Applies to:
Azure SQL Managed Instance
This article contains the most common questions about Azure SQL Managed Instance.
Note
Microsoft Entra ID was previously known as Azure Active Directory (Azure AD).
Supported features
Where can I find a list of features supported on SQL Managed Instance?
For a list of supported features in SQL Managed Instance, see Azure SQL Managed Instance features.
For differences in syntax and behavior between Azure SQL Managed Instance and SQL Server, see T-SQL differences from SQL Server.
Technical specification, resource limits and other limitations
Where can I find technical characteristics and resource limits for SQL Managed Instance?
For available hardware characteristics, see Technical differences in hardware configurations. For available service tiers and their characteristics, see Technical differences between service tiers.
What service tier am I eligible for?
Any customer is eligible for any service tier. Both Standard and Enterprise editions covered with Software Assurance can be exchanged by using the Azure Hybrid Benefit (AHB) for the General Purpose (which includes the Next-gen General Purpose service tier upgrade, currently in preview) or Business Critical service tier using the following exchange ratios 1 Standard edition = 1 General Purpose, 1 Enterprise edition = 1 Business Critical, 1 Enterprise edition = 4 General Purpose, and 4 General Purpose = 1 Enterprise Edition. For more information, see Specific rights of the AHB.
What subscription types are supported for SQL Managed Instance?
For the list of supported subscription types, see Supported subscription types.
Which Azure regions are supported?
Managed instances can be created in most of the Azure regions; see Supported regions for SQL Managed Instance. If you need managed instance in a region that is currently not supported, send a support request via the Azure portal.
Are there any quota limitations for SQL Managed Instance deployments?
SQL Managed Instance has two default limits: limit on the number of subnets you can use and a limit on the number of vCores you can provision. Limits vary across the subscription types and regions. For the list of regional resource limitations by subscription type, see table from Regional resource limitation. These are soft limits that can be increased on demand. If you need to provision more managed instances in your current regions, send a support request to increase the quota using the Azure portal. For more information, see Request quota increases for Azure SQL Database.
Can I increase the number of databases limit (100) on my managed instance on demand?
The limit of 100 databases per SQL Managed Instance is a hard limit that can't be changed in the General Purpose and Business Critical service tiers. You can have up to 500 databases in the Next-gen General Purpose service tier.
Where can I migrate if I have more than 16 TB of data?
You can consider migrating to other Azure flavors that suit your workload: Azure SQL Database Hyperscale or SQL Server on Azure Virtual Machines.
Where can I migrate if I have specific hardware requirements such as larger RAM to vCore ratio or more CPUs?
You can consider migrating to SQL Server on Azure Virtual Machines or Azure SQL Database memory/cpu optimized.
Known issues and defects
Where can I find known issues and defects?
For product defects and known issues, see Known issues.
New features
Where can I find latest features and the features in public preview?
For new and preview features, see What's new.
Create, update, delete, or move a managed instance
How can I provision a managed instance?
You can provision a managed instance from Azure portal, PowerShell, Azure CLI and ARM templates.
Can I provision managed instances in an existing subscription?
Yes, you can provision a managed instance in an existing subscription if that subscription belongs to the Supported subscription types.
Why couldn't I provision a managed instance in the subnet which name starts with a digit?
This is a current limitation on underlying component that verifies subnet name against the regex ^[a-zA-Z_][^\/:*?"<>|`'^]*(?<![.\s])$. All names that pass the regex and are valid subnet names are currently supported.
How can I scale my managed instance?
You can scale your managed instance from Azure portal, PowerShell, Azure CLI or ARM templates.
Can I move my managed instance from one region to another?
Yes, you can. For instructions, see Move resources across regions.
How can I delete my managed instance?
You can delete managed instances via Azure portal, PowerShell, Azure CLI or Resource Manager REST APIs.
How much time does it take to create or update an instance, or to restore a database?
Expected time to create a new managed instance or to change service tiers (vCores, storage), depends on several factors. See Management operations.
Create, update, delete, or move database
Can I drop and recreate a database on a managed instance using the same database name?
Restoring each database is guaranteed during the entire defined retention period - even databases that were created and then deleted after only a few seconds. When a database is created, deleted, or restored, backups are taken at different intervals to preserve the data so it's possible to restore during the given retention period. If a database is dropped before a backup operation completes, the drop operation might be blocked with the following error:
Message database 'backup_restore_db_lkg_native_restore' already exists. Choose a different database name.
To avoid this error, check the state of the drop operation before recreating a database with the same name. For more information, see sys.dm_operation_status. Once the operation state shows Completed, it's possible to RESTORE or CREATE a database with the same name.
The following common use cases are likely to encounter this error:
If multiple databases are dropped and created again with the same name in short succession. When a database is dropped, the remaining tail-end of the transaction log is backed up synchronously before the drop operation finishes, as the image shows:
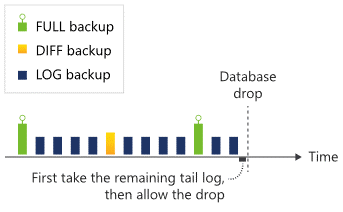
It's not possible to create a database with the same name until the tail-log is backed up and the drop operation completes. The sequential nature of the drop operation puts databases dropped in short succession into a queue, which can prolong the process of dropping the databases and delays the possibility of creating new ones using the same name.
If a database is restored and dropped before a full backup is created. When a database is restored, the first step of the restoration process is to take a new full backup of the database. If you try to restore a database, and then drop it immediately before the full backup completes, you won't be able to drop the database and create another database with that same name until the full backup is taken, and the database drop operation completes. Depending on the size of the database, the full backup could take hours.
Free SQL Managed Instance offer
What if I don't see the banner and **Apply Offer** button?
It's possible your subscription isn't eligible for the free SQL Managed Instance. Otherwise, there's a limit of one free instance per subscription. You need to remove an existing free instance to create another one. If you have recently deleted your free instance, it can take up to one hour for the free offer banner to reappear.
Help! I'm no longer able to connect to my instance!
It's likely you ran out of credits for the month. Go to your SQL managed instance in the Azure portal and check the state to see if your instance is in a stopped state due to insufficient credits.
My vCore hours are being used faster than I expected, how can I see what is using the vCore hours?
This functionality is currently unavailable.
Can I restore a database to the free instance?
Yes, you can restore an automated backup from Azure storage, or you can Restore a database backup by using SQL Server Management Studio (SSMS).
Does the free Azure SQL Managed Instance offer provide a production-quality instance?
Despite the resource limitations, the free SQL Managed is designed to let you test your workloads without any impact. The performance you experience while using the free SQL Managed Instance is identical to the performance of a production version of the instance.
Can I upgrade to a larger or more powerful instance?
The free SQL Managed Instance offers 4 and 8 vCore options. If your business requires an instance with more resources, create a fully fledged paid SQL Managed Instance.
Can I change the backup option to geo-redundant storage?
Backup options can't be changed for the free SQL Managed Instance.
Can I use my Student subscription with the free Azure SQL Managed Instance?
Currently, the Student subscription is ineligible. For eligible subscriptions, review the free SQL Managed Instance offer prerequisites.
Naming conventions
Can a managed instance have the same name as a SQL Server on-premises instance?
Changing a managed instance name isn't supported.
Can I change DNS zone prefix?
Yes, the SQL Managed Instance default DNS zone .database.windows.net can be changed with your own. However, the managed instance hostname part of its FQDN should remain the same.
To use another DNS zone instead of the default, for example, .contoso.com:
- Use SQL Server Client Network Utility (CliConfg) to define an alias. You can use either just the managed instance hostname, or the managed instance hostname followed by a custom domain name. The CliConfg tool just adds alias in the registry under "HKLM\SOFTWARE\Microsoft\MSSQLServer\Client\ConnectTo" or "HKLM\SOFTWARE\WOW6432Node\Microsoft\MSSQLServer\Client\ConnectTo" depending if you use the 64-bit version (C:\Windows\System32\cliconfg.exe) or the 32-bit version (C:\Windows\SysWOW64\cliconfg.exe), so it can be done using group policy or a script as well. Use both to ensure 32-bit and 64-bit programs can resolve the alias.
- Use CNAME record in DNS with managed instance hostname pointing to managed instance FQDN. In this case,
TrustServerCertificate=TRUEis needed when using authentication with Microsoft Entra ID (formerly Azure Active Directory). - Use A record in DNS with managed instance hostname pointing to the managed instance IP address. Using IP address isn't recommended, as it can change without notice. In this case,
TrustServerCertificate=TRUEis needed when using Microsoft Entra authentication.
Migration options
How can I migrate from Azure SQL Database single or elastic pool to SQL Managed Instance?
Azure SQL Managed Instance offers the same performance levels per compute and storage size as other deployment options of Azure SQL Database. If you want to consolidate data on a single instance, or you simply need a feature supported exclusively in SQL Managed Instance, you can migrate your data by using export/import (BACPAC) functionality. Here are other ways to consider for SQL Database migration to SQL Managed Instance:
- Using Data Source External
- Using SQLPackage
- Using BCP
How can I migrate my instance database to a single Azure SQL Database?
One option is to export a database to BACPAC and then import the BACPAC file. This is the recommended approach if your database is smaller than 100 GB.
Transactional replication can be used if all tables in the database have primary keys and there are no In-memory OLTP objects in the database.
How can I migrate my SQL Server instance to SQL Managed Instance?
To migrate your SQL Server instance, see SQL Server to Azure SQL Managed Instance Guide.
How can I migrate from other platforms to SQL Managed Instance?
For migration information about migrating from other platforms, see Azure Database Migration Guide.
Performance
How can I compare Azure SQL Managed Instance performance to SQL Server performance?
For a performance comparison between managed instance and SQL Server, a good starting point is Best practices for performance comparison between Azure SQL Managed Instance and SQL Server article.
What causes performance differences between SQL Managed Instance and SQL Server?
See Key causes of performance differences between SQL Managed Instance and SQL Server. The transaction log file size can impact General Purpose SQL Managed Instance performance. For more information, see Impact of log file size on General Purpose.
How do I tune performance of my managed instance?
You can optimize the performance of your managed instance by:
- Automatic tuning that provides peak performance and stable workloads through continuous performance tuning based on AI and machine learning.
- In-memory OLTP that improves throughput and latency on transactional processing workloads and delivers faster business insights.
- Applying some of the best practices for application and database tuning.
- Switching the connection type from proxy to redirect mode for lower latency and higher throughput, in case your workload consists of lots of small transactions.
How can I further tune performance of my General Purpose managed instance?
To improve performance on a General Purpose instance, consider increasing data file size. To optimize storage performance on a General Purpose instance, see Storage best practice guidelines for General Purpose tier.
My query duration is too long. How can I analyze wait statistics on my managed instance?
See Analyzing wait statistics on SQL Managed Instance. Wait statistics are information that might help you understand why the query duration is long and identify the queries that are waiting for something in database engine.
Monitoring, Metrics and Alerts
What are the options for monitoring and alerting for my managed instance?
For all possible options to monitor and alert on SQL Managed Instance consumption and performance, see Azure SQL Managed Instance monitoring options blog post. For the real-time performance monitoring for SQL Managed Instance, see Real-time performance monitoring for Azure SQL Managed Instance.
How can I monitor performance of my managed instance?
How can I monitor the real-time performance of my managed instance?
Can I use SQL Profiler for performance tracking?
Yes, SQL Profiler is supported on SQL Managed Instance. For more information, see SQL Profiler. Instead, however, you should consider Extended Events for "tracing" activity with less impact to the monitored instance. For more information, see Extended Events.
Are Database Advisor and Query Performance Insight supported for SQL Managed Instance databases?
No, they aren't supported. You can use DMVs and Query Store together with SQL Profiler and XEvents to monitor your databases.
How can I monitor CPU usage on my managed instance?
Can I create metric alerts on SQL Managed Instance?
Yes. For instructions, see Create alerts for SQL Managed Instance. For more tips and tricks, see the blog.
Can I create metric alerts on a database in a managed instance?
You can't, alerting metrics are available for a managed instance only. Alerting metrics for individual databases in a managed instance aren't available.
Storage size
What is the maximum storage size for SQL Managed Instance?
Storage size for SQL Managed Instance depends on the selected service tier (General Purpose, Next-gen General Purpose or Business Critical). For storage limitations of these service tiers, see Resource limits.
What is the minimum storage size available for a managed instance?
The minimum amount of storage available in an instance is 32 GB. Storage can be added in increments of 32 GB up to the maximum storage size. First 32 GB are free of charge.
Can I increase storage space assigned to an instance, independently from compute resources?
Yes, you can purchase add-on storage, independently from compute, to some extent. See Max instance reserved storage in the Table.
How can I optimize my storage performance in General Purpose service tier?
To optimize storage performance, see Storage best practices in General Purpose.
Back up and restore
Is the backup storage deducted from my managed instance storage?
No, backup storage isn't deducted from your managed instance storage space. The backup storage is independent from the instance storage space and it isn't limited in size. Backup storage is limited by the time period to retain the backup of your instance databases, configurable up to 35 days. For details, see Automated backups.
How can I see when automated backups are made on my managed instance?
To track when automated backups have been performed on a SQL managed instance, review Monitor backup activity.
Is on-demand backup supported?
Yes, you can create a copy-only full backup in their Azure Blob Storage, but it will only be restorable to a managed instance. For details, see Copy-only backup. However, copy-only backup is impossible if the database is encrypted by service-managed TDE since the certificate used for encryption is inaccessible. In such case, use point-in-time-restore feature to move the database to another managed instance, or switch to customer-managed key.
Is native restore (from .bak files) to SQL Managed Instance supported?
Yes, it's supported and available for SQL Server 2005+ versions. To use native restore, upload your .bak file to Azure blob storage and execute T-SQL commands. For more information, see Native restore from URL.
Is native restore from SQL Managed Instance to SQL Server supported?
Yes, but only to SQL Server 2022, during the mainstream support period of SQL Server 2022. It's possible that, in the future, some Azure SQL Managed Instance features might be introduced that require changes to the database format, making backups incompatible with the latest version of SQL Server. Access to such features requires explicit opt-in.
Business continuity
Are my system databases replicated to the secondary instance in a failover group?
System databases aren't replicated to the secondary instance in a failover group. Therefore, scenarios that depend on objects from the system databases are impossible on the secondary instance unless the objects are manually created on the secondary. For workaround, see Enable scenarios dependent on the object from the system databases.
Networking requirements
What are the current inbound/outbound NSG constraints on the managed instance subnet?
What are the current inbound/outbound NSG constraints on the managed instance subnet?
The required NSG and UDR rules are documented in subnet service-aided configuration, and automatically set by the service. Please keep in mind that these rules are just the ones we need for maintaining the service. To connect to managed instance and use different features you will need to set additional, feature specific rules, that you need to maintain.
How can I set inbound NSG rules on management ports?
SQL Managed Instance is responsible for setting rules on management ports. This is achieved through functionality named service-aided subnet configuration. This is to ensure uninterrupted flow of management traffic in order to fulfill an SLA.
Can I get the source IP ranges that are used for the inbound management traffic?
Yes. You could analyze traffic coming through your networks security group by configuring Network Watcher flow logs.
Can I set NSG to control access to the data endpoint (port 1433)?
Yes. After a managed instance is provisioned, you can set NSG that controls inbound access to the port 1433. It's advised to narrow its IP range as much as possible.
Can I set the NVA or on-premises firewall to filter the outbound management traffic based on FQDNs?
No. This isn't supported for several reasons:
- Routing traffic that represents a response to an inbound management request would be asymmetric and couldn't work.
- Routing traffic to Azure Storage would be affected by throughput constraints and latency so this way we won't be able to provide expected service quality and availability.
- These configurations are error prone and aren't supportable.
Can I set the NVA or firewall for the outbound nonmanagement traffic?
Yes. The simplest way to achieve this is to add 0/0 rule to a UDR associated with the managed instance subnet to route traffic through NVA.
How many IP addresses do I need for a managed instance?
Subnet must have sufficient number of available IP addresses. To determine VNet subnet size for SQL Managed Instance, see Determine required subnet size and range for Azure SQL Managed Instance.
What if there aren't enough IP addresses for performing instance update operation?
In case there aren't enough IP addresses in the subnet where your SQL managed instance is provisioned, create a new subnet and move the SQL managed instance to it. We also suggest that the new subnet is created with more IP addresses allocated so future update operations avoid similar situations. Learn how to move Azure SQL Managed Instance across subnets.
Do I need an empty subnet to create a managed instance?
No. You can use either an empty subnet or a subnet that already contains managed instances.
Can I change the subnet address range?
Not if there are managed instances inside. This is an Azure networking infrastructure limitation. You're only allowed to add additional address space to an empty subnet.
Can I move my managed instance to another subnet?
Yes. A SQL managed instance can be moved to another subnet inside the same virtual network or in a different virtual network in an online way. Learn how to move Azure SQL Managed Instance across subnets.
Do I need an empty virtual network to create a managed instance?
This isn't required. You can either Create a virtual network for Azure SQL Managed Instance or Configure an existing virtual network for Azure SQL Managed Instance.
Can I place a managed instance with other services in a subnet?
No. Currently we don't support placing a managed instance in a subnet that already contains other resource types.
Connectivity
Can I connect to my managed instance using its IP address?
No, this isn't supported. A managed instance's host name maps to the load balancer in front of the managed instance's virtual cluster. As one virtual cluster can host multiple managed instances, a connection can't be routed to the proper managed instance without specifying its name. For more information on SQL Managed Instance virtual cluster architecture, see Virtual cluster connectivity architecture.
Can my managed instance have a static IP address?
Currently, only private endpoints to managed instances guarantee static IP addresses.
In rare but necessary situations, we might do an online migration of a managed instance to a new virtual cluster, or a different virtual machine group within the virtual cluster, because of technology stack changes that aim to improve the security and reliability of the service. Migrating to a new virtual machine group or virtual cluster results in changing the IP address that is mapped to the managed instance host name. The managed instance service doesn't provide static IP address support, and reserves the right to change the IP address without notice, as a part of regular maintenance cycles.
For the above reason, VNet-local and public endpoints should only be accessed via their associated domain names. We strongly discourage relying on immutability of their IP address as doing so might lead to prolonged unavailability while the service is healthy.
If you require a static IP address that is reachable from outside the virtual network, you can deploy Azure Firewall with a frontend public IP address and configure a NAT rule to translate inbound traffic to a managed instance's private endpoint. Then, set up DNS resolution or configure client aliases so that that SQL clients connect to the firewall's public IP address via managed instance's fully qualified domain name.
Does SQL Managed Instance have a public endpoint?
Yes, a public endpoint can be enabled to enable inbound traffic from the Internet to reach SQL Managed Instance. For more information, see Use SQL Managed Instance with public endpoints and Configure public endpoint in SQL Managed Instance.
Can I specify a custom port for SQL data endpoint(s)?
No, using a custom port isn't available. For VNet-local endpoint, SQL Managed Instance uses default port number 1433 and for public data endpoint, SQL Managed Instance uses default port number 3342.
What is the recommended way to connect managed instances placed in different regions?
Both global virtual network peering (VNet peering) and Azure virtual WAN are recommended methods to connect two managed instances in different regions. Express Route circuit peering is an alternative option. If neither option is possible in your environment, the only other connectivity method is a Site-to-Site VPN connection. Configure Site-to-Site VPN by using the Azure portal, PowerShell, or the Azure CLI
Does SQL Managed Instance support Global VNet Peering?
Support for global virtual network peering (VNet peering) for newly created virtual clusters was added to Azure SQL Managed Instance on September 22, 2020. As such, virtual network peering is supported for managed instances created in empty subnets after Sept 22, 2020. For instances deployed before this date, peering support is limited to networks within the same region due to the constraints of global virtual network peering. For more information, review the relevant section of the Azure Virtual Networks frequently asked questions.
To use global VNet peering with instances created before Sept 2020, considering configuring a maintenance window or moving the instance to a new subnet as either option will move the instance to a new virtual cluster that supports global virtual network peering.
See how to check if global virtual network peering is supported on the virtual cluster if needed.
Mitigate data exfiltration risks
How can I mitigate data exfiltration risks?
To mitigate any data exfiltration risks, customers are recommended to apply a set of security settings and controls:
- Turn on Transparent Data Encryption (TDE) on all databases.
- Turn off Common Language Runtime (CLR). This is recommended on-premises as well.
- Use Microsoft Entra authentication only.
- Access the instance with a low-privileged DBA account.
- Configure JIT jumpbox access for the sysadmin account.
- Turn on SQL auditing, and integrate it with alerting mechanisms.
- Turn on Threat Detection from the Microsoft Defender for SQL suite.
- Apply a service endpoint policy to the subnet to control outbound traffic to Azure Storage.
- CREATE EXTERNAL TABLE AS SELECT (CETAS) is disabled by default. To enable CETAS via the
allowPolyBaseExportserver configuration option, see CREATE EXTERNAL TABLE AS SELECT (CETAS).
DNS
Can I configure a custom DNS resolver for SQL Managed Instance?
Can I do a DNS refresh?
Change time zone
Can I change the time zone for an existing managed instance?
Time zone configuration can be set when a managed instance is provisioned for the first time. Changing the time zone of an existing managed instance isn't supported. For details, see Time zone limitations.
Workarounds include creating a new managed instance with the proper time zone and then either performing a manual backup and restore, or what we recommend, performing a cross-instance point-in-time restore.
Security and database encryption
Is the sysadmin server role available for SQL Managed Instance?
Yes, customers can create logins that are members of the sysadmin role. Customers who assume the sysadmin privilege are also assuming responsibility for operating the instance, which can negatively impact the SLA commitment. To add a login to the sysadmin server role, see Microsoft Entra authentication.
Is Transparent Data Encryption supported for SQL Managed Instance?
Yes, Azure SQL Managed Instance supports Transparent Data Encryption (TDE). For details, see Transparent Data Encryption for SQL Managed Instance.
Can I use the "bring your own key" model for TDE?
Yes, Azure Key Vault for BYOK scenario is available for Azure SQL Managed Instance. For details, see Transparent Data Encryption with customer-managed key.
Can I migrate an encrypted SQL Server database?
Yes, you can. To migrate an encrypted SQL Server database, you need to export and import your existing certificates into SQL Managed Instance, then take a full database backup and restore it to a managed instance.
You can also use Azure Database Migration Service to migrate the TDE encrypted databases.
How can I configure TDE protector rotation for SQL Managed Instance?
You can rotate TDE protector for SQL Managed Instance using Azure Cloud Shell. For instructions, see Transparent Data Encryption in SQL Managed Instance using your own key from Azure Key Vault.
Can I restore my encrypted database to SQL Managed Instance?
Yes, you don't need to decrypt your database to restore it to SQL Managed Instance. You do need to provide a certificate/key used as the encryption key protector on the source system to SQL Managed Instance to be able to read data from the encrypted backup file. There are two possible ways to do it:
- Upload certificate-protector to SQL Managed Instance. It can be done using PowerShell only. The sample script describes the whole process.
- Upload asymmetric key-protector to Azure Key Vault and point SQL Managed Instance to it. This approach resembles bring-your-own-key (BYOK) TDE use case that also uses Key Vault integration to store the encryption key. If you don't want to use the key as an encryption key protector, and just want to make the key available for SQL Managed Instance to restore encrypted database(s), follow instructions for setting up BYOK TDE, and don't check the checkbox Make the selected key the default TDE protector.
Once you make the encryption protector available to SQL Managed Instance, you can proceed with the standard database restore procedure.
Purchasing models and benefits
What purchasing models are available for SQL Managed Instance?
SQL Managed Instance offers vCore-based purchasing model.
What cost benefits are available for SQL Managed Instance?
You can save costs with the Azure SQL benefits in the following ways:
- Maximize existing investments in on-premises licenses and save up to 55 percent with Azure Hybrid Benefit.
- Commit to a reservation for compute resources and save up to 33 percent with Reserved Instance Benefit. Combine this with Azure Hybrid benefit for savings up to 82 percent.
- Save up to 55 percent versus list prices with Azure Dev/Test Pricing Benefit that offers discounted rates for your ongoing development and testing workloads.
Who is eligible for Reserved Instance benefit?
To be eligible for reserved Instance benefit, your subscription type must be an enterprise agreement (offer numbers: MS-AZR-0017P or MS-AZR-0148P) or an individual agreement with pay-as-you-go pricing (offer numbers: MS-AZR-0003P or MS-AZR-0023P). For more information about reservations, see Reserved Instance Benefit.
Is it possible to cancel, exchange, or refund reservations?
You can cancel, exchange, or refund reservations with certain limitations. For more information, see Self-service exchanges and refunds for Azure Reservations.
Billing for Azure SQL Managed Instance and backup storage
What are the SQL Managed Instance pricing options?
To explore SQL Managed Instance pricing options, see Pricing page.
How can I track billing cost for my managed instance?
You can do so using the Microsoft Cost Management solution. Navigate to Subscriptions in the Azure portal and select Cost Analysis.
Use the Accumulated costs option and then filter by the Resource type as microsoft.sql/managedinstances.
Can I use Microsoft or third party tools (developer and otherwise) to access SQL Managed Instance without additional cost?
You can use compatible Microsoft or third party client tools to access SQL Managed Instance, and you won't be charged any additional costs on your Azure invoice. However, if some of the tools require a license, you're required to have a legally licensed software. This is governed by separate agreements you have with each individual tool manufacturer.
How much do automated backups cost?
You get the equal amount of free backup storage space as the reserved data storage space purchased, regardless of the backup retention period set. If your backup storage consumption is within the allocated free backup storage space, automated backups on SQL Managed Instance are no additional cost to you, therefore will be free of charge. Exceeding the use of backup storage above the free space result in additional cost. See the Backup storage section of the pricing page for details. More technical information on SQL Managed Instance automated backups is available at Backup storage consumption explained.
How can I monitor billing cost for my backup storage consumption?
You can monitor cost for backup storage via Azure portal. For instructions, see Monitor costs for automated backups.
How can I optimize my backup storage costs on the managed instance?
To optimize your backup storage costs, see Fine backup tuning on SQL Managed Instance.
Cost-saving use cases
Where can I find use cases and resulting cost savings with SQL Managed Instance?
SQL Managed Instance case studies:
To get a better understanding of the benefits, costs, and risks associated with deploying Azure SQL Managed Instance, there's also a Forrester study: The Total Economic Impact of Microsoft Azure SQL Managed Instance databases.
Password policy
What password policies are applied for SQL Managed Instance SQL logins?
SQL Managed Instance password policy for SQL logins inherits Azure platform policies that are applied to the VMs forming virtual cluster holding the managed instance. At the moment it is not possible to change any of these settings as these settings are defined by Azure and inherited by managed instance.
Important
Azure platform can change policy requirements without notifying services relying on that policies.
What are current Azure platform policies?
Each login must set its password upon sign-in, and change its password after it reaches maximum age.
| Policy | Security Setting |
|---|---|
| Maximum password age | 42 days |
| Minimum password age | One day |
| Minimum password length | 10 characters |
| Password must meet complexity requirements | Enabled |
Is it possible to disable password complexity and expiration in SQL Managed Instance at the login level?
Yes, it's possible to control CHECK_POLICY and CHECK_EXPIRATION fields at the login level. You can check current settings by executing following T-SQL command:
SELECT *
FROM sys.sql_logins
After that, you can modify specified login settings by executing :
ALTER LOGIN <login_name> WITH CHECK_POLICY = OFF;
ALTER LOGIN <login_name> WITH CHECK_EXPIRATION = OFF;
(Replace 'test' with desired login name and adjust policy and expiration values.)
Service updates
What is the Root CA change for Azure SQL Database & SQL Managed Instance?
What is a planned maintenance event for SQL Managed Instance?
Azure feedback and support
Where can I leave my ideas for SQL Managed Instance improvements?
You can vote for a new SQL Managed Instance feature or create a new improvement idea in the SQL Managed Instance Feedback Forum. This way you can contribute to the product development and help us prioritize our potential improvements.
How can I create Azure support request?
To learn how to create Azure support request, see How to create Azure support request.
November 2022 feature wave
I can no longer see the November 2022 feature wave in the Azure portal. Why?
Changes and capabilities that were introduced in the November 2022 feature wave have been integrated to majority of instances and are now available by default. Since taking separate action to enroll an instance is no longer necessary, options that mention the November 2022 feature wave have been removed from the Azure portal.
My instance isn't able to use features introduced by the November 2022 feature wave. Why?
The feature wave is available to instances in eligible subnets. If you don't see new features, it's likely the subnet that contains your SQL managed instance isn't eligible as it's still in the enrollment process. Instances in subnets not enrolled in the wave continue to see the Feature Wave page in the Azure Portal.
Next-gen General Purpose service tier upgrade
My instance is part of a failover group and when I tried to enable the Next-gen General Purpose upgrade for my instance, it failed. Why?
For instances inside of a failover group, changing the service tier to, or from, the Next-gen General Purpose tier is not supported. You must first delete the failover group before modifying either replica, and then re-create the failover group after the change takes effect.
Why can't I enable zone redundancy for my Next-gen General Purpose SQL Managed Instance?
Zone redundancy is not currently supported for the Next-gen General Purpose service tier.
Can I enable the Next-gen General Purpose upgrade for my for Instance Pool?
No, the Next-gen General Purpose service tier upgrade is not currently supported for Instance Pools, or instances inside a pool.