Manage tamper protection for your organization using Microsoft Intune
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender Antivirus
- Microsoft Defender for Business
- Microsoft 365 Business Premium
Platforms
- Windows
Tamper protection helps protect certain security settings, such as virus and threat protection, from being disabled or changed. If you're part of your organization's security team, and you're using Microsoft Intune, you can manage tamper protection for your organization in the Intune admin center. Or, you can use Configuration Manager. With Intune or Configuration Manager, you can perform the following tasks:
- Turn tamper protection on (or off) for some or all devices.
- Protect Microsoft Defender Antivirus exclusions from tampering (certain requirements must be met).
Important
If you're using Microsoft Intune to manage Defender for Endpoint settings, make sure to set DisableLocalAdminMerge to true on devices.
When tamper protection is turned on, tamper-protected settings cannot be changed. To avoid breaking management experiences, including Intune (and Configuration Manager), keep in mind that changes to tamper-protected settings might appear to succeed but are actually blocked by tamper protection. Depending on your particular scenario, you have several options available:
If you must make changes to a device and those changes are blocked by tamper protection, we recommend using troubleshooting mode to temporarily disable tamper protection on the device. Note that after troubleshooting mode ends, any changes made to tamper-protected settings are reverted to their configured state.
You can use Intune or Configuration Manager to exclude devices from tamper protection.
If you're managing tamper protection through Intune, you can change tamper-protected antivirus exclusions.
Requirements for managing tamper protection in Intune
| Requirement | Details |
|---|---|
| Roles and permissions | You must have appropriate permissions assigned through roles, such as Security Administrator. See Microsoft Entra roles with Intune access. |
| Device management | Your organization uses Configuration Manager or Intune to manage devices. Co-Managed devices are not supported for this feature. |
| Intune licenses | Intune licenses are required. See Microsoft Intune licensing. |
| Operating System | Windows devices must be running Windows 10 version 1709 or later or Windows 11. (For more information about releases, see Windows release information.) For Mac, see Protect macOS security settings with tamper protection. |
| Security intelligence | You must be using Windows security with security intelligence updated to version 1.287.60.0 (or later). |
| Antimalware platform | Devices must be using antimalware platform version 4.18.1906.3 (or later) and anti-malware engine version 1.1.15500.X (or later). See Manage Microsoft Defender Antivirus updates and apply baselines. |
| Microsoft Entra ID | Your Intune and Defender for Endpoint tenants must share the same Microsoft Entra infrastructure. |
| Defender for Endpoint | Your devices must be onboarded to Defender for Endpoint. |
Note
If devices are not enrolled in Microsoft Defender for Endpoint, tamper protection shows up as Not Applicable until the onboarding process completes. Tamper protection can prevent changes to security settings from occurring. If you see an error code with Event ID 5013, see Review event logs and error codes to troubleshoot issues with Microsoft Defender Antivirus.
Turn tamper protection on (or off) in Microsoft Intune
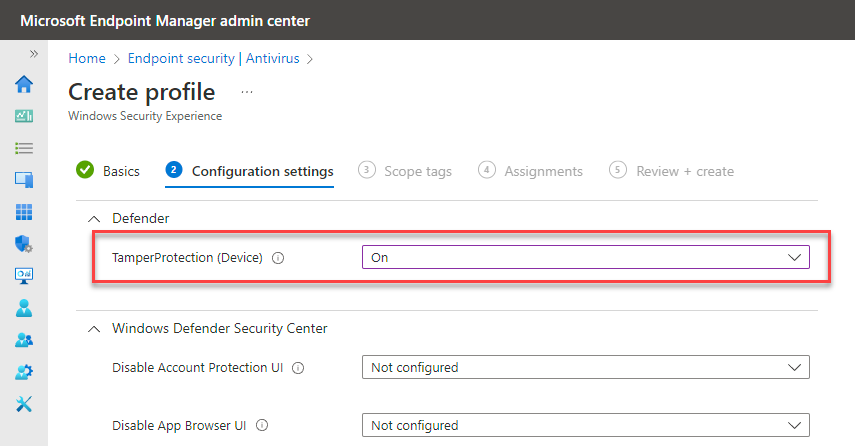
In the Intune admin center, go to Endpoint security > Antivirus, and then choose + Create Policy.
- In the Platform list, select Windows 10, Windows 11, and Windows Server.
- In the Profile list, select Windows Security experience.
Create a profile that includes the following setting:
- TamperProtection (Device): On
Finish selecting options and settings for your policy.
Deploy the policy to devices.
Tamper protection for antivirus exclusions
If your organization has exclusions defined for Microsoft Defender Antivirus, tamper protection protects those exclusions, provided all of the following conditions are met:
| Condition | Criteria |
|---|---|
| Microsoft Defender platform | Devices are running Microsoft Defender platform 4.18.2211.5 or later. For more information, see Monthly platform and engine versions. |
DisableLocalAdminMerge setting |
This setting is also known as preventing local list merging. DisableLocalAdminMerge must be enabled so that settings configured on a device aren't merged with organization policies, such as settings in Intune. For more information, see DisableLocalAdminMerge. |
| Device management | Devices are either managed in Intune only, or are managed with Configuration Manager only. Sense must be enabled. |
| Antivirus exclusions | Microsoft Defender Antivirus exclusions are managed in Microsoft Intune or Configuration Manager. For more information, see Settings for Microsoft Defender Antivirus policy in Microsoft Intune for Windows devices. Functionality to protect Microsoft Defender Antivirus exclusions is enabled on devices. For more information, see How to determine whether antivirus exclusions are tamper protected on a Windows device. |
Note
For example, when Configuration Manager is used solely to manage exclusions and the required conditions are met, exclusions from Configuration Manager are tamper protected. In this case, there is no need to push antivirus exclusions using Microsoft Intune.
For more detailed information about Microsoft Defender Antivirus exclusions, see Exclusions for Microsoft Defender for Endpoint and Microsoft Defender Antivirus.
How to determine whether antivirus exclusions are tamper protected on a Windows device
You can use a registry key to determine whether the functionality to protect Microsoft Defender Antivirus exclusions is enabled. The following procedure describes how to view, but not change, tamper protection status.
On a Windows device open Registry Editor. (Read-only mode is fine; you're not editing the registry key.)
To confirm that the device is managed by Intune only or managed by Configuration Manager only, with Sense enabled, check the following registry key values:
ManagedDefenderProductType(located atComputer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows DefenderorHKLM\SOFTWARE\Microsoft\Windows Defender)EnrollmentStatus(located atComputer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SenseCMorHKLM\SOFTWARE\Microsoft\SenseCM)
The following table summarizes what the registry key values mean:
ManagedDefenderProductTypevalueEnrollmentStatusvalueWhat the value means 6(any value) The device is managed with Intune only.
(Meets a requirement for exclusions to be tamper protected.)74The device is managed with Configuration Manager.
(Meets a requirement for exclusions to be tamper protected.)73The device is co-managed with Configuration Manager and Intune.
(This is not supported for exclusions to be tamper protected.)A value other than 6or7(any value) The device isn't managed by Intune only or Configuration Manager only.
(Exclusions aren't tamper protected.)To confirm that tamper protection is deployed and that exclusions are tamper protected, check the
TPExclusionsregistry key (located atComputer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\FeaturesorHKLM\SOFTWARE\Microsoft\Windows Defender\Features).TPExclusionsWhat the value means 1The required conditions are met, and the new functionality to protect exclusions is enabled on the device.
(Exclusions are tamper protected.)0Tamper protection isn't currently protecting exclusions on the device.
(If all the requirements are met and this state seems incorrect, contact support.)
Caution
Do not change the value of the registry keys. Use the preceding procedure for information only. Changing keys has no effect on whether tamper protection applies to exclusions.
See also
- Frequently asked questions (FAQs) on tamper protection
- Defender for Endpoint on non-Windows devices
- Troubleshoot problems with tamper protection
- Manage Microsoft Defender for Endpoint on devices with Microsoft Intune
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.