Configure admin access
Microsoft Defender for Cloud Apps supports role-based access control. This article provides instructions for setting access to Defender for Cloud Apps for your admins. For more information about assigning administrator roles, see the articles for Microsoft Entra ID and Microsoft 365.
Microsoft 365 and Microsoft Entra roles with access to Defender for Cloud Apps
Note
- Microsoft 365 and Microsoft Entra roles aren't listed in the Defender for Cloud Apps Manage admin access page. To assign roles in Microsoft 365 or Microsoft Entra ID, go to the relevant RBAC settings for that service.
- Defender for Cloud Apps uses Microsoft Entra ID to determine the user's directory level inactivity timeout setting. If a user is configured in Microsoft Entra ID to never sign out when inactive, the same setting will apply in Defender for Cloud Apps as well.
By default, the following Microsoft 365 and Microsoft Entra ID admin roles have access to Defender for Cloud Apps:
| Role name | Description |
|---|---|
| Global administrator and Security administrator | Administrators with Full access have full permissions in Defender for Cloud Apps. They can add admins, add policies and settings, upload logs and perform governance actions, access and manage SIEM agents. |
| Cloud App Security administrator | Allows full access and permissions in Defender for Cloud Apps. This role grants full permissions to Defender for Cloud Apps, like the Microsoft Entra ID Global administrator role. However, this role is scoped to Defender for Cloud Apps and won't grant full permissions across other Microsoft security products. |
| Compliance administrator | Has read-only permissions and can manage alerts. Can't access Security recommendations for cloud platforms. Can create and modify file policies, allow file governance actions, and view all the built-in reports under Data Management. |
| Compliance data administrator | Has read-only permissions, can create and modify file policies, allow file governance actions, and view all discovery reports. Can't access Security recommendations for cloud platforms. |
| Security operator | Has read-only permissions and can manage alerts. These admins are restricted from doing the following actions:
|
| Security reader | Has read-only permissions and can create API access tokens. These admins are restricted from doing the following actions:
|
| Global reader | Has full read-only access to all aspects of Defender for Cloud Apps. Can't change any settings or take any actions. |
Important
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
Note
App governance features are controlled by Microsoft Entra ID roles only. For more information, see App governance roles.
Roles and permissions
| Permissions | Global Admin | Security Admin | Compliance Admin | Compliance Data Admin | Security Operator | Security Reader | Global Reader | PBI Admin | Cloud App Security admin |
|---|---|---|---|---|---|---|---|---|---|
| Read alerts | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Manage alerts | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Read OAuth applications | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Perform OAuth application actions | ✔ | ✔ | ✔ | ✔ | |||||
| Access discovered apps, the cloud app catalog, and other cloud discovery data | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Configure API connectors | ✔ | ✔ | ✔ | ✔ | |||||
| Perform cloud discovery actions | ✔ | ✔ | ✔ | ||||||
| Access files data and file policies | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Perform file actions | ✔ | ✔ | ✔ | ✔ | |||||
| Access governance log | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Perform governance log actions | ✔ | ✔ | ✔ | ✔ | |||||
| Access scoped discovery governance log | ✔ | ✔ | ✔ | ||||||
| Read policies | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Perform all policy actions | ✔ | ✔ | ✔ | ✔ | |||||
| Perform file policy actions | ✔ | ✔ | ✔ | ✔ | ✔ | ||||
| Perform OAuth policy actions | ✔ | ✔ | ✔ | ✔ | |||||
| View manage admin access | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Manage admins and activity privacy | ✔ | ✔ | ✔ |
Built-in admin roles in Defender for Cloud Apps
The following specific admin roles can be configured in the Microsoft Defender portal, in the Permissions > Cloud Apps > Roles area:
| Role name | Description |
|---|---|
| Global administrator | Has Full access similar to the Microsoft Entra Global Administrator role but only to Defender for Cloud Apps. |
| Compliance administrator | Grants the same permissions as the Microsoft Entra Compliance administrator role but only to Defender for Cloud Apps. |
| Security reader | Grants the same permissions as the Microsoft Entra Security reader role but only to Defender for Cloud Apps. |
| Security operator | Grants the same permissions as the Microsoft Entra Security operator role but only to Defender for Cloud Apps. |
| App/instance admin | Has full or read-only permissions to all of the data in Defender for Cloud Apps that deals exclusively with the specific app or instance of an app selected. For example, you give a user admin permission to your Box European instance. The admin will see only data that relates to the Box European instance, whether it's files, activities, policies, or alerts:
|
| User group admin | Has full or read-only permissions to all of the data in Defender for Cloud Apps that deals exclusively with the specific groups assigned to them. For example, if you assign a user admin permissions to the group "Germany - all users", the admin can view and edit information in Defender for Cloud Apps only for that user group. The User group admin has the following access:
Notes:
|
| Cloud Discovery global admin | Has permission to view and edit all cloud discovery settings and data. The Global Discovery admin has the following access:
|
| Cloud Discovery report admin |
|
Important
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
The built-in Defender for Cloud Apps admin roles only provide access permissions to Defender for Cloud Apps.
Override admin permissions
If you want to override an administrator's permission from Microsoft Entra ID or Microsoft 365, you can do so by manually adding the user to Defender for Cloud Apps and assigning the user permissions. For example, if you want to assign Stephanie, who is a Security reader in Microsoft Entra ID to have Full access in Defender for Cloud Apps, you can add her manually to Defender for Cloud Apps and assign her Full access to override her role and allow her the necessary permissions in Defender for Cloud Apps. Note that it isn't possible to override Microsoft Entra roles that grant Full access (Global administrator, Security administrator, and Cloud App Security administrator).
Important
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
Add additional admins
You can add additional admins to Defender for Cloud Apps without adding users to Microsoft Entra administrative roles. To add additional admins, perform the following steps:
Important
- Access to the Manage admin access page is available to members of the Global Administrators, Security Administrators, Compliance Administrators, Compliance Data Administrators, Security Operators, Security Readers, and Global Readers groups.
- To edit the Manage admin access page and grant other users access to Defender for Cloud Apps, you must have at least a Security Administrator role.
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
In the Microsoft Defender Portal, in the left-hand menu, select Permissions.
Under Cloud Apps, choose Roles.
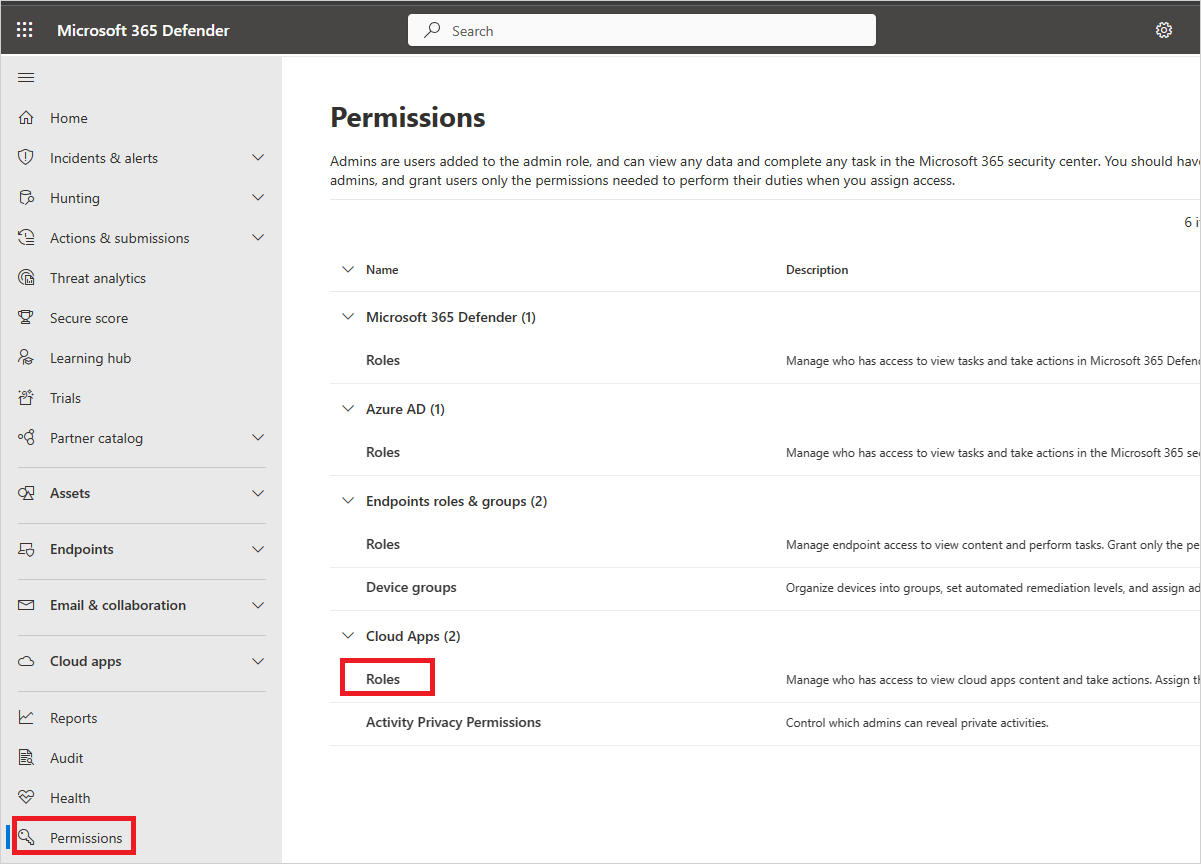
Select +Add user to add the admins who should have access to Defender for Cloud Apps. Provide an email address of a user from inside your organization.
Note
If you want to add external Managed Security Service Providers (MSSPs) as administrators for Defender for Cloud Apps, make sure you first invite them as a guest to your organization.
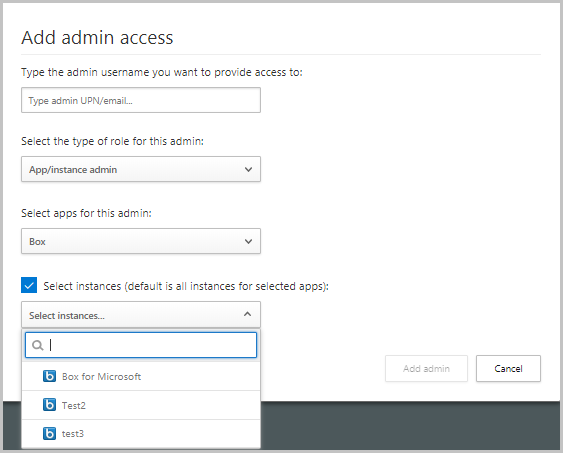
Next, select the drop-down to set what type of role the admin has. If you select App/Instance admin, select the app and instance for the admin to have permissions for.
Note
Any admin, whose access is limited, that attempts to access a restricted page or perform a restricted action will receive an error that they don't have permission to access the page or perform the action.
Select Add admin.
Invite external admins
Defender for Cloud Apps enables you to invite external admins (MSSPs) as administrators of your organization's (MSSP customer) Defender for Cloud Apps service. To add MSSPs, make sure Defender for Cloud Apps is enabled on the MSSPs tenant, and then add them as Microsoft Entra B2B collaboration users in the MSSPs customers Azure portal. Once added, MSSPs can be configured as administrators and assigned any of the roles available in Defender for Cloud Apps.
To add MSSPs to the MSSP customer Defender for Cloud Apps service
- Add MSSPs as a guest in the MSSP customer directory using the steps under Add guest users to the directory.
- Add MSSPs and assign an administrator role in the MSSP customer Defender for Cloud Apps using the steps under Add additional admins. Provide the same external email address used when adding them as guests in the MSSP customer directory.
Access for MSSPs to the MSSP customer Defender for Cloud Apps service
By default, MSSPs access their Defender for Cloud Apps tenant through the following URL: https://security.microsoft.com.
MSSPs however, will need to access the MSSP customer Microsoft Defender Portal using a tenant-specific URL in the following format: https://security.microsoft.com/?tid=<tenant_id>.
MSSPs can use the following steps to obtain the MSSP customer portal tenant ID and then use the ID to access the tenant-specific URL:
As an MSSP, sign in to Microsoft Entra ID with your credentials.
Switch directory to the MSSP customer's tenant.
Select Microsoft Entra ID > Properties. You'll find the MSSP customer tenant ID in the Tenant ID field.
Access the MSSP customer portal by replacing the
customer_tenant_idvalue in the following URL:https://security.microsoft.com/?tid=<tenant_id>.
Admin activity auditing
Defender for Cloud Apps lets you export a log of admin sign-in activities and an audit of views of a specific user or alerts carried out as part of an investigation.
To export a log, perform the following steps:
In the Microsoft Defender Portal, in the left-hand menu, select Permissions.
Under Cloud Apps, choose Roles.
In the Admin roles page, in the top-right corner, select Export admin activities.
Specify the required time range.
Select Export.