Customize data sensitivity settings
This article describes how to customize data sensitivity settings in Microsoft Defender for Cloud.
Data sensitivity settings are used to identify and focus on managing the critical sensitive data in your organization.
- The sensitive info types and sensitivity labels that come from Microsoft Purview compliance portal and which you can select in Defender for Cloud. By default Defender for Cloud uses the built-in sensitive information types provided by Microsoft Purview compliance portal. Some of the information types and labels are enabled by default, Of these built-in sensitive information types, there's a subset supported by sensitive data discovery. You can view a reference list of this subset, which also lists which information types are supported by default. The sensitivity settings page allows you to modify the default settings.
- You can optionally allow the import of custom sensitive info types and allow the import of sensitivity labels that you defined in Microsoft Purview.
- If you import labels, you can set sensitivity thresholds that determine the minimum threshold sensitivity level for a label to be marked as sensitive in Defender for Cloud.
This configuration helps you focus on your critical sensitive resources and improve the accuracy of the sensitivity insights.
Before you start
- Make sure that you review the prerequisites and requirements for customizing data sensitivity settings.
- In Defender for Cloud, enable sensitive data discovery capabilities in the Defender CSPM and/or Defender for Storage plans.
Changes in sensitivity settings take effect the next time that resources are discovered.
Import custom sensitivity info types/labels
To import custom sensitivity info types and labels, you need to have Enterprise Mobility and Security E5/A5/G5 licensing. Learn more about sensitivity labeling licensing.
Defender for Cloud uses built-in sensitive info types. You can optionally import your own custom sensitive info types and labels from Microsoft Purview compliance portal to align with your organization's needs.
Import as follows (Import only once):
- Log into Microsoft Purview compliance portal.
- Navigate to Information Protection > Labels.
- In the consent notice message, select Turn on and then select Yes to share your custom info types and sensitivity labels with Defender for Cloud.
Note
- Imported labels appear in Defender for Cloud in the order rank that's set in Microsoft Purview.
- The two sensitivity labels that are set to highest priority in Microsoft Purview are turned on by default in Defender for Cloud.
Customize sensitive data categories/types
To customize data sensitivity settings that appear in Defender for Cloud, review the prerequisites, and then do the following.
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Environment settings.
Select Data sensitivity.
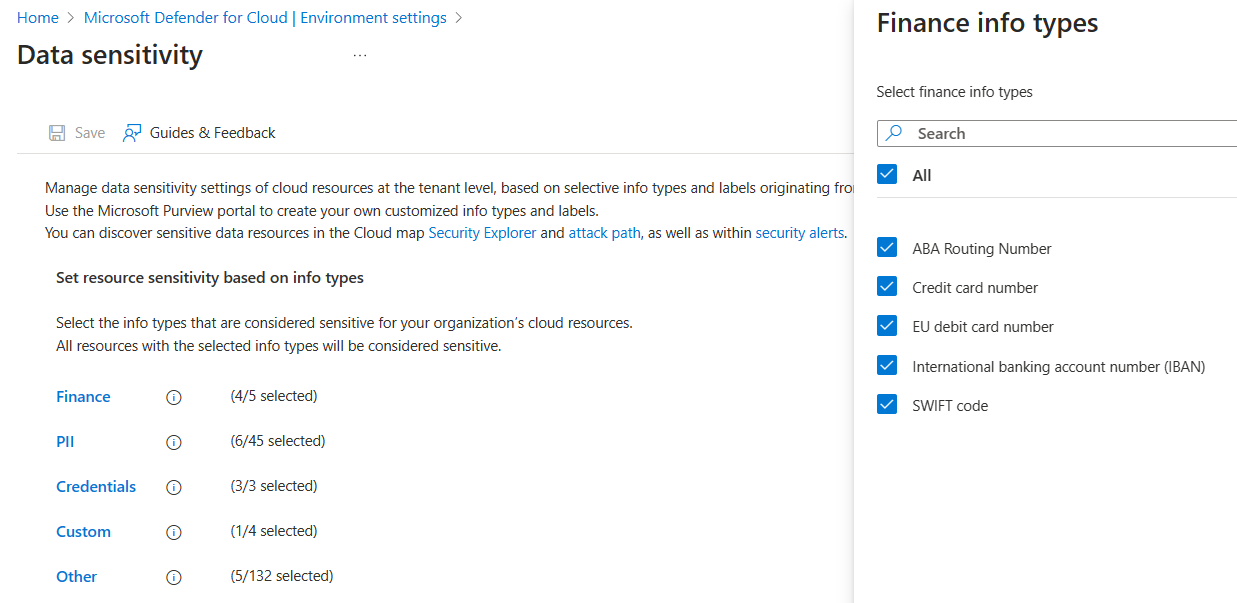
Select the info type category that you want to customize:
- The Finance, PII, and Credentials categories contain the default info type data that are typically sought out by attackers.
- The Custom category contains custom info types from your Microsoft Purview compliance portal configuration.
- The Other category contains all of the rest of the built-in available info types.
Select the info types that you want to be marked as sensitive.
Select Apply and Save.
Set the threshold for sensitive data labels
You can set a threshold to determine the minimum sensitivity level for a label to be marked as sensitive in Defender for Cloud.
If you're using Microsoft Purview sensitivity labels, make sure that:
- the label scope is set to "Items"; under which you should configure auto labeling for files and emails
- labels must be published with a label policy that is in effect.
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Environment settings.
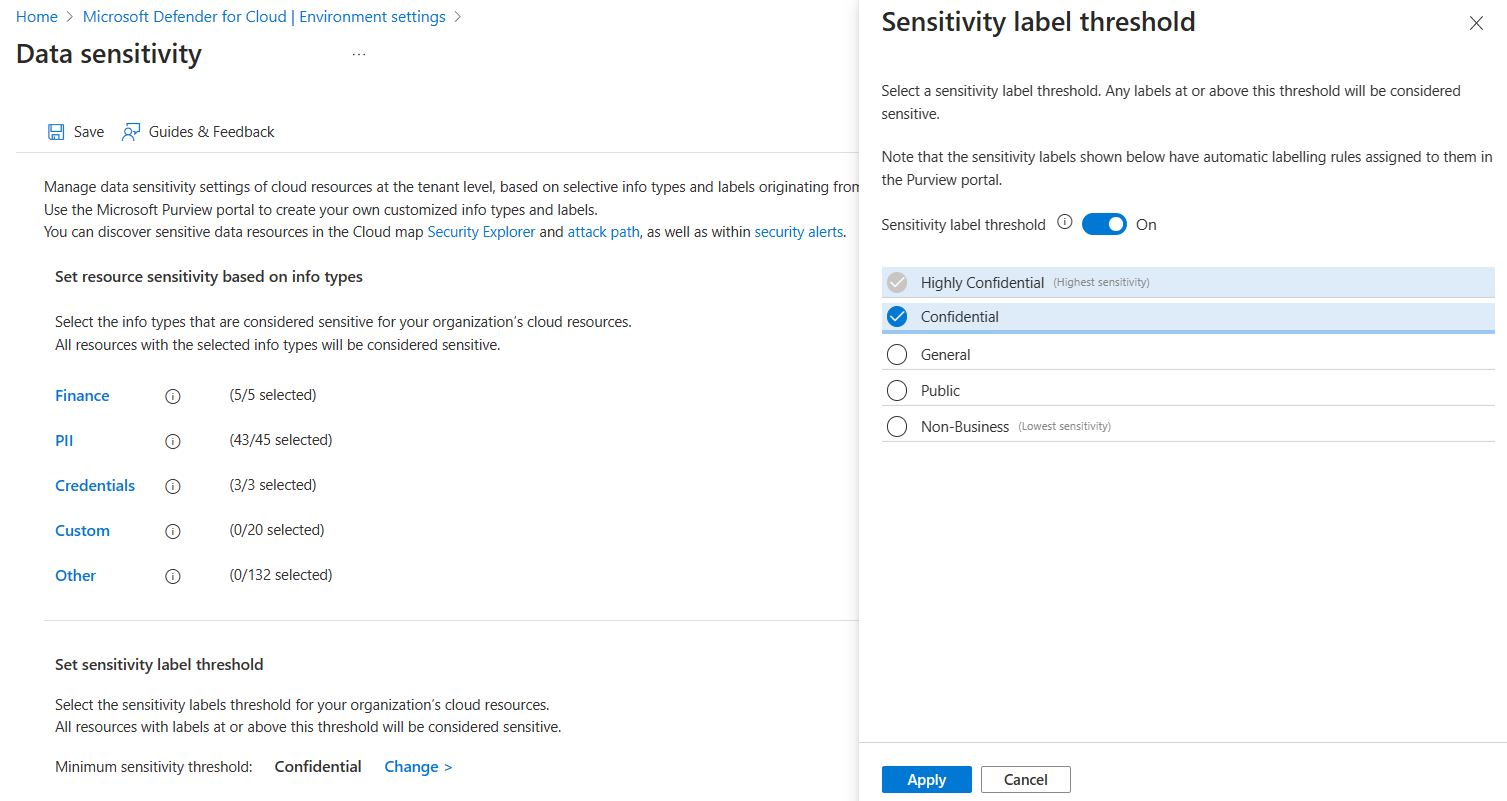
Select Data sensitivity. The current minimum sensitivity threshold is shown.
Select Change to see the list of sensitivity labels and select the lowest sensitivity label that you want marked as sensitive.
Select Apply and Save.
Note
- When you turn on the threshold, you select a label with the lowest setting that should be considered sensitive in your organization.
- Any resources with this minimum label or higher are presumed to contain sensitive data.
- For example, if you select Confidential as minimum, then Highly Confidential is also considered sensitive. General, Public, and Non-Business aren't.
- You can’t select a sub label in the threshold. However, you can see the sublabel as the affected label on resources in attack path/Cloud Security Explorer, if the parent label is part of the threshold (part of the sensitive labels selected).
- The same settings will apply to any supported resource (object storage and databases).
Next steps
Review risks to sensitive data