Poznámka:
Přístup k této stránce vyžaduje autorizaci. Můžete se zkusit přihlásit nebo změnit adresáře.
Přístup k této stránce vyžaduje autorizaci. Můžete zkusit změnit adresáře.
Jedním z klíčových rozdílů mezi aplikacemi pro UPW a tradičními desktopovými aplikacemi je to, že názvy UPW se nacházejí v kontejneru aplikace, který podléhá správě životního cyklu procesů (PLM). Aplikace pro UPW je možné pozastavit, obnovit nebo ukončit na všech platformách službou Runtime Broker a existují vyhrazené nástroje, které můžete použít k vynucení těchto přechodů při testování nebo ladění kódu, který je zpracovává.
Funkce v sadě Visual Studio 2015
Integrovaný ladicí program v sadě Visual Studio 2015 vám může pomoct prozkoumat potenciální problémy při používání exkluzivních funkcí UPW. Aplikaci můžete přepnout do různých stavů PLM pomocí panelu nástrojů Události životního cyklu, který se zobrazí při spuštění a ladění aplikace.
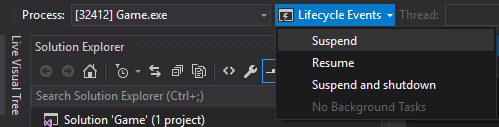
Nástroj PLMDebug
PLMDebug.exe je nástroj příkazového řádku, který umožňuje řídit stav PLM balíčku aplikace a dodává se jako součást sady Windows SDK. Po instalaci se nástroj ve výchozím nastavení nachází ve složce C:\Program Files (x86)\Windows Kits\10\Debuggers\x64 .
PLMDebug také umožňuje zakázat PLM pro všechny nainstalované balíčky aplikací, což je nezbytné pro některé ladicí programy. Zakázáním PLM zabráníte ukončení aplikace službou Runtime Broker, než budete mít možnost ladit. Pokud chcete plM zakázat, použijte přepínač /enableDebug následovaný úplným názvem balíčku aplikace UPW (krátký název, název rodiny balíčků nebo AUMID balíčku nebude fungovat):
plmdebug /enableDebug [PackageFullName]
Po nasazení aplikace pro UPW ze sady Visual Studio se v okně výstupu zobrazí celý název balíčku. Případně můžete úplný název balíčku načíst spuštěním rutiny Get-AppxPackage v konzole PowerShellu.
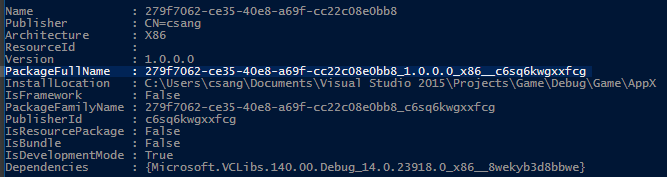
Volitelně můžete zadat absolutní cestu k debuggeru, který se automaticky spustí při aktivaci balíčku vaší aplikace. Pokud to chcete udělat pomocí sady Visual Studio, budete muset jako ladicí program zadat VSJITDebugger.exe. VSJITDebugger.exe ale vyžaduje, abyste zadali přepínač -p spolu s ID procesu (PID) aplikace pro UPW. Vzhledem k tomu, že není možné předem znát PID vaší aplikace pro UWP, tento scénář není možný implementovat přímo.
Toto omezení můžete obejít tak, že napíšete skript nebo nástroj, který identifikuje proces vaší hry, a pak shell spustí VSJITDebugger.exe, předá PID vaší aplikace UPW. Následující ukázka kódu jazyka C# ukazuje jednoduchý přístup k tomuto účelu.
using System.Diagnostics;
namespace VSJITLauncher
{
class Program
{
static void Main(string[] args)
{
// Name of UWP process, which can be retrieved via Task Manager.
Process[] processes = Process.GetProcessesByName(args[0]);
// Get PID of most recent instance
// Note the highest PID is arbitrary. Windows may recycle or wrap the PID at any time.
int highestId = 0;
foreach (Process detectedProcess in processes)
{
if (detectedProcess.Id > highestId)
highestId = detectedProcess.Id;
}
// Launch VSJITDebugger.exe, which resides in C:\Windows\System32
ProcessStartInfo startInfo = new ProcessStartInfo("vsjitdebugger.exe", "-p " + highestId);
startInfo.UseShellExecute = true;
Process process = new Process();
process.StartInfo = startInfo;
process.Start();
}
}
}
Příklad použití ve spojení s PLMDebug:
plmdebug /enableDebug 279f7062-ce35-40e8-a69f-cc22c08e0bb8_1.0.0.0_x86__c6sq6kwgxxfcg "\"C:\VSJITLauncher.exe\" Game"
kde Game je název procesu a 279f7062-ce35-40e8-a69f-cc22c08e0bb8_1.0.0.0_x86__c6sq6kwgxxfcg je úplný název balíčku ukázkového balíčku aplikace pro UPW.
Všimněte si, že každé volání /enableDebug musí být později svázáno s jiným voláním PLMDebug s přepínačem /disableDebug . Kromě toho musí být cesta k ladicímu programu absolutní (relativní cesty nejsou podporovány).