@DIKSHANTANTJAIN-7516, I worked upon this ask of yours and a couple of ways is what I could find suitable in your case, as usually, user_type is not an exposed attribute value that can be pulled into saml claims. You can check the approved attribute values that can be pulled in for claims here: https://learn.microsoft.com/en-us/azure/active-directory/develop/active-directory-claims-mapping#table-3-valid-id-values-per-source
Please refer to the screenshot below for a better understanding.
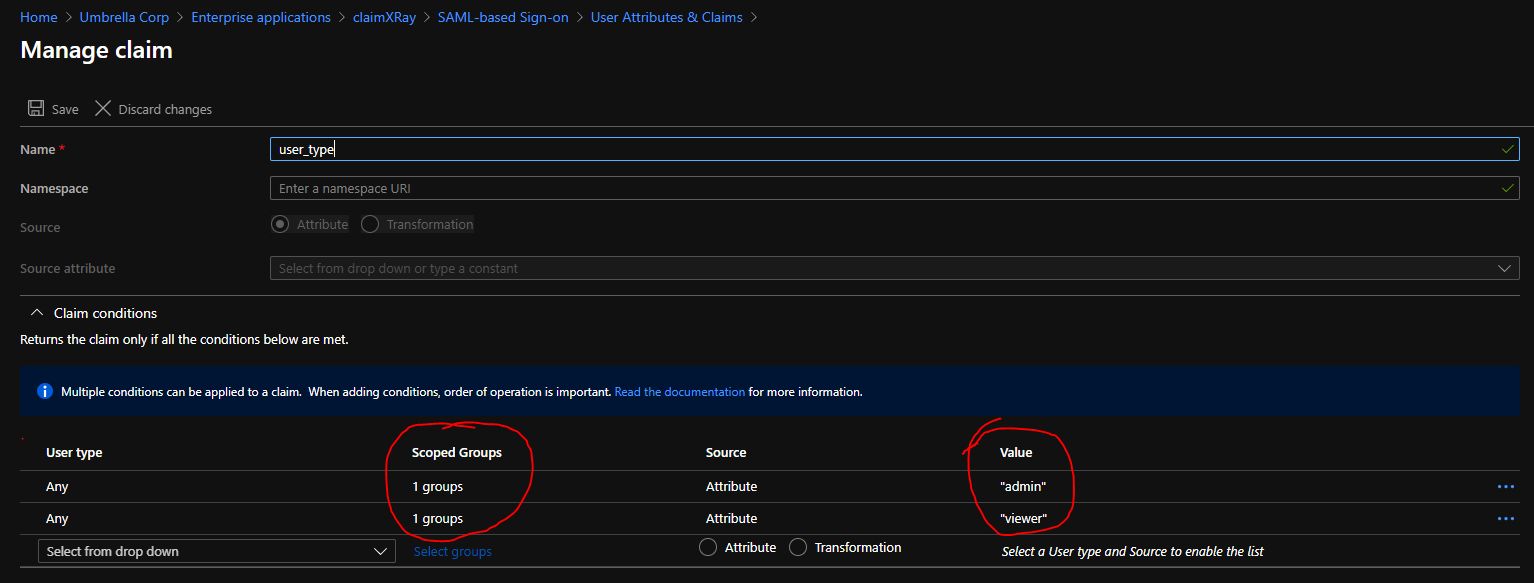
Here I created two groups one called AdminTest which has all Admin accounts in it and the other called ViewerGroup where users that are supposed to get viewers claims issued are added. I added those two groups to the Scoped Groups section of Claim Conditions
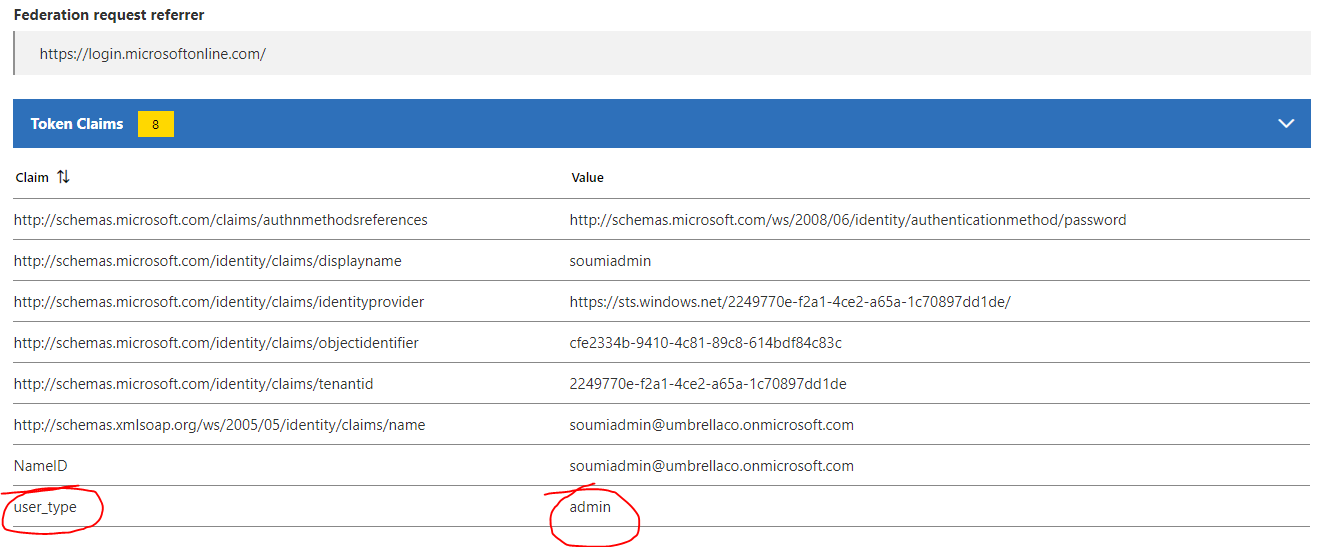
user_type: Admin:
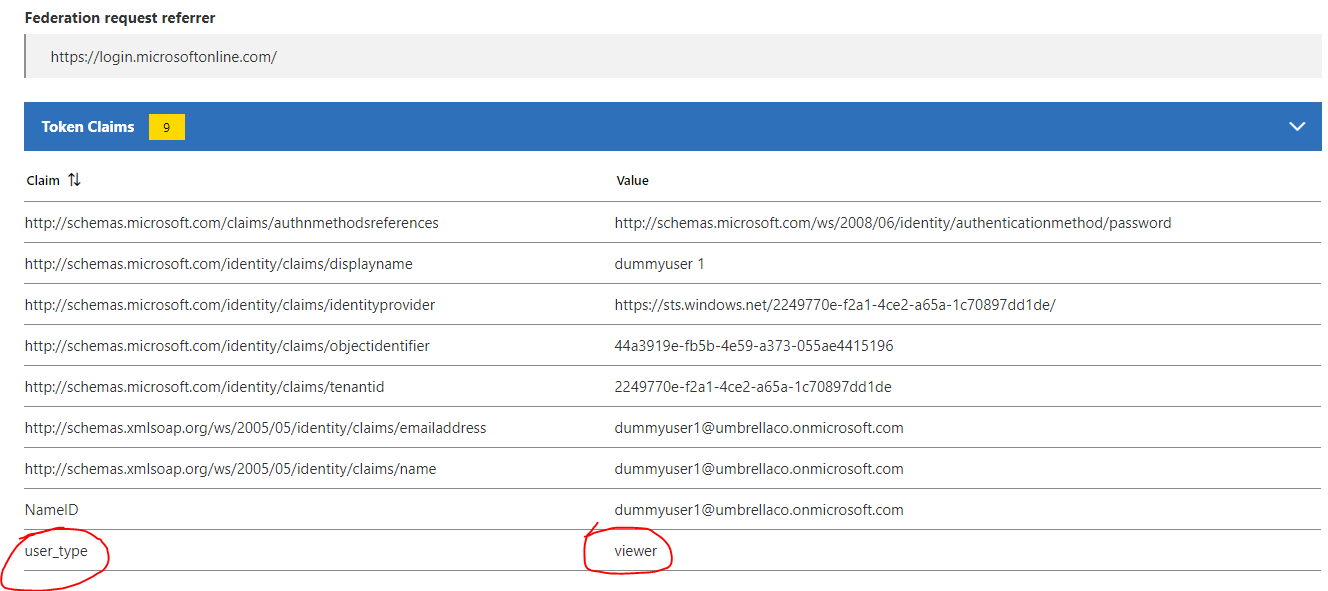
user-type: Viewer
This can be a possibility that you can surely try out for both on-prem and cloud-only users as these are just flat values that are passed based on the Group Memberships of the user. Now the second thing that can also be done is if the user is an on-prem user and has been synced to Azure AD. then you can create the respective extensionAttribute values in on-prem AD and then sync then to Azure AD. When this sync happens, the extension attributes of on-prem AD would be mapped to extension attributes of Azure AD and those extension attributes can be pulled in the saml claims.
Hope this helps.
Do let us know if this helps and if there are any more queries around this, please do let us know so that we can help you further. Also, please do not forget to accept the response as Answer; if the above response helped in answering your query.