Skype for Business topologies supported with Modern Authentication
This article lists what online and on-premises topologies are supported with Modern Authentication in Skype for Business, and security features that apply to each topology.
Modern Authentication in Skype for Business
Skype for Business can use security advantages of Modern Authentication. Because Skype for Business works closely with Exchange, the sign in behavior Skype for Business client users see will also be affected by the MA status of Exchange. This will also apply if you have a Skype for Business split-domain hybrid. That's numerous moving parts, but the aim here's an easy to visualize list of supported topologies.
Given Skype for Business, Skype for Business online, Exchange Server, and Exchange online, what topologies are supported with MA?
Supported MA topologies in Skype for Business
There are potentially two server applications, and two Microsoft 365 or Office 365 workloads, involved with Skype for Business topologies used by MA.
Skype for Business server (CU 5) on-premises
Skype for Business online (SFBO)
Exchange server on-premises
Exchange server online (EXO)
Another important part of MA is knowing where the authentication (authN) and authorization (authZ) of users take place. The two options are:
Microsoft Entra ID, online in the Microsoft Cloud
Active Directory Federation Server (ADFS) on-premises
So it looks a bit like this, with EXO and SFBO in the Cloud with Microsoft Entra ID, and Exchange Server (EXCH) and Skype for Business server (SFB) on-premises.
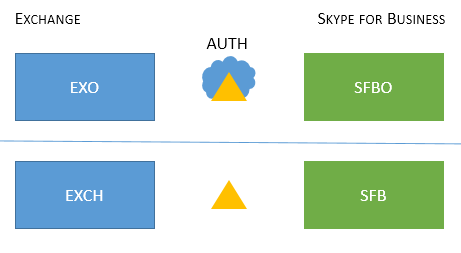
Here are the supported topologies. Note the key for the graphics:
If the icon is dimmed or grey, it isn't used in the scenario.
EXO is Exchange Online.
SFBO is Skype for Business Online.
EXCH is Exchange on-premises.
SFB is Skype for Business on-premises.
Authorizing servers are represented by triangles, for example, the Microsoft Entra ID is a triangle with a cloud behind it.
Arrows point at the authorizing server that will be used to when clients try to reach the specified server resource.
First, let's cover MA with Skype for Business in both On-premises-only or Cloud-only topologies.
Important
Are you ready to set up Modern Authentication in Skype for Business Online? The steps to enable this feature are right here.
| Topology name |
Example |
Description |
Supported |
|---|---|---|---|
| Cloud only |
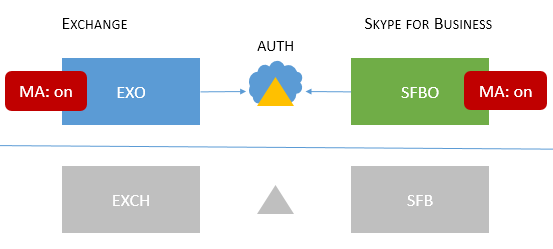 Users homed/mailboxes located: Online Users homed/mailboxes located: Online |
MA is on for both EXO and SFBO. Therefore, the authorization server is Microsoft Entra ID. |
Multifactor authentication (MFA), Client-certificate based authentication (CBA), Conditional Access (CA)/Mobile Application Management (MAM) with Intune. * |
| On-premises only |
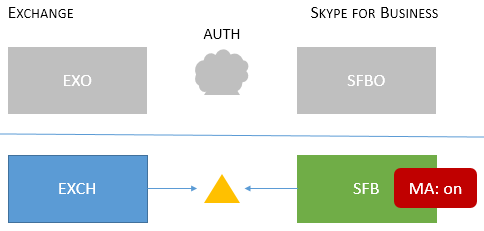 Users homed/mailboxes located: On-premises Users homed/mailboxes located: On-premises |
MA is on for SFB on-premises. Therefore, the authorization server is ADFS. For configuration details, see this article. |
MFA (Windows Desktop only - mobile clients aren't supported). No Exchange integration features. We do not recommend this approach. Please see here: https://aka.ms/ModernAuthOverview |
Important
It's recommended that the MA state be the same across Skype for Business and Exchange (and their online counterparts) to reduce the number of prompts.
Mixed topologies involve combinations of SFB split-domain hybrids. These are the Mixed topologies currently supported:
| Topology name |
Example |
Description |
Supported |
|---|---|---|---|
| Mixed 1 |
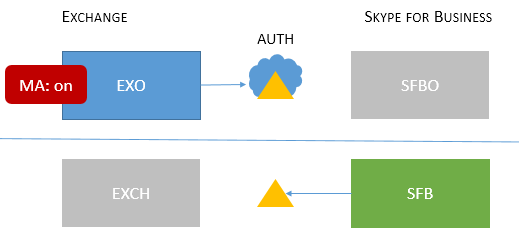 Users homed/mailboxes located: EXO and SFB |
MA isn't enabled for SFB; no SFB MA features available in this topology. |
No MA features for SFB. |
| Mixed 2 |
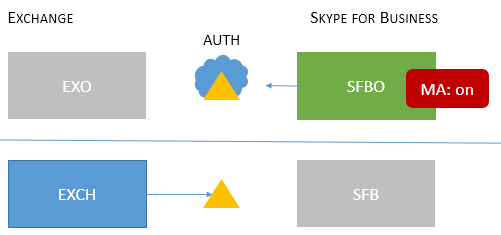 Users homed/mailboxes located: EXCH and SFBO |
MA is on for SFBO only. The authorization server is Microsoft Entra ID for users homed in SFBO, but AD for EXCH on-premises. |
MFA, CBA, CA/MAM with Intune.* |
| Mixed 3 |
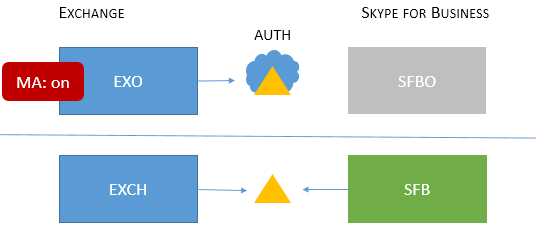 Users homed/mailboxes located: EXO + SFB, or EXCH + SFB |
No SFB MA features available in this topology |
No MA features for SFB. |
| Mixed 4 |
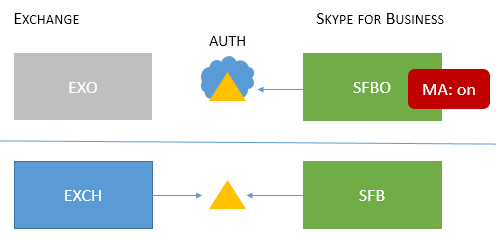 Users homed/mailboxes located: EXCH +SFBO or EXCH + SFB |
MA is on for SFBO, therefore the authorization server is Microsoft Entra ID for users homed in SFBO. On-premises users in SFB and EXO use AD. |
MFA, CBA, CA/MAM with Intune for online users only.* |
| Mixed 5 |
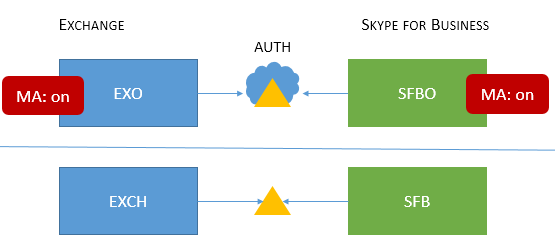 Users homed/mailboxes located: EXO + SFBO, EXO + SFB, EXCH + SFBO, or EXCH + SFB |
MA is on in both EXO and SFBO, therefore the authorization server is Microsoft Entra ID for users homed in SFBO; on-premises users in EXCH and SFB use AD. |
MFA, CBA, CA/MAM with Intune for online users only.* |
| Mixed 6 |
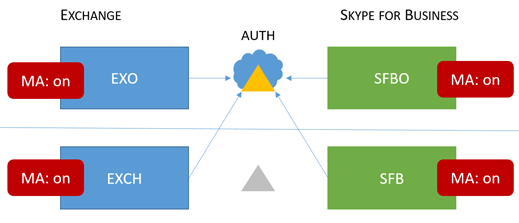 Users homed/mailboxes located: EXO + SFBO, EXO + SFB, EXCH + SFBO, or EXCH + SFB |
MA is on everywhere, therefore the authorization server is Microsoft Entra ID for all users. (online and on-premises) See https://aka.ms/ModernAuthOverview for deployment steps. |
MFA, CBA, and CA/MAM (via Intune) for all users. |
* - MFA includes Windows Desktop, MAC, iOS, Android devices, and Windows Phones; CBA includes Windows Desktop, iOS, and Android devices; CA/MAM with Intune, includes Android and iOS devices.
Important
It's very important to note that users may see multiple prompts in some cases, notably where the MA state is not the same across all the server resources that clients may need and request, as is the case with all versions of the Mixed topologies.
Important
Also note that in some cases (Mixed 1, 3, and 5 specifically) an AllowADALForNonLyncIndependentOfLync registry key must be set for proper configuration for Windows Desktop Clients.