Configure Snowflake for automatic user provisioning
This tutorial demonstrates the steps that you perform in Snowflake and Microsoft Entra ID to configure Microsoft Entra ID to automatically provision and deprovision users and groups to Snowflake. For important details on what this service does, how it works, and frequently asked questions, see What is automated SaaS app user provisioning in Microsoft Entra ID?.
Capabilities supported
- Create users in Snowflake
- Remove users in Snowflake when they don't require access anymore
- Keep user attributes synchronized between Microsoft Entra ID and Snowflake
- Provision groups and group memberships in Snowflake
- Allow single sign-on to Snowflake (recommended)
Prerequisites
The scenario outlined in this tutorial assumes that you already have the following prerequisites:
- A Microsoft Entra tenant
- One of the following roles: Application Administrator, Cloud Application Administrator, or Application Owner.
- A Snowflake tenant
- At least one user in Snowflake with the ACCOUNTADMIN role.
Step 1: Plan your provisioning deployment
- Learn about how the provisioning service works.
- Determine who will be in scope for provisioning.
- Determine what data to map between Microsoft Entra ID and Snowflake.
Step 2: Configure Snowflake to support provisioning with Microsoft Entra ID
Before you configure Snowflake for automatic user provisioning with Microsoft Entra ID, you need to enable System for Cross-domain Identity Management (SCIM) provisioning on Snowflake.
Sign in to Snowflake as an administrator and execute the following from either the Snowflake worksheet interface or SnowSQL.
use role accountadmin; create role if not exists aad_provisioner; grant create user on account to role aad_provisioner; grant create role on account to role aad_provisioner; grant role aad_provisioner to role accountadmin; create or replace security integration aad_provisioning type = scim scim_client = 'azure' run_as_role = 'AAD_PROVISIONER'; select system$generate_scim_access_token('AAD_PROVISIONING');Use the ACCOUNTADMIN role.

Create the custom role AAD_PROVISIONER. All users and roles in Snowflake created by Microsoft Entra ID will be owned by the scoped down AAD_PROVISIONER role.
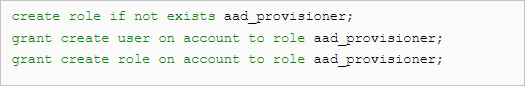
Let the ACCOUNTADMIN role create the security integration using the AAD_PROVISIONER custom role.
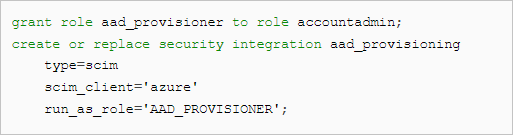
Create and copy the authorization token to the clipboard and store securely for later use. Use this token for each SCIM REST API request and place it in the request header. The access token expires after six months and a new access token can be generated with this statement.

Step 3: Add Snowflake from the Microsoft Entra application gallery
Add Snowflake from the Microsoft Entra application gallery to start managing provisioning to Snowflake. If you previously set up Snowflake for single sign-on (SSO), you can use the same application. However, we recommend that you create a separate app when you're initially testing the integration. Learn more about adding an application from the gallery.
Step 4: Define who will be in scope for provisioning
The Microsoft Entra provisioning service allows you to scope who will be provisioned based on assignment to the application, or based on attributes of the user or group. If you choose to scope who will be provisioned to your app based on assignment, you can use the steps to assign users and groups to the application. If you choose to scope who will be provisioned based solely on attributes of the user or group, you can use a scoping filter.
Keep these tips in mind:
When you're assigning users and groups to Snowflake, you must select a role other than Default Access. Users with the Default Access role are excluded from provisioning and will be marked as not effectively entitled in the provisioning logs. If the only role available on the application is the Default Access role, you can update the application manifest to add more roles.
If you need additional roles, you can update the application manifest to add new roles.
Step 5: Configure automatic user provisioning to Snowflake
This section guides you through the steps to configure the Microsoft Entra provisioning service to create, update, and disable users and groups in Snowflake. You can base the configuration on user and group assignments in Microsoft Entra ID.
To configure automatic user provisioning for Snowflake in Microsoft Entra ID:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications.
In the list of applications, select Snowflake.
Select the Provisioning tab.
Set Provisioning Mode to Automatic.

In the Admin Credentials section, enter the SCIM 2.0 base URL and authentication token that you retrieved earlier in the Tenant URL and Secret Token boxes, respectively.
Note
The Snowflake SCIM endpoint consists of the Snowflake account URL appended with
/scim/v2/. For example, if your Snowflake account name isacmeand your Snowflake account is in theeast-us-2Azure region, the Tenant URL value ishttps://acme.east-us-2.azure.snowflakecomputing.com/scim/v2.Select Test Connection to ensure that Microsoft Entra ID can connect to Snowflake. If the connection fails, ensure that your Snowflake account has admin permissions and try again.

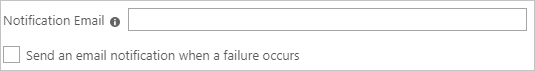
In the Notification Email box, enter the email address of a person or group who should receive the provisioning error notifications. Then select the Send an email notification when a failure occurs check box.
Select Save.
In the Mappings section, select Synchronize Microsoft Entra users to Snowflake.
Review the user attributes that are synchronized from Microsoft Entra ID to Snowflake in the Attribute Mapping section. The attributes selected as Matching properties are used to match the user accounts in Snowflake for update operations. Select the Save button to commit any changes.
Attribute Type active Boolean displayName String emails[type eq "work"].value String userName String name.givenName String name.familyName String externalId String Note
Snowflake supported custom extension user attributes during SCIM provisioning:
- DEFAULT_ROLE
- DEFAULT_WAREHOUSE
- DEFAULT_SECONDARY_ROLES
- SNOWFLAKE NAME AND LOGIN_NAME FIELDS TO BE DIFFERENT
How to set up Snowflake custom extension attributes in Microsoft Entra SCIM user provisioning is explained here.
In the Mappings section, select Synchronize Microsoft Entra groups to Snowflake.
Review the group attributes that are synchronized from Microsoft Entra ID to Snowflake in the Attribute Mapping section. The attributes selected as Matching properties are used to match the groups in Snowflake for update operations. Select the Save button to commit any changes.
Attribute Type displayName String members Reference To configure scoping filters, see the instructions in the Scoping filter tutorial.
To enable the Microsoft Entra provisioning service for Snowflake, change Provisioning Status to On in the Settings section.

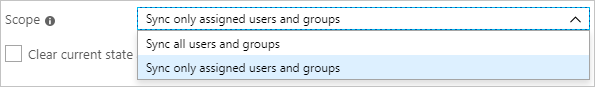
Define the users and groups that you want to provision to Snowflake by choosing the desired values in Scope in the Settings section.
If this option is not available, configure the required fields under Admin Credentials, select Save, and refresh the page.
When you're ready to provision, select Save.

This operation starts the initial synchronization of all users and groups defined in Scope in the Settings section. The initial sync takes longer to perform than subsequent syncs. Subsequent syncs occur about every 40 minutes, as long as the Microsoft Entra provisioning service is running.
Step 6: Monitor your deployment
After you've configured provisioning, use the following resources to monitor your deployment:
- Use the provisioning logs to determine which users have been provisioned successfully or unsuccessfully.
- Check the progress bar to see the status of the provisioning cycle and how close it is to completion.
- If the provisioning configuration seems to be in an unhealthy state, the application will go into quarantine. Learn more about quarantine states.
Connector limitations
Snowflake-generated SCIM tokens expire in 6 months. Be aware that you need to refresh these tokens before they expire, to allow the provisioning syncs to continue working.
Troubleshooting tips
The Microsoft Entra provisioning service currently operates under particular IP ranges. If necessary, you can restrict other IP ranges and add these particular IP ranges to the allowlist of your application. That technique will allow traffic flow from the Microsoft Entra provisioning service to your application.
Change log
- 07/21/2020: Enabled soft-delete for all users (via the active attribute).
- 10/12/2022: Updated Snowflake SCIM Configuration.
Additional resources
- Managing user account provisioning for enterprise apps
- What are application access and single sign-on with Microsoft Entra ID?