RDP Shortpath for Azure Virtual Desktop
RDP Shortpath establishes a UDP-based transport between a local device Windows App or the Remote Desktop app on supported platforms and session host in Azure Virtual Desktop. By default, the Remote Desktop Protocol (RDP) begins a TCP-based reverse connect transport, then tries to establish a remote session using UDP. If the UDP connection succeeds the TCP connection drops, otherwise the TCP connection is used as a fallback connection mechanism.
UDP-based transport offers better connection reliability and more consistent latency. TCP-based reverse connect transport provides the best compatibility with various networking configurations and has a high success rate for establishing RDP connections.
RDP Shortpath can be used in two ways:
Managed networks, where direct connectivity is established between the client and the session host when using a private connection, such as Azure ExpressRoute or a site-to-site virtual private network (VPN). A connection using a managed network is established in one of the following ways:
A direct UDP connection between the client device and session host, where you need to enable the RDP Shortpath listener and allow an inbound port on each session host to accept connections.
A direct UDP connection between the client device and session host, using the Simple Traversal Underneath NAT (STUN) protocol between a client and session host. Inbound ports on the session host aren't required to be allowed.
Public networks, where direct connectivity is established between the client and the session host when using a public connection. There are two connection types when using a public connection, which are listed here in order of preference:
A direct UDP connection using the Simple Traversal Underneath NAT (STUN) protocol between a client and session host.
An relayed UDP connection using the Traversal Using Relay NAT (TURN) protocol between a client and session host.
The transport used for RDP Shortpath is based on the Universal Rate Control Protocol (URCP). URCP enhances UDP with active monitoring of the network conditions and provides fair and full link utilization. URCP operates at low delay and loss levels as needed.
Important
- RDP Shortpath for public networks via STUN for Azure Virtual Desktop is available in the Azure public cloud and Azure Government cloud.
- RDP Shortpath for public networks via TURN for Azure Virtual Desktop is only available in the Azure public cloud.
Key benefits
Using RDP Shortpath has the following key benefits:
Using URCP to enhance UDP achieves the best performance by dynamically learning network parameters and providing the protocol with a rate control mechanism.
Higher throughput.
When using STUN, the removal of extra relay points reduces round-trip time improves connection reliability and the user experience with latency-sensitive applications and input methods.
In addition, for managed networks:
RDP Shortpath brings support for configuring Quality of Service (QoS) priority for RDP connections through Differentiated Services Code Point (DSCP) marks.
The RDP Shortpath transport allows limiting outbound network traffic by specifying a throttle rate for each session.
How RDP Shortpath works
To learn how RDP Shortpath works for managed networks and public networks, select each of the following tabs.
You can achieve the direct line of sight connectivity required to use RDP Shortpath with managed networks using the following methods.
Site-to-site or Point-to-site VPN (IPsec), such as Azure VPN Gateway
Having direct line of sight connectivity means that the client can connect directly to the session host without being blocked by firewalls.
Note
If you're using other VPN types to connect to Azure, we recommend using a UDP-based VPN. While most TCP-based VPN solutions support nested UDP, they add inherited overhead of TCP congestion control, which slows down RDP performance.
To use RDP Shortpath for managed networks, you must enable a UDP listener on your session hosts. By default, port 3390 is used, although you can use a different port.
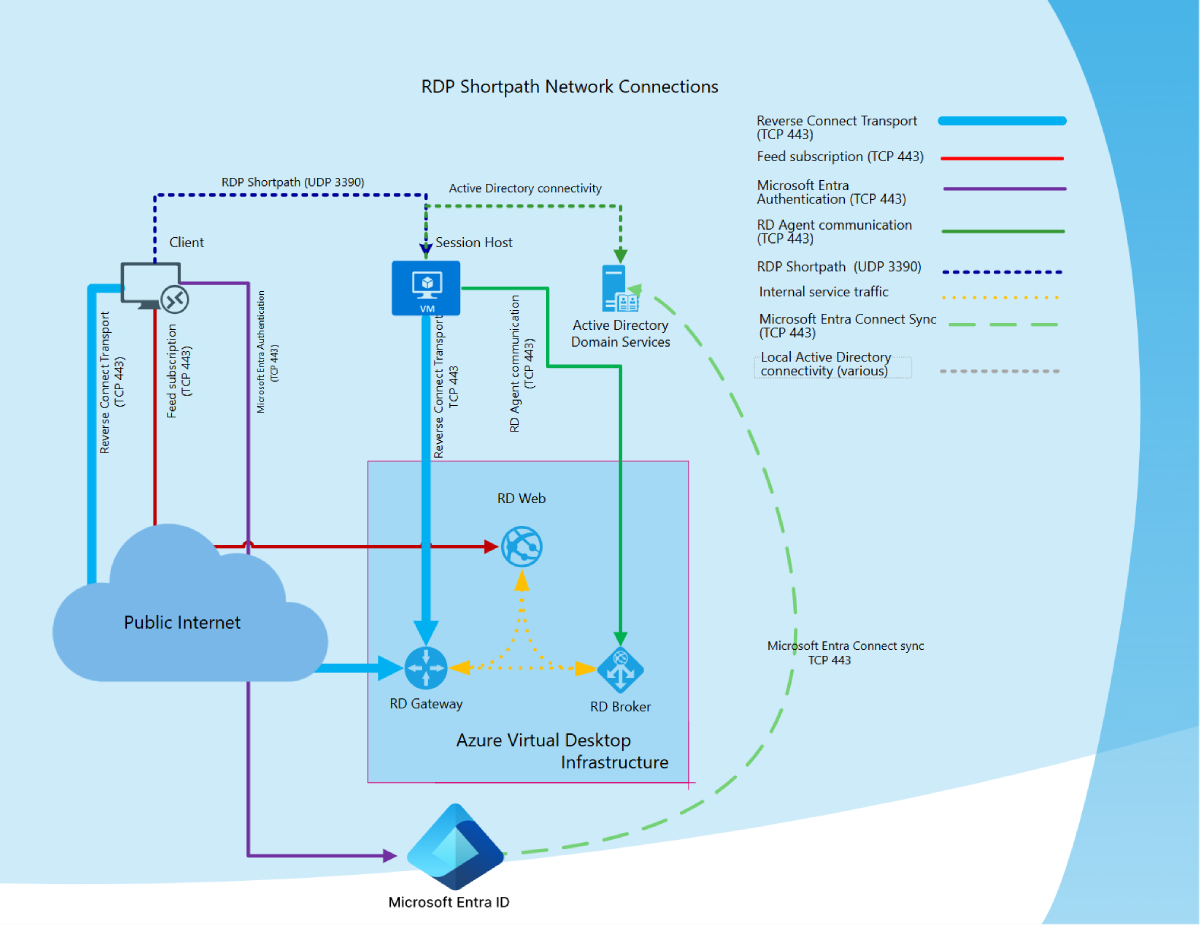
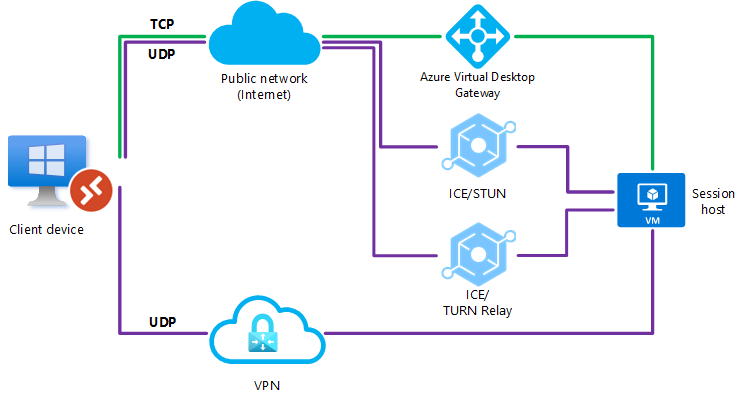
The following diagram gives a high-level overview of the network connections when using RDP Shortpath for managed networks and session hosts joined to an Active Directory domain.
Connection sequence
All connections begin by establishing a TCP-based reverse connect transport over the Azure Virtual Desktop Gateway. Then, the client and session host establish the initial RDP transport, and start exchanging their capabilities. These capabilities are negotiated using the following process:
The session host sends the list of its IPv4 and IPv6 addresses to the client.
The client starts the background thread to establish a parallel UDP-based transport directly to one of the session host's IP addresses.
While the client is probing the provided IP addresses, it continues to establish the initial connection over the reverse connect transport to ensure there's no delay in the user connection.
If the client has a direct connection to the session host, the client establishes a secure connection using TLS over reliable UDP.
After establishing the RDP Shortpath transport, all Dynamic Virtual Channels (DVCs), including remote graphics, input, and device redirection, are moved to the new transport. However, if a firewall or network topology prevents the client from establishing direct UDP connectivity, RDP continues with a reverse connect transport.
If your users have both RDP Shortpath for managed network and public networks available to them, then the first-found algorithm will be used. The user will use whichever connection gets established first for that session.
Connection security
RDP Shortpath extends RDP multi-transport capabilities. It doesn't replace the reverse connect transport but complements it. Initial session brokering is managed through the Azure Virtual Desktop service and the reverse connect transport. All connection attempts are ignored unless they match the reverse connect session first. RDP Shortpath is established after authentication, and if successfully established, the reverse connect transport is dropped and all traffic flows over the RDP Shortpath.
RDP Shortpath uses a secure connection using TLS over reliable UDP between the client and the session host using the session host's certificates. By default, the certificate used for RDP encryption is self-generated by the operating system during the deployment. You can also deploy centrally managed certificates issued by an enterprise certification authority. For more information about certificate configurations, see Remote Desktop listener certificate configurations.
Note
The security offered by RDP Shortpath is the same as that offered by TCP reverse connect transport.
Example scenarios
Here are some example scenarios to show how connections are evaluated to decide whether RDP Shortpath is used across different network topologies.
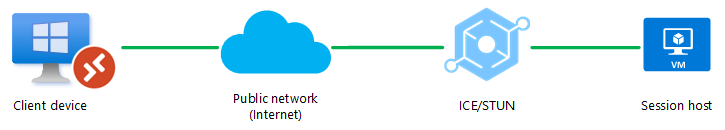
Scenario 1
A UDP connection can only be established between the client device and the session host over a public network (internet). A direct connection, such as a VPN, isn't available. UDP is allowed through firewall or NAT device.
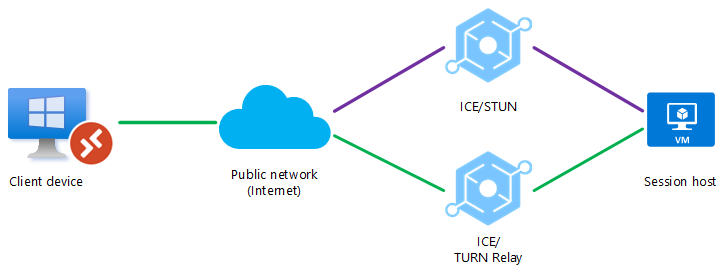
Scenario 2
A firewall or NAT device is blocking a direct UDP connection, but a relayed UDP connection can be relayed using TURN between the client device and the session host over a public network (internet). Another direct connection, such as a VPN, isn't available.
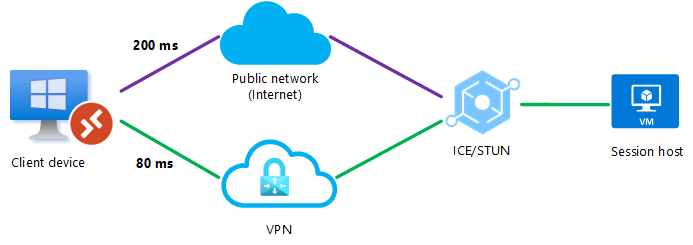
Scenario 3
A UDP connection can be established between the client device and the session host over a public network or over a direct VPN connection, but RDP Shortpath for managed networks isn't enabled. When the client initiates the connection, the ICE/STUN protocol can see multiple routes and will evaluate each route and choose the one with the lowest latency.
In this example, a UDP connection using RDP Shortpath for public networks over the direct VPN connection will be made as it has the lowest latency, as shown by the green line.
Scenario 4
Both RDP Shortpath for public networks and managed networks are enabled. A UDP connection can be established between the client device and the session host over a public network or over a direct VPN connection. When the client initiates the connection, there are simultaneous attempts to connect using RDP Shortpath for managed networks through port 3390 (by default) and RDP Shortpath for public networks through the ICE/STUN protocol. The first-found algorithm will be used and the user will use whichever connection gets established first for that session.
Since going over a public network has more steps, for example a NAT device, a load balancer, or a STUN server, it's likely that the first-found algorithm will select the connection using RDP Shortpath for managed networks and be established first.
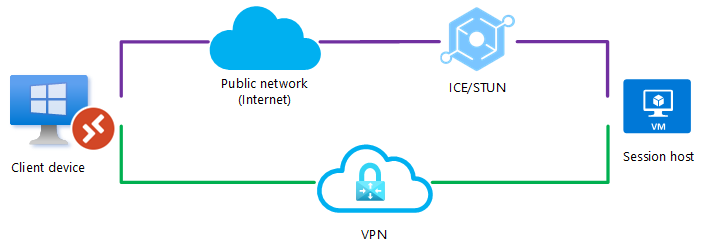
Scenario 5
A UDP connection can be established between the client device and the session host over a public network or over a direct VPN connection, but RDP Shortpath for managed networks isn't enabled. To prevent ICE/STUN from using a particular route, an admin can block one of the routes for UDP traffic. Blocking a route would ensure the remaining path is always used.
In this example, UDP is blocked on the direct VPN connection and the ICE/STUN protocol establishes a connection over the public network.
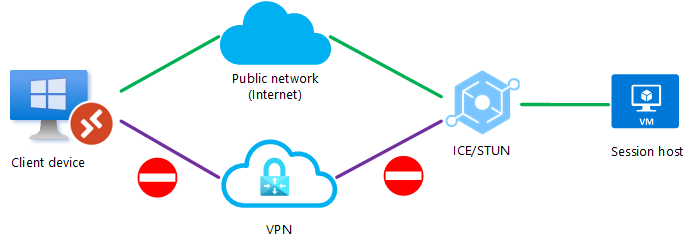
Scenario 6
Both RDP Shortpath for public networks and managed networks are configured, however a UDP connection couldn't be established using direct VPN connection. A firewall or NAT device is also blocking a direct UDP connection using the public network (internet), but a relayed UDP connection can be relayed using TURN between the client device and the session host over a public network (internet).
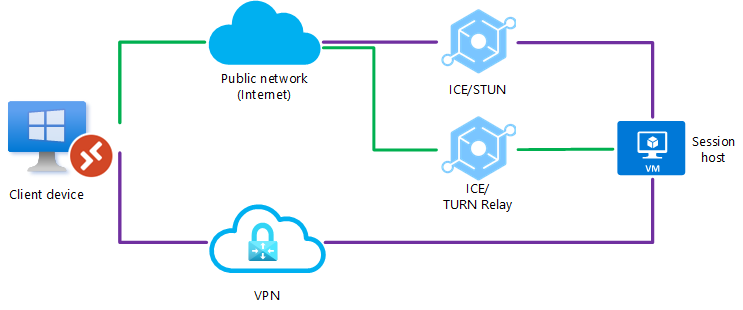
Scenario 7
Both RDP Shortpath for public networks and managed networks are configured, however a UDP connection couldn't be established. In this instance, RDP Shortpath will fail and the connection will fall back to TCP-based reverse connect transport.
Next steps
- Learn how to Configure RDP Shortpath.
- Learn more about Azure Virtual Desktop network connectivity at Understanding Azure Virtual Desktop network connectivity.
- Understand Azure egress network charges.
- To understand how to estimate the bandwidth used by RDP, see RDP bandwidth requirements.