Poznámka
Přístup k této stránce vyžaduje autorizaci. Můžete se zkusit přihlásit nebo změnit adresáře.
Přístup k této stránce vyžaduje autorizaci. Můžete zkusit změnit adresáře.
Služba AD FS (Active Directory Federation Services) poskytuje zjednodušené, zabezpečené federování identit a funkce jednotného přihlašování (SSO). Uživatelé federovaní s Microsoft Entra ID nebo Microsoft 365 se můžou ověřit pomocí místních přihlašovacích údajů pro přístup ke všem cloudovým prostředkům. V důsledku toho musí mít vaše nasazení vysoce dostupnou infrastrukturu služby AD FS, aby se zajistil přístup k prostředkům místně i v cloudu.
Nasazení služby AD FS v Azure může pomoct dosáhnout vysoké dostupnosti bez příliš velkého úsilí. Nasazení služby AD FS v Azure má několik výhod:
- Výkon skupin dostupnosti Azure poskytuje vysoce dostupnou infrastrukturu.
- Nasazení se dají snadno škálovat. Pokud potřebujete vyšší výkon, můžete snadno migrovat na výkonnější počítače pomocí zjednodušeného procesu nasazení v Azure.
- Geografická redundance Azure zajišťuje vysokou dostupnost vaší infrastruktury po celém světě.
- Azure Portal usnadňuje správu infrastruktury pomocí vysoce zjednodušených možností správy.
Principy návrhu
Následující diagram znázorňuje doporučenou základní topologii pro nasazení infrastruktury SLUŽBY AD FS v Azure.
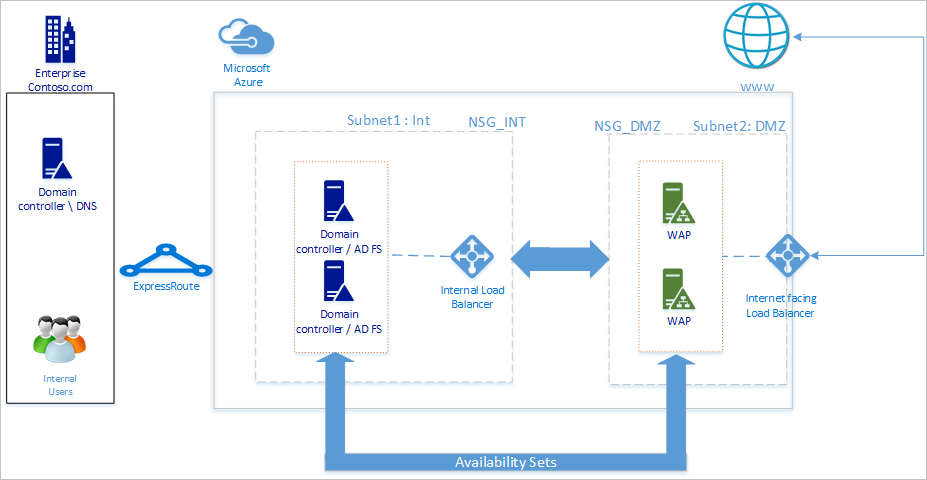
Doporučujeme, aby vaše síťová topologie se řídila těmito obecnými principy:
- Nasaďte službu AD FS na samostatné servery, abyste se vyhnuli ovlivnění výkonu řadičů domény.
- Servery proxy webových aplikací (WAP) musíte nasadit, aby se uživatelé mohli spojit se službou AD FS, když nejsou v podnikové síti.
- Proxy servery webových aplikací byste měli nastavit v demilitarizované zóně (DMZ) a povolit pouze přístup TCP/443 mezi DMZ a interní podsítí.
- Pokud chcete zajistit vysokou dostupnost proxy serverů služby AD FS a webových aplikací, doporučujeme použít interní nástroj pro vyrovnávání zatížení pro servery AD FS a Azure Load Balancer pro proxy servery webových aplikací.
- Pokud chcete zajistit redundanci pro nasazení služby AD FS, doporučujeme seskupit dva nebo více virtuálních počítačů do skupiny dostupnosti pro podobné úlohy. Tato konfigurace zajišťuje, že během plánované nebo neplánované události údržby je k dispozici alespoň jeden virtuální počítač.
- Proxy servery webových aplikací byste měli nasadit v samostatné síti DMZ. Jednu virtuální síť můžete rozdělit do dvou podsítí a potom nasadit proxy servery webových aplikací v izolované podsíti. Můžete nakonfigurovat nastavení skupiny zabezpečení sítě pro každou podsíť a povolit pouze požadovanou komunikaci mezi těmito dvěma podsítěmi.
Nasazení sítě
Při vytváření sítě můžete buď vytvořit dvě podsítě ve stejné virtuální síti, nebo vytvořit dvě různé virtuální sítě. Doporučujeme použít přístup s jednou sítí, protože vytvoření dvou samostatných virtuálních sítí také vyžaduje vytvoření dvou samostatných bran virtuální sítě pro účely komunikace.
Vytvoření virtuální sítě
Vytvoření virtuální sítě:
Přihlaste se k webu Azure Portal pomocí svého účtu Azure.
Na portálu vyhledejte a vyberte Virtuální sítě.
Na stránce Virtuální sítě vyberte + Vytvořit.
V části Vytvořit virtuální síť přejděte na kartu Základy a nakonfigurujte následující nastavení:
V podrobnostech projektu nakonfigurujte následující nastavení:
V části Předplatné vyberte název vašeho předplatného.
V části Skupina prostředků vyberte buď název existující skupiny prostředků, nebo vyberte Vytvořit novou a vytvořte novou.
Pro podrobnosti o instanci nakonfigurujte následující nastavení:
Jako název virtuální sítě zadejte název vaší virtuální sítě.
Vyberte region, ve kterém chcete vytvořit virtuální síť.
Vyberte Další.
Na kartě Zabezpečení povolte libovolnou službu zabezpečení, kterou chcete použít, a pak vyberte Další.
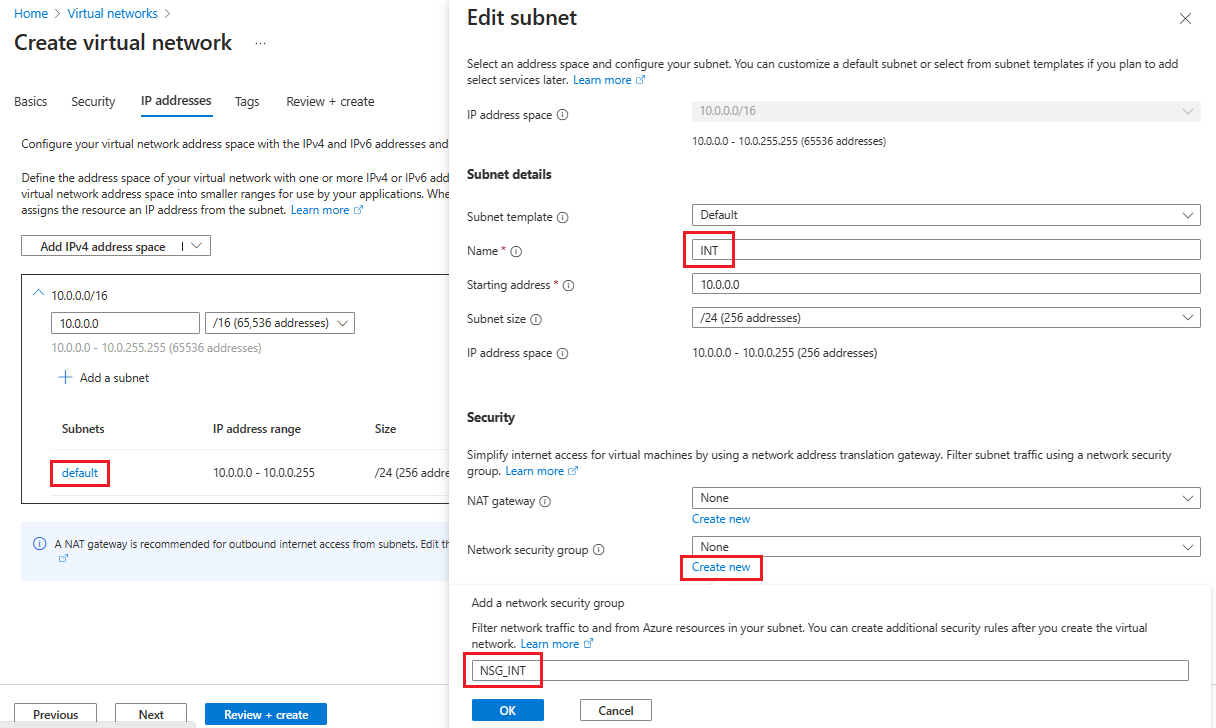
Na kartě IP adresy vyberte název podsítě, kterou chcete upravit. V tomto příkladu upravujeme výchozí podsíť, kterou služba automaticky vytvoří.
Na stránce Upravit podsíť přejmenujte podsíť na INT.
Zadejte IP adresu a informace o velikosti podsítě pro vaši podsíť a definujte adresní prostor IP adres.
V části Skupina zabezpečení sítě vyberte Vytvořit novou.
V tomto příkladu zadejte název NSG_INT a vyberte OK a pak vyberte Uložit. Teď máte svou první podsíť.
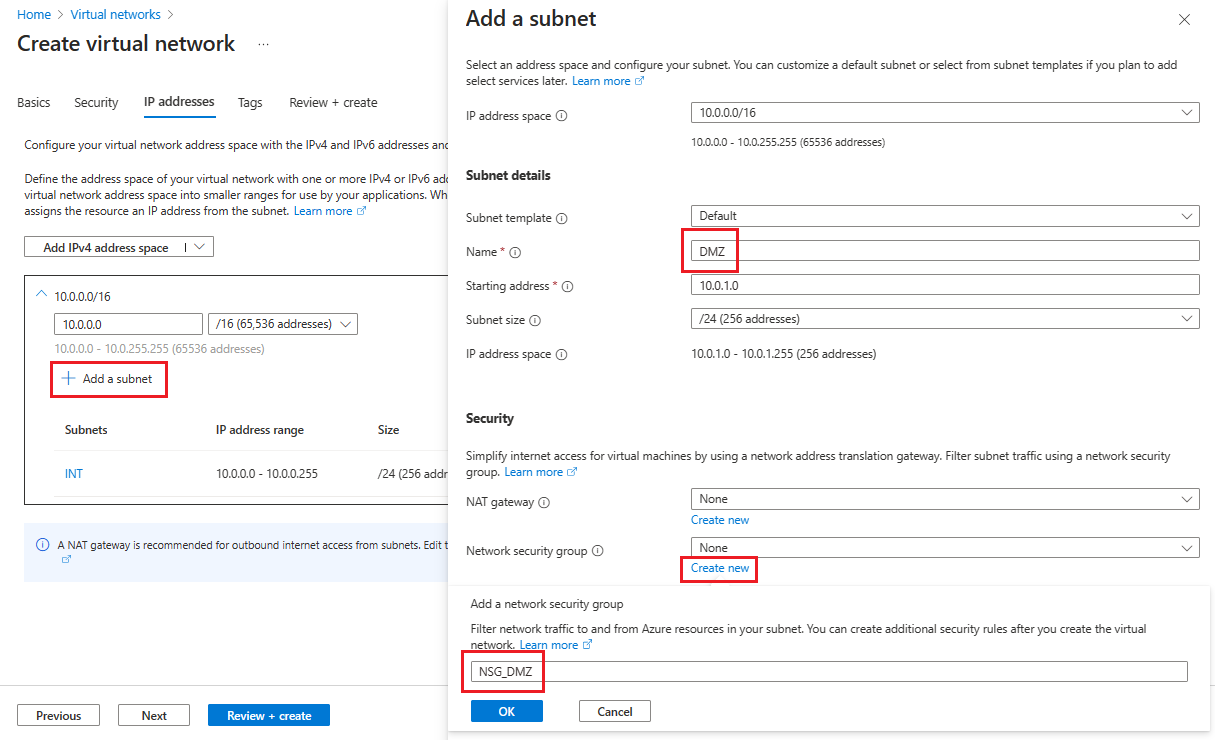
Pokud chcete vytvořit druhou podsíť, vyberte + Přidat podsíť.
Na stránce Přidat podsíť zadejte dmZ pro druhý název podsítě a do prázdných polí zadejte informace o vaší podsíti a definujte adresní prostor IP adres.
V části Skupina zabezpečení sítě vyberte Vytvořit novou.
Zadejte název NSG_DMZ, vyberte OK a pak vyberte Přidat.
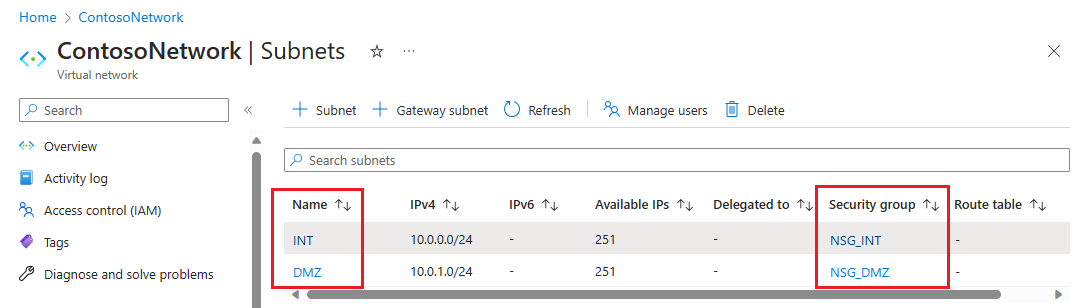
Vyberte možnost Zkontrolovat a vytvořit, poté vyberte Vytvořit.
Teď máte virtuální síť, která obsahuje dvě podsítě, z nichž každá má přidruženou skupinu zabezpečení sítě.
Zabezpečení virtuální sítě
Skupina zabezpečení sítě (NSG) obsahuje seznam pravidel seznamu řízení přístupu (ACL), která povolují nebo zakazují síťový provoz k instancím virtuálních počítačů v rámci virtuální sítě. Skupiny zabezpečení sítě můžete přidružit buď k podsítím, nebo k jednotlivým instancím virtuálních počítačů v těchto podsítích. Pokud je NSG přidružená k podsíti, pravidla ACL platí pro všechny instance virtuálních počítačů v této podsíti.
Skupiny zabezpečení sítě přidružené k vašim podsítím automaticky obsahují některá výchozí příchozí a odchozí pravidla. Výchozí pravidla zabezpečení nemůžete odstranit, ale můžete je přepsat pravidly, která mají vyšší prioritu. A podle požadované úrovně zabezpečení můžete přidat další příchozí a odchozí pravidla.
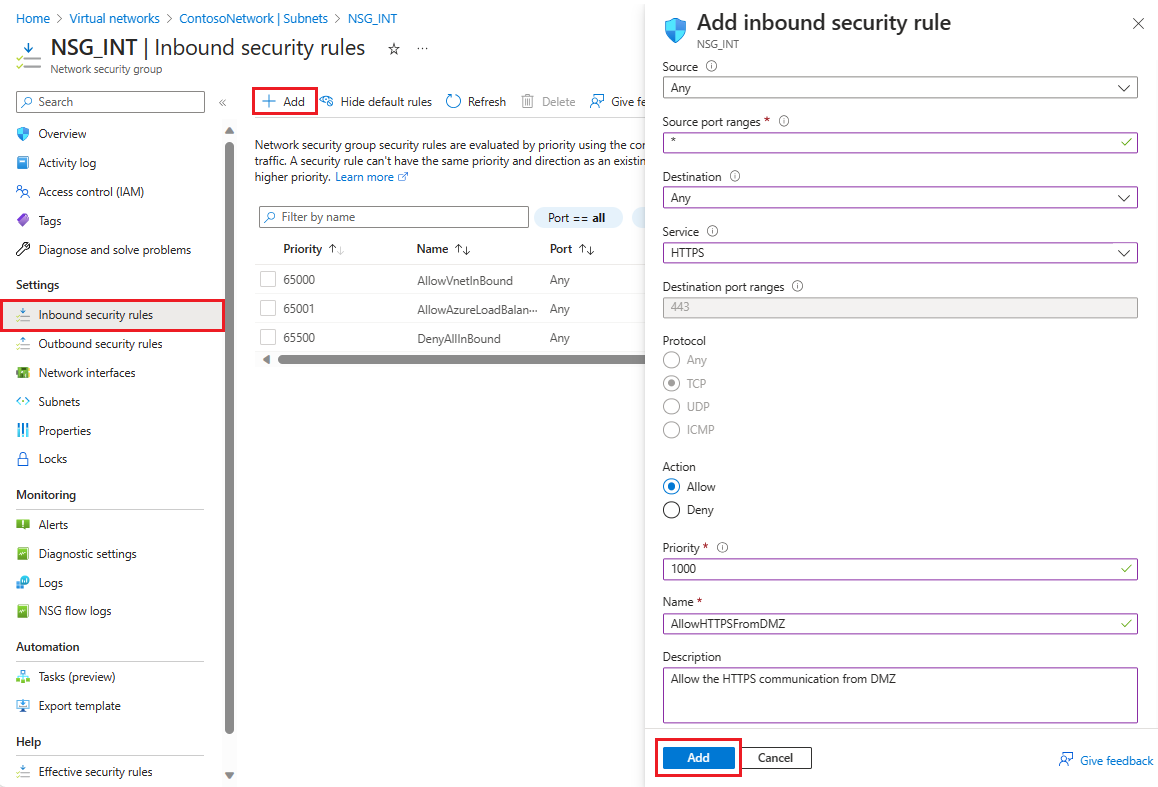
Teď do každé z našich dvou skupin zabezpečení přidejte několik pravidel. V prvním příkladu přidáme příchozí pravidlo zabezpečení do skupiny zabezpečení NSG_INT .
Na stránce Podsítě virtuální sítě vyberte NSG_INT.
Vlevo vyberte Příchozí pravidla zabezpečení a pak vyberte + Přidat.
V Přidat příchozí pravidlo zabezpečení nakonfigurujte pravidlo s následujícími informacemi:
Jako zdroj zadejte 10.0.1.0/24.
U rozsahů zdrojových portů ponechte buď prázdné, pokud nechcete povolit provoz, nebo vyberte hvězdičku (*) a povolte provoz na jakémkoli portu.
Jako cíl zadejte 10.0.0.0/24.
V případě služby vyberte HTTPS. Služba automaticky vyplní informační pole pro rozsahy cílových portů a protokol v závislosti na tom, kterou službu zvolíte.
V části Akce vyberte Povolit.
Jako prioritu zadejte 1010.
Jako název zadejte AllowHTTPSFromDMZ.
Jako popis zadejte Povolit komunikaci HTTPS z DMZ.
Po dokončení vyberte Přidat.
 Nové příchozí pravidlo zabezpečení se teď přidá na začátek seznamu pravidel pro NSG_INT.
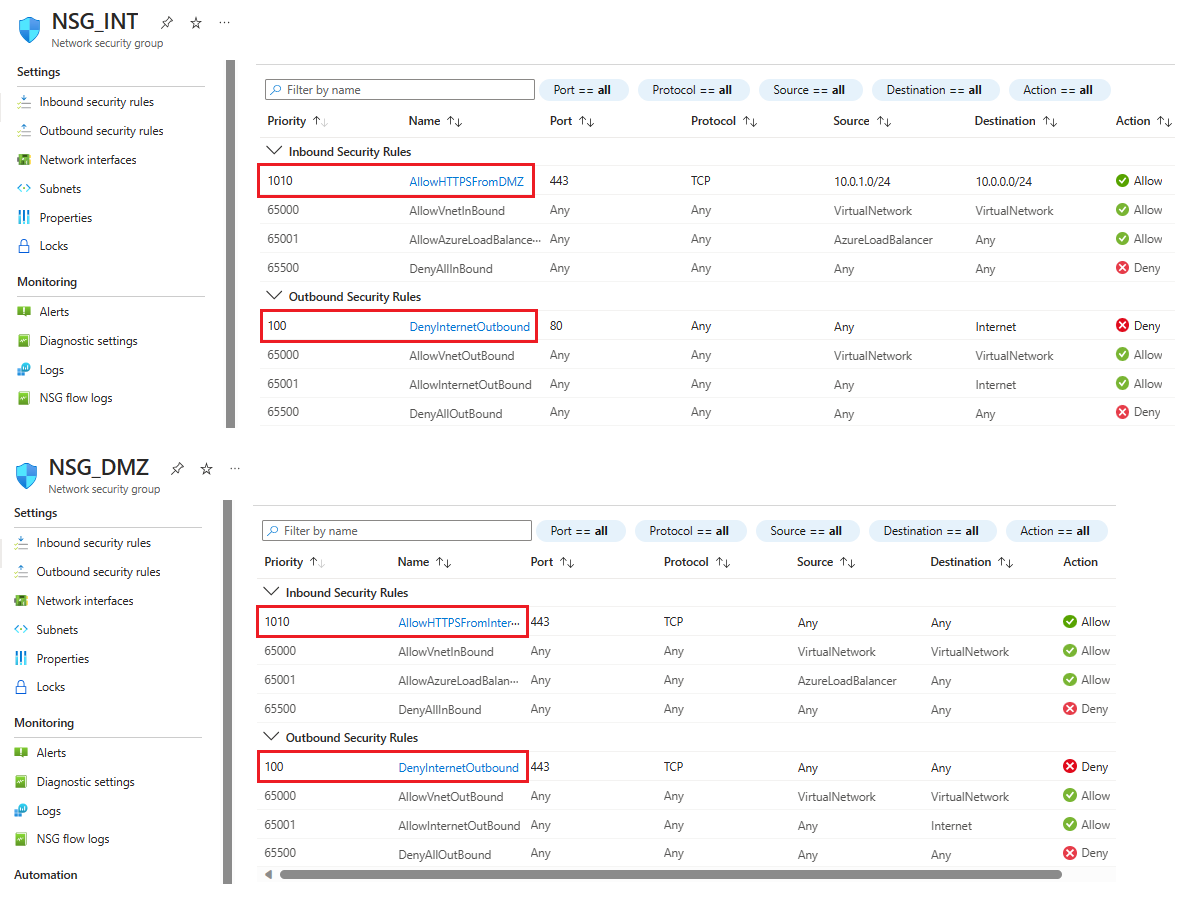
Nové příchozí pravidlo zabezpečení se teď přidá na začátek seznamu pravidel pro NSG_INT.Opakujte tyto kroky s hodnotami zobrazenými v následující tabulce. Kromě nového pravidla, které jste vytvořili, musíte do uvedeného pořadí priority přidat následující další pravidla, která pomáhají zabezpečit interní podsíť a podsíť DMZ.
NSG Typ pravidla Zdroj Cíl Služba Činnost Priorita Název Popis NSG_INT Odchozí Jakýkoliv Značka služby / Internet Vlastní (80/Libovolný) Zamítnout 100 DenyInternetOutbound Přístup k internetu není k dispozici. NSG_DMZ Příchozí Jakýkoliv Jakýkoliv Vlastní (hvězdička (*)/libovolné) Povolit 1010 PovolitHTTPSZInternetu Povolit přístup HTTPS z internetu do DMZ. NSG_DMZ Odchozí Jakýkoliv Značka služby / Internet Vlastní (80/Libovolný) Zamítnout 100 DenyInternetOutbound Všechno kromě protokolu HTTPS na internet je zablokované. Po zadání hodnot pro každé nové pravidlo vyberte Přidat a pokračujte k dalšímu, dokud se pro každou skupinu zabezpečení sítě nepřidají dvě nová pravidla zabezpečení.
Po konfiguraci by stránky NSG měly vypadat jako na následujícím snímku obrazovky:
Poznámka:
Pokud virtuální síť vyžaduje ověřování klientských uživatelských certifikátů, jako je ověřování clientTLS pomocí uživatelských certifikátů X.509, musíte pro příchozí přístup povolit port TCP 49443.
Vytvoření připojení k místnímu prostředí
Pro nasazení řadiče domény v Azure potřebujete připojení k lokálnímu prostředí. Místní infrastrukturu můžete připojit k infrastruktuře Azure pomocí jedné z následujících možností:
- Připojení z bodu do místa
- Virtuální sítě site-to-site
- ExpressRoute
Pokud vaše organizace nevyžaduje připojení typu point-to-site nebo připojení typu site-to-site, doporučujeme použít ExpressRoute. ExpressRoute umožňuje vytvářet privátní připojení mezi datovými centry Azure a infrastrukturou, která je v místním prostředí nebo v prostředí kolokace. Připojení ExpressRoute se také nepřipojují k veřejnému internetu, takže jsou spolehlivější, rychlejší a bezpečnější. Další informace o ExpressRoute a různých možnostech připojení pomocí ExpressRoute najdete v technickém přehledu ExpressRoute.
Vytvoření skupin dostupnosti
Pro každou roli (DC/AD FS a WAP) vytvořte skupiny dostupnosti, které obsahují aspoň dva počítače. Tato konfigurace pomáhá dosáhnout vyšší dostupnosti pro každou roli. Při vytváření skupin dostupnosti musíte rozhodnout, které z následujících domén chcete použít:
V doméně selhání sdílejí virtuální počítače stejný zdroj napájení a fyzický síťový přepínač. Doporučujeme minimálně dvě domény selhání. Výchozí hodnota je 2 a můžete ji nechat as-is pro toto nasazení.
V aktualizační doméně se počítače během aktualizace restartují společně. Doporučujeme minimálně dvě aktualizační domény. Výchozí hodnota je 5 a můžete ji nechat as-is pro toto nasazení.
Vytvoření skupin dostupnosti:
Na webu Azure Portal vyhledejte a vyberte Skupiny dostupnosti a pak vyberte + Vytvořit.
V části Vytvořit sadu dostupnosti přejděte na kartu Základy a zadejte následující informace:
V části Project details (Podrobnosti projektu):
V části Předplatné vyberte název vašeho předplatného.
Pro skupinu prostředků vyberte existující skupinu prostředků nebo vytvořte novou .
V části Podrobnosti o instanci:
Jako Název zadejte název skupiny dostupnosti. V tomto příkladu zadejte contosodcset.
Pro oblast vyberte oblast, kterou chcete použít.
U domén selhání ponechte výchozí hodnotu 2.
U aktualizačních domén ponechte výchozí hodnotu 5.
Pro použití spravovaných disků v tomto příkladu vyberte Ne (Classic ).
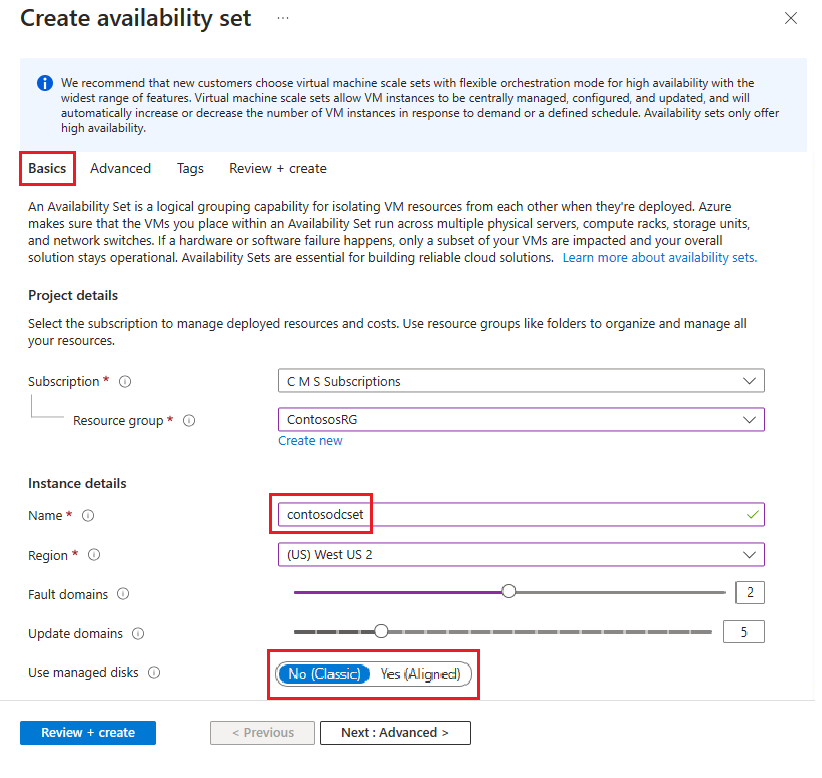
Až budete hotovi, vyberte Zkontrolovat a vytvořit a pak Vytvořit.
Opakujte předchozí kroky a vytvořte druhou sadu dostupnosti s názvem contososac2.
Nasazení virtuálních počítačů
Dalším krokem je nasazení virtuálních počítačů, které hostují různé role ve vaší infrastruktuře. V každé skupině dostupnosti doporučujeme minimálně dva počítače. V tomto příkladu vytvoříme čtyři virtuální počítače pro základní nasazení.
Vytvoření virtuálních počítačů:
Vyhledejte a vyberte virtuální počítače na webu Azure Portal.
Na stránce Virtuální počítače vyberte + Vytvořit a pak zvolte virtuální počítač Azure.
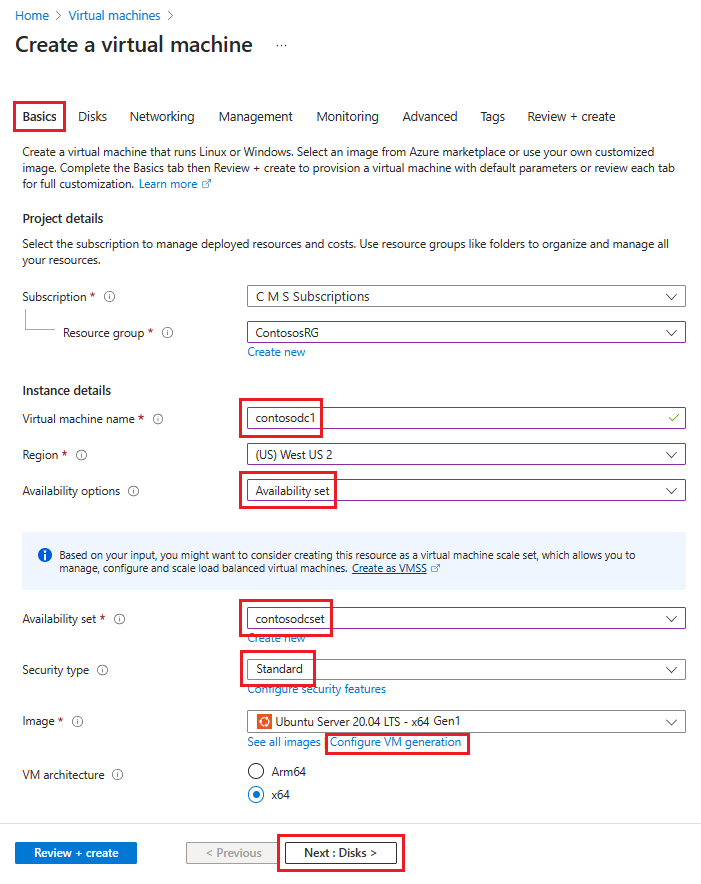
V části Vytvořit virtuální počítač přejděte na kartu Základy a zadejte následující informace:
V části Project details (Podrobnosti projektu):
V části Předplatné vyberte název vašeho předplatného.
Pro skupinu prostředků vyberte existující skupinu prostředků nebo vytvořte novou .
V části Podrobnosti o instanci:
Jako název virtuálního počítače zadejte název virtuálního počítače. Pro první počítač v tomto příkladu zadejte contosodc1.
V sekci Oblast vyberte oblast, kterou chcete použít.
U možností dostupnosti vyberte Skupina dostupnosti.
Pro sadu dostupnosti Availability set vyberte contosodcset.
Jako typ zabezpečení vyberte Standard.
V části Předplatné vyberte název vašeho předplatného.
V části Image vyberte image, kterou chcete použít, a pak vyberte Konfigurovat generování virtuálních počítačů a vyberte Gen 1.
V části Účet správce:
Jako typ ověřování vyberte veřejný klíč SSH.
Do pole Uživatelské jméno zadejte uživatelské jméno, které se má pro účet použít.
Jako název páru klíčů zadejte název páru klíčů, který se má pro účet použít.
U všeho, co není zadané, můžete ponechat výchozí hodnoty.
Až budete hotovi, vyberte Další: Disky.
Na kartě Sítě zadejte následující informace:
Pro virtuální síť vyberte název virtuální sítě, která obsahuje podsítě, které jste vytvořili v předchozí části.
Pro možnost Podsíť vyberte svou INT podsíť.
Pro skupinu zabezpečení sítě NIC vyberte Žádné.
U všeho, co není zadané, můžete ponechat výchozí hodnoty.
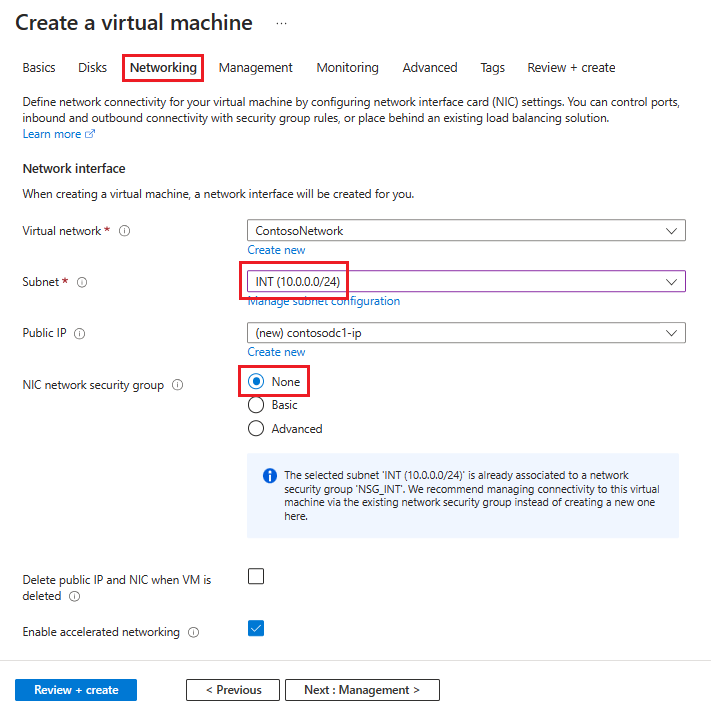
Po provedení všech možností vyberte Zkontrolovat a vytvořit a pak vyberte Vytvořit.
Tento postup opakujte pomocí informací v této tabulce a vytvořte tři zbývající virtuální počítače:
| Název virtuálního počítače | Podsíť | Možnosti dostupnosti | Skupina dostupnosti | Účet úložiště |
|---|---|---|---|---|
| contosodc2 | INT | Skupina dostupnosti | contosodcset | contososac2 |
| contosowap1 | demilitarizovaná zóna | Skupina dostupnosti | contosowapset | contososac1 |
| contosowap2 | DMZ (demilitarizovaná zóna) | Skupina dostupnosti | contosowapset | contososac2 |
Nastavení nezadávají skupinu zabezpečení sítě, protože Azure umožňuje používat skupinu zabezpečení sítě na úrovni podsítě. Síťový provoz počítače můžete řídit pomocí jednotlivé skupiny zabezpečení sítě přidružené k podsíti nebo objektu síťové karty . Další informace najdete v tématu Co je skupina zabezpečení sítě (NSG).
Pokud spravujete DNS, doporučujeme použít statickou IP adresu. Můžete použít Azure DNS a v záznamech DNS pro vaši doménu odkazovat na nové počítače pomocí jejich plně kvalifikovaných názvů domén Azure. Další informace najdete v tématu Změna privátní IP adresy na statickou.
Po dokončení nasazení by se na stránce Virtuální počítače měly zobrazit všechny čtyři virtuální počítače.
Konfigurace serverů DC a AD FS
Aby bylo možné ověřit jakýkoli příchozí požadavek, musí služba AD FS kontaktovat řadič domény. Pokud chcete ušetřit nákladnou cestu z Azure do místního řadiče domény pro ověřování, doporučujeme nasadit repliku tohoto řadiče domény v Azure. Aby bylo možné dosáhnout vysoké dostupnosti, doporučuje se vytvořit sadu dostupnosti alespoň dvou řadičů domény.
| Řadič domény | Role | Účet úložiště |
|---|---|---|
| contosodc1 | Replika | contososac1 |
| contosodc2 | Replika | contososac2 |
Doporučujeme provést následující akce:
Povýšit dva servery na repliky řadičů domény s podporou DNS
Servery SLUŽBY AD FS nakonfigurujte tak, že pomocí správce serveru nainstalujete roli SLUŽBY AD FS.
Vytvoření a nasazení interního nástroje pro vyrovnávání zatížení (ILB)
Vytvoření a nasazení interního vyrovnávače zatížení:
Na webu Azure Portal vyhledejte a vyberte Nástroje pro vyrovnávání zatížení a zvolte + Vytvořit.
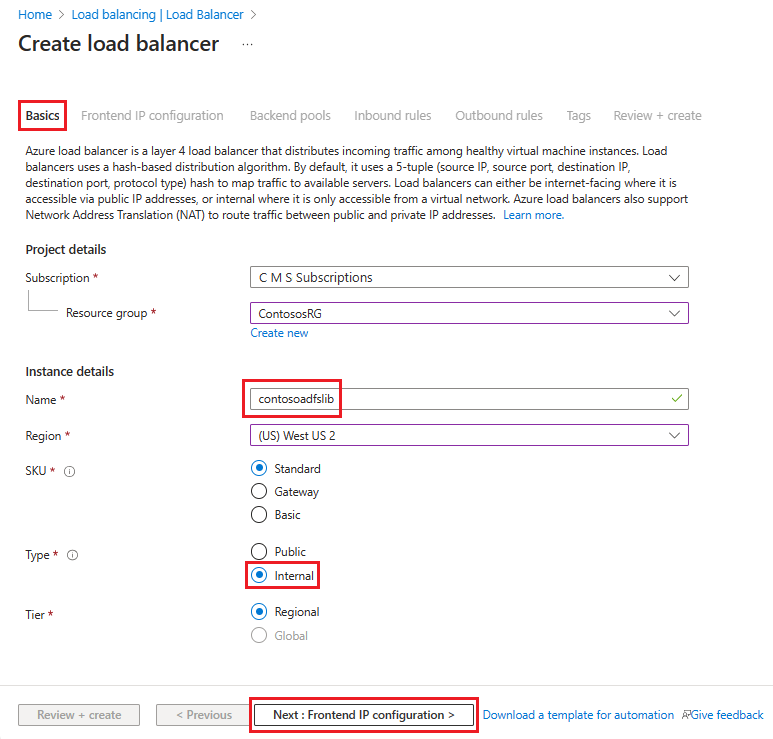
V části Vytvořit nástroj pro vyrovnávání zatížení zadejte nebo vyberte tyto informace na kartě Základy :
V části Project details (Podrobnosti projektu):
V části Předplatné vyberte název vašeho předplatného.
Pro skupinu prostředků vyberte existující skupinu prostředků nebo vytvořte novou .
V části Podrobnosti o instanci:
Jako Název zadejte název vašeho nástroje pro vyrovnávání zatížení.
Pro Region vyberte region, který chcete použít.
Jako typ vyberte Interní.
Ponechte SKU a Tier jako výchozí hodnoty a pak vyberte Další: Konfigurace IP adresy front-endu
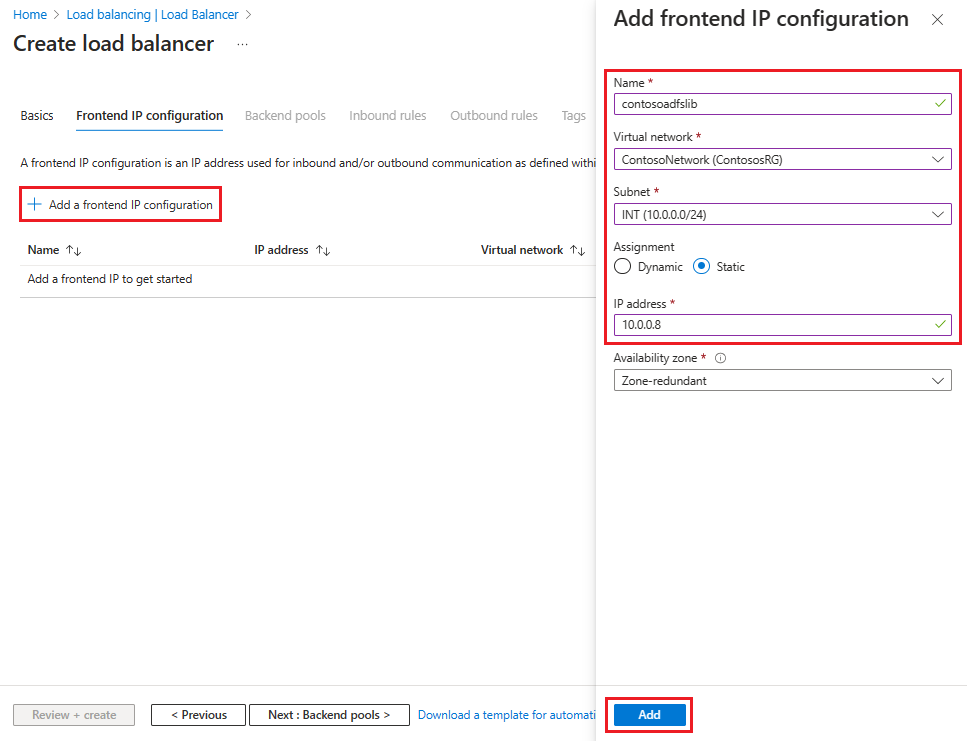
Vyberte + Přidat konfiguraci front-endové IP adresy a pak zadejte nebo vyberte tyto informace na stránce Přidat konfiguraci IP adresy front-endu .
Jako název zadejte název konfigurace front-endové IP adresy.
V případě virtuální sítě vyberte virtuální síť, do které chcete službu AD FS nasadit.
Jako podsíť vyberte INT, což byla interní podsíť, kterou jste vytvořili v předchozí části.
Jako přiřazení vyberte Statická.
Jako IP adresu zadejte svoji IP adresu.
Ponechte zónu dostupnosti jako výchozí a pak vyberte Přidat.
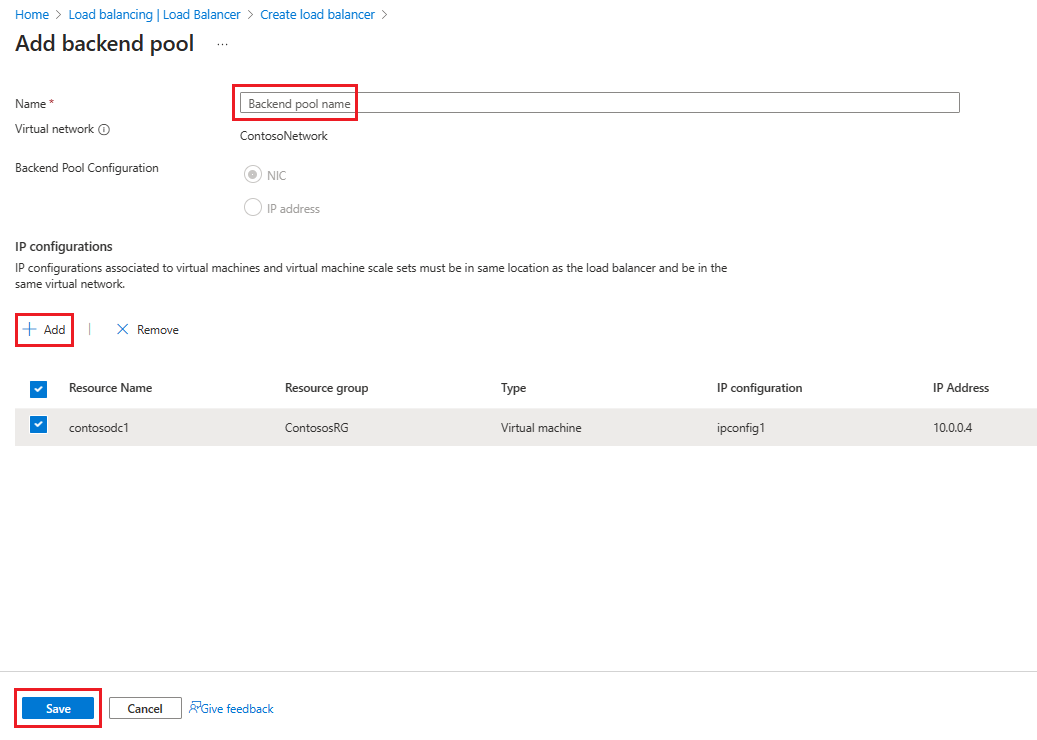
Vyberte Další: Backendové fondy, a pak vyberte + Přidat backendový fond.
Na stránce Přidat back-endový fond zadejte název back-endového fondu do pole Název . V oblasti konfigurace IP vyberte + Přidat.
Na stránce Přidat backendový fond vyberte virtuální počítač, který se přiřadí k backendovému fondu, vyberte Přidat a pak vyberte Uložit.
Vyberte Další: Příchozí pravidla.
Na kartě Příchozí pravidla vyberte Přidat pravidlo vyrovnávání zatížení a na stránce Přidat pravidlo vyrovnávání zatížení zadejte následující informace:
Do pole Název zadejte název pravidla.
Jako IP adresu front-endu vyberte adresu, kterou jste vytvořili dříve.
U backendového fondu vyberte backendový fond, který jste vytvořili dříve.
V části Protokol vyberte TCP.
For Port, enter 443.
U back-endového portu vyberte Vytvořit nový a zadejte následující hodnoty, které vytvoří sondu stavu:
Jako název zadejte název zdravotní sondy.
Jako protokol zadejte HTTP.
Jako port zadejte 80.
Jako cestu zadejte /adfs/probe.
Pro interval ponechte výchozí hodnotu 5.
Jakmile budete hotovi, zvolte tlačítko Uložit.
Až budete hotovi, vyberte Uložit a uložte příchozí pravidlo.
Výběrem možnosti Uložit uložte příchozí pravidlo.
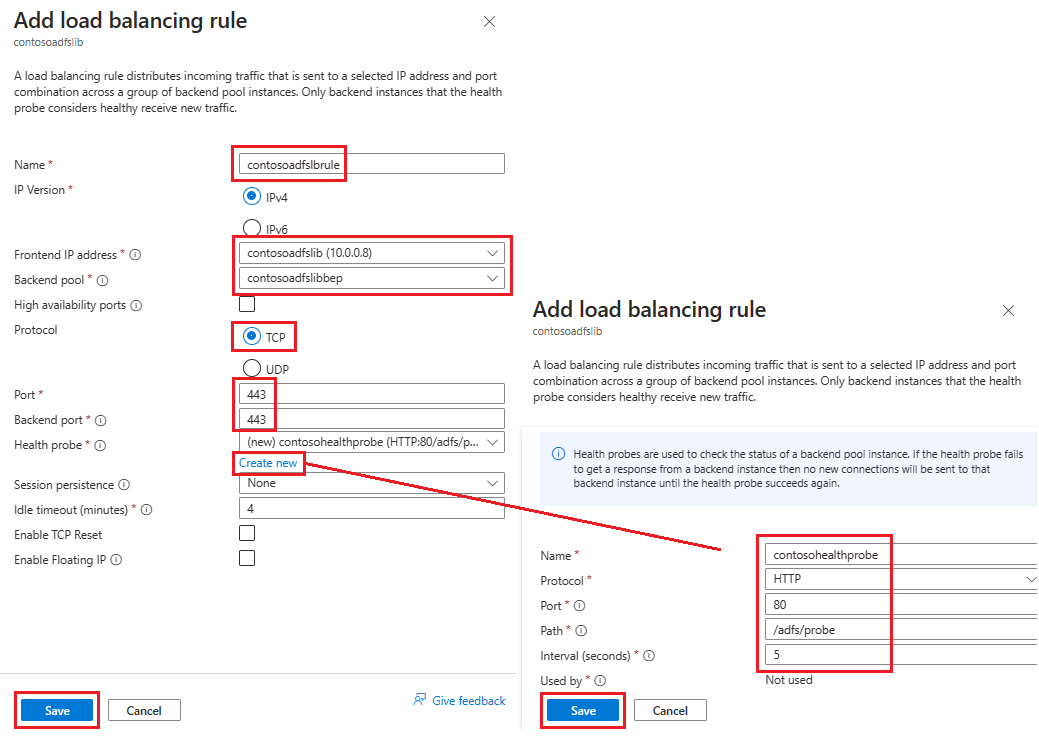
Vyberte možnost Zkontrolovat a vytvořit, poté vyberte Vytvořit.
Po výběru Vytvořit a nasazení interního vyrovnávače zatížení se zobrazí v seznamu vyrovnávačů zatížení, jak je ukázáno na následujícím snímku obrazovky.
Aktualizace serveru DNS pomocí interního vyrovnávače zatížení (ILB)
Pomocí interního serveru DNS vytvořte záznam A pro ILB. Toto nastavení zajišťuje, aby všechna data přenášená do fs.contoso.com skončila na ILB pomocí příslušné trasy. Záznam A by měl být pro federační službu s IP adresou, která směřuje na IP adresu interního vyrovnávače zátěže. Například pokud je IP adresa interního nástroje pro vyrovnávání zatížení (ILB) 10.3.0.8 a nainstalovaná federační služba je fs.contoso.com, vytvořte záznam A pro fs.contoso.com ukazující na 10.3.0.8.
Výstraha
Pokud pro databázi SLUŽBY AD FS používáte interní databázi Windows (WID), nastavte tuto hodnotu tak, aby dočasně odkazovala na primární server SLUŽBY AD FS. Pokud neprovedete tuto dočasnou změnu nastavení, proxy webových aplikací selže s registrací. Po úspěšné registraci všech proxy serverů webových aplikací změňte záznam DNS, aby směřoval na nástroj pro vyrovnávání zatížení.
Poznámka:
Pokud vaše nasazení používá také protokol IPv6, vytvořte odpovídající záznam AAAA.
Konfigurace proxy serverů webových aplikací pro přístup k serverům SLUŽBY AD FS
Aby se proxy servery webových aplikací mohly spojit se servery služby AD FS za interním nástrojem pro vyrovnávání zatížení, vytvořte pro interní nástroj pro vyrovnávání zatížení záznam v souboru %systemroot%\system32\drivers\etc\hosts. Rozlišující název (DN) by měl být název federační služby, například fs.contoso.com. Položka IP by měla být IP adresa interního load balanceru (ILB), což je v tomto příkladu 10.3.0.8.
Výstraha
Pokud pro databázi SLUŽBY AD FS používáte interní databázi Windows (WID), nastavte tuto hodnotu tak, aby dočasně odkazovala na primární server SLUŽBY AD FS. Pokud ne, registrace proxy webových aplikací se nezdaří. Po úspěšné registraci všech proxy serverů webových aplikací změňte tuto položku DNS tak, aby směřovala k vyrovnávači zatížení.
Nainstalujte roli proxy webových aplikací
Jakmile zajistíte, že proxy servery webových aplikací budou mít přístup k serverům služby AD FS za interním vyrovnáním zatížení, můžete nainstalovat proxy servery webových aplikací. Proxy servery webových aplikací nemusí být připojené k doméně. Nainstalujte role proxy webových aplikací na dva proxy servery webových aplikací tak, že vyberete roli Vzdálený přístup . Správce serveru vás provede dokončením instalace WAP.
Další informace o nasazení WAP najdete v tématu Instalace a konfigurace proxy serveru webových aplikací.
Vytvoření a nasazení internetového (veřejného) nástroje pro vyrovnávání zatížení
Vytvoření a nasazení internetového nástroje pro vyrovnávání zatížení:
Na webu Azure Portal vyberte Nástroje pro vyrovnávání zatížení a pak zvolte Vytvořit.
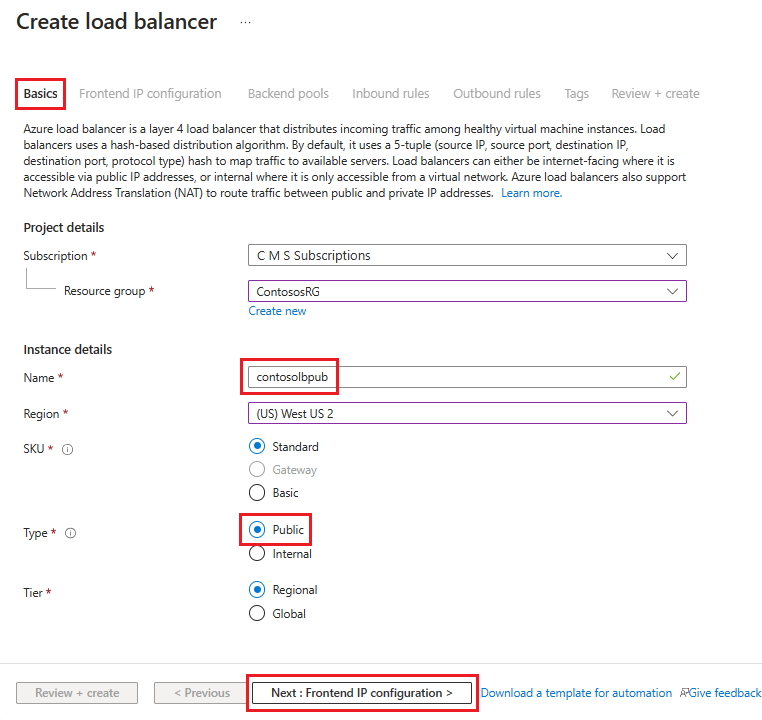
V části Vytvořit nástroj pro vyrovnávání zatížení přejděte na kartu Základy a nakonfigurujte následující nastavení:
V části Project details (Podrobnosti projektu):
V části Předplatné vyberte název vašeho předplatného.
Pro skupinu prostředků vyberte existující skupinu prostředků nebo vytvořte novou .
V části Podrobnosti o instanci:
Jako Název zadejte název vašeho nástroje pro vyrovnávání zatížení.
Vyberte region, který chcete použít.
Jako Typ vyberte Veřejný.
Ponechte SKU a Tier jako výchozí hodnoty a pak vyberte Další: Konfigurace IP frontendu
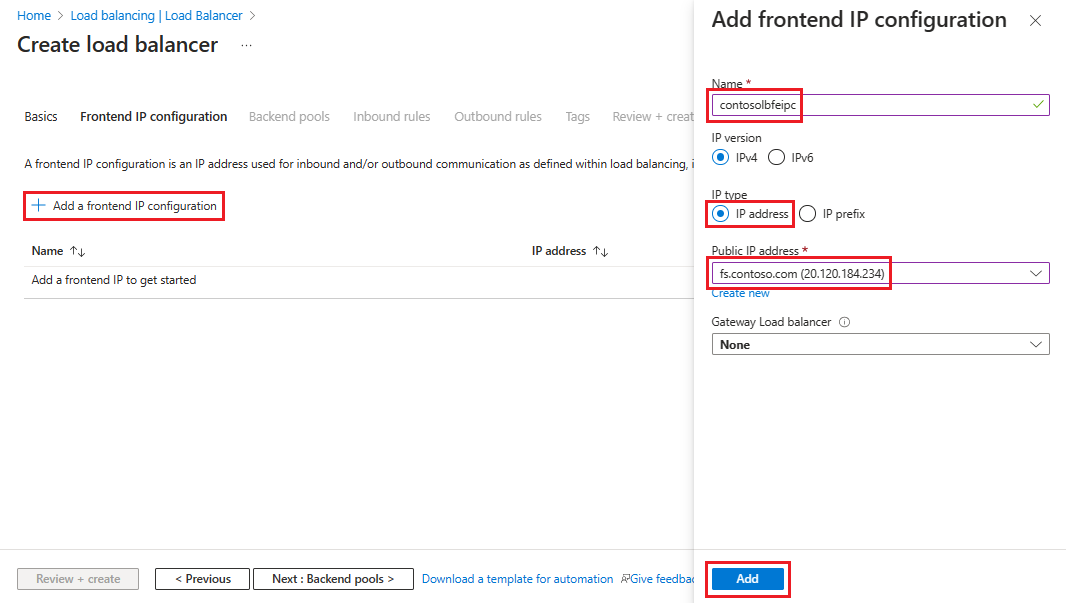
Vyberte + Přidat konfiguraci front-endové IP adresy a pak zadejte nebo vyberte tyto informace na stránce Přidat konfiguraci IP adresy front-endu .
Jako název zadejte název konfigurace front-endové IP adresy.
Jako typ IP vyberte IP adresu.
V části Veřejná IP adresa vyberte veřejnou IP adresu, kterou chcete použít, z rozevíracího seznamu nebo vyberte Vytvořit a vytvořte novou a pak vyberte Přidat.
Vyberte Další: Backend pooly a pak vyberte + Přidat backend pool.
Na stránce Přidat backendovou skupinu zadejte název pro backendovou skupinu do pole Název. V oblasti konfigurace IP vyberte + Přidat.
Na stránce Přidat back-endový fond vyberte virtuální počítač, který se zarovná s back-endovým fondem, vyberte Přidat a pak vyberte Uložit.

Vyberte Další: Příchozí pravidla a pak vyberte Přidat pravidlo vyrovnávání zatížení. Na stránce Přidat pravidlo vyrovnávání zatížení nakonfigurujte následující nastavení:
Do pole Název zadejte název pravidla.
Jako IP adresu front-endu vyberte adresu, kterou jste vytvořili dříve.
U back-endového fondu vyberte back-endový fond, který jste vytvořili dříve.
V části Protokol vyberte TCP.
For Port, enter 443.
Jako back-endový port zadejte 443.
Do sondy stavu zadejte následující hodnoty:
Do pole Název zadejte název sondy zdravotního stavu.
Jako protokol zadejte HTTP.
Jako port zadejte 80.
Jako cestu zadejte /adfs/probe.
Pro interval ponechte výchozí hodnotu 5.
Jakmile budete hotovi, zvolte tlačítko Uložit.
Až budete hotovi, vyberte Uložit a uložte příchozí pravidlo.
Vyberte možnost Zkontrolovat a vytvořit, poté vyberte Vytvořit.
Po výběru Vytvořit a nasazení veřejného ILB by seznam měl obsahovat seznam vyrovnávačů zatížení.
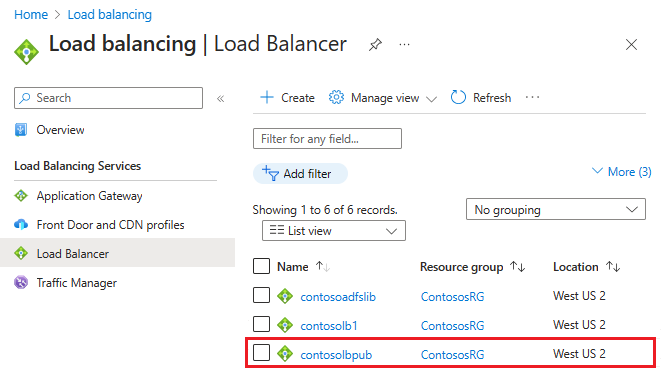
Přiřaďte DNS štítek veřejné IP adrese
Konfigurace popisku DNS pro veřejnou IP adresu:
Na webu Azure Portal vyhledejte veřejné IP adresy a pak vyberte IP adresu, kterou chcete upravit.
V části Nastavení vyberte Konfigurace.
V části Zadejte popisek DNS (volitelné) přidejte položku do textového pole (například fs.contoso.com), která se přeloží na popisek DNS externího nástroje pro vyrovnávání zatížení (například contosofs.westus.cloudapp.azure.com).
Výběrem možnosti Uložit dokončete přiřazení popisku DNS.
Otestování přihlášení ke službě AD FS
Nejjednodušší způsob, jak službu AD FS otestovat, je použití stránky IdpInitiatedSignOn.aspx. Chcete-li to provést, musíte povolit IdpInitiatedSignOn ve vlastnostech služby AD FS.
Pokud chcete zkontrolovat, jestli máte povolenou vlastnost IdpInitiatedSignOn:
V PowerShellu spusťte na serveru AD FS následující rutinu a nastavte ji na povolenou.
Set-AdfsProperties -EnableIdPInitiatedSignOnPage $trueZ libovolného externího počítače přistupte k
https:\//adfs-server.contoso.com/adfs/ls/IdpInitiatedSignon.aspx.Měla by se zobrazit následující stránka služby AD FS:
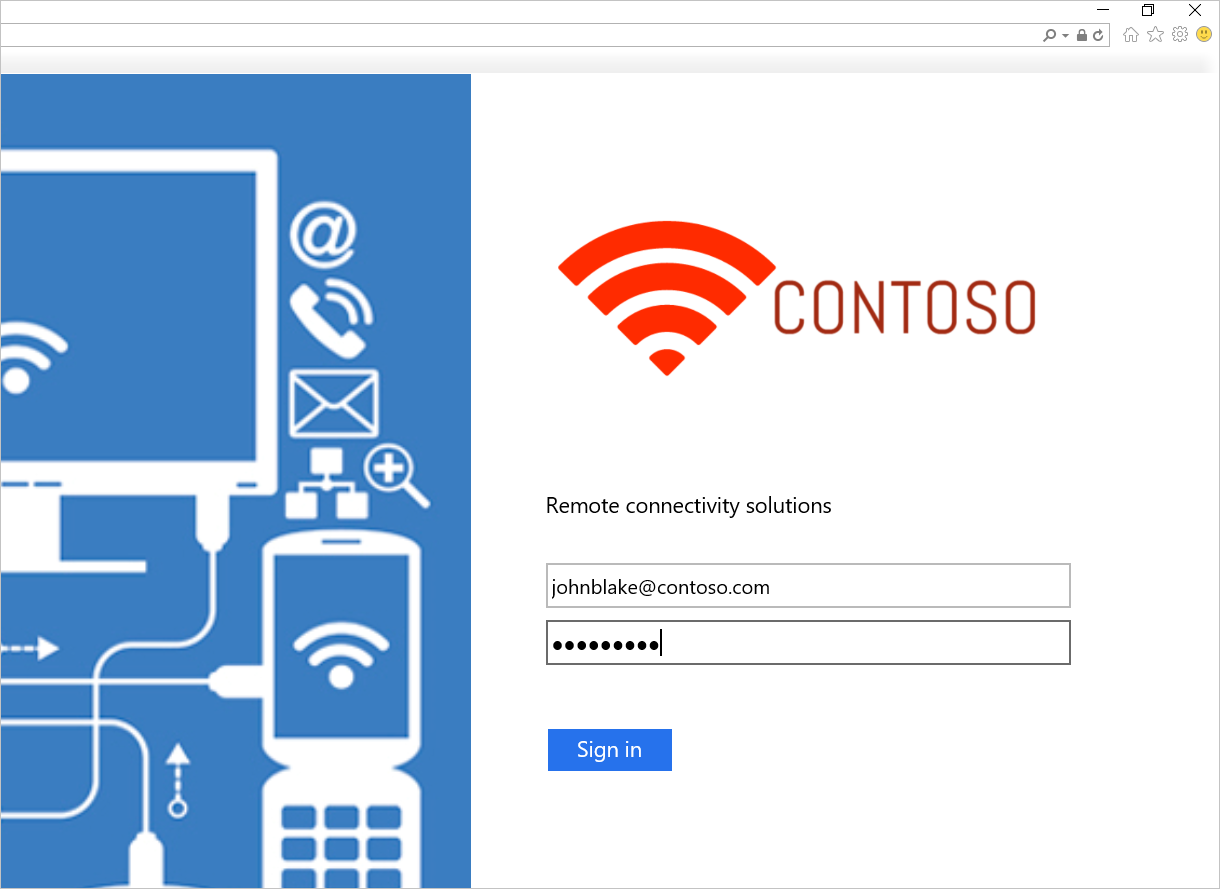
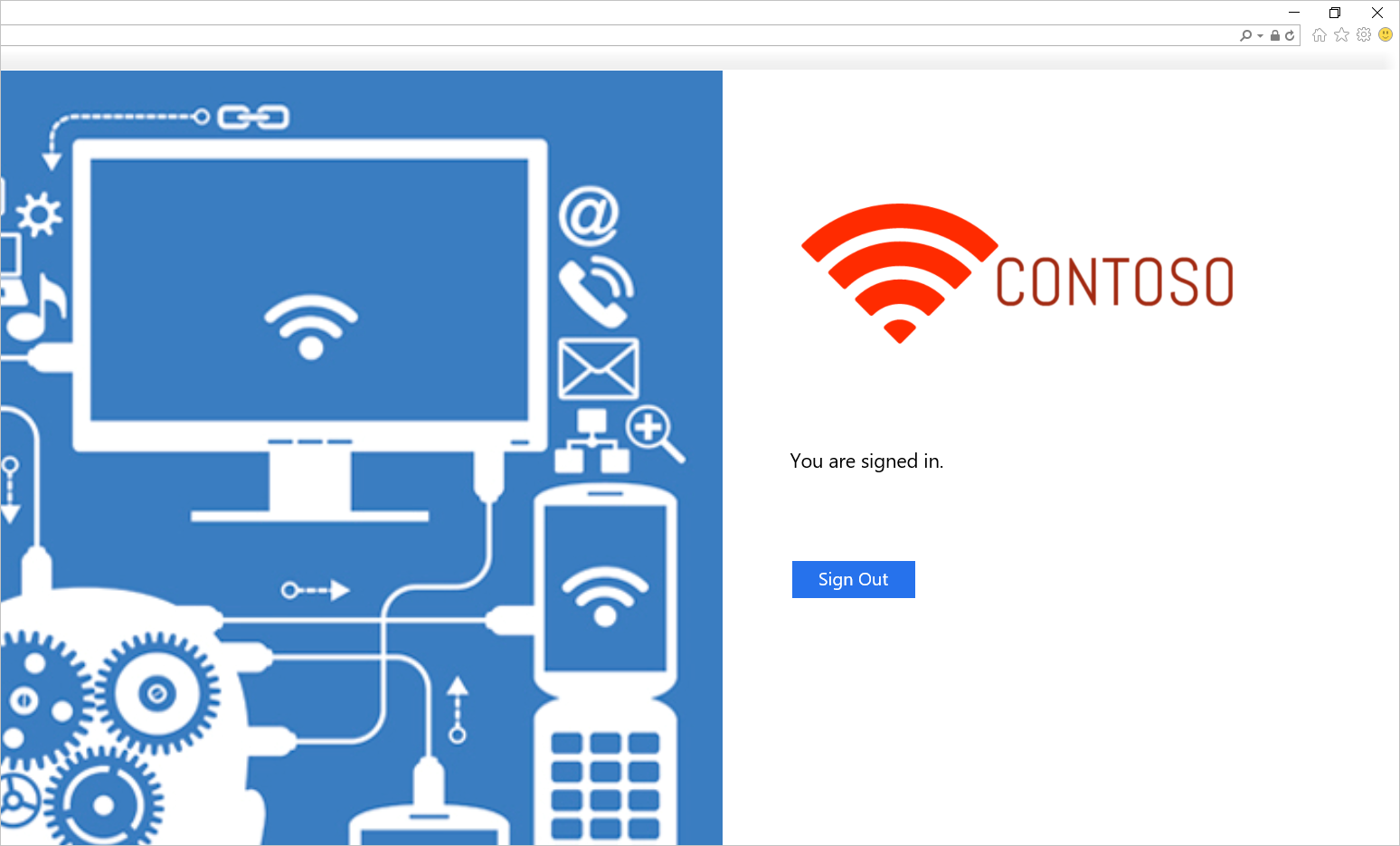
Zkuste se přihlásit. Pokud se úspěšně přihlásíte, měla by se zobrazit zpráva, jak je znázorněno na následujícím snímku obrazovky.
Šablona pro nasazení služby AD FS v Azure
Šablona nasadí nastavení se šesti počítači se dvěma počítači pro řadiče domény, službu AD FS a WAP.
Ad FS v šabloně nasazení Azure
Při nasazování této šablony můžete použít existující virtuální síť nebo vytvořit novou virtuální síť. Následující tabulka uvádí parametry, které můžete použít k přizpůsobení nasazení.
| Parameter | Popis |
|---|---|
| Místo | Oblast, do které chcete prostředky nasadit. |
| TypÚčtuÚložiště | Typ účtu úložiště, který chcete vytvořit. |
| VirtualNetworkUsage | Určuje, jestli chcete vytvořit novou virtuální síť nebo použít existující. |
| VirtualNetworkName | Název virtuální sítě. Povinné pro stávající i nové využití virtuální sítě. |
| VirtualNetworkResourceGroupName | Určuje název skupiny prostředků, ve které se nachází existující virtuální síť. Pokud používáte existující virtuální síť, je tato možnost povinným parametrem, aby nasazení zjistilo ID existující virtuální sítě. |
| VirtualNetworkAddressRange | Rozsah adres nové virtuální sítě. Povinné, pokud vytváříte novou virtuální síť. |
| InternalSubnetName | Název interní podsítě. Povinné pro nové i existující možnosti využití virtuální sítě. |
| InternalSubnetAddressRange | Rozsah adres interní podsítě, která obsahuje řadiče domény a servery AD FS. Povinné, pokud vytváříte novou virtuální síť. |
| DMZSubnetAddressRange | Rozsah adres podsítě DMZ, která obsahuje proxy servery aplikací pro Windows. Povinné, pokud vytváříte novou virtuální síť. |
| DMZSubnetName | Název interní podsítě, která je povinná pro nové i stávající možnosti využití virtuální sítě. |
| ADDC01NICIPAddress | Interní IP adresa prvního řadiče domény. Tato IP adresa je staticky přiřazená řadiči domény a musí být platnou IP adresou v rámci interní podsítě. |
| ADDC02NIC IP adresa | Interní IP adresa druhého řadiče domény. Tato IP adresa je staticky přiřazená řadiči domény a musí být platnou IP adresou v rámci interní podsítě. |
| ADFS01NICIPAddress | Interní IP adresa prvního serveru služby AD FS. Tato IP adresa je staticky přiřazena k serveru služby AD FS a musí být platnou IP adresou v rámci interní podsítě. |
| ADFS02NICIPAddress | Interní IP adresa druhého serveru AD FS. Tato IP adresa je staticky přiřazena k serveru služby AD FS a musí být platnou IP adresou v rámci interní podsítě. |
| WAP01NICIPAddress | Interní IP adresa prvního serveru WAP. Tato IP adresa je staticky přiřazena k serveru WAP a musí být platnou IP adresou v podsíti DMZ. |
| WAP02NICIPAddress | Interní IP adresa druhého serveru WAP. Tato IP adresa je staticky přiřazena k serveru WAP a musí být platnou IP adresou v podsíti DMZ. |
| Soukromá IP adresa vyrovnávače zatížení ADFS | Interní IP adresa nástroje pro vyrovnávání zatížení služby AD FS. Tato IP adresa je staticky přiřazená nástroji pro vyrovnávání zatížení a musí být platnou IP adresou v rámci interní podsítě. |
| ADDCVMNamePrefix | Předpona názvu VM pro řadiče domény |
| ADFSVMNamePrefix | Předpona názvu virtuálního počítače pro servery AD FS. |
| WAPVMNamePrefix | Předpona názvu VM pro servery WAP |
| ADDCVMSize | Velikost VM řadičů domény. |
| ADFSVMSize | Velikost virtuálního počítače serverů AD FS. |
| WAPVMSize | Velikost virtuálního počítače serverů WAP. |
| AdminUserName | Název místního správce virtuálních počítačů. |
| AdminPassword | Heslo pro účet místního správce virtuálních počítačů. |
Související odkazy
- Skupiny dostupnosti
- Azure Load Balancer
- Interní nástroj pro vyrovnávání zatížení
- Internetový nástroj pro vyrovnávání zatížení
- Úložištní účty
- Virtuální sítě Azure
- Odkazy AD FS a proxy webových aplikací
Další kroky
- Integrujte své lokální identity s Microsoft Entra ID
- Konfigurace a správa služby AD FS pomocí služby Microsoft Entra Connect
- Vysoká dostupnost nasazení AD FS napříč geografickými oblastmi v Azure s využitím služby Azure Traffic Manager