Begivenhed
31. mar., 23 - 2. apr., 23
Den største Fabric-, Power BI- og SQL-læringshændelse. 31. marts - 2. april. Brug koden FABINSIDER til at gemme $400.
Tilmeld dig i dagDenne browser understøttes ikke længere.
Opgrader til Microsoft Edge for at drage fordel af de nyeste funktioner, sikkerhedsopdateringer og teknisk support.
This article describes how to run your Azure Stream Analytics (ASA) job in an Azure virtual network.
Virtual network support enables you to lock down access to Azure Stream Analytics to your virtual network infrastructure. This capability provides you with the benefits of network isolation and can be accomplished by deploying a containerized instance of your ASA job inside your Virtual Network. Your virtual network injected ASA job can then privately access your resources within the virtual network via:
Currently, this capability is only available in select regions: East US, East US 2, West US, West US 2, Central US, North-Central US, Central Canada, West Europe, North Europe, Southeast Asia, Brazil South, Japan East, UK South, Central India, Australia East, France Central, Germany West Central, and UAE North. If you're interested in enabling virtual network integration in your region, fill out this form. Regions are added based on demand and feasibility. We will notify you if we are able to accommodate your request.
A General purpose V2 (GPV2) Storage account is required for virtual network injected ASA jobs.
Virtual network injected ASA jobs require access to metadata such as checkpoints to be stored in Azure tables for operational purposes.
If you already have a GPV2 account provisioned with your ASA job, no extra steps are required.
Users with higher scale jobs with Premium storage are still required to provide a GPV2 storage account.
If you wish to protect storage accounts from public IP based access, consider configuring it using Managed Identity and Trusted Services as well.
For more information on storage accounts, see Storage account overview and Create a storage account.
An Azure Virtual Network, you can use existing or create one.
An operational Azure Nat Gateway, see IMPORTANT note below.
Vigtigt
ASA virtual network injected jobs use an internal container injection technology provided by Azure networking.
To enhance the security and reliability of your Azure Stream Analytics jobs, you will need to either:
Configure a NAT Gateway: This will ensure that all outbound traffic from your VNET is routed through a secure and consistent public IP address.
Disable Default Outbound Access: This will prevent any unintended outbound traffic from your VNET, enhancing the security of your network.
Azure NAT Gateway is a fully managed and highly resilient Network Address Translation (NAT) service. When configured on a subnet, all outbound connectivity uses the NAT gateway's static public IP addresses.
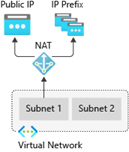
For more information about Azure NAT Gateway, see Azure NAT Gateway.
Virtual network integration depends on a dedicated subnet.
When configuring your delegated subnet, it is crucial to consider the IP range to accommodate both current and future requirements for your ASA workload. Since the subnet size cannot be modified once established, it is recommended to select a subnet size that can support the potential scale of your job. Additionally, be aware that Azure Networking reserves the first five IP addresses within the subnet range for internal use.
The scale operation affects the real, available supported instances for a given subnet size.
When you indicate virtual network integration with your Azure Stream Analytics job, Azure portal automatically delegates the subnet to the ASA service. Azure undelegates the subnet in the following scenarios:
The subnet configuration must enable intra-subnet network traffic. This means that it must allow inbound and outbound traffic where both the source and destination IP addresses reside within the same subnet. Learn more here.
Several Stream Analytics jobs can utilize the same subnet. The last job here refers to no other jobs utilizing the specified subnet. When the last job has been deleted or removed by associated, Azure Stream Analytics releases the subnet as a resource, which was delegated to ASA as a service. Allow several minutes for this action to be completed.
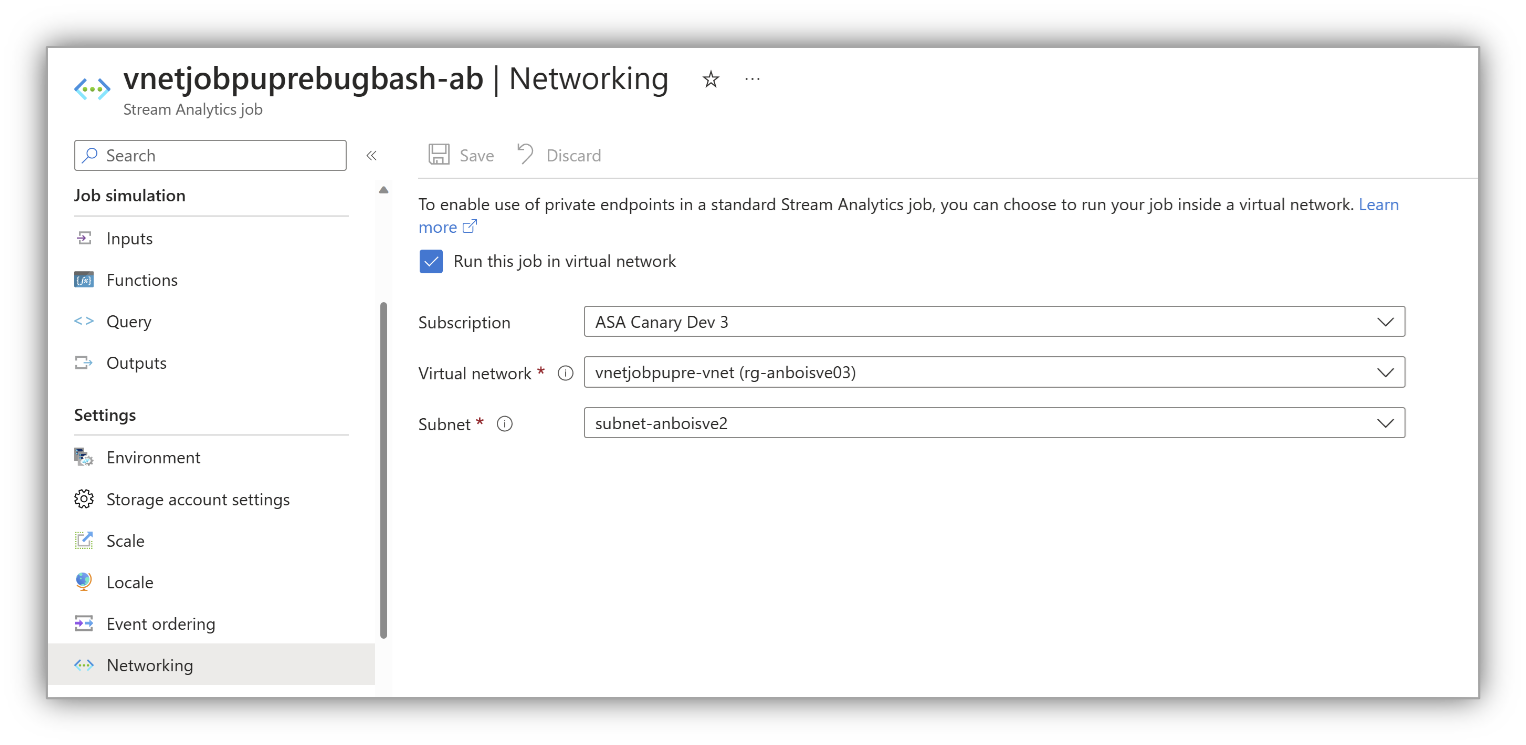
From the Azure portal, navigate to Networking from menu bar and select Run this job in virtual network. This step informs us that your job must work with a virtual network:
Configure the settings as prompted and select Save.
In Visual Studio Code, reference the subnet within your ASA job. This step tells your job that it must work with a subnet.
In the JobConfig.json, set up your VirtualNetworkConfiguration as shown in the following image.
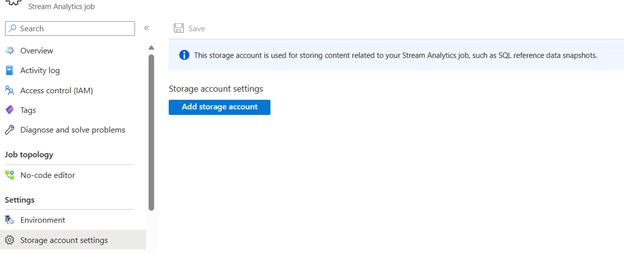
On the Stream Analytics job page, select Storage account settings under Configure on the left menu.
On the Storage account settings page, select Add storage account.
Follow instructions to configure your storage account settings.
Vigtigt
You must have at least the following Role-based access control permissions on the subnet or at a higher level to configure virtual network integration through Azure portal, CLI or when setting the virtualNetworkSubnetId site property directly:
| Action | Description |
|---|---|
Microsoft.Network/virtualNetworks/read |
Read the virtual network definition |
Microsoft.Network/virtualNetworks/subnets/read |
Read a virtual network subnet definition |
Microsoft.Network/virtualNetworks/subnets/join/action |
Joins a virtual network |
Microsoft.Network/virtualNetworks/subnets/write |
Optional. Required if you need to perform subnet delegation |
If the virtual network is in a different subscription than your ASA job, you must ensure that the subscription with the virtual network is registered for the Microsoft.StreamAnalytics resource provider. You can explicitly register the provider by following this documentation, but it's automatically registered when creating the job in a subscription.
No extra configuration is required for the virtual network integration feature to reach through your virtual network to on-premises resources. You simply need to connect your virtual network to on-premises resources by using ExpressRoute or a site-to-site VPN.
Outside of basic requirements listed in this document, virtual network integration has no extra charge for use beyond the Azure Stream Analytics pricing charges.
The feature is easy to set up, but that doesn't mean your experience is problem free. If you encounter problems accessing your desired endpoint, contact Microsoft Support.
Bemærk
For direct feedback on this capability, reach out to askasa@microsoft.com.
Begivenhed
31. mar., 23 - 2. apr., 23
Den største Fabric-, Power BI- og SQL-læringshændelse. 31. marts - 2. april. Brug koden FABINSIDER til at gemme $400.
Tilmeld dig i dagTræning
Modul
Konfigurer virtuelle netværk - Training
Få mere at vide om, hvordan du konfigurerer virtuelle netværk og undernet, herunder IP-adressering.
Certificering
Microsoft Certified: Azure Network Engineer Associate - Certifications
Demonstrer design, implementering og vedligeholdelse af Azure-netværksinfrastruktur, belastningsjustering af trafik, netværksrouting og meget mere.