /forceto ensure the policy files are configured. - Open the Windows Local Group Policy Editor.
- Navigate to Computer Configuration > Administrative Templates > Dev Tunnels.
- Apply the desired policy changes.