Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article describes the requirements for installing the Microsoft Defender for Identity sensor v3.x.
Sensor version limitations
Before you activate the Defender for Identity sensor v3.x, note that v3.x:
- Doesn't support VPN integration.
- Has limitations working with Azure ExpressRoute. For more information, see Azure ExpressRoute for Microsoft 365.
Server requirements
Before activating the Defender for Identity sensor v3.x, make sure that the server on which you're activating the sensor:
- Has Defender for Endpoint deployed. The Microsoft Defender Antivirus component can be in either active or passive mode.
- Doesn't have a Defender for Identity sensor v2.x already deployed.
- Is running Windows Server 2019 or later.
- Includes the October 2025 or later cumulative update.
Licensing requirements
Deploying Defender for Identity requires one of the following Microsoft 365 licenses:
- Enterprise Mobility + Security E5 (EMS E5/A5)
- Microsoft 365 E5 (Microsoft E5/A5/G5)
- Microsoft 365 E5/A5/G5/F5* Security
- Microsoft 365 F5 Security + Compliance*
Both F5 licenses require Microsoft 365 F1/F3 or Office 365 F3 and Enterprise Mobility + Security E3. Purchase licenses in the Microsoft 365 portal or through Cloud Solution Partner (CSP) licensing. For more information, see Licensing and privacy FAQs.
Role and permissions requirements
To create your Defender for Identity workspace, you need a Microsoft Entra ID tenant.
You must either be a Security Administrator, or have the following Unified RBAC permissions:
System settings (Read and manage)Security settings (All permissions)
Memory requirements
The following table describes memory requirements on the server used for the Defender for Identity sensor, depending on the type of virtualization you're using:
| VM running on | Description |
|---|---|
| Hyper-V | Ensure that Enable Dynamic Memory isn't enabled for the VM. |
| VMware | Ensure that the amount of memory configured and the reserved memory are the same, or select the Reserve all guest memory (All locked) option in the VM settings. |
| Other virtualization host | Refer to the vendor-supplied documentation on how to ensure that memory is always fully allocated to the VMs. |
Important
When running as a virtual machine, always allocate all memory to the virtual machine.
Version 3 of the sensor prevents the sensor from overusing CPU or memory by limiting CPU utilization at 30%, and memory usage to 1.5 GB. However, if Falcon Identity already uses substantial system resources, the domain controller might still experience performance strain.
Configure RPC auditing
Applying the Unified Sensor RPC Audit tag to a device improves security visibility and unlocks more identity detections. Once applied, the configuration is enforced on all existing and future devices that match the rule criteria. The tag is visible in the Device Inventory for transparency and auditing capabilities.
In the Microsoft Defender portal, navigate to: System > Settings > Microsoft Defender XDR > Asset Rule Management.
Select Create a new rule.
In the side panel:
- Enter a Rule name and Description.
- Set rule conditions using
Device name,Domain, orDevice tagto target the desired machines. Target domain controllers with the sensor v3.x installed. - Make sure that the Defender for Identity sensor v3.x is already deployed on the selected devices.
Add the Unified Sensor RPC Audit tag to the selected devices.
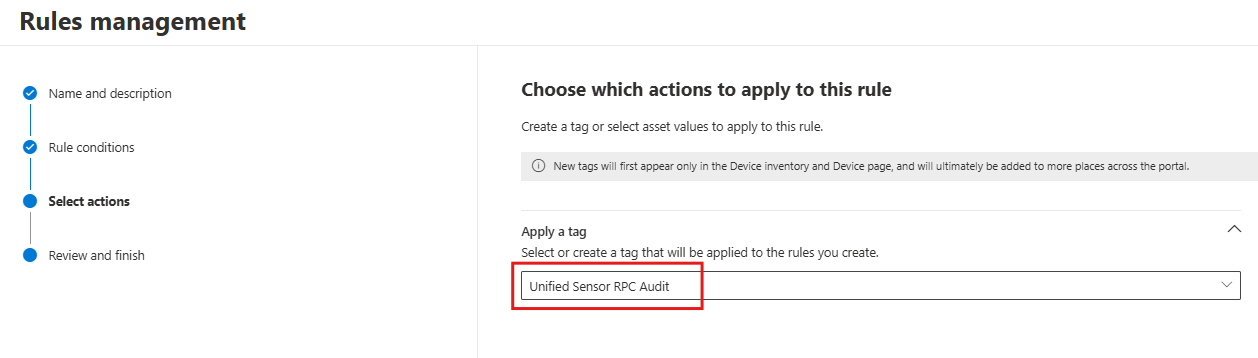
Select Next to review and finish creating the rule, and then select Submit. The rule might take up to one hour to take effect.
Remove RPC auditing from a device
To offboard a device from this configuration, delete the asset rule or modify the rule conditions so the device no longer matches.
Note
It might take up to one hour for changes to be reflected in the portal.
Learn more about asset management rules.
Configure Windows event auditing
Defender for Identity uses Windows event log entries to detect specific activities. This data is used in various detection scenarios and can be used in advanced hunting queries. For optimal protection and monitoring, make sure that collection of windows events is properly configured.
See Configure Defender for Identity to collect Windows events automatically (Preview).
If you don't select automatic Windows auditing configuration, you must configure Windows event auditing manually or using PowerShell.
Recommended configurations for optimal performance
We recommend that you make sure these items are properly configured for optimal performance.
- Set the Power Option of the machine running the Defender for Identity sensor to High Performance.
- Synchronize the time on servers and domain controllers where you install the sensor to within five minutes of each other.
- This sensor uses the local system identity of the server for Active Directory and response actions. If you had Group Managed Service Account (gMSA) configured for an earlier version of the sensor, make sure to remove gMSA. If gMSA is enabled, the response actions won't work. In environments that use both v2 and v3 sensors, use local system accounts for all of your sensors.
Test your prerequisites
We recommend running the Test-MdiReadiness.ps1 script to test and see if your environment has the necessary prerequisites.
The Test-MdiReadiness.ps1 script is also available from Microsoft Defender XDR, on the Identities > Tools page (Preview).