Configure P2S VPN Gateway for Microsoft Entra ID authentication – Microsoft-registered app
This article helps you configure your point-to-site (P2S) VPN gateway for Microsoft Entra ID authentication using the new Microsoft-registered Azure VPN Client App ID.
Note
The steps in this article apply to Microsoft Entra ID authentication using the new Microsoft-registered Azure VPN Client App ID and associated Audience values. This article doesn't apply to the older, manually registered Azure VPN Client app for your tenant. For the manually registered Azure VPN Client steps, see Configure P2S using manually registered VPN client.
VPN Gateway now supports a new Microsoft-registered App ID and corresponding Audience values for the latest versions of the Azure VPN Client. When you configure a P2S VPN gateway using the new Audience values, you skip the Azure VPN Client app manual registration process for your Microsoft Entra tenant. The App ID is already created and your tenant is automatically able to use it with no extra registration steps. This process is more secure than manually registering the Azure VPN Client because you don't need to authorize the app or assign permissions via the Global administrator role.
Previously, you were required to manually register (integrate) the Azure VPN Client app with your Microsoft Entra tenant. Registering the client app creates an App ID representing the identity of the Azure VPN Client application and requires authorization using the Global Administrator role. To better understand the difference between the types of application objects, see How and why applications are added to Microsoft Entra ID.
When possible, we recommend that you configure new P2S gateways using the Microsoft-registered Azure VPN client App ID and its corresponding Audience values, instead of manually registering the Azure VPN Client app with your tenant. If you have a previously configured Azure VPN gateway that uses Microsoft Entra ID authentication, you can update the gateway and clients to take advantage of the new Microsoft-registered App ID. Updating the P2S gateway with the new Audience value is required if you want Linux clients to connect. The Azure VPN Client for Linux isn't backward compatible with the older Audience values.
If you have an existing P2S gateway that you want to update to use a new Audience value, see Change Audience for a P2S VPN gateway. If you want to create or modify a custom Audience value, see Create a custom audience app ID for P2S VPN. If you want to configure or restrict access to P2S based on users and groups, see Scenario: Configure P2S VPN access based on users and groups.
Considerations and limitations
A P2S VPN gateway can only support one Audience value. It can't support multiple Audience values simultaneously.
At this time, the newer Microsoft-registered App ID doesn't support as many Audience values as the older, manually registered app. If you need an Audience value for anything other than Azure Public or Custom, use the older manually registered method and values.
The Azure VPN Client for Linux isn't backward compatible with P2S gateways configured to use the older Audience values that align with the manually registered app. The Azure VPN Client for Linux does support Custom Audience values.
-
While it's possible that the Azure VPN Client for Linux might work on other Linux distributions and releases, the Azure VPN Client for Linux is only supported on the following releases:
- Ubuntu 20.04
- Ubuntu 22.04
The Azure VPN Client for macOS and Windows is backward compatible with P2S gateways configured to use the older Audience values that align with the manually registered app. You can also use Custom Audience values with these clients.
Azure VPN Client Audience values
The following table shows the versions of the Azure VPN Client that are supported for each App ID and the corresponding available Audience values.
| App ID | Supported Audience values | Supported clients |
|---|---|---|
| Microsoft-registered | - Azure Public: c632b3df-fb67-4d84-bdcf-b95ad541b5c8 |
- Linux - Windows - macOS |
| Manually registered | - Azure Public: 41b23e61-6c1e-4545-b367-cd054e0ed4b4- Azure Government: 51bb15d4-3a4f-4ebf-9dca-40096fe32426- Azure Germany: 538ee9e6-310a-468d-afef-ea97365856a9- Microsoft Azure operated by 21Vianet: 49f817b6-84ae-4cc0-928c-73f27289b3aa |
- Windows - macOS |
| Custom | <custom-app-id> |
- Linux - Windows - macOS |
Point-to-site workflow
Successfully configuring a P2S connection using Microsoft Entra ID authentication requires a sequence of steps.
This article helps you:
- Verify your tenant.
- Configure the VPN gateway with the appropriate required settings.
- Generate and download the VPN Client configuration package.
The articles in the Next steps section help you:
- Download the Azure VPN Client on the client computer.
- Configure the client using the settings from the VPN Client configuration package.
- Connect.
Prerequisites
This article assumes the following prerequisites:
A VPN gateway
Certain gateway options are incompatible with P2S VPN gateways that use Microsoft Entra ID authentication. The VPN gateway can't use the Basic SKU or a policy-based VPN type. For more information about gateway SKUs, see About gateway SKUs. For more information about VPN types, see VPN Gateway settings.
If you don't already have a functioning VPN gateway that's compatible with Microsoft Entra ID authentication, see Create and manage a VPN gateway - Azure portal. Create a compatible VPN gateway, then return to this article to configure P2S settings.
A Microsoft Entra tenant
- The steps in this article require a Microsoft Entra tenant. For more information, see Create a new tenant in Microsoft Entra ID.
Add the VPN client address pool
The client address pool is a range of private IP addresses that you specify. The clients that connect over a point-to-site VPN dynamically receive an IP address from this range. Use a private IP address range that doesn't overlap with the on-premises location that you connect from, or the VNet that you want to connect to. If you configure multiple protocols and SSTP is one of the protocols, then the configured address pool is split between the configured protocols equally.
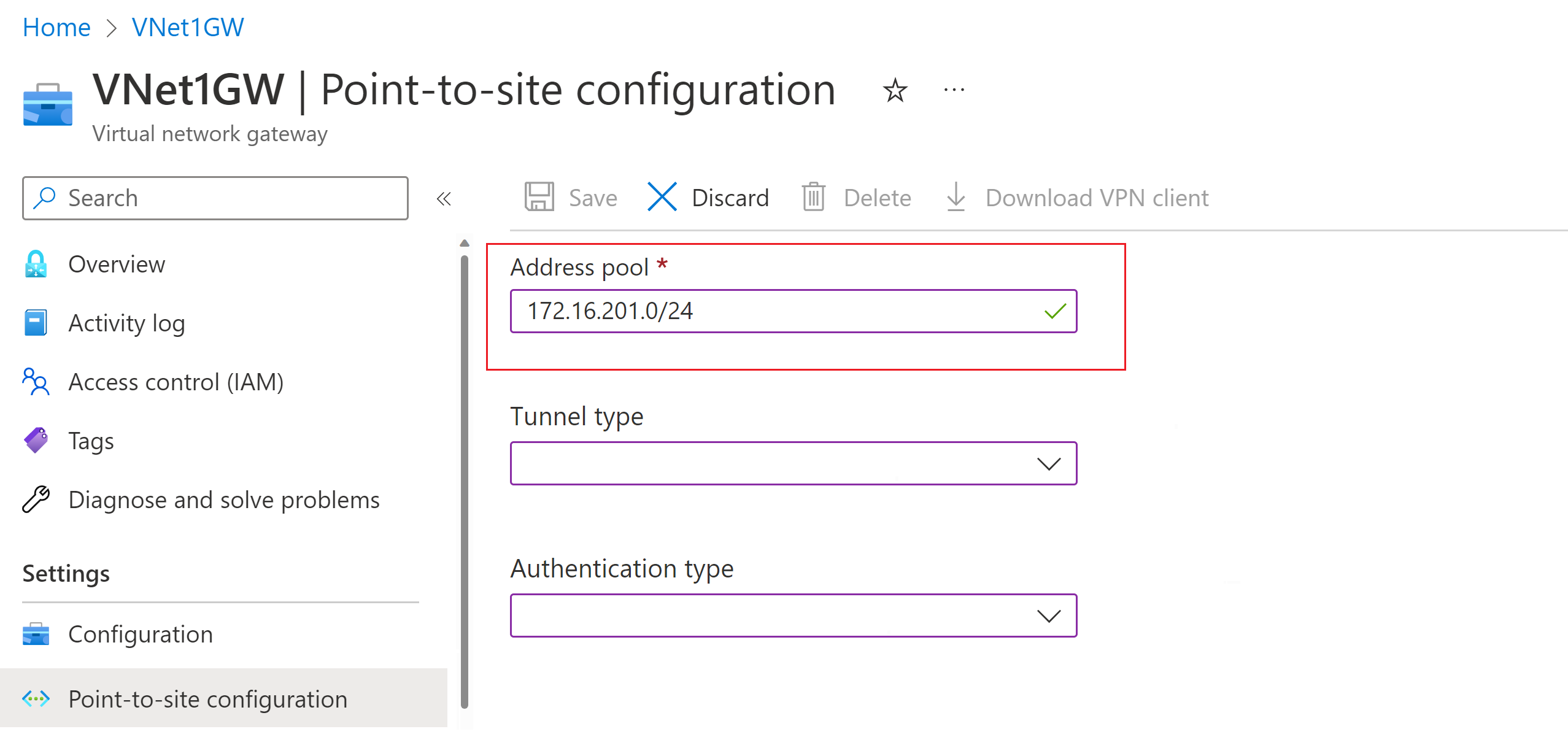
In the Azure portal, go to your VPN gateway.
On the page for your gateway, in the left pane, select Point-to-site configuration.
Click Configure now to open the configuration page.
On the Point-to-site configuration page, in the Address pool box, add the private IP address range that you want to use. VPN clients dynamically receive an IP address from the range that you specify. The minimum subnet mask is 29 bit for active/passive and 28 bit for active/active configuration.
Continue to the next section to configure more settings.
Configure tunnel type and authentication
Important
The Azure portal is in the process of updating Azure Active Directory fields to Entra. If you see Microsoft Entra ID referenced and you don't see those values in the portal yet, you can select Azure Active Directory values.
Locate the tenant ID of the directory that you want to use for authentication. For help with finding your tenant ID, see How to find your Microsoft Entra tenant ID.
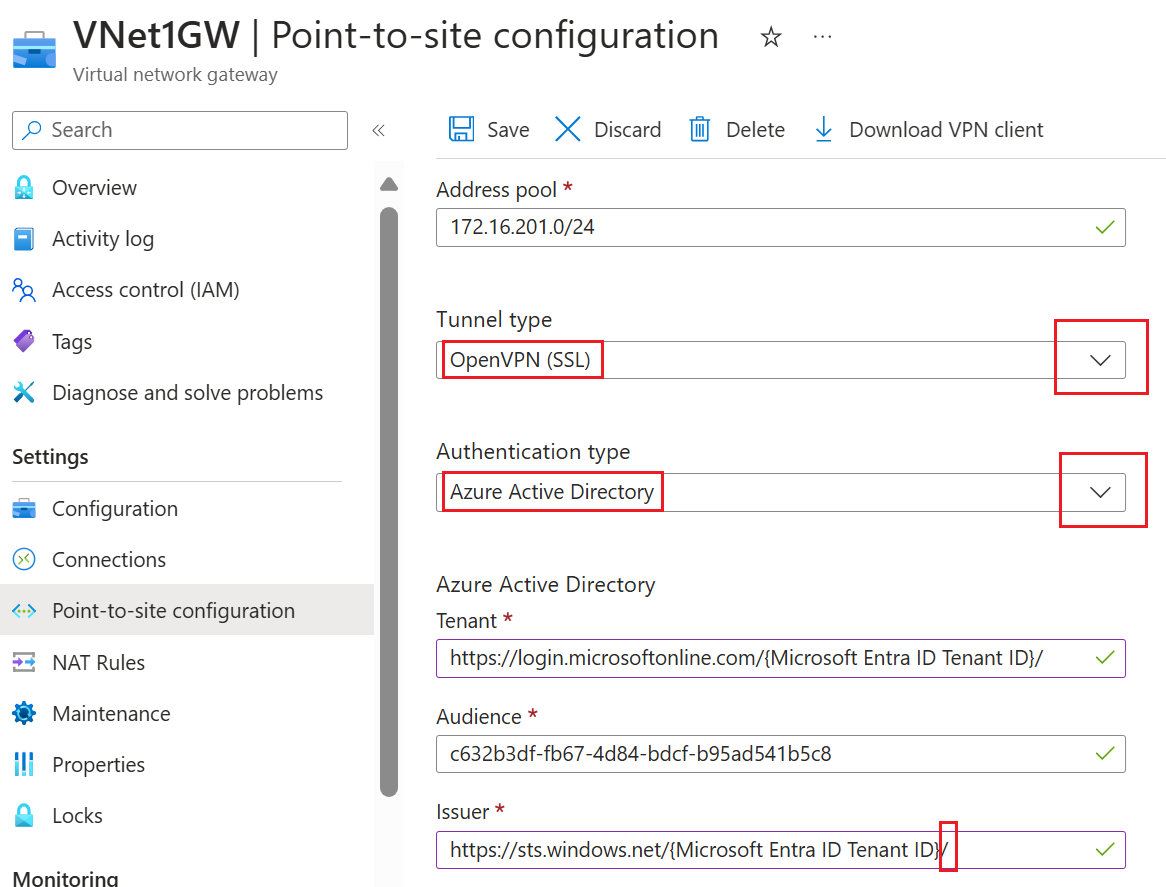
Configure tunnel type and authentication values.
Configure the following values:
- Address pool: client address pool
- Tunnel type: OpenVPN (SSL)
- Authentication type: Microsoft Entra ID
For Microsoft Entra ID values, use the following guidelines for Tenant, Audience, and Issuer values. Replace {Microsoft ID Entra Tenant ID} with your tenant ID, taking care to remove {} from the examples when you replace this value.
Tenant: TenantID for the Microsoft Entra ID tenant. Enter the tenant ID that corresponds to your configuration. Make sure the Tenant URL doesn't have a
\(backslash) at the end. Forward slash is permissible.- Azure Public:
https://login.microsoftonline.com/{Microsoft ID Entra Tenant ID}
- Azure Public:
Audience: The corresponding value for the Microsoft-registered Azure VPN Client App ID. Custom audience is also supported for this field.
- Azure Public:
c632b3df-fb67-4d84-bdcf-b95ad541b5c8
- Azure Public:
Issuer: URL of the Secure Token Service. Include a trailing slash at the end of the Issuer value. Otherwise, the connection might fail. Example:
https://sts.windows.net/{Microsoft ID Entra Tenant ID}/
You don't need to click Grant administrator consent for Azure VPN client application. This link is only for manually registered VPN clients that use the older Audience values. It opens a page in the Azure portal.
Once you finish configuring settings, click Save at the top of the page.
Download the VPN client profile configuration package
In this section, you generate and download the Azure VPN client profile configuration package. This package contains the settings that you can use to configure the Azure VPN client profile on client computers.
At the top of the Point-to-site configuration page, click Download VPN client. It takes a few minutes for the client configuration package to generate.
Your browser indicates that a client configuration zip file is available. It's named the same name as your gateway.
Extract the downloaded zip file.
Browse to the unzipped "AzureVPN" folder.
Make a note of the location of the “azurevpnconfig.xml” file. The azurevpnconfig.xml contains the setting for the VPN connection. You can also distribute this file to all the users that need to connect via e-mail or other means. The user will need valid Microsoft Entra ID credentials to connect successfully.
Configure the Azure VPN Client
Next, you examine the profile configuration package, configure the Azure VPN Client for the client computers, and connect to Azure. See the articles listed in the Next steps section.
Next steps
Configure the Azure VPN Client.