Poznámka:
Přístup k této stránce vyžaduje autorizaci. Můžete se zkusit přihlásit nebo změnit adresáře.
Přístup k této stránce vyžaduje autorizaci. Můžete zkusit změnit adresáře.
Platí pro: Windows Server 2025, Windows Server 2022, Windows Server 2019, Windows Server 2016
Důležitý
Viz Docker Container Networking pro obecné síťové příkazy, možnosti a syntaxi Dockeru. S výjimkou všech případů popsaných v nepodporovaných funkcích a možnostech sítějsou všechny síťové příkazy Dockeru podporovány ve Windows se stejnou syntaxí jako v Linuxu. Síťové zásobníky windows a Linuxu se ale liší a například zjistíte, že některé síťové příkazy Linuxu (například ifconfig) nejsou ve Windows podporované.
Základní síťová architektura
Toto téma obsahuje přehled o tom, jak Docker vytváří a spravuje hostitelské sítě ve Windows. Kontejnery Windows fungují podobně jako virtuální počítače, pokud jde o sítě. Každý kontejner má virtuální síťový adaptér (vNIC), který je připojený k virtuálnímu přepínači Hyper-V (vSwitch). Systém Windows podporuje pět různých síťových ovladačů nebo režimů, které lze vytvářet prostřednictvím Dockeru: nat, overlay, transparent, l2bridgea l2tunnel. V závislosti na infrastruktuře fyzické sítě a požadavcích na síť s více hostiteli byste měli zvolit síťový ovladač, který nejlépe vyhovuje vašim potřebám.
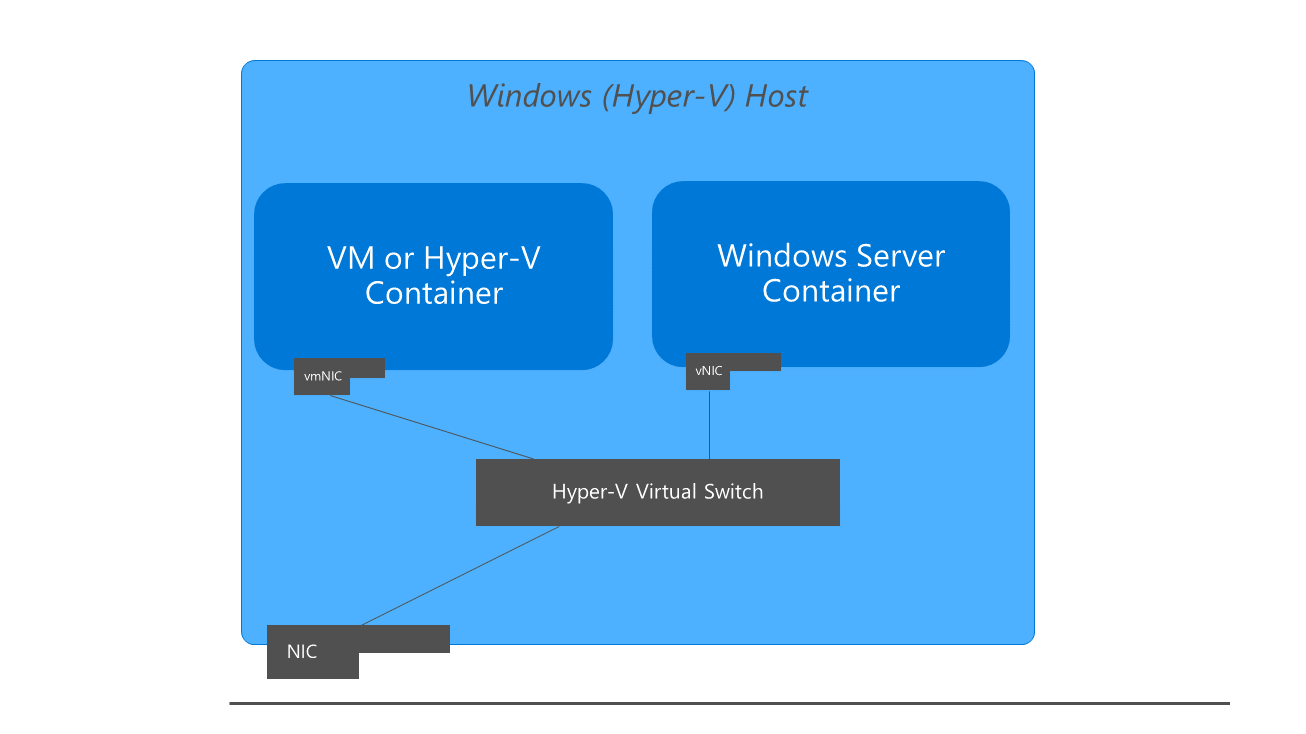
Při prvním spuštění Docker Engine vytvoří výchozí síť NAT, 'nat', která používá interní vSwitch a komponentu Windows s názvem WinNAT. Pokud jsou na hostiteli nějaké externí vSwitchy vytvořené prostřednictvím PowerShell nebo Hyper-V Manager, budou také k dispozici pro Docker s použitím transparentního síťového ovladače a mohou být viděny při spuštění příkazu docker network ls.
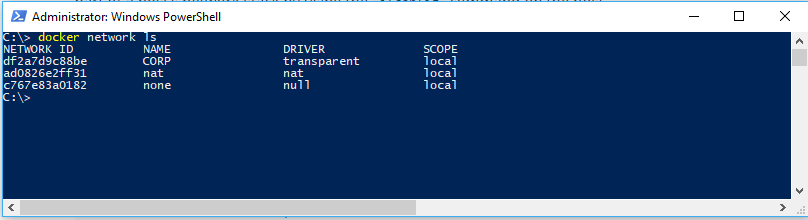
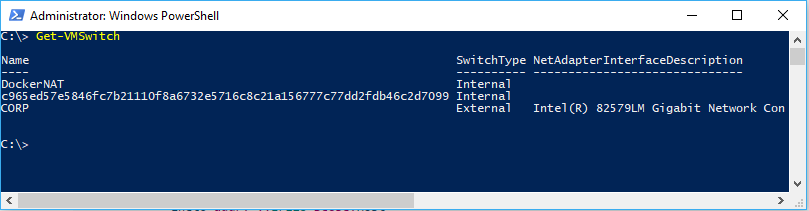
- Interní vSwitch je ten, který není přímo připojen k síťovému adaptéru na hostiteli kontejneru.
- Externí vSwitch je ten, který je přímo připojený k síťovému adaptéru na hostiteli kontejneru.
 .
.
Síť nat je výchozí sítí pro kontejnery běžící ve Windows. Všechny kontejnery, které běží ve Windows bez příznaků nebo argumentů pro implementaci konkrétních konfigurací sítě, se připojí k výchozí síti nat a automaticky přiřadí IP adresu z interního rozsahu IP adres sítě nat. Výchozí interní předpona IP adres používaná pro nat je 172.16.0.0/16.
Správa sítě kontejnerů s využitím hostitelské síťové služby
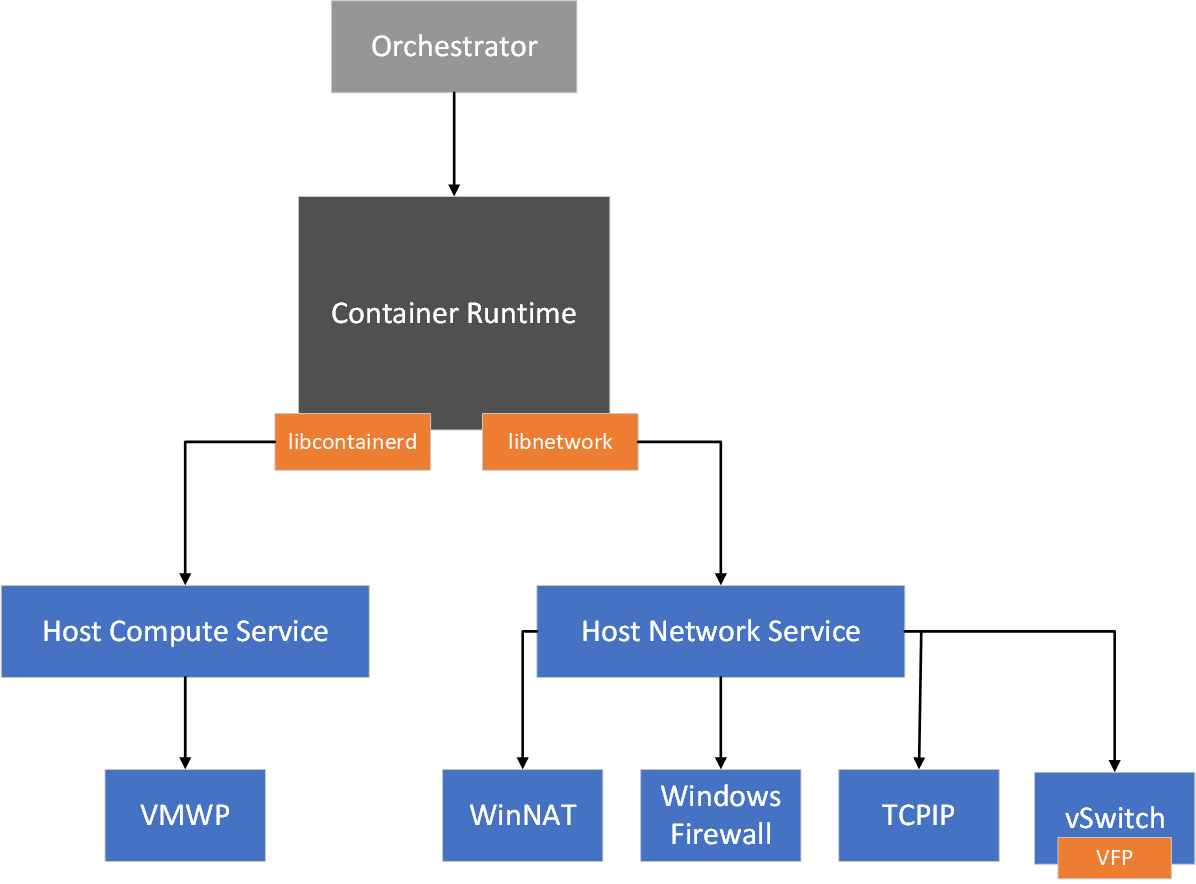
Služba HNS (Host Networking Service) a hostitelská výpočetní služba (HCS) spolupracují na vytváření kontejnerů a připojování koncových bodů k síti. S HNS můžete interagovat prostřednictvím modulu PowerShell Helper.
Vytvoření sítě
- HNS vytvoří virtuální přepínač Hyper-V pro každou síť.
- HNS vytvoří podle potřeby překlad adres (NAT) a fondy IP adres.
Vytvoření koncového bodu
- HNS vytvoří síťový obor názvů pro každý koncový bod kontejneru.
- HNS/HCS umístí v(m)NIC do síťového oboru názvů.
- HNS vytvoří porty (vSwitch)
- HNS přiřadí koncovému bodu IP adresu, informace DNS, trasy atd. (v režimu sítě).
Vytvoření zásad
- Pro výchozí síť pro překlad adres (NAT) HNS vytváří pravidla přesměrování portů WinNAT a mapování spolu se souvisejícími pravidly povolení ve Windows Firewall.
- Pro všechny ostatní sítě využívá HNS virtuální platformu filtrování (VFP) k vytvoření zásad, která zahrnuje vyrovnávání zatížení, seznamy ACL a zapouzdření. Další informace o rozhraních API HNS a schématu najdete v tématu rozhraní API služby Host Compute Network (HCN) pro virtuální počítače a kontejnery.
Nepodporované funkce a možnosti sítě
V současné době se ve Windows nepodporují následující možnosti sítě NEJSOU podporované:
- Kontejnery Windows z Windows Serveru 2022 mají následující podporu pro sítě IPv6:
- Kontejnery připojené k sítím l2bridge podporují zásobník IPv6.
- Kontejnery připojené k transparentním sítím podporují komunikaci pomocí protokolu IPv6 s vlastními IP adresami, ale nemají podporu pro přiřazení IP adres poskytované službou HNS a další síťové služby, jako je vyrovnávání zatížení a seznamy ACL.
- Kontejnery Windows připojené k síti NAT a překryvným sítím nepodporují komunikaci přes zásobník IPv6.
- Šifrovaná komunikace kontejneru přes protokol IPsec.
- sítě v režimu hostitele.
- Sítě ve virtualizované infrastruktuře Azure prostřednictvím transparentního síťového ovladače
| Příkaz | Nepodporovaná možnost |
|---|---|
docker run |
--ip6, --dns-option |
docker network create |
--aux-address, --internal, --ip-range, --ipam-driver, --ipam-opt, --ipv6, --opt encrypted |