Hello @Benjamin Ra ,
Welcome to the MS Q&A Forum.
This article lists common problems that are related to Microsoft Azure Files when you connect from Windows clients.
Second, try mounting Azure file share with storage account key. If the share fails to mount, download AzFileDiagnostics to help you validate the client running environment, detect the incompatible client configuration which would cause access failure for Azure Files, give prescriptive guidance on self-fix, and collect the diagnostics traces.
Third, you can run the Debug-AzStorageAccountAuth cmdlet to conduct a set of basic checks on your AD configuration with the logged on AD user. This cmdlet is supported on AzFilesHybrid v0.1.2+ version. You need to run this cmdlet with an AD user that has owner permission on the target storage account.
Unzip the files, and run a Powershell with ADM rights where you have the files:
$ResourceGroupName = "<resource-group-name-here>"
$StorageAccountName = "<storage-account-name-here>"
Debug-AzStorageAccountAuth -StorageAccountName $StorageAccountName -ResourceGroupName $ResourceGroupName -Verbose
Above cmdlet performs these checks below in sequence and provides guidance for failures: (here)
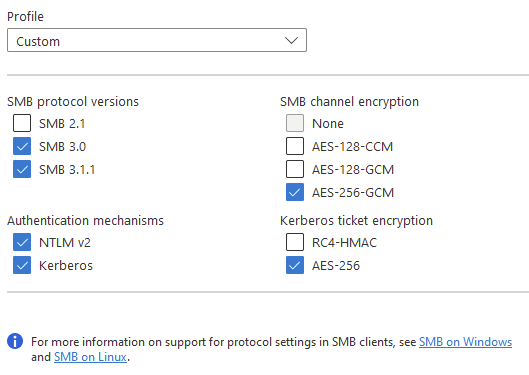
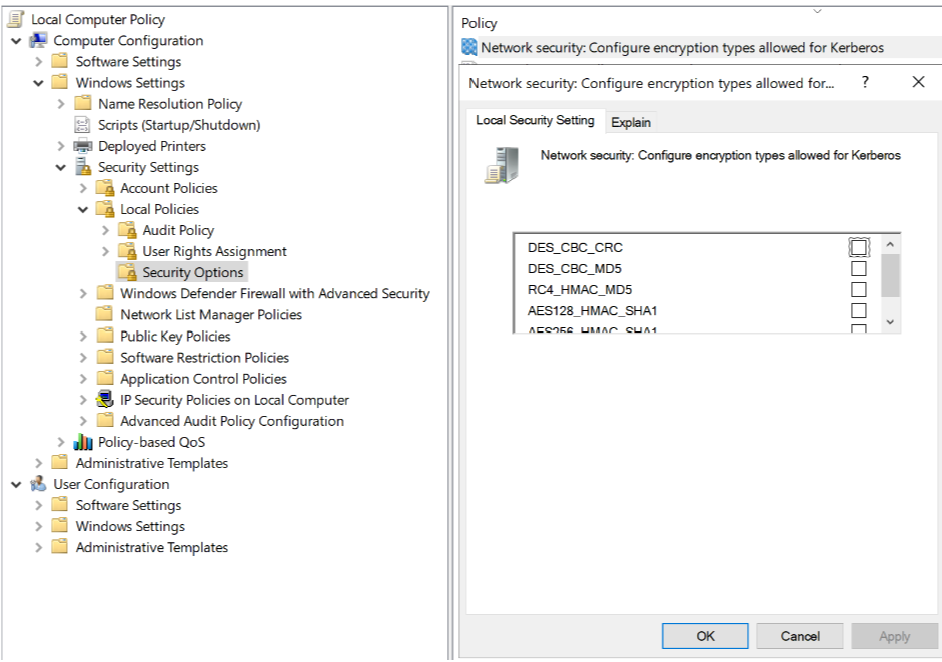
PS: I don't find if this limitation is still actual, anyway I want to point to it: "Issues Description Azure files supports Kerberos authentication with AD auth with RC4-HMAC and AES 256 encryption. AES 256 encryption support is currently limited to storage accounts with names <= 15 characters in length and needs to be manually enabled for accounts which already have AD Auth enabled. "
Sincerely,
Olga Os