Why Pursue ACSC Essential Eight User Backup Guidelines?
The Australian Cyber Security Center (ACSC) leads the Australian Government's efforts to improve cyber security. The ACSC recommends all Australian organizations implement the Essential Eight mitigation strategies from the ACSC's Strategies to Mitigate Cyber Security Incidents as a baseline. The baseline, known as the Essential Eight, are foundational cyber security measures that make it much harder for adversaries to compromise systems.
The Essential Eight Maturity Levels allow organizations to assess the appropriateness of their cyber security measures against common threats in today's interconnected ICT landscape.
Backups are an essential strategy to ensure important data is protected from loss, whether that occurs as a result of physical means such as hardware failure, theft, accidental damage, or natural disasters, or logical means such as accidental deletion, corruption, and virus or malware infections. As an Essential Eight mitigation, backups are also perhaps one of the more difficult to provide prescriptive guidance for the implementation varies considerably based on each organization's unique needs. The importance of Regular Backups can be seen by its inclusion os one of the Essential Eight strategies in ACSC's Strategies to Mitigate Cyber Security Incidents.
The traditional approach to backups is to take a full, differential, or incremental copy of the data on a regular schedule and store the backup media offline, ideally in a separate facility, so that a clean copy of your data can be restored in a timely manner. While it may be tempting to mirror such an approach in an online world, the scale of cloud services can render such measures impractical and costly.
Does this mean you don't need to backup your data with services such as Microsoft 365? No! You absolutely need to ensure your information is protected. However the way you go about that with services like Microsoft 365 will naturally be different to how you may currently protect your on-premises file shares. Organizations should focus on configuring the built-in retention settings to ensure data is protected within the service as necessary to meet business requirements. Organizations should also invest in a data classification scheme to identify the truly critical information to protect with other controls. Microsoft 365 provides services to allow users and administrators to restore files and emails if accidental deletion or corruption. For data stored in on-premises workloads or in Azure services, Azure Backup provides a simple, secure, and cost-efficient solution to back up data and recover it from the Microsoft Azure cloud.
Finally, in a disaster recovery scenario the configuration necessary to restore the environment to operational status can be as important as the data itself. Server and domain information can be captured through a backup of the System State with the Microsoft Azure Recovery Services (MARS) agent and stored in the Azure Backup Service. For the configuration of cloud services such as Microsoft 365 and Azure, infrastructure-as-code solutions offer an alternative to manual changes directly within the admin portal, with scripts or deployment templates able to reset an environment to the desired settings or to provision a second tenant with the same configuration.
As the Essential Eight outlines a minimum set of preventative measures, organizations need to implement extra measures where it's warranted by their environment. Further, while the Essential Eight can help to mitigate most cyber threats, it will not mitigate all cyber threats. As such, other mitigation strategies and security controls need to be considered, including strategies from the Strategies to Mitigate Cyber Security Incidents | Cyber.gov.au and the Information Security Manual (ISM) | Cyber.gov.au.
A mapping between Maturity Level 1, 2 and 3 of the Regular Backups component of the Essential Eight Controls to the ISM is outlined in the following table and referenced from Essential Eight to ISM Mapping. These updates are based on the December 2023 release of the ISM.
| ISM control Mar 2024 | Maturity Level | Mitigation |
|---|---|---|
| 1511 | 1, 2, 3 | Backups of data, applications, and settings are performed and retained in accordance with business criticality and business continuity requirements. |
| 1515 | 1, 2, 3 | Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. |
| 1810 | 1, 2, 3 | Backups of data, applications, and settings are synchronized to enable restoration to a common point in time. |
| 1811 | 1, 2, 3 | Backups of data, applications, and settings are retained in a secure and resilient manner. |
| 1812 | 1, 2, 3 | Unprivileged accounts can't access backups belonging to other accounts. |
| 1814 | 1, 2, 3 | Unprivileged accounts are prevented from modifying and deleting backups. |
| 1705 | 2, 3 | Privileged accounts (excluding backup administrator accounts) can't access backups belonging to other accounts |
| 1707 | 2, 3 | Privileged accounts (excluding backup administrator accounts) are prevented from modifying and deleting backups. |
| 1813 | 2, 3 | Unprivileged accounts can't access backups belonging to other accounts, nor their own accounts. |
| 1706 | 3 | Privileged accounts (excluding backup administrator accounts) can't access their own backups. |
| 1708 | 3 | Backup administrator accounts are prevented from modifying and deleting backups during their retention period. |
Approach
In-Place Retention in Microsoft 365
Under the Shared Responsibility Model, customers always retain responsibility for information and data. Traditional backup implementations have typically focused on protection of the storage container and everything within it. This catch-all strategy may have been necessary to protect against the wide variety of threats faced on-premises, but with the adoption of cloud services responsibility for the physical environment shifts to the cloud provider and alternate controls can be employed to mitigate threats from loss or failure of equipment and the physical or logical corruption of data that could occur as a result. In such cases, the need to recover infrastructure from a backup can be negated by developments in resiliency.
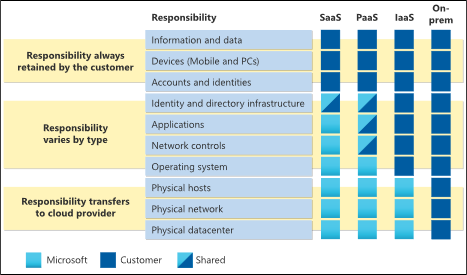
A full breakdown of the resiliency and continuity of Microsoft Cloud services is beyond the scope of this document. Organizations should familiarize themselves with the concepts presented in the Risk Assessment Guide for Microsoft Cloud and review the appropriate external audit reports available through the Service Trust Portal.
One of the standard principles of information protection is that data and backups should be kept separately, so the idea of using retention within the service often seems counter-intuitive to customers at first. There are many advantages to retaining information within a cloud service. Consider the storage available to the average organization with Microsoft 365 E3 licensing:
- OneDrive for Business, where a user stores their own files similar to a home directory on a file share, provides 1 TB per user with an option to expand storage by default to 5 TB, and more storage available upon request to Microsoft Support.
- Exchange Online allows for a 100-GB primary mailbox and unlimited storage in a personal archive.
- SharePoint Online, which provides the backend storage for collaboration sites and Microsoft Teams, provides an initial 1 TB of pooled storage per customer and a further 10 GB per licensed user.
As a result, for a typical 1,000-user organization, Microsoft 365 provides over 5,111 TB or 5.11 PB of storage before you even consider the unlimited storage for mailbox archives and the mailboxes and personal files of departed users.
Duplicating all of this information in an external service would take a significant amount of time to transfer for backup and restore operations, and over time may represent a substantial financial cost to the business. More so, there are other risks to consider when moving data outside the service, such as the regulatory compliance implications of transferring data outside of the geographic region, intentionally or not, or the potential exposure risk of data being compromised through third-party services. Ultimately though, one of the greatest considerations is user convenience - in the event of deleted files or even a ransomware infection that wipes out a user's entire directory, OneDrive for Business makes it easy for a user to restore a good version of a file, or to restore a whole library to a particular point in time, all without administrator assistance.
Retention Policies and Retention Labels
Retention policies and labels provide a means to control how data is retained in Microsoft 365. Retention policies can be applied to locations such as Exchange Online mailboxes and public folders, SharePoint Online sites, OneDrive for Business accounts, Microsoft 365 groups, Teams messages, and Viva Engage (Yammer) content. A single policy can be applied to multiple locations or to individual sites or users, and items inherit the retention settings assigned to the container. When retention settings are applied, people work with their files or emails in the usual way however the system transparently stores a copy of data in a secured location hidden from users whenever a file or message is modified or deleted.
For detailed information about how retention settings work for different workloads, see the following articles:
- Learn about retention for SharePoint and OneDrive
- Learn about retention for Microsoft Teams
- Learn about retention for Viva Engage (Yammer)
- Learn about retention for Exchange
Retention policies should be used to assign the same retention settings for content at a site or mailbox level, however for more granular application retention labels can be used to assign settings at an item level (folder, document, or email). Unlike retention policies, retention labels travel with the content if it's moved to another location in your Microsoft 365 tenant. Retention labels also provide features that retention policies don't, such as triggering a disposition review at the end of the retention period or marking the content as a record.
Retention labels can be applied manually or automatically based on keywords, patterns, sensitive information types or trainable classifiers. Sensitive Information Types can be used to recognize patterns representing confidential information in files and emails, such as personal data, financial account numbers, and medical data. Trainable Classifiers extend this approach by using Machine Learning to understand and classify an item based on what it is, recognizing resumes and source code immediately or organization-specific information such as contracts and work orders after a training period.
Retention policies and labels are essential components of a data lifecycle management plan and should be evaluated both in terms of a backup stand-in as well as their broader data governance implications.
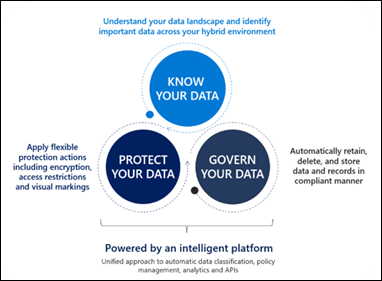
Exceptions to In-Place Retention
For some types of truly critical information, it may be practical to maintain a copy outside of the online services. Disaster recovery plans and an employee contact register stored in a SharePoint site would be of little value if power or communications failures meant you couldn't access the Internet, for example. Organizations should employ standard Risk Management practices to ensure they plan appropriately for significant events based on probability and impact. Identifying and classifying data can help to ensure the most important information can be stored in an alternate location without the cost of duplicating unnecessary data.
While not intended as backup or recovery solutions, OneDrive for Business and Outlook as part of Microsoft Office Apps for Enterprise both store copies of data synchronized with the cloud services on a user's local machine that can be accessed or even copied if access to the original data source in unavailable. The OneDrive client application could also be used to synchronize key documents to an offsite machine.
Third-party migration tools could be used to mirror content between online services and standby instances of Microsoft SharePoint Server or Microsoft Exchange Server in private cloud solutions. Such elaborate and costly solutions wouldn't be warranted for most organizations or users but could be implemented for business-critical data and accounts if determined to be necessary through a quantitative risk analysis.
Back up on-premises and cloud-based services with Azure Backup
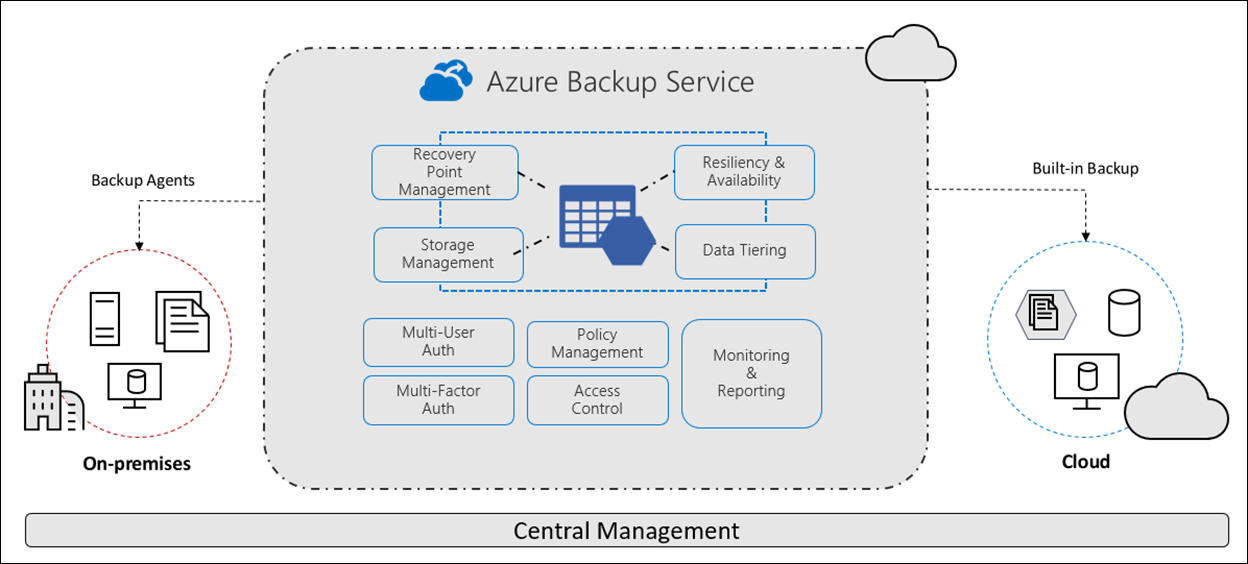
The Azure Backup service provides a simple, secure and cost-effective solution to back up and recover on-premises and cloud-based data from within Microsoft Azure. Native controls in Azure enable backups of Windows/Linux VMs, Azure Managed Disks, Azure Files shares, SQL databases, SAP HANA databases, and Azure Blobs. The Microsoft Azure Recovery Services (MARS) agent provides the ability to back up files, folders and system state from on-premises or virtual machines, and integration with on-premises Azure Backup Server (MABS) or System Center Data Protection Manager (DPM) servers to backup workloads such as Hyper-V VMs, Microsoft SQL Server, SharePoint Server, Microsoft Exchange, or even VMware VMs.
Azure Backup includes extensive security capabilities to protect data in transit and at rest, including fine-grained role-based access controls, encryption of data, protection from unintentional deletion, and monitoring and alerting of suspicious activity.
Management and control of identity and user access
Storage accounts used by Recovery Services vaults are isolated and can't be accessed by users for any malicious purposes. The access is only allowed through Azure Backup management operations, such as restore. Azure Backup enables you to control the managed operations through fine-grained access using Azure role-based access control (Azure RBAC). Azure RBAC allows you to segregate duties within your team and grant only the amount of access to users necessary to do their jobs.
Azure Backup provides three built-in roles to control backup management operations:
- Backup Contributor: to create and manage backups, except deleting Recovery Services vault and giving access to others
- Backup Operator: everything a contributor does except removing backup and managing backup policies
- Backup Reader: permissions to view all backup management operations
There's also some further detail on the specific abilities assigned to these three built-in roles at the following page Manage Backups with Azure role-based access control. Special consideration should also focus on the owners of Azure resources (for example, Azure resource Group owners) as they inherit permissions over their assets, including Azure Backup permissions.
To provide an extra layer of protection to critical operations on your Recovery Services vaults, Azure Backup supports multi-user authorization through Resource Guard. While Microsoft Entra Privileged Identity Management could be used to ensure backup admins must obtain approval to access elevated permissions, the user would then have access to all of the capabilities that role provides including modifying backup policies to reduce retention or disabling the soft delete feature that ensures deleted backups are available for a further 14 days. Resource Guard addresses authorization by requiring the backup admin to have permission both to the Recovery Services vault and the Resource Guard instance in a separate subscription or tenant.
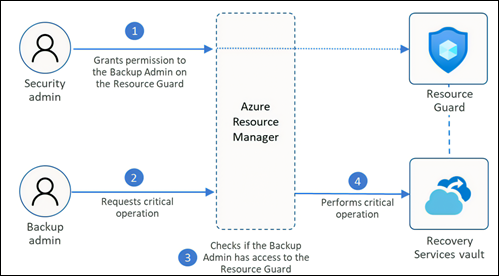
In order for a backup admin to perform a critical operation such as modifying a policy or disabling soft delete they would first need to obtain the Backup Contributor role in the subscription hosting Azure Backup and then the Contributor role on the Resource Guard, otherwise the action would fail. With PIM both elevations would be logged including capturing a justification as to why this was required, assigned for a short period of time and automatically revoked, and could even require approval from different administrators.
Manage Settings and Programs for Client Devices
Rather than backing up client devices to preserve setting and applications, modern management approaches ensure client devices are easily replaced with minimal impact to users. Data storage locations can automatically be redirected to and synchronized with cloud services, meaning any copies on the device are there to facilitate offline access only. Applications could be provisioned automatically based on user or device policies in a management solution such as Microsoft Intune, and application settings stored in a cloud-based user profile.
Windows Autopilot makes it easy for users to set up their own computer, whether it has been preconfigured by the organization or purchased new from a retailer, and can also be used to reset, repurpose, or recover devices.
Considerations for ransomware recovery and malicious actions
The previous sections have highlighted how data can be preserved within the Microsoft services as an alternative to traditional processes for backup and restore scenarios, however given the intent of the Essential 8 control it's worth paying specific attention to the impact of a ransomware incident and the deliberate actions of a rogue administrator or compromised privileged account.
Under a modern management and zero trust approach the endpoint itself should have negligible consequences because a client machine compromised by ransomware could be remotely wiped and reprovisioned by technologies such as Windows Autopilot without loss of data. Servers could be restored or recreated from backups of virtual machines or system state in Azure Backup, which would include restoring user files located on network shares. To recover a user's files stored in SharePoint Online or OneDrive for Business, you can restore the entire site to a previous point in time within the last 30 days as described later in this article in the section Restoring SharePoint and OneDrive to a Known Good State. In the rare case that the ransomware-deleted email messages these could likely be recovered from the Deleted Items.
Microsoft publishes specific guidance to Recover from a ransomware attack and call out options in Step 6 of that guidance for recovering emails - specifically, how an admin can utilize Exchange Online to Recover deleted messages in a user's mailbox, and how an end user can Recover deleted items in Outlook for Windows, including accessing the hidden 'Recoverable Items' folder.
Just as the services can be configured to retain or back up data, they could also be configured to purge data by someone with malicious intent, whether that's a disgruntled employee or an external actor with access to a compromised privileged account. In two real-world examples, an administrator was coerced to disable retention policies on an executive's account, allowing the executive to purge their files and emails to destroy evidence, and an external threat actor with access to an administrator's account was able to delete backups before launching a Wiper Attack against the organization. These scenarios highlight the need for a defence-in-depth approach including compensating controls to manage administrative privileges.
Microsoft 365 includes the Preservation Lock feature that can prevent administrators from disabling or deleting retention policies and labels or making them less restrictive. While this is an important capability for ensuring the security of your data and demonstrating regulatory compliance, it should be used with caution because no one - including a global administrator and even Microsoft Support - can turn it off.
Other options for protecting policies include tight controls on Role-based Access with Just-In-Time elevation and approval so that no user may obtain the necessary privileges on their own. These capabilities are described in more detail in the guide for Restricting Administrative Privileges.
For Azure Backup, Resource Guard provides an extra layer of security beyond Privileged Identity Management by requiring permissions from a separate subscription in order to perform protected operations such as deleting or modifying policies or disabling soft delete. Done properly, this can ensure approval and oversight by a separate team, meaning any changes to protected functions require the involvement of at least two or three individuals.
Getting Started
Set a Default Retention Policy
In order to protect data in Microsoft 365 you'll need to create a retention policy and apply it to the appropriate locations. Unlike retention labels, you can apply more than one retention policy to the same content, meaning you could create a standard organization-wide default and apply longer retention either at the container-level (retention policy) or item-level (retention label) where necessary.
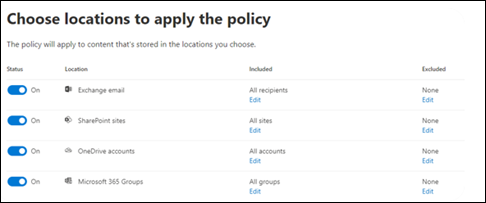
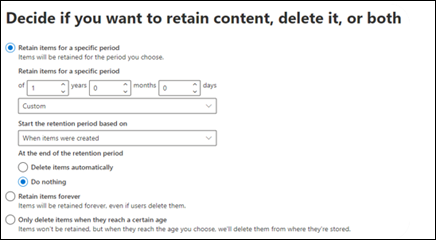
For example, create a retention policy in the Data lifecycle management solution in the Microsoft Purview portal that applies to all Exchange email recipients, all SharePoint sites, all OneDrive accounts, and all Microsoft 365 groups and set a policy to retain items for 1 year with no action at the end. The policy is applied to all existing locations and new locations created afterwards will inherit these settings. If an item is deleted it will be held in the appropriate location (Recoverable Items folder for Exchange, Preservation Hold library for SharePoint and OneDrive) for 1 year before the clean-up process is allowed to run. Items that weren't deleted will remain in their location when the 1-year hold expires and can stay there indefinitely, however if deleted after that they immediately move to the clean-up phase for permanent deletion in the appropriate service.
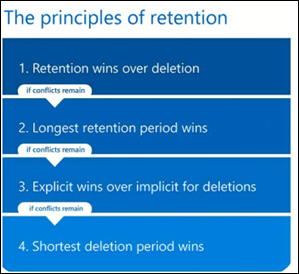
Longer retention settings can be enforced as necessary through more retention policies applied to specific users or sites, or with retention labels on items that contain sensitive information. Retention policies can have either an Adaptive or Static scope, and the options available in the policy may vary depending on this selection. Multiple policies may need to be created to cover all locations in the tenant as Teams and Viva Engage (Yammer) settings can't be defined in static policies that include other services.
Retain Content for Departed Users
The traditional approach to retaining content owned by users that have left the company may be to export the mailbox to a PST and store it with the personal files on a file server or offline storage medium, however organizations often want this data online so it's accessible not only for manual review by a manager or successor but to provide visibility of that data through eDiscovery solutions. Microsoft 365 will hold a user's data for 30 days by default after the license has been removed or the account deleted, during which time it can be accessed or reactivated if the user returns to the organization. To retain data after this period expires, Microsoft 365 retention policies and retention labels can prevent the deletion clean-up process from starting for as long as there's still content to be protected. This means if content is protected by a 1 year hold as defined in the previous section, then a user who leaves the organization will have their emails and files retained by Microsoft 365 for at least the next year even after the account has been deleted and the license reassigned.
While Exchange Online still supports legacy litigation hold functionality whereby the entire mailbox and archive can be protected until such time as the hold is removed, Microsoft instead recommends the use of Microsoft 365 retention to apply different settings based on the content and manage what should happen to data when the retention period expires.
For more information on managing former employees in Microsoft 365 on Managing former employees.
| ISM control Mar 2024 | Maturity | Control | Measure |
|---|---|---|---|
| 1511 | 1, 2, 3 | Backups of data, applications, and settings are performed and retained in accordance with business criticality and business continuity requirements. | Microsoft 365 retention ensures data stored within the services is captured and retained in a highly resilient environment. Retention labels and/or policies must be configured as described previously, however there's no requirement to schedule or run a specific copy process as files are preserved through normal write or delete operations. |
| 1515 | 1, 2, 3 | Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. | Retention labels and/or policies should be validated such that data retention performs as expected. |
| 1705 | 2, 3 | Privileged accounts (excluding backup administrator accounts) can't access backups belonging to other accounts. | Access to data covered by Retention labels and/or policies should be verified so that access is well understood. Special care should be taken to ensure privileged accounts can't access backups of other accounts nor their own in addition to verification. |
| 1707 | 2, 3 | Privileged accounts (excluding backup administrator accounts) are prevented from modifying and deleting backups. | Access to data covered by Retention labels and/or policies should be verified so that access is well understood. Special care should be taken to ensure privileged accounts can't access backups of other accounts nor their own in addition to verification. |
| 1810 | 1, 2, 3 | Backups of data, applications, and settings are synchronized to enable restoration to a common point in time. | Retention policies are stored as part of the Microsoft 365 service, and management and governance of these policies should be managed appropriately. |
| 1811 | 1, 2, 3 | Backups of data, applications, and settings are retained in a secure and resilient manner. | Retention policies are stored as part of the Microsoft 365 service, and management and governance of these policies should be managed appropriately. |
Restore Deleted Mailbox Items as a User
When a user deletes an item in their mailbox, it's moved to the Deleted Items folder and can be recovered by opening the folder and dragging the item back to the desired location. If the user deletes the item from Deleted Items, empties the Deleted Items folder, or permanently deleted the item from another folder by pressing Shift+Delete then the item will be stored in the Recoverable Items folder.
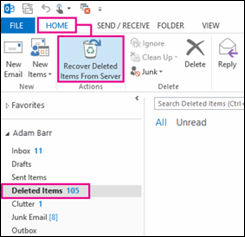
To restore an item from the Recoverable Items folder, users can select the option to Recover Deleted Items from the toolbar in the Outlook desktop application or by right-clicking on the Deleted Items folder in Outlook on the web. The appropriate items can then be selected and restored, which will return the item to the Deleted Items folder where it can then be moved to a more permanent location. Users may also purge items from the Recover Deleted Items interface, at which point they can only be recovered by an administrator.
More information on recovering deleted items is available from Recover deleted items in Outlook for Windows and Recover deleted items or email in Outlook Web App.
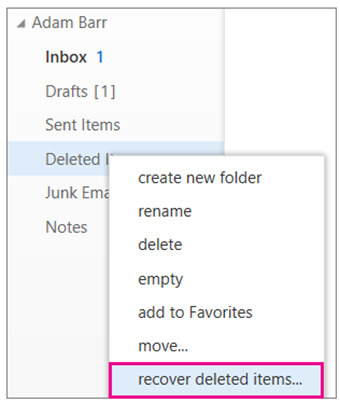
Restoring Deleted Mailbox Items as an Administrator
Administrators can recover deleted items on behalf of a user through several means.
To recover deleted items for a single user, administrators can select the Recover deleted items option within the Mailbox settings for a recipient in the new Exchange Admin Center.
Administrators may also use Exchange Online PowerShell to recover deleted items using the Get-RecoverableItems and Restore-RecoverableItems commands. With both the Exchange Admin Center and PowerShell methods, items are restored to their original locations.
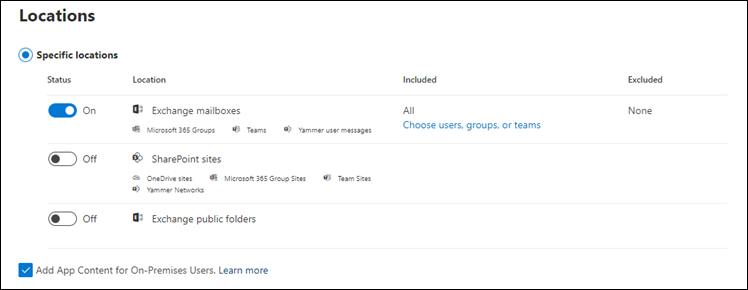
To search for messages across multiple users, administrators can use the Content Search feature in the Microsoft Purview compliance portal.
Once the search has completed a detailed report of the results are available, and administrators may further refine the query or export the results to PST files.
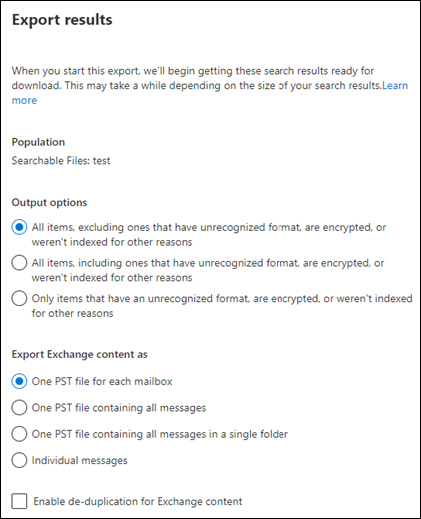
The Content Search approach can also be used to recover files stored in SharePoint Online and is the same mechanism for finding and exporting content as that used in a Standard eDiscovery case.
| ISM control Mar 2024 | Maturity | Control | Measure |
|---|---|---|---|
| 1515 | 1, 2, 3 | Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. | Restoration of mailbox items by both users and administrators should be documented, tested and validates to ensure the process is defined and understood. |
Restoring a Previous Version of a File in SharePoint and OneDrive
Versioning is enabled by default on all lists and libraries in SharePoint Online and OneDrive for Business, with the last 500 versions of a document retained automatically. SharePoint stores only the changes between files to optimize storage requirements however versioning does contribute to site quotas and can be adjusted on individual lists and libraries as required.
To restore a previous version of a file in SharePoint or OneDrive through the browser open the document library, select the file to be restored, select the ellipses and select Version History. Individual versions can be viewed and restored or even deleted if necessary to save space.
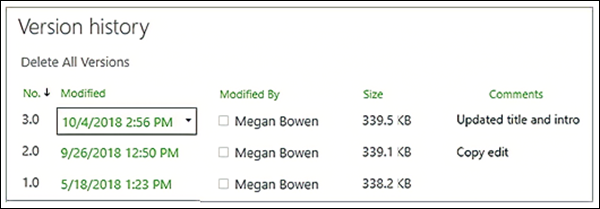
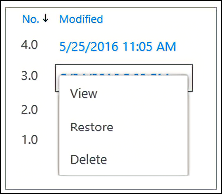
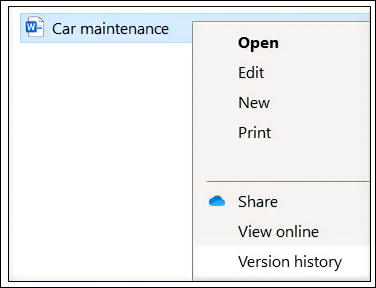
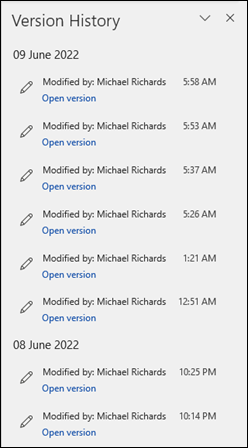
Version history can also be accessed in Explorer by right-selecting on a file or in Microsoft 365 Apps for enterprise through File > Info:
| ISM control Mar 2024 | Maturity | Control | Measure |
|---|---|---|---|
| 1515 | 1, 2, 3 | Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. | While data retained in Microsoft 365 services may not require restoration testing for the purposes of ensuring successful backup completion, you should ensure you understand the various options for recovering files, sites, or e-mail messages within the platform and which would be appropriate for a given scenario. Microsoft 365 makes restoration capabilities available directly to the end user in a self-service fashion, so appropriate documentation and Helpdesk services should be available to anyone with questions. |
Restoring SharePoint and OneDrive to a Known Good State
If many of your files in OneDrive or a SharePoint document library were deleted, overwritten, corrupted, or infected by malware you can restore the entire library to a previous point within the past 30 days. From the Settings icon in the top-right select Restore your OneDrive or Restore this library:
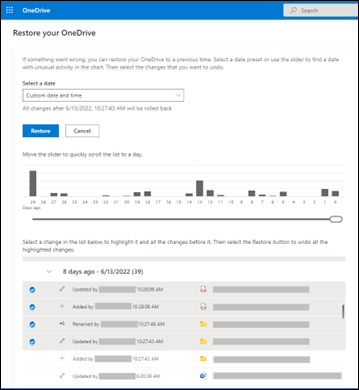
Select Yesterday, One week ago, Three weeks ago, or Custom date and time from the drop-down box and the slider will adjust accordingly with the appropriate files selected. Once you're happy select Restore and the highlighted changes are undone:
More information on recovering missing, deleted, or corrupted items is available from How to recover missing, deleted, or corrupted items in SharePoint and OneDrive.
| ISM control Mar 2024 | Maturity | Control | Measure |
|---|---|---|---|
| 1511 | 1, 2, 3 | Backups of data, applications, and settings are performed and retained in accordance with business criticality and business continuity requirements. | Files could be stored in SharePoint Online/OneDrive for Business or on a file share and backed up either way through Microsoft 365 retention or Azure Backup. |
| 1515 | 1, 2, 3 | Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. | While data retained in Microsoft 365 services may not require restoration testing for the purposes of ensuring successful backup completion, you should ensure you understand the various options for recovering files, sites, or e-mail messages within the platform and which would be appropriate for a given scenario. It is valuable to ensure that this understanding of the options for recovering files, sites and e-mails should be reinforced regularly to ensure administrators and/or IT personnel remain up to date on the latest processes. |
Configuring Azure Backup
The process to configure Azure Backup depends on the services you wish to protect, however the first step will always be the creation of the vaults in which to store backups. Azure offers two types of vaults, Recovery Services vaults and Backup vaults, and which type you need to create will be dictated by the data sources you intend to use.
Recovery Services vaults typically house copies of data or configuration information for services such as Azure Virtual Machines, Azure Files, and Azure SQL databases, and support integration with System Center Data Protection Manager, Windows Server, and Azure Backup Server. Recovery Services vaults support the soft delete function, which maintains copies of deleted backups for 14 days with no other cost implications.
Backup vaults houses backup data for newer Azure workloads such as Azure Database for PostgreSQL, Azure Blobs, Azure Disks, Kubernetes Service, and AVS Virtual Machines.
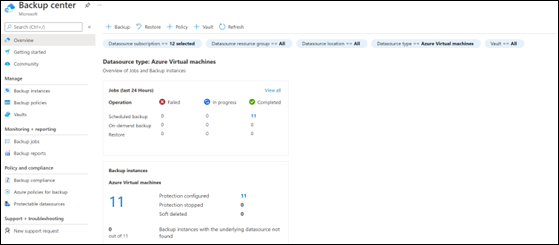
Vaults and backups can be created through the Azure Backup Center provides a single unified management experience to govern, monitor, operate, and analyze backups at scale.
Detailed guidance for configuring the various backup operations is available from Microsoft Docs, for example: Azure VM, SQL on Azure VM, Azure Disk, Azure Blobs, and Azure Files.
The Microsoft Azure Recovery Services (MARS) agent can be used to back up files, folders, and the volume or system state from on-premises computers, or even to back up individual files and folders from an Azure virtual machine. The MARS agent can be downloaded and installed on an individual server for direct backup to Azure, or on a Microsoft Azure Backup Server (MABS) or System Center Data Protection Manager (DPM) server; in this scenario, machines and workloads backup to MABS/DPM and then the MARS agent is used to back up to an Azure vault.
To protect on-premises workloads such as Hyper-V virtual machines, Microsoft SQL Server, SharePoint Server, and Microsoft Exchange, install the Microsoft Azure Backup Server on a domain-joined server. MABS can also now be used to protect VMware VMs.
| ISM control Mar 2024 | Maturity | Control | Measure |
|---|---|---|---|
| 1511 | 1, 2, 3 | Backups of data, applications, and settings are performed and retained in accordance with business criticality and business continuity requirements. | Azure Backup offers a simple solution for backing up resources to the cloud, with options for locally- and geographically redundant storage. Backups can be performed on-demand or on a schedule and may include software and server configuration information through the Windows Server System State. |
| 1515 | 1, 2, 3 | Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. | Azure Backup offers a wide range of traditional backup services across on-premises and cloud workloads. Restoration options vary depending on the workload but in general you can select a point in time to restore to and whether to recover to the original or an alternate location. Test plans should incorporate all options. |
Microsoft 365 Backup
The Microsoft 365 Backup service is Microsoft's born-in-the-cloud backup solution to backup data located on-premises and in Azure. It replaces your existing on-premises or offsite backup solution with a reliable, secure, and cost competitive cloud backup solution. It also provides the flexibility of protecting your assets running in the cloud.
Key architectural takeaways:
- Data never leaves the Microsoft 365 data trust boundary or the geographic locations of your current data residency.
- The backups are immutable unless expressly deleted by the Backup tool admin via product offboarding.
- OneDrive, SharePoint, and Exchange have multiple physically redundant copies of your data to protect against physical disasters.
Using the Microsoft 365 Desired State Configuration (DSC) Tool to Manage Tenant Configuration
Microsoft 365 DSC is an Open-Source initiative lead by Microsoft engineers and maintained by the community that allows you to write a definition for how your Microsoft 365 tenant should be configured, automate the deployment of that configuration and ensures the monitoring of the defined configuration, notifying and acting on detected configuration drifts. It also allows you to extract a full-fidelity configuration out of any existing Microsoft 365 tenant, including major workloads such as Exchange Online, Teams, SharePoint, OneDrive, Security and Compliance, Power Platforms, Intune and Planner.
The Microsoft 365 DSC user guide is available and can help you get started. The tool can be used in many ways depending on the preferences of your organization: in the simplest form, the tool can be used to extract the configuration from your Microsoft 365 tenant and save it as a series of files in case recovery or restoration is needed in future. Another option would be to maintain a staging tenant and deploy all changes to the production environment through the tool.
| ISM control Mar 2024 | Maturity | Control | Measure |
|---|---|---|---|
| 1511 | 1, 2, 3 | Backups of data, applications, and settings are performed and retained in accordance with business criticality and business continuity requirements. | Configuration settings for the Microsoft 365 environment can be captured with the Microsoft 365DSC tool, either as a user-friendly Excel or HTML report, or as an export package that can be used to reset the tenant configuration. |
| 1515 | 1, 2, 3 | Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. | Microsoft 365DSC tool can be used to import previously captured configuration data for restore purposes. |
Level 1 Requirements
Backups of data, applications, and settings are performed and retained in accordance with business criticality and business continuity requirements
Microsoft 365 retention ensures data stored within the services is captured and retained in a highly resilient environment. Retention labels and/or policies must be configured as described previously, however there's no requirement to schedule or run a specific copy process as files are preserved through normal write or delete operations.
Azure Backup offers a simple solution for backing up resources to the cloud, with options for locally- and geographically redundant storage. Backups can be performed on-demand or on a schedule and may include software and server configuration information through the Windows Server System State.
Configuration settings for the Microsoft 365 environment can be captured with the Microsoft 365DSC tool, either as a user-friendly Excel or HTML report, or as an export package that can be used to reset the tenant configuration. Files could be stored in SharePoint Online/OneDrive for Business or on a file share and backed up either way through Microsoft 365 retention or Azure Backup.
Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises
While data retained in Microsoft 365 services may not require restoration testing for the purposes of ensuring successful backup completion, you should ensure you understand the various options for recovering files, sites, or e-mail messages within the platform and which would be appropriate for a given scenario. Microsoft 365 makes restoration capabilities available directly to the end user in a self-service fashion, so appropriate documentation and Helpdesk services should be available to anyone with questions. This understanding of the options for recovering files, sites, and e-mail messages should be reinforced regularly through the disaster recovery exercises.
Azure Backup offers a wide range of traditional backup services across on-premises and cloud workloads. Restoration options vary depending on the workload but in general you can select a point in time to restore to and whether to recover to the original or an alternate location. Test plans should incorporate all options.
Unprivileged Accounts Can't Access Backups Belonging to Other Accounts
With Microsoft 365 in-place retention there's no separate copy of the data and access is based on the location of the information. For example, all users with Read permissions can view the version history of a file in SharePoint Online, however only a user with Contribute permissions may actually restore a previous version. Regarding the control, this means unprivileged accounts can't access more information than they already have access to.
Backup Contributor, Backup Operator, or Backup Reader roles must be granted in order to access Azure Backups, and therefore by definition unprivileged accounts wouldn't have any access to data.
Unprivileged Accounts are Prevented from Modifying or Deleting Backups
No user, privileged or otherwise, is able to modify or delete retained copies of data in Microsoft 365.
Unprivileged accounts don't have access to Azure Backup at all, let alone permissions to modify or delete backups.
Level 2 Requirements
Unprivileged Accounts Can't Access Backups Belonging to Other Accounts
There are no separate backups in Microsoft 365 for unprivileged accounts to access, and they would only be able to see versions of files they already have access to. In general, if the intent of the control is to ensure users aren't able to gain access to information through a backup repository that they would otherwise be unable to see, then Microsoft 365 would comply with the requirement as there's no duplication of content as part of in-place retention - unprivileged accounts can only access data for which they're authorized, and even privileged accounts must be granted specific access rights.
Unprivileged Accounts, and Privileged Accounts (Excluding Backup Administrators), are Prevented from Modifying or Deleting Backups
No user, privileged or otherwise, is able to modify or delete retained copies of data in Microsoft 365. Privileged users could however modify or delete retention policies such that information is no longer preserved. Preservation lock can be used to ensure no one - including global admins - can turn off the policy, delete the policy, or make it less restrictive. While this can help protect against rogue administrators, it's critical you understand the impact to your organization before deciding whether to utilize this control.
Under the RBAC model for Azure Backup, only Backup Contributors have permission to modify or delete backups. Azure Backup also provides a soft delete function that is enabled by default and retains deleted backups for an extra 14 days if accidental or malicious deletion.
Level 3 Requirements
Unprivileged Accounts, and Privileged Accounts (Excluding Backup Administrators), Can't Access Backups
There are no separate backups in Microsoft 365 for privileged or unprivileged accounts to access. While users can access retained files and versions of which, there's no distinction between accessing this data as the primary copy versus a backup.
Unprivileged accounts or privileged accounts not granted appropriate permissions don't have any access to Azure Backup and therefore can't access backups.
Unprivileged Accounts, and Privileged Accounts (Excluding Backup Break Glass Accounts), are Prevented from Modifying or Deleting Backups
As with the Maturity Level 2 requirement, no user, privileged or otherwise, is able to modify or delete retained copies of data in Microsoft 365.
Only Backup Contributors have permission to modify or delete backups in Azure Backup. To ensure only backup break glass accounts have these permissions, only grant this role to such accounts.
Managing Maturity Levels with Microsoft Platform
The following information provides guidance on implementation actions to achieve desired maturity level for regular backups. The Microsoft security and compliance platform can be used to achieve the implementation and track compliance. Microsoft Purview Compliance Manager provide templates to assess, manage, and track the implementation of Essential Eight controls.
Organizations can choose the Essential Eight template and create assessments based on the maturity level they're targeting. The assessment template provides actionable guidance for implementing the improvement actions to achieve the desired maturity level. Refer to the ACSC's Essential Eight Maturity Model for more details.
Reference - Articles
- Resiliency and continuity overview
- What is the Azure Backup service?
- Introduction - Microsoft365DSC - Your Cloud Configuration
- Learn about retention policies and retention labels
- Create and manage inactive mailboxes
- Malware and ransomware protection in Microsoft 365
- Deploy ransomware protection for your Microsoft 365 tenant
- Essential Eight Maturity Model to ISM Mapping
Reference - Maturity Levels
| ISM Control Mar 2024 | Level 1 | Level 2 | Level 3 |
|---|---|---|---|
| 1511 Backups of data, applications, and settings are performed and retained in accordance with business criticality and business continuity requirements. | Y | Y | Y |
| 1810 Backups of data, applications, and settings are synchronized to enable restoration to a common point in time. | Y | Y | Y |
| 1811 Backups of data, applications, and settings are retained in a secure and resilient manner. | Y | Y | Y |
| 1515 Restoration of data, applications, and settings from backups to a common point in time is tested as part of disaster recovery exercises. | Y | Y | Y |
| 1812 Unprivileged accounts can't access backups belonging to other accounts. | Y | Y | Y |
| 1814 Unprivileged accounts are prevented from modifying and deleting backups. | Y | Y | Y |
| 1813 Unprivileged accounts can't access backups belonging to other accounts, nor their own accounts. | N | Y | Y |
| 1705 Privileged accounts (excluding backup administrator accounts) can't access backups belonging to other accounts | N | Y | Y |
| 1707 Privileged accounts (excluding backup administrator accounts) are prevented from modifying and deleting backups. | N | Y | Y |
| 1706 Privileged accounts (excluding backup administrator accounts) can't access their own backups. | N | N | Y |
| 1708 Backup administrator accounts are prevented from modifying and deleting backups during their retention period. | N | N | Y |
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for