PIN reset
This article describes how Microsoft PIN reset service enables your users to recover a forgotten Windows Hello for Business PIN, and how to configure it.
Overview
Windows Hello for Business provides the capability for users to reset forgotten PINs. There are two forms of PIN reset:
- Destructive PIN reset: the user's existing PIN and underlying credentials, including any keys or certificates added to their Windows Hello container, are deleted from the client and a new sign in key and PIN are provisioned. Destructive PIN reset is the default option, and doesn't require configuration
- Non-destructive PIN reset: the user's Windows Hello for Business container and keys are preserved, but the user's PIN that they use to authorize key usage is changed. For nondestructive PIN reset, you must deploy the Microsoft PIN reset service and configure your clients' policy to enable the PIN recovery feature
How nondestructive PIN reset works
Requirements:
- Hybrid or cloud-only Windows Hello for Business deployments
- Windows Enterprise, Education and Pro editions. There's no licensing requirement for this feature
When nondestructive PIN reset is enabled on a client, a 256-bit AES key is generated locally. The key is added to a user's Windows Hello for Business container and keys as the PIN reset protector. This PIN reset protector is encrypted using a public key retrieved from the Microsoft PIN reset service and then stored on the client for later use during PIN reset. After a user initiates a PIN reset, completes authentication and multifactor authentication to Microsoft Entra ID, the encrypted PIN reset protector is sent to the Microsoft PIN reset service, decrypted, and returned to the client. The decrypted PIN reset protector is used to change the PIN used to authorize Windows Hello for Business keys, and it's then cleared from memory.
Using Group Policy, Microsoft Intune or a compatible MDM solution, you can configure Windows devices to securely use the Microsoft PIN reset service, which enables users to reset their forgotten PIN without requiring re-enrollment.
The following table compares destructive and nondestructive PIN reset:
| Category | Destructive PIN reset | Nondestructive PIN reset |
|---|---|---|
| Functionality | The user's existing PIN and underlying credentials, including any keys or certificates added to their Windows Hello container, are deleted from the client and a new sign in key and PIN are provisioned. | You must deploy the Microsoft PIN reset service and client policy to enable the PIN recovery feature. During a nondestructive PIN reset, the user's Windows Hello for Business container and keys are preserved, but the user's PIN that they use to authorize key usage is changed. |
| Microsoft Entra joined | Cert Trust, Key Trust, and cloud Kerberos trust | Cert Trust, Key Trust, and cloud Kerberos trust |
| Microsoft Entra hybrid joined | Cert Trust and cloud Kerberos trust for both settings and above the lock support destructive PIN reset. Key Trust doesn't support this option from above the lock screen. This is due to the sync delay between when a user provisions their Windows Hello for Business credential and being able to use it for sign-in. It does support from the settings page and the users must have a corporate network connectivity to the DC. | Cert Trust, Key Trust, and cloud Kerberos trust for both settings and above the lock support nondestructive PIN reset. No network connection is required for the DC. |
| On Premises | If AD FS is used for on premises deployments, users must have a corporate network connectivity to federation services. | The PIN reset service relies on Microsoft Entra identities, so it's only available for Microsoft Entra hybrid joined and Microsoft Entra joined devices. |
| Additional configuration required | Supported by default and doesn't require configuration | Deploy the Microsoft PIN reset service and client policy to enable the PIN recovery feature. |
| MSA/Enterprise | MSA and Enterprise | Enterprise only. |
Enable the Microsoft PIN Reset Service in your Microsoft Entra tenant
Before you can use nondestructive PIN reset, you must register two applications in your Microsoft Entra tenant:
- Microsoft Pin Reset Service Production
- Microsoft Pin Reset Client Production
To register the applications, follow these steps:
- Go to the Microsoft PIN Reset Service Production website, and sign in as at least an Application Administrator. Review the permissions requested by the Microsoft Pin Reset Service Production application and select Accept to give consent to the application to access your organization
- Go to the Microsoft PIN Reset Client Production website, and sign as at least an Application Administrator. Review the permissions requested by the Microsoft Pin Reset Client Production application, and select Next.
- Review the permissions requested by the Microsoft Pin Reset Service Production application and select Accept to confirm consent to both applications to access your organization.
Note
After acceptance, the redirect page will show a blank page. This is a known behavior.
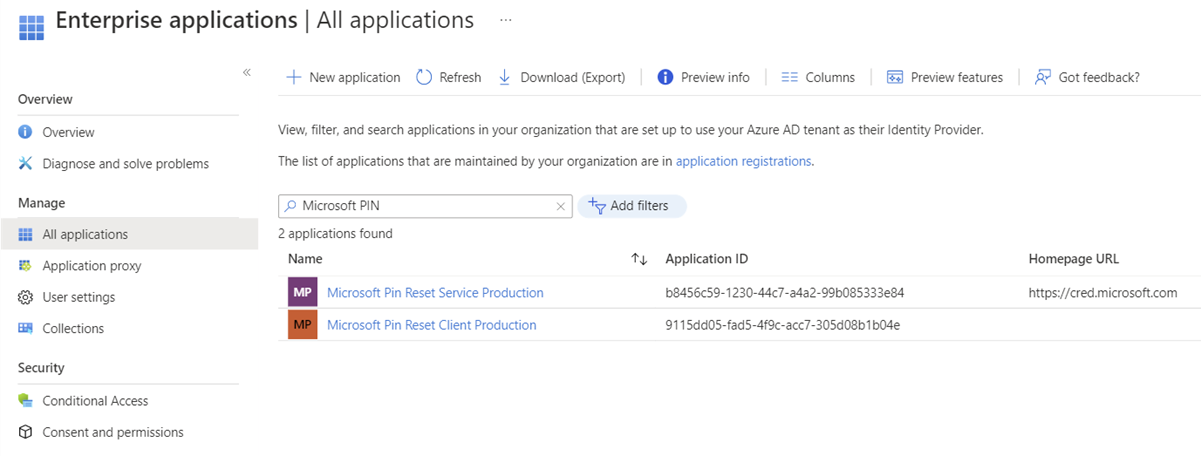
Confirm that the two PIN Reset service principals are registered in your tenant
- Sign in to the Microsoft Entra Manager admin center
- Select Microsoft Entra ID > Applications > Enterprise applications
- Search by application name "Microsoft PIN" and verify that both Microsoft Pin Reset Service Production and Microsoft Pin Reset Client Production are in the list
Enable PIN recovery on the clients
To enable PIN recovery on the clients, you can use:
- Microsoft Intune/MDM
- Group policy
The following instructions provide details how to configure your devices. Select the option that best suits your needs.
To configure devices with Microsoft Intune, create a Settings catalog policy and use the following settings:
| Category | Setting name | Value |
|---|---|---|
| Windows Hello For Business | Enable Pin Recovery | True |
Assign the policy to a group that contains as members the devices or users that you want to configure.
Note
You can also configure PIN recovery from the Endpoint security blade:
- Sign in to the Microsoft Intune admin center
- Select Endpoint security > Account protection > Create Policy
Alternatively, you can configure devices using a custom policy with the PassportForWork CSP.
| OMA-URI | Data type | Value |
|---|---|---|
./Vendor/MSFT/Policy/PassportForWork/TenantId/Policies/EnablePinRecovery |
Boolean | True |
Note
You must replace TenantId with the identifier of your Microsoft Entra tenant. To look up your Tenant ID, see How to find your Microsoft Entra tenant ID or try the following, ensuring to sign-in with your organization's account::
GET https://graph.microsoft.com/v1.0/organization?$select=id
Confirm that PIN Recovery policy is enforced on the devices
The PIN reset configuration can be viewed by running dsregcmd /status from the command line. This state can be found under the output in the user state section as the CanReset line item. If CanReset reports as DestructiveOnly, then only destructive PIN reset is enabled. If CanReset reports DestructiveAndNonDestructive, then nondestructive PIN reset is enabled.
Sample User state Output for Destructive PIN Reset
+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+
NgcSet : YES
NgcKeyId : {FA0DB076-A5D7-4844-82D8-50A2FB42EC7B}
CanReset : DestructiveOnly
WorkplaceJoined : NO
WamDefaultSet : YES
WamDefaultAuthority : organizations
WamDefaultId : https://login.microsoft.com
WamDefaultGUID : { B16898C6-A148-4967-9171-64D755DA8520 } (AzureAd)
+----------------------------------------------------------------------+
Sample User state Output for Non-Destructive PIN Reset
+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+
NgcSet : YES
NgcKeyId : {FA0DB076-A5D7-4844-82D8-50A2FB42EC7B}
CanReset : DestructiveAndNonDestructive
WorkplaceJoined : NO
WamDefaultSet : YES
WamDefaultAuthority : organizations
WamDefaultId : https://login.microsoft.com
WamDefaultGUID : { B16898C6-A148-4967-9171-64D755DA8520 } (AzureAd)
+----------------------------------------------------------------------+
Configure allowed URLs for federated identity providers on Microsoft Entra joined devices
Applies to: Microsoft Entra joined devices
PIN reset on Microsoft Entra joined devices uses a flow called web sign-in to authenticate users in the lock screen. Web sign-in only allows navigation to specific domains. If web sign-in attempts to navigate to a domain that isn't allowed, it displays a page with the error message: We can't open that page right now.
If you have a federated environment and authentication is handled using AD FS or a non-Microsoft identity provider, then you must configure your devices with a policy to allow a list of domains that can be reached during PIN reset flows. When set, it ensures that authentication pages from that identity provider can be used during Microsoft Entra joined PIN reset.
To configure devices with Microsoft Intune, create a Settings catalog policy and use the following settings:
| Category | Setting name | Value |
|---|---|---|
| Authentication | Configure Web Sign In Allowed Urls | Provide a semicolon delimited list of domains needed for authentication during the PIN reset scenario. An example value would be signin.contoso.com;portal.contoso.com |
Assign the policy to a group that contains as members the devices or users that you want to configure.
Alternatively, you can configure devices using a custom policy with the Policy CSP.
| Setting |
|---|
./Vendor/MSFT/Policy/Config/Authentication/ConfigureWebSignInAllowedUrls |
Note
For Azure Government, there is a known issue with PIN reset on Microsoft Entra joined devices failing. When the user attempts to launch PIN reset, the PIN reset UI shows an error page that says, "We can't open that page right now". The ConfigureWebSignInAllowedUrls policy can be used to work around this issue. If you are experiencing this problem and you are using Azure US Government cloud, set login.microsoftonline.us as the value for the ConfigureWebSignInAllowedUrls policy.
User experience
Destructive and nondestructive PIN reset scenarios use the same steps for initiating a PIN reset. If users have forgotten their PINs, but have an alternate sign-in method, they can navigate to Sign-in options in Settings and initiate a PIN reset from the PIN options. If users don't have an alternate way to sign into their devices, PIN reset can also be initiated from the Windows lock screen with the PIN credential provider. Users must authenticate and complete multifactor authentication to reset their PIN. After PIN reset is complete, users can sign in using their new PIN.
Important
For Microsoft Entra hybrid joined devices, users must have corporate network connectivity to domain controllers to complete destructive PIN reset. If AD FS is being used for certificate trust or for on-premises only deployments, users must also have corporate network connectivity to federation services to reset their PIN.
Reset PIN from Settings
- Sign-in to Windows 10 using an alternate credential
- Open Settings > Accounts > Sign-in options
- Select PIN (Windows Hello) > I forgot my PIN and follow the instructions
Reset PIN from the lock screen
For Microsoft Entra joined devices:
- If the PIN credential provider isn't selected, expand the Sign-in options link, and select the PIN pad icon
- Select I forgot my PIN from the PIN credential provider
- Select an authentication option from the list of presented options. This list is based on the different authentication methods enabled in your tenant (like Password, PIN, Security key)
- Follow the instructions provided by the provisioning process
- When finished, unlock your desktop using your newly created PIN
For Microsoft Entra hybrid joined devices:
- If the PIN credential provider isn't selected, expand the Sign-in options link, and select the PIN pad icon
- Select I forgot my PIN from the PIN credential provider
- Enter your password and press enter
- Follow the instructions provided by the provisioning process
- When finished, unlock your desktop using your newly created PIN
Note
Key trust on Microsoft Entra hybrid joined devices doesn't support destructive PIN reset from above the Lock Screen. This is due to the sync delay between when a user provisions their Windows Hello for Business credential and being able to use it for sign-in. For this deployment model, you must deploy non-destructive PIN reset for above lock PIN reset to work.
You may find that PIN reset from Settings only works post sign in. Also, the lock screen PIN reset function doesn't work if you have any matching limitation of self-service password reset from the lock screen. For more information, see Enable Microsoft Entra self-service password reset at the Windows sign-in screen.


