Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
During local development, applications need to authenticate to Azure to access various Azure services. You can authenticate locally by using one of the following approaches:
- Use a developer account with one of the developer tools supported by the Azure Identity library.
- Use a service principal. For more information, see Authenticate Java apps to Azure services during local development by using service principals.
This article explains how to authenticate by using a developer account with tools supported by the Azure Identity library. In this article, you learn:
- How to use Microsoft Entra groups to efficiently manage permissions for multiple developer accounts.
- How to assign roles to developer accounts to scope permissions.
- How to sign in to supported local development tools.
- How to authenticate by using a developer account from your app code.
Supported developer tools for authentication
During local development, an app can authenticate to Azure by using your Azure credentials. For this authentication to work, you must be signed in to Azure from a developer tool such as one of the following:
- Azure CLI
- Azure Developer CLI
- Azure PowerShell
- Visual Studio Code
- IntelliJ IDEA
The Azure Identity library can detect that the developer is signed in from one of these tools. The library can then obtain the Microsoft Entra access token via the tool to authenticate the app to Azure as the signed-in user.
This approach takes advantage of the developer's existing Azure accounts to streamline the authentication process. However, a developer's account likely has more permissions than the app requires, therefore exceeding the permissions the app runs with in production. As an alternative, you can create application service principals to use during local development, which can be scoped to have only the access needed by the app.
Create a Microsoft Entra group for local development
Create a Microsoft Entra group to encapsulate the roles (permissions) the app needs in local development rather than assigning the roles to individual service principal objects. This approach offers the following advantages:
- Every developer has the same roles assigned at the group level.
- If a new role is needed for the app, it only needs to be added to the group for the app.
- If a new developer joins the team, a new application service principal is created for the developer and added to the group, ensuring the developer has the right permissions to work on the app.
Navigate to the Microsoft Entra ID overview page in the Azure portal.
Select All groups from the left-hand menu.
On the Groups page, select New group.
On the New group page, fill out the following form fields:
- Group type: Select Security.
- Group name: Enter a name for the group that includes a reference to the app or environment name.
- Group description: Enter a description that explains the purpose of the group.
Select the No members selected link under Members to add members to the group.
In the flyout panel that opens, search for the service principal you created earlier and select it from the filtered results. Choose the Select button at the bottom of the panel to confirm your selection.
Select Create at the bottom of the New group page to create the group and return to the All groups page. If you don't see the new group listed, wait a moment and refresh the page.
Assign roles to the group
Next, determine what roles (permissions) your app needs on what resources and assign those roles to the Microsoft Entra group you created. Groups can be assigned a role at the resource, resource group, or subscription scope. This example shows how to assign roles at the resource group scope, since most apps group all their Azure resources into a single resource group.
In the Azure portal, navigate to the Overview page of the resource group that contains your app.
Select Access control (IAM) from the left navigation.
On the Access control (IAM) page, select + Add and then choose Add role assignment from the drop-down menu. The Add role assignment page provides several tabs to configure and assign roles.
On the Role tab, use the search box to locate the role you want to assign. Select the role, and then choose Next.
On the Members tab:
- For the Assign access to value, select User, group, or service principal .
- For the Members value, choose + Select members to open the Select members flyout panel.
- Search for the Microsoft Entra group you created earlier and select it from the filtered results. Choose Select to select the group and close the flyout panel.
- Select Review + assign at the bottom of the Members tab.
On the Review + assign tab, select Review + assign at the bottom of the page.
Sign in to Azure by using developer tooling
Next, sign in to Azure by using one of the developer tools that you can use to perform authentication in your development environment. The account you authenticate should also exist in the Microsoft Entra group you created and configured earlier.
Developers using Visual Studio Code can authenticate with their developer account directly through the editor via the broker. Apps that use DefaultAzureCredential or VisualStudioCodeCredential can then use this account to authenticate app requests through a seamless single-sign-on experience.
In Visual Studio Code, go to the Extensions panel and install the Azure Resources extension. This extension lets you view and manage Azure resources directly from Visual Studio Code. It also uses the built-in Visual Studio Code Microsoft authentication provider to authenticate with Azure.
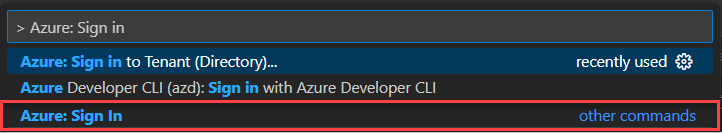
Open the Command Palette in Visual Studio Code, then search for and select Azure: Sign in.
Tip
Open the Command Palette using
Ctrl+Shift+Pon Windows/Linux orCmd+Shift+Pon macOS.
Authenticate to Azure services from your app
The Azure Identity library provides implementations of TokenCredential that support various scenarios and Microsoft Entra authentication flows. The following steps show you how to use DefaultAzureCredential or a specific development tool credential when working with user accounts locally.
Implement the code
Add the
azure-identitydependency to yourpom.xmlfile:<dependency> <groupId>com.azure</groupId> <artifactId>azure-identity</artifactId> </dependency>Choose one of the credential implementations based on your scenario.
- Use a credential specific to your development tool: this option is best for single person or single tool scenarios.
- Use a credential available for use in any development tool: this option is best for open-source projects and diverse tool teams.
Use a credential specific to your development tool
Pass a TokenCredential instance corresponding to a specific development tool to the Azure service client constructor, such as AzureCliCredential.
import com.azure.identity.AzureCliCredential;
import com.azure.identity.AzureCliCredentialBuilder;
import com.azure.security.keyvault.secrets.SecretClient;
import com.azure.security.keyvault.secrets.SecretClientBuilder;
AzureCliCredential credential = new AzureCliCredentialBuilder().build();
SecretClient client = new SecretClientBuilder()
.vaultUrl("https://<your-key-vault-name>.vault.azure.net")
.credential(credential)
.buildClient();
Each tool credential follows the same pattern. Replace the credential type and its corresponding builder as needed:
AzureCliCredential/AzureCliCredentialBuilderAzureDeveloperCliCredential/AzureDeveloperCliCredentialBuilderAzurePowerShellCredential/AzurePowerShellCredentialBuilderIntelliJCredential/IntelliJCredentialBuilderVisualStudioCodeCredential/VisualStudioCodeCredentialBuilder
Use a credential available for use in any development tool
Use a DefaultAzureCredential instance optimized for all local development tools. This example requires the environment variable AZURE_TOKEN_CREDENTIALS set to dev. For more information, see Exclude a credential type category.
import com.azure.identity.DefaultAzureCredential;
import com.azure.identity.DefaultAzureCredentialBuilder;
import com.azure.security.keyvault.secrets.SecretClient;
import com.azure.security.keyvault.secrets.SecretClientBuilder;
DefaultAzureCredential credential = new DefaultAzureCredentialBuilder()
.requireEnvVars(AzureIdentityEnvVars.AZURE_TOKEN_CREDENTIALS)
.build();
SecretClient client = new SecretClientBuilder()
.vaultUrl("https://<your-key-vault-name>.vault.azure.net")
.credential(credential)
.buildClient();
Next steps
This article covered authentication during development by using credentials available on your computer. This form of authentication is one of multiple ways you can authenticate in the Azure SDK for Java. The following articles describe other ways:
- Authenticate Java apps to Azure services during local development by using service principals
- Authenticate Azure-hosted Java apps to Azure resources by using a system-assigned managed identity
- Authenticate Azure-hosted Java apps to Azure resources by using a user-assigned managed identity
If you run into issues related to development environment authentication, see Troubleshoot development environment authentication.
After you master authentication, see Configure logging in the Azure SDK for Java for information on the logging functionality provided by the SDK.

