Tutorial: Create a two-way forest trust in Microsoft Entra Domain Services with an on-premises domain (Preview)
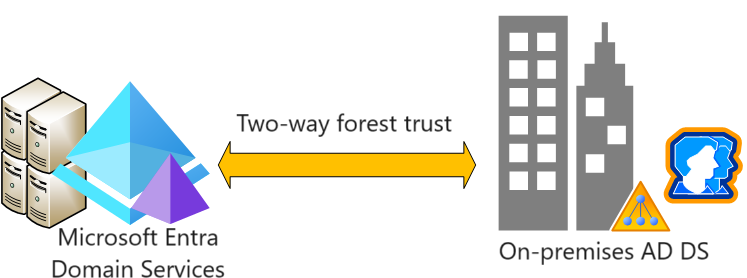
You can create a forest trust between Microsoft Entra Domain Services and on-premises AD DS environments. The forest trust relationship lets users, applications, and computers authenticate against an on-premises domain from the Domain Services managed domain, or vice versa. A forest trust can help users access resources in scenarios such as:
- Environments where you can't synchronize password hashes, or where users exclusively sign in using smart cards and don't know their password.
- Hybrid scenarios that require access to on-premises domains.
You can choose from three possible directions when you create a forest trust, depending on how users need to access resources. Domain Services only supports forest trusts. An external trust to a child domain on-premises isn't supported.
| Trust direction | User access |
|---|---|
| Two-way (preview) | Allows users in both the managed domain and the on-premises domain to access resources in either domain. |
| One-way outgoing | Allows users in the on-premises domain to access resources in the managed domain, but not vice versa. |
| One-way incoming (preview) | Allows users in the managed domain to access resources in the on-premises domain. |
In this tutorial, you learn how to:
- Configure DNS in an on-premises AD DS domain to support Domain Services connectivity
- Create a two-way forest trust between the managed domain and the on-premises domain
- Test and validate the forest trust relationship for authentication and resource access
If you don't have an Azure subscription, create an account before you begin.
Prerequisites
To complete this tutorial, you need the following resources and privileges:
- An active Azure subscription.
- If you don't have an Azure subscription, create an account.
- A Microsoft Entra tenant associated with your subscription, either synchronized with an on-premises directory or a cloud-only directory.
- A Domain Services managed domain that is configured with a custom DNS domain name and a valid SSL certificate.
- An on-premises Active Directory domain that is reachable from the managed domain over a VPN or ExpressRoute connection.
- Application Administrator and Groups Administrator Microsoft Entra roles in your tenant to modify a Domain Services instance.
- A Domain Admin account in the on-premises domain that has the permissions to create and verify trust relationships.
Important
You need to use a minimum of Enterprise SKU for your managed domain. If needed, change the SKU for a managed domain.
Sign in to the Microsoft Entra admin center
In this tutorial, you create and configure the outbound forest trust from Domain Services using the Microsoft Entra admin center. To get started, first sign in to the Microsoft Entra admin center.
Networking considerations
The virtual network that hosts the Domain Services forest needs a VPN or ExpressRoute connection to your on-premises Active Directory. Applications and services also need network connectivity to the virtual network hosting the Domain Services forest. Network connectivity to the Domain Services forest must be always on and stable otherwise users may fail to authenticate or access resources.
Before you configure a forest trust in Domain Services, make sure your networking between Azure and on-premises environment meets the following requirements:
- Make sure firewall ports allow traffic that is necessary to create and use a trust. For more information about which ports need to be open to use a trust, see Configure firewall settings for AD DS trusts.
- Use private IP addresses. Don't rely on DHCP with dynamic IP address assignment.
- Avoid overlapping IP address spaces to allow virtual network peering and routing to successfully communicate between Azure and on-premises.
- An Azure virtual network needs a gateway subnet to configure an Azure site-to-site (S2S) VPN or ExpressRoute connection.
- Create subnets with enough IP addresses to support your scenario.
- Make sure Domain Services has its own subnet, don't share this virtual network subnet with application VMs and services.
- Peered virtual networks are NOT transitive.
- Azure virtual network peerings must be created between all virtual networks you want to use the Domain Services forest trust to the on-premises AD DS environment.
- Provide continuous network connectivity to your on-premises Active Directory forest. Don't use on-demand connections.
- Make sure there's continuous DNS name resolution between your Domain Services forest name and your on-premises Active Directory forest name.
Configure DNS in the on-premises domain
To correctly resolve the managed domain from the on-premises environment, you may need to add forwarders to the existing DNS servers. To configure the on-premises environment to communicate with the managed domain, complete the following steps from a management workstation for the on-premises AD DS domain:
Select Start > Administrative Tools > DNS.
Select your DNS zone, such as aaddscontoso.com.
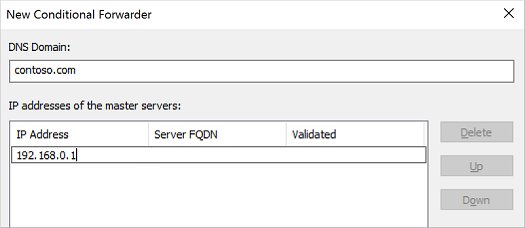
Select Conditional Forwarders, then right-select and choose New Conditional Forwarder...
Enter your other DNS Domain, such as contoso.com, then enter the IP addresses of the DNS servers for that namespace, as shown in the following example:
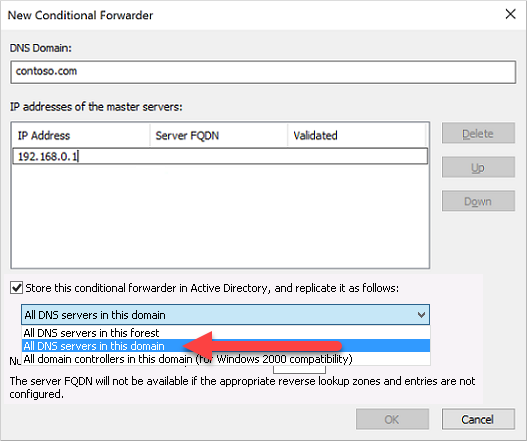
Check the box for Store this conditional forwarder in Active Directory, and replicate it as follows, then select the option for All DNS servers in this domain, as shown in the following example:
Important
If the conditional forwarder is stored in the forest instead of the domain, the conditional forwarder fails.
To create the conditional forwarder, select OK.
Create a two-way forest trust in the on-premises domain
The on-premises AD DS domain needs a two-way forest trust for the managed domain. This trust must be manually created in the on-premises AD DS domain; it can't be created from the Microsoft Entra admin center.
To configure a two-way trust in the on-premises AD DS domain, complete the following steps as a Domain Admin from a management workstation for the on-premises AD DS domain:
- Select Start > Administrative Tools > Active Directory Domains and Trusts.
- Right-click the domain, such as onprem.contoso.com, then select Properties.
- Choose Trusts tab, then New Trust.
- Enter the name for Domain Services domain name, such as aaddscontoso.com, then select Next.
- Select the option to create a Forest trust, then to create a Two-way trust.
- Choose to create the trust for This domain only. In the next step, you create the trust in the Microsoft Entra admin center for the managed domain.
- Choose to use Forest-wide authentication, then enter and confirm a trust password. This same password is also entered in the Microsoft Entra admin center in the next section.
- Step through the next few windows with default options, then choose the option for No, do not confirm the outgoing trust.
- Select Finish.
If the forest trust is no longer needed for an environment, complete the following steps as a Domain Admin to remove it from the on-premises domain:
- Select Start > Administrative Tools > Active Directory Domains and Trusts.
- Right-click the domain, such as onprem.contoso.com, then select Properties.
- Choose Trusts tab, then Domains that trust this domain (incoming trusts), click the trust to be removed, and then click Remove.
- On the Trusts tab, under Domains trusted by this domain (outgoing trusts), click the trust to be removed, and then click Remove.
- Click No, remove the trust from the local domain only.
Create a two-way forest trust in Domain Services
To create the two-way trust for the managed domain in the Microsoft Entra admin center, complete the following steps:
In the Microsoft Entra admin center, search for and select Microsoft Entra Domain Services, then select your managed domain, such as aaddscontoso.com.
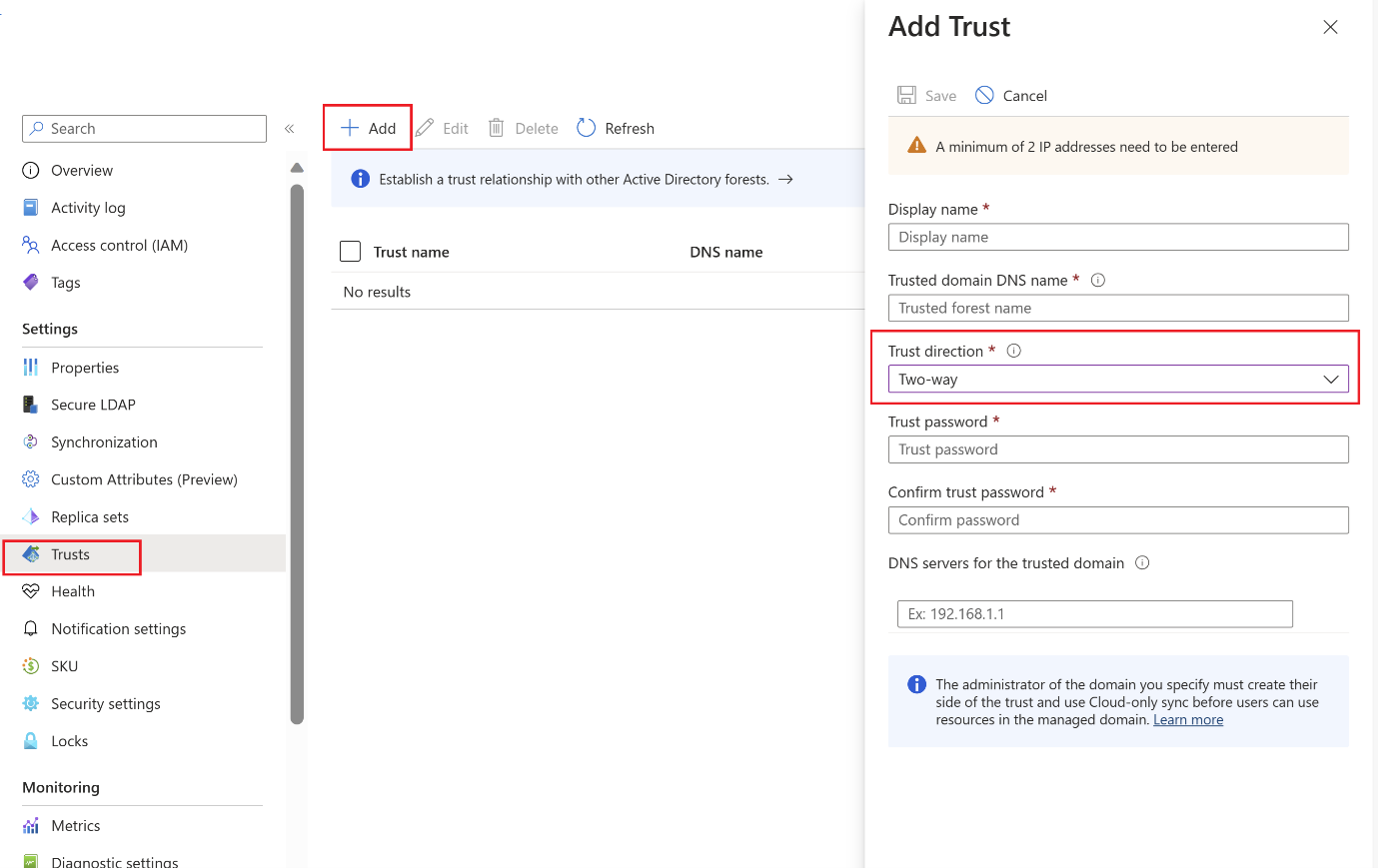
From the menu on the left-hand side of the managed domain, select Trusts, then choose to + Add a trust.
Select Two-way as the trust direction.
Enter a display name that identifies your trust, then the on-premises trusted forest DNS name, such as onprem.contoso.com.
Provide the same trust password that was used to configure the inbound forest trust for the on-premises AD DS domain in the previous section.
Provide at least two DNS servers for the on-premises AD DS domain, such as 10.1.1.4 and 10.1.1.5.
When ready, Save the outbound forest trust.
If the forest trust is no longer needed for an environment, complete the following steps to remove it from Domain Services:
- In the Microsoft Entra admin center, search for and select Microsoft Entra Domain Services, then select your managed domain, such as aaddscontoso.com.
- From the menu on the left-hand side of the managed domain, select Trusts, choose the trust, and click Remove.
- Provide the same trust password that was used to configure the forest trust and click OK.
Validate resource authentication
The following common scenarios let you validate that forest trust correctly authenticates users and access to resources:
- On-premises user authentication from the Domain Services forest
- Access resources in the Domain Services forest using on-premises user
On-premises user authentication from the Domain Services forest
You should have Windows Server virtual machine joined to the managed domain. Use this virtual machine to test your on-premises user can authenticate on a virtual machine. If needed, create a Windows VM and join it to the managed domain.
Connect to the Windows Server VM joined to the Domain Services forest using Azure Bastion and your Domain Services administrator credentials.
Open a command prompt and use the
whoamicommand to show the distinguished name of the currently authenticated user:whoami /fqdnUse the
runascommand to authenticate as a user from the on-premises domain. In the following command, replaceuserUpn@trusteddomain.comwith the UPN of a user from the trusted on-premises domain. The command prompts you for the user's password:Runas /u:userUpn@trusteddomain.com cmd.exeIf the authentication is a successful, a new command prompt opens. The title of the new command prompt includes
running as userUpn@trusteddomain.com.Use
whoami /fqdnin the new command prompt to view the distinguished name of the authenticated user from the on-premises Active Directory.
Access resources in the Domain Services forest using on-premises user
From the Windows Server VM joined to the Domain Services forest, you can test scenarios. For example, you can test if a user who signs in to the on-premises domain can access resources in the managed domain. The following examples cover common test scenarios.
Enable file and printer sharing
Connect to the Windows Server VM joined to the Domain Services forest using Azure Bastion and your Domain Services administrator credentials.
Open Windows Settings.
Search for and select Network and Sharing Center.
Choose the option for Change advanced sharing settings.
Under the Domain Profile, select Turn on file and printer sharing and then Save changes.
Close Network and Sharing Center.
Create a security group and add members
Open Active Directory Users and Computers.
Right-select the domain name, choose New, and then select Organizational Unit.
In the name box, type LocalObjects, then select OK.
Select and right-click LocalObjects in the navigation pane. Select New and then Group.
Type FileServerAccess in the Group name box. For the Group Scope, select Domain local, then choose OK.
In the content pane, double-click FileServerAccess. Select Members, choose to Add, then select Locations.
Select your on-premises Active Directory from the Location view, then choose OK.
Type Domain Users in the Enter the object names to select box. Select Check Names, provide credentials for the on-premises Active Directory, then select OK.
Note
You must provide credentials because the trust relationship is only one way. This means users from the Domain Services managed domain can't access resources or search for users or groups in the trusted (on-premises) domain.
The Domain Users group from your on-premises Active Directory should be a member of the FileServerAccess group. Select OK to save the group and close the window.
Create a file share for cross-forest access
- On the Windows Server VM joined to the Domain Services forest, create a folder and provide name such as CrossForestShare.
- Right-select the folder and choose Properties.
- Select the Security tab, then choose Edit.
- In the Permissions for CrossForestShare dialog box, select Add.
- Type FileServerAccess in Enter the object names to select, then select OK.
- Select FileServerAccess from the Groups or user names list. In the Permissions for FileServerAccess list, choose Allow for the Modify and Write permissions, then select OK.
- Select the Sharing tab, then choose Advanced Sharing….
- Choose Share this folder, then enter a memorable name for the file share in Share name such as CrossForestShare.
- Select Permissions. In the Permissions for Everyone list, choose Allow for the Change permission.
- Select OK two times and then Close.
Validate cross-forest authentication to a resource
Sign in a Windows computer joined to your on-premises Active Directory using a user account from your on-premises Active Directory.
Using Windows Explorer, connect to the share you created using the fully qualified host name and the share such as
\\fs1.aaddscontoso.com\CrossforestShare.To validate the write permission, right-select in the folder, choose New, then select Text Document. Use the default name New Text Document.
If the write permissions are set correctly, a new text document is created. Complete the following steps to open, edit, and delete the file as appropriate.
To validate the read permission, open New Text Document.
To validate the modify permission, add text to the file and close Notepad. When prompted to save changes, choose Save.
To validate the delete permission, right-select New Text Document and choose Delete. Choose Yes to confirm file deletion.
Next steps
In this tutorial, you learned how to:
- Configure DNS in an on-premises AD DS environment to support Domain Services connectivity
- Create a one-way inbound forest trust in an on-premises AD DS environment
- Create a one-way outbound forest trust in Domain Services
- Test and validate the trust relationship for authentication and resource access
For more conceptual information about forest in Domain Services, see How do forest trusts work in Domain Services?.