Poznámka:
Přístup k této stránce vyžaduje autorizaci. Můžete se zkusit přihlásit nebo změnit adresáře.
Přístup k této stránce vyžaduje autorizaci. Můžete zkusit změnit adresáře.
Tento dokument vám pomůže nastavit ukázkovou aplikaci, která používá následující prostředky z rozhraní API brány. Jsou poskytovány kroky pro:
- Vytvořte prostředek Gateway s jedním HTTPS listenerem.
- Vytvořte prostředek HTTPRoute , který odkazuje na back-endovou službu.
- Vytvořte prostředek BackendTLSPolicy , který má certifikát klienta a certifikační autority pro back-endovou službu odkazovanou v httpRoute.
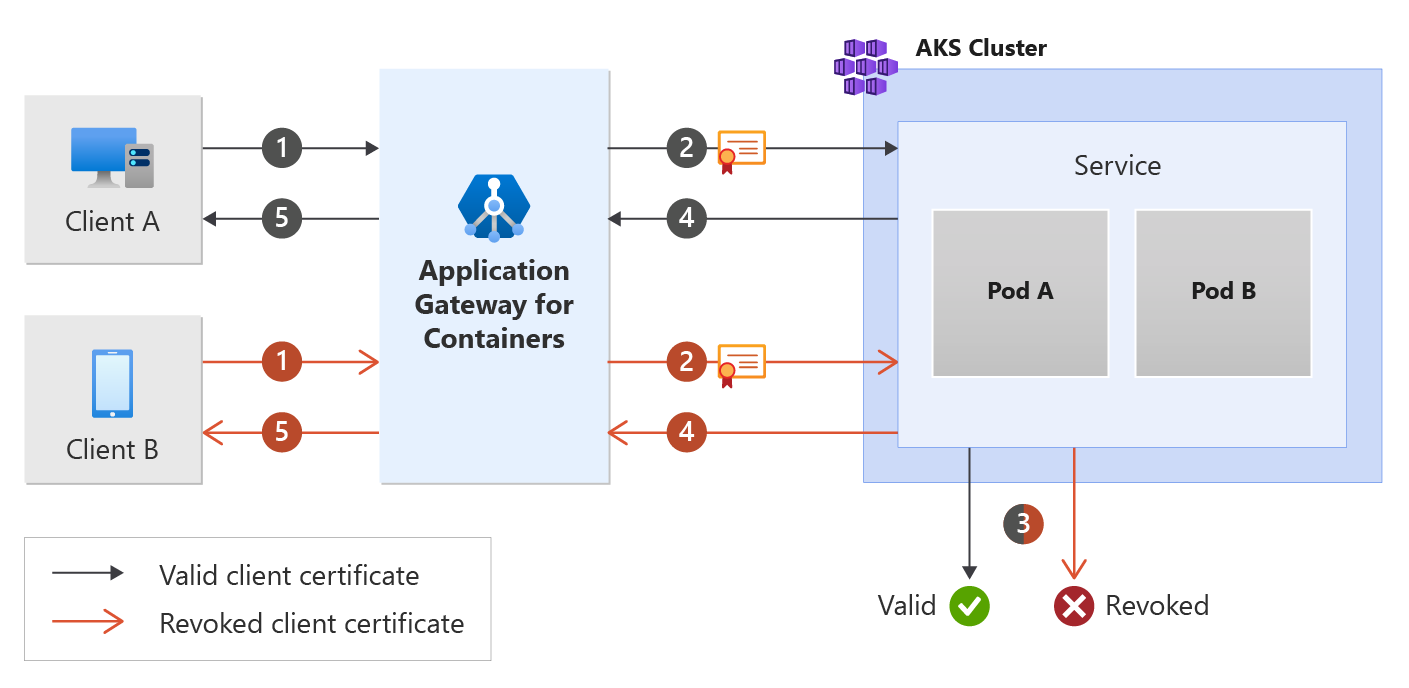
Background
Mutual Transport Layer Security (MTLS) je proces, který spoléhá na certifikáty k šifrování komunikace a identifikaci klientů do služby. To umožňuje back-endovým úlohám dále zvýšit stav zabezpečení tím, že důvěřují jenom připojení z ověřených zařízení.
Podívejte se na následující obrázek:
Požadavky
Pokud sledujete strategii nasazení BYO, ujistěte se, že jste nastavili prostředky Application Gateway pro kontejnery a ALB Controller.
Pokud postupujete podle strategie nasazení spravované ALB, ujistěte se, že zřídíte ALB Controller a prostředky Application Gateway pro kontejnery prostřednictvím vlastního prostředku ApplicationLoadBalancer.
Nasazení ukázkové aplikace HTTP:
Pomocí následujícího souboru deployment.yaml v clusteru vytvořte ukázkovou webovou aplikaci a nasaďte ukázkové tajné kódy, které demonstrují vzájemné ověřování back-endu (mTLS).
kubectl apply -f https://raw.githubusercontent.com/MicrosoftDocs/azure-docs/refs/heads/main/articles/application-gateway/for-containers/examples/https-scenario/end-to-end-ssl-with-backend-mtls/deployment.yamlTento příkaz vytvoří v clusteru následující:
- Obor názvů s názvem
test-infra - Jedna služba nazvaná
mtls-appv prostoru jmentest-infra - Jedno nasazení nazvané
mtls-appvtest-infranamespace. - Jedna konfigurační mapa nazývaná
mtls-app-nginx-cmv jmenném prostorutest-infra - Čtyři tajemství nazvaná
backend.com,frontend.com,gateway-client-cert, aca.bundlevtest-infrajmenném prostoru
- Obor názvů s názvem
Nasadit požadované prostředky rozhraní Gateway API
Vytvoření brány
kubectl apply -f - <<EOF
apiVersion: gateway.networking.k8s.io/v1
kind: Gateway
metadata:
name: gateway-01
namespace: test-infra
annotations:
alb.networking.azure.io/alb-namespace: alb-test-infra
alb.networking.azure.io/alb-name: alb-test
spec:
gatewayClassName: azure-alb-external
listeners:
- name: https-listener
port: 443
protocol: HTTPS
allowedRoutes:
namespaces:
from: Same
tls:
mode: Terminate
certificateRefs:
- kind : Secret
group: ""
name: frontend.com
EOF
Poznámka:
Když kontroler ALB vytvoří prostředky Application Gateway pro kontejnery v Azure Resource Manageru, použije pro front-endový prostředek následující zásady vytváření názvů: fe-<eight randomly generated characters>
Pokud chcete změnit název front-endového prostředku vytvořeného v Azure, zvažte použití vlastní strategie nasazení.
Po vytvoření prostředku brány se ujistěte, že stav je platný, naslouchací modul je naprogramován a brána má přiřazenou adresu.
kubectl get gateway gateway-01 -n test-infra -o yaml
Příklad výstupu úspěšného vytvoření brány:
status:
addresses:
- type: IPAddress
value: xxxx.yyyy.alb.azure.com
conditions:
- lastTransitionTime: "2023-06-19T21:04:55Z"
message: Valid Gateway
observedGeneration: 1
reason: Accepted
status: "True"
type: Accepted
- lastTransitionTime: "2023-06-19T21:04:55Z"
message: Application Gateway For Containers resource has been successfully updated.
observedGeneration: 1
reason: Programmed
status: "True"
type: Programmed
listeners:
- attachedRoutes: 0
conditions:
- lastTransitionTime: "2023-06-19T21:04:55Z"
message: ""
observedGeneration: 1
reason: ResolvedRefs
status: "True"
type: ResolvedRefs
- lastTransitionTime: "2023-06-19T21:04:55Z"
message: Listener is accepted
observedGeneration: 1
reason: Accepted
status: "True"
type: Accepted
- lastTransitionTime: "2023-06-19T21:04:55Z"
message: Application Gateway For Containers resource has been successfully updated.
observedGeneration: 1
reason: Programmed
status: "True"
type: Programmed
name: https-listener
supportedKinds:
- group: gateway.networking.k8s.io
kind: HTTPRoute
Po vytvoření brány vytvořte prostředek HTTPRoute.
kubectl apply -f - <<EOF
apiVersion: gateway.networking.k8s.io/v1
kind: HTTPRoute
metadata:
name: https-route
namespace: test-infra
spec:
parentRefs:
- name: gateway-01
rules:
- backendRefs:
- name: mtls-app
port: 443
EOF
Po vytvoření prostředku HTTPRoute se ujistěte, že je trasa Přijata a prostředek Application Gateway pro kontejnery je naprogramován.
kubectl get httproute https-route -n test-infra -o yaml
Ověřte, že stav prostředku služby Application Gateway for Containers byl úspěšně aktualizován.
status:
parents:
- conditions:
- lastTransitionTime: "2023-06-19T22:18:23Z"
message: ""
observedGeneration: 1
reason: ResolvedRefs
status: "True"
type: ResolvedRefs
- lastTransitionTime: "2023-06-19T22:18:23Z"
message: Route is Accepted
observedGeneration: 1
reason: Accepted
status: "True"
type: Accepted
- lastTransitionTime: "2023-06-19T22:18:23Z"
message: Application Gateway For Containers resource has been successfully updated.
observedGeneration: 1
reason: Programmed
status: "True"
type: Programmed
controllerName: alb.networking.azure.io/alb-controller
parentRef:
group: gateway.networking.k8s.io
kind: Gateway
name: gateway-01
namespace: test-infra
Vytvořit BackendTLSPolicy
kubectl apply -f - <<EOF
apiVersion: alb.networking.azure.io/v1
kind: BackendTLSPolicy
metadata:
name: mtls-app-tls-policy
namespace: test-infra
spec:
targetRef:
group: ""
kind: Service
name: mtls-app
namespace: test-infra
default:
sni: backend.com
ports:
- port: 443
clientCertificateRef:
name: gateway-client-cert
group: ""
kind: Secret
verify:
caCertificateRef:
name: ca.bundle
group: ""
kind: Secret
subjectAltName: backend.com
EOF
Po vytvoření objektu BackendTLSPolicy zkontrolujte stav objektu a ujistěte se, že je zásada platná:
kubectl get backendtlspolicy -n test-infra mtls-app-tls-policy -o yaml
Příklad výstupu platného vytvoření objektu BackendTLSPolicy:
status:
conditions:
- lastTransitionTime: "2023-06-29T16:54:42Z"
message: Valid BackendTLSPolicy
observedGeneration: 1
reason: Accepted
status: "True"
type: Accepted
Otestování přístupu k aplikaci
Nyní jsme připraveni směrovat provoz do naší ukázkové aplikace prostřednictvím plně kvalifikovaného názvu domény přiřazeného k frontendu. K získání plně kvalifikovaného názvu domény použijte následující příkaz:
fqdn=$(kubectl get gateway gateway-01 -n test-infra -o jsonpath='{.status.addresses[0].value}')
Curling tohoto FQDN by měl vracet odpovědi z back-endu, jak je nakonfigurováno na HTTPRoute.
curl --insecure https://$fqdn/
Blahopřejeme, nainstalovali jste kontroler ALB, nasadili back-endovou aplikaci a směrovali provoz do aplikace prostřednictvím příchozího přenosu dat ve službě Application Gateway for Containers.