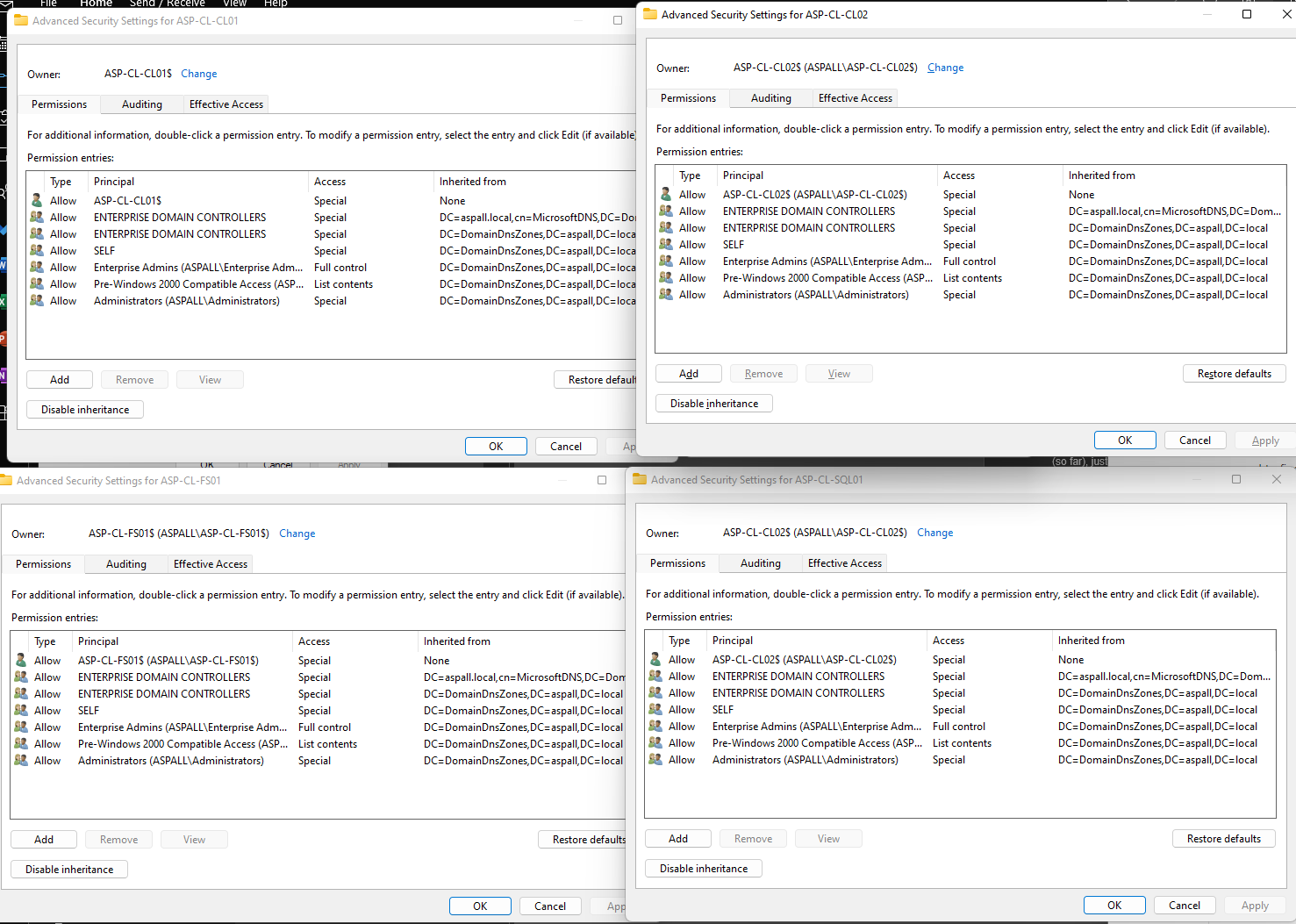
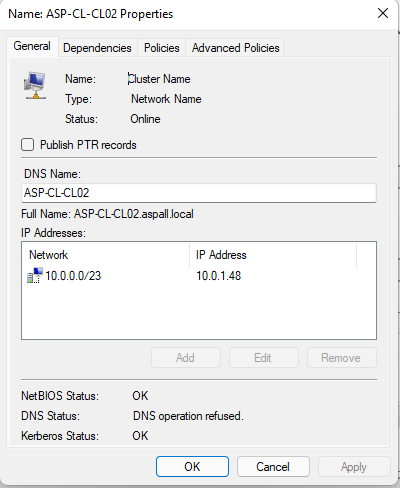
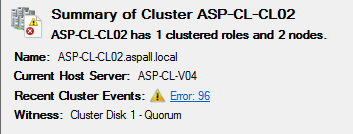
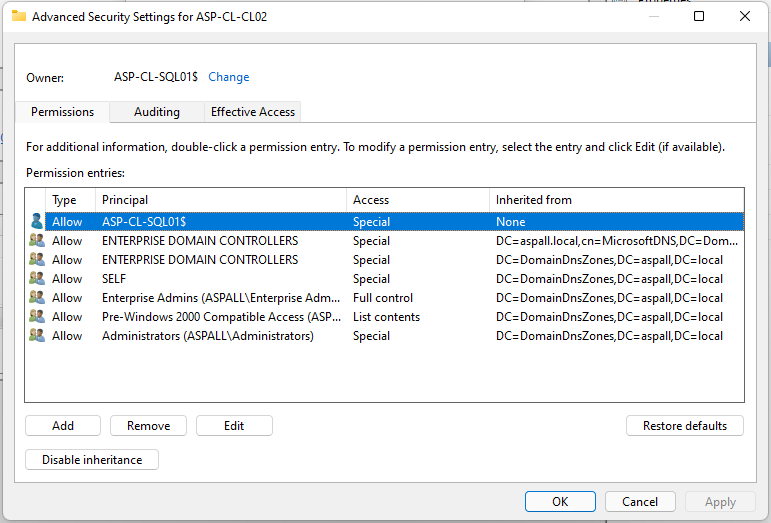
The silence from Microsoft on this is deafening. To think, an enterprise level feature, is basically broken, and has been broken for a while now. I just closed a ticket with Microsoft support regarding this issue and they were of no help at all. The tech did indicate that this is a known issue with Microsoft but could not give me an ETA on a fix/patch for this issue. Also, he refused to produce the 'internal' documentation from Microsoft regarding this 'Known Issue'. The real kicker here is that this issue can be resolved by offlining the cluster, running the Update-ClusterNetworkNameResource (which works sporadically) command via PowerShell, execute a repair on the cluster, and/or sometimes it self-heals. Because of this the Microsoft tech always has an out, as they are technically break/fix and if an issue isn't broken they refuse to help, and tell you to submit a root cause analysis ticket to Microsoft Premier support. My argument is that these issues are SYMPTOMS of the real issue. If Microsoft knows the reason/cause for this issue they need to provide information on what causes this issue, HOW TO FIX IT, and/or a patch or ETA on when a patch will be published to resolve this issue.